Sanctum AppScan Helps To Catch Security Flaws Before They Creep In
Catching a defect during deployment now runs about 100 times more expensive than modifying it in the code at design time, and the price will only increase as SOA and composite applications become the preferred application development method. If not resolved, these problems will allow hackers to easily take down a system, steal identities and even change critical data.

\
MARIO MOREJON
\
Technical Editor
Unfortunately, security flaws are made quite frequently, and corporate firewalls often are useless when a security hole exists in an application. Nonetheless, there is hope in the form of Sanctum's AppScan, which helps developers test their applications at design time.
Sanctum AppScan DE 1.7 can test for security defects while developers write the application. The tool has wizards that make it easy to use in .Net and Java. In three easy steps, AppScan tests, shows recommendations for fixes and provides answers for fixing the code. The tool can be installed as a plug-in to leading IDEs such as IBM WebSphere Studio, Eclipse, JBuilder and Visual Basic 6, so developers do not have to go outside their favorite environments to run tests.
For Java developers, Sanctum also provides code samples of how to build input validations and how to use the tool correctly. For .Net, AppScan simply points developers to existing facilities in .Net where they can fix their application.
Proponents of service-based architectures believe that reducing business logic in source code by splitting it into smaller manageable components will enable programmers to discover most security leaks at design time. Although that might work with applications that are created from the ground up with the architecture, most composite applications have many legacy dependencies that could pose security risks. Since most existing applications are simply wrapped with a messaging interface to enable them to communicate as Web services, hackers can still penetrate these systems by finding indirect ways to access legacy components.
The messaging layer required by Web services also can pose other security problems when working with XML, such as denial-of-service attacks or applications being tricked into changing the location where documents are validated.
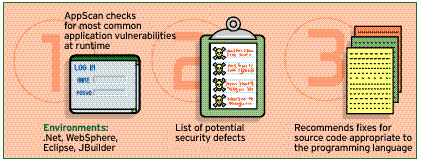
AppScan helps determine when legacy applications are exposed by recommending which fix is appropriate. In a composite application, the developer has to manually determine if the security hole matches anything in the service. If no defects match what was listed by AppScan, all the legacy modules in the application have to be checked manually by re-creating a similar test.
A manual workaround can be done by extracting the business logic from the legacy code that requires input and by creating new rules in the Web service based on those inputs. This mechanism can enforce some restrictions, but it is not foolproof. Developers should still use AppScan repeatedly until all tests show no warnings or
recommended fixes.
Unfortunately, Sanctum only sells testing tools that examine runtime code and cannot trace code in debug mode. The current versions cannot even determine the location of the flaw in the code. Working with composite applications can make this task more difficult for AppScan users.
Any layer of a Web application can compromise data, so AppScan checks for most security vulnerabilities such as buffer overflows, cross-site scripting, cookie poisoning and missing Web server patches. The tool can also check for flaws in parameters such as SQL injection attacks or some brute force password-guessing methods.
AppScan separates all its tests into two categories: common Web vulnerabilities or application-specific defects. Most common Web vulnerabilities fall under typical problems with an infrastructure. These problems are vendor-related and can be resolved with patches. The window of exposure is often short, and it usually takes less than a year for the vendor to release a patch. Because application-specific defects are built by customers or solution providers, they tend to last a lot longer and are usually discovered when an audit is performed or when a hacker breaks in.
CHANNEL PROGRAM SNAPSHOTS
>SANCTUM APPSCAN (CRN Test Center Recommended)
PRICE: $1.495
MARGIN: 35 percent
DISTRIBUTORS: Direct from vendor
TECH RATING:

CHANNEL RATING:

CHANNEL OVERVIEW: Sanctum, Santa Clara, Calif., assists partners in either selling or integrating AppScan. The vendor's channel managers and direct-sales representatives participate in joint sales and marketing activities. Sanctum's partner Web site includes collateral materials and other marketing resources as well as a Q&A tech support database. On-site technical and sales training are provided.
Note: Vendors can earn up to five stars for technical merit and five for their channel program. If the average of these two scores is four stars or greater, the product earns CRN Test Center Recommended status.