NAC Grows Up
There are a million things to take into consideration when building out network security; making sure that even employees and welcomed guests only get in if they're prescreened is right at the top. Still, development of a common industry standard for deploying Network Access Control (NAC) has been elusive as vendors take different approaches to get the job done.
NAC has gotten a bad rap in the past by creating obstacles for end users whenever they didn't follow strict procedures. The process became so clumsy that at one time the technology was referred to as "help-desk call generators." That was certainly no way to endear itself to either a CIO or a CFOand#8212;not to mention every user that needs access.
That's changed today. Even though there's no standard way to deploy a NAC solution (some are hardware-based, some are software-based, some combine both elements), ease-of-use has taken leaps forwardand#8212;as has the industry's understanding of the threat landscape.
There was a time when the impetus for hackers and other forms of cybermiscreants was for "street cred" and bragging rights. Today's threats are, in general, motivated by profit; a guarantee that inventive tactics for penetrating networks and accessing sensitive data are relentless and plentiful.
And so the CRN Test Center looked at three solutions available to VARs to provide both ease of access and security.
Methodology
CRN Test Center reviewers considered a variety of vendors and solutions before finalizing the scope and vendors for this test. Vendors approach the NAC space from a variety of angles, looking at traditional client security, offering desktop agents and comprehensive policy servers. While a majority of the vendors offer an appliance-based solution, a handful of them offer software solutions, leaving channel partners free to source their own hardware.
Reviewers placed themselves in the mindset of a solution provider looking for a comprehensive solution that would work within privacy, compliance and data-retention requirements. The customer network would consist of guests with limited access, along with roaming and on-site users. To balance the competing features, the solutions were restricted to software products. NAC vendors Sophos, Burlington, Mass.; StillSecure, Superior, Colo.; and Symantec Corp., Cupertino, Calif., participated in this review. Reviewers examined the feature set, management interface and flexibility in creating policies and profiles. Ease of deployment was also considered. As usual, reviewers also considered each company's channel program to determine which would be best.
Next: StillSecure Safe Access 5.0 StillSecure Safe Access 5.0
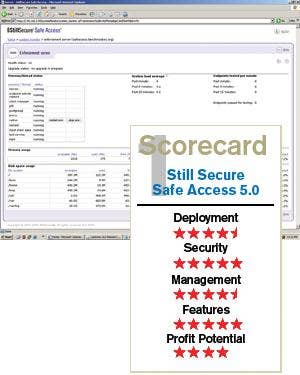
StillSecure submitted its Safe Access 5.0 product for review. StillSecure gives solution providers the option of either getting the software and installing it on their own hardware, or having StillSecure provide the server as well. The company has a list of specific hardware platforms that it has tested the product on and works with the partner to make sure the sourced hardware is sufficient. For the minimum requirements, the server must have at least an Intel Pentium 4 processor at 2 GHz, 2 GB of RAM, Gigabit Ethernet networking, a CD-ROM drive and networking cards (the exact number varies with the type of installation). StillSecure is currently pushing Dell servers as the ideal platform, so reviewers asked the company to source the server as well. The Dell PowerEdge 1950 server came with Intel Xeon processors, a 73-GB SAS hard drive and two networking ports. StillSecure said Safe Access will cost as low as $20 per IP address in a 2,500-user deployment.
Safe Access is deployed as an enforcement server on the network. Depending on the network size and needs, customers can choose to have multiple enforcement servers on the network, and they can all be managed from a single management server. The enforcement server can be installed in one of the three enforcement methodsand#8212;inline, DHCP or 802.1x. Reviewers chose to install SafeAccess inline on a single server. This option means there are no changes required to the network's existing configuration settings. The DHCP method performs an end point assessment before the DHCP server assigns an IP address. The 802.1x method requires a RADIUS server and is ideal for quarantining ports between VLANs.
For deployment, the SafeAccess software needs to be installed on the designated server. No other software can be installed on that machine because Safe Access installs StillSecure OS, the company's own hardened Linux-based OS. Because this was a single-server installation, the management and enforcement servers resided on the same box. The server requires a static IP address and host name, along with other basic networking information. Once the software has installed, the server reboots into Safe Access. The rest of the configurationand#8212;time information, admin password, etc.and#8212;is done with a workstation using a Web browser with at least 128-bit encryption.
The management interface was cleanly laid out in a three-pane window. All the options for policies, reports and configuration were available to the left, information was in the middle pane, and more details and information were to the right. User authentication can occur against LDAP or a RDBMS. For testing, reviewers used an LDAP-based server.
StillSecure's Safe Access performs authorization based on the physical device. This means all the users must meet the same end-point-security requirements (patches installed, antivirus running, etc.) before being allowed network access. StillSecure does support authorization based on user roles to a limited extent, where different security requirements kick in, based on whether the user is connecting from a VPN or LAN. This can be defined by creating a NAC policy for LANs, VPNs, wireless, etc. After creating the NAC policy, the end-point checks can be mapped to a device group. The NAC policy is not created on the individual user level.
When a guest tries to connect, an Active X agent performs a system assessment on the guest's machine. If the guest passes muster, they are allowed onto the network. While the initial checks are run before the client is allowed on the network, Safe Access can be configured to retest end points at set intervals. So if the guest turns off the antivirus after connecting to the network, a retest will find that and correct it. Safe Access supports most major antivirus products and many of the smaller ones, such as ClamWin and Panda. It also supports personal firewalls such as Check Point's ZoneAlarm. And it can check for Windows operating system patches and for other software packages, such as Microsoft Office.
Many of the checks are configured into the box, such as operating system services and security authentication. Safe Access also supports custom checks, so tests to ensure an in-house-application is installed, or that there aren't certain files on the machine, can be created. The checks are created using a Python-based process. Programming-savvy IT admins can develop their own checks, but this is an area where solution providers can offer value.
Next: Symantec End Point Protection Client And Network Access Control Symantec End Point Protection Client And Network Access Control
Today, Symantec's NAC solution automatically remediates machines that are placed into quarantine. This solution eliminates the need for users to connect to special sites. Symantec offers a layered architecture, where users seeking access are routed through a single gateway enforcer server, a policy manager with a central management console and an end-point client.
Symantec's NAC also works with third-party software patch solutions like Altiris and Microsoft Systems Management Server to automate patch management. Contractors, consultants and even employees that are connecting with other users' machines can take advantage of this flexibility. The users don't need to have persistent access point clients on machines that they're using temporarily.
Now at version 11.0, Symantec's End Point Protection Client and Network Access Control management tools arrive with multiple enforcement optionsand#8212;802.1x, DHCP enforcement, LAN enforcement and a host-based self enforcement. But NAC is more about checking the integrity of end points than it is about figuring out the authentication process through Active Directory, LDAP and 802.1x RADIUS. The self-enforcement option, for instance, is the easiest method to deploy for companies looking to introduce NAC.
Host-based self-enforcement uses personal firewalls installed on end-user machines. In a self-enforcement scenario, devices check their own statuses. If agents don't find them compliant, they will automatically switch the machines into a quarantine state. The process is driven by policies.
Administrators can create quarantine policies for firewalls, antivirus, desktop IDS/IPS and particular device controls. Symantec's NAC tools go beyond network devices, too. The policies work on just about any device that is accessible through IP and SNMP.
The enforcer will detect clients that are trying to connect and will challenge them to see if they have agents installed. Clients without agents are processed through a scanner. Noncompliant clients end up in a quarantine zone or blocked altogether. Symantec's NAC offering also has a peer-to-peer enforcement option. With this option, only employees from the same group can connect into a LAN.
Scanning without agents has one advantage: It doesn't require loading agents. However, it's extremely limited. There's also a delay for users that are trying to come in through gateway, VPN or other external access points.
Dissolvable agents, which can perform the same functions as the permanent agents, tend to be the most popular way to interact with clients. Even the authentication process runs the same way, but as clients pass through the authentication process the agents delete themselves.
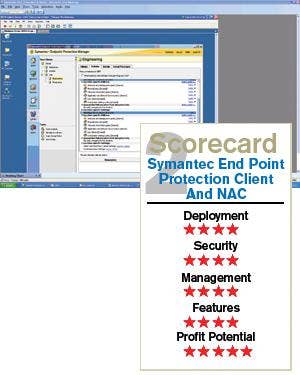
Overall, Symantec's NAC solution is simple to deploy and manage. The management interface is intuitive enough that even junior administrators can create sophisticated policies with little assistance. The Test Center found the products quite comprehensive in their coverage.
Next: Sophos NAC Advanced Sophos NAC Advanced
Sophos NAC Advanced, like the others, is a software-based solution. The premise of how the solution works is a three-way strategy to protect the end pointand#8212;by assessing Microsoft security patches, antimalware software and personal firewall.
Sophos' claim is that this type of end-point-driven focus is important to counteracting today's type of security threats.
Sophos NAC Advanced is capable of monitoring managed and unmanaged computers. Managed PCs are assessed through an installed, persistent agent. Unmanaged PCs (unknown on the network, or "guest users") are assessed through Web technology.
The testing environment consisted of a Windows 2003 server on which NAC Advanced's Console, Enterprise Console and DHCP enhancer were installed. In addition, two Windows XP clients served as guinea pigs: one client a managed one with the agent installed, and the other unmanaged to test the Web interaction capabilities.
Upon logging into the managed client, Sophos' NAC registered and updated the PC with the latest policy information. The unmanaged PC was kept quarantined off-network until going to a designated URL to make it compliant.
Policies, with Sophos' product, can be enforced in a couple of different ways: DHCP, VPN (IPSec or SSL) or 802.1x. There is also an agent enforcement option built into the NAC agent.
The management interface is detailed and customizable. The only critique is that interfaces seem to be all over the place. There's the Enterprise Console and the NAC Console. The Enterprise Console is a dashboard that gives an overall look at the NAC-protected environment of a network. Items listed can include the number of managed or unmanaged computers, status on updates (which evoke an MMC snap-in) and alerts on computers with malware or suspect files. The interface also offers a more drilled-down view and the state of the machines' antivirus versions, firewall and any alerts or errors. Threshold levels can be defined; if a level is exceeded, the dashboard status indicator reflects urgency. SMTP e-mail alerts can be sent as well.
Reporting is another feature. Reports are customizable and can be viewed in tabular or chart views. Reports are exportable as PDF, Excel, Word, HTML, RTF, XML or HTTP. Inside a generated tabular report, any alerts listed are hyperlinks, which will redirect to Sophos' Web site for additional information.
The NAC Console differs from the Enterprise Console primarily because it is there that policies and profiles are configured. There were a couple of "what-if" scenarios reviewers posed. For instance, machines are checked to ensure they have the latest antivirus signature files. This is a good protection against known threats. A zero-day attack would still leave a NAC-protected machine vulnerable.
Sophos contends that zero-day protection is integrated with its antimalware protection, which employs Behavioral Genotype technology as a defense against zero-day exploits. For zero-day protection, NAC is only as good as the antimalware solution deployed in an enterprise.
There are also spoofing and the possibility that a machine appears to have, but does not have, the proper compliancy requirements. Sophos states that its solution uses a multitude of checks, such as, files, registries, processes and APIs.
NAC Advanced currently only supports the Windows platform, but Sophos has plans to include other platforms. Reviewers would also liked to have seen "in-the-box" policies designed for specific regulations like PCI and HIPAA.
Next: The Bottom Line Bottom Line
In many cases, a software-based solution for NAC will meet the needs of an organizationand#8212;and provide an integrator with the opportunity to wrap custom solutions or services around it.
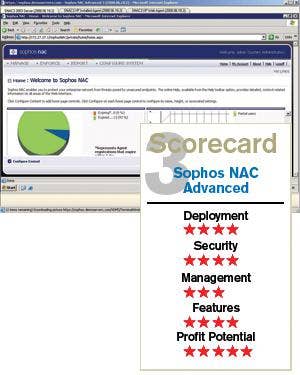
After evaluating each of these products, the Test Center found that StillSecure's Safe Access 5.0 slightly outpaced the others, followed by Symantec's solution and then Sophos'.
Safe Access 5.0 is robust and customizable, justifying adding a NAC as an extra layer of security. Symantec offers a nice solution, but finds itself more limited than Safe Access 5.0 without deploying agents. Sophos, too, is good, but we were left wanting more. While all the solutions could be fine in particular deployments, functionality led us to choose Safe Access 5.0 first, Symantec second and Sophos third in this comparative review.
Five Key Players
in Network Access Control
COMPANY:
Sophos
\
Burlington, Mass.
\
(781) 5800
\
\
\
KEY PRODUCT:
Sophos NAC Advanced
\
\
CHANNEL POINTS:
Sophos has a three-tiered partner program Platinum, Gold and Silver. A training and
program is offered as well as 24-hour technical support, dedicated channel managers, sales and marketing tools, free product training and increased margins.
COMPANY:
Symantec
\
Cupertino, Calif.
\
(408) 517-8000
\
\
\
KEY PRODUCT:
Symantec End Point Protection Client and Network Access Control
\
\
CHANNEL POINTS:
Symantec has a four-level partner program: Registed, Silver Gold and Platinum. All levels receive access to markeing tools as well as access to the PartnerNet
and Tools. A configuration/quote generator tool is also available for all partners. Online technical support is available for all partners, but 24x7 support varies among levels.
COMPANY:
McAfee
\
Santa Clara, Calif.
\
(866) 736-3971
\
\
\
KEY PRODUCT:
McAfee Network Access Control.
\
\
CHANNEL POINTS:
McAfee offers an extensive and varied partner program with four divisions: Security Innovation Alliance Partners, McAfee Service Provider Partners,
Partners and Partner Security Services Partners. Partners receive support, training marketing tools and substantial incentives and rebates.
COMPANY:
Juniper Networks
\
Sunnyvale, Calif.
\
888-JUNIPER (888-586-4737)
\
\
\
KEY PRODUCT:
Juniper Networks UAC deployed with EX-series Ethernet switches
\
\
CHANNEL POINTS:
Juniper's andquot;J-Partnerandquot; architecture, provides an array of partner programs designed to provide partners with the tools they need to deliver customer satisfaction. Tncentives, training and support spans across all of their partner programs.
COMPANY:
Trend Micro
\
Cupertino, Calif.
\
(800) 228-5651
\
\
\
KEY PRODUCT:
Network VirusWall Enforcer
\
\
CHANNEL POINTS:
Trend Micro offers three partner programs SecureOne Partner, Vantage Partner and VantageONE Partner. Technical and Sales certification as available for partners. Vantage partners can participate in the Vantage Rewards program and receive cash for selling Trend Micro products.
Mario Morejon, Fahmida Y. Rashid and Samara Lynn contributed to this story.