Data Leakage: VARs Can't Just Be Plumbers
If it's true that loose lips sink ships, then it's also true that confidential data leaking from corporate networks can bring the highest-flying companies crashing to earth.
As more organizations wake up to the need to secure confidential data on their networks, solution providers are seeing growing interest in data leak prevention.
Sensitive information in databases, spreadsheets, e-mail archives and documents spread throughout the network can be lost in many different ways: by employees e-mailing unencrypted documents; through infection by a virus or worm; by malicious insiders taking advantage of lax security measures; and via stolen laptops and storage devices.
While not all data leakage is crucial, the loss of source code, product plans or customer lists can be. And as TJX Companies, the owner of TJ Maxx and other retail chains, recently found out, stolen credit card data can have a damaging impact on the corporate brand. With all the publicity surrounding such security breaches, data leak prevention—or DLP—is becoming a hot topic, with a number of vendors getting into the market.
But solution providers say DLP is not just about products for locking down all the ways data can be lost or stolen, it is also about helping companies shore up outdated processes that can lead to data leakage. As one Fortune 500 CEO recently told a solution provider interviewed for this story: "I don't just buy DLP to stop theft—I also buy it to stop stupid."
DLP Moves Into The Mainstream
After catching on first in the highly regulated financial and medical industries, which use the technology to lock down mountains of personally identifiable data for compliance reasons, DLP is now moving steadily into the mainstream, solution providers say.
Joe Luciano, CEO of Access IT Group, a New York-based solution provider, said that he's seen momentum in the DLP market increase noticeably over the past six to eight months as market perception of DLP shifts from something to prevent unauthorized use of USB drives to a viable technology for protecting data anywhere on the network. "In general, DLP is anything having to do with information you don't want leaving your virtual premises. In that context, almost every company, including small- and medium-size ones, needs to have this," Luciano said.
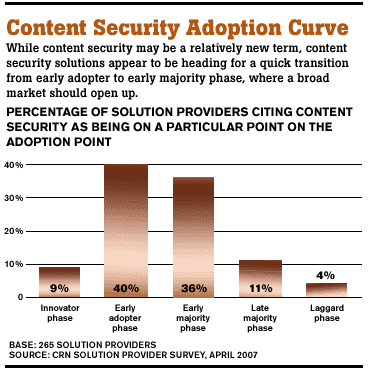
Even in nonregulated industries, companies are starting to realize the need to protect intellectual property. IDC predicts the market for solutions that discover, protect and control confidential data to grow 33 percent annually, from $1.1 billion currently to $3.2 billion in 2011. In the April CRN Solution Provider poll, nearly a third of solution providers placed content security solutions, of which DLP is a key component, in the early majority adoption phase. "Data leakage is something that hits the pockets of small organizations as well as large ones," Luciano said.
The high cost of DLP solutions, though, continues to inhibit broader adoption. Stopping data leaks from desktops and laptops, for example, can cost up to $25 to $50 per end point, Luciano estimated. Other solution providers said the hefty price tag, combined with the reality that many companies don't realize they have problems with data leakage, means DLP is a different type of buying decision. "Not everyone has a budget for DLP, and I think you're going to see a lot of pushback from companies unless they've had a breach," said Larry Dannemiller, president of Business Security Solutions, Houston. "Selling DLP is definitely not like selling a firewall."
Another stumbling block is that DLP solutions require policy changes and can be disruptive. Jamie Bjerke, director of technical services at Information Security Technology, St. Paul, Minn., said most customers aren't going full throttle yet on DLP because of concerns that it could throw their business processes into disarray. "With most detection mechanisms, there are some concerns about blocking traffic," he said.
Next: The Services Opportunity
The Services Opportunity
All DLP products hinge on defining and implementing policy controls. Although it's easy to create policies, developing effective ones requires a level of expertise, and that's where the channel comes into play. The size and scope of DLP implementations spells opportunity for VARs, and CRN spoke with several who have had six-figure DLP engagements consisting of software and services. For large enterprises, DLP can easily add up to projects of several hundred thousand dollars.
"These are big deals with long sales cycles in the range of six to 12 months, and deployments ranging from a few days to a few months," said Sreekanth Ravi, chairman and CEO of Code Green Networks, a Santa Clara, Calif.-based startup targeting the SMB market with a DLP product.
DLP-related services include data classification and protection, project management, hardware and software installation, and deployment and testing of the technology. "DLP is a complete project management flow, as opposed to just putting in a box and turning it on," Dannemiller said. He estimated Business Security Solutions receives $3 in consulting services for every dollar spent on hardware.
Organizations are looking to solution providers for help in creating and managing policies governing access to data as well as its movement within the network, which could include outlining how information lives in a database. "There is a lot of work that needs to be done on the front end in terms of understanding what data needs to be secured and in classifying data throughout an organization," Bjerke said.
Security integrators with the skills to effectively classify data as critical and noncritical and fingerprint data so it can be tracked and harder to hide are seeing no shortage of opportunities, Dannemiller said."A lot of vendors' products will catch fingerprinted data in outgoing e-mails," he said. "But there are tricks and techniques to get around this, like hiding data in ZIP files, pasting confidential data from Microsoft Word into Powerpoint, and changing file names."
New Skill Sets Required
While conventional security skills are sufficient for inbound threats, the outbound protection on which DLP depends requires information management skills that are not so readily available. When DLP technology first began to emerge, solution providers would focus mainly on figuring out where sensitive data resided on the network and how to protect it. Since then, the scope of DLP has expanded to account not just for data in motion, but also data at rest.
As a result, DLP projects over time have evolved to include both security and storage technologies, said Paul Adamonis, director of security solutions at Forsythe, a Skokie, Ill.-based solution provider. "Data in motion still needs to be protected and kept from going out, but it's increasingly being coupled with data classification initiatives and the need to identify who's accessing what files at which point in time," he said. "DLP has become an all-encompassing policy around data classification and protection."
Ravi said solution providers also must also have deep knowledge of different types of documents and protocols. "Traditional security skills are easier to find than the information management skills required for outbound content management," he said. "That's why it's important for DLP vendors to build channel programs and recruit partners that can help you reach all parts of the market."
Ken Phelan, CTO of Gotham Technology Group, a New York-based solution provider, said the initial setup of DLP solutions is fairly simple. The bigger services opportunity is in dealing with all of the alert data that DLP solutions can generate. "You're going to get a lot of incidents in any size organization, so the challenge is to prioritize the incidents and figure out how to tighten up the processes," he said.
Embedding DLP technology into an organization's processes usually involves heavy collaboration between the client and the VAR, Phelan added. "These include PMO processes, data processes and the big question: 'What's the best place to encrypt?' " he said.
Next: Manageability Key In Vendor Selection
Manageability Key In Vendor Selection
To deal with the mountain of alerts generated by DLP solutions, manageability may be the single most important consideration when selecting a vendor.
"Having a management console telling you what's going on is the key to avoiding false positives, which is a big issue with DLP," Dannemiller said. "The management console allows companies to go in and decipher what happened and is especially good at answering questions like: 'Did we block it? Is it encrypted?' "
Vendors such as 8e6 Technologies, Orange, Calif., Finjan, San Jose, Calif., and Clearswift, Redwood City, Calif., offer DLP as part of a more comprehensive content security solution such as content filtering or antimalware. Those products tend to have advanced management interfaces and a tighter coupling to the network. That can simplify ongoing management and better integrate DLP into an overall security solution. Finjan and Code Green have also approached DLP from the bigger picture of compliance and have incorporated compliance reporting and auditing tools into their products.
Dannemiller said the management console should generate an all-important audit trail that shows whether the risky behavior associated with one user also has been going on with other users. When a leak incident occurs, "you build one story, and it lets you know what to block, determine the severity of the breach and stop the same thing from happening again," he said.
Each vendor's DLP offering has components that focus on monitoring data at different parts of the network. Some products cover data at rest, using a software agent installed on desktops, while others watch for leaks at the network gateway.
The iGuard appliance from Reconnex, Mountain View, Calif., for example, sits at the network edge and passively monitors all traffic via an Ethernet tap, taking action when a policy is violated. The benefit to that design is minimal impact on network performance and elimination of software agents.
Vontu, San Francisco, has a product line that combines monitoring data at rest and data in motion to cover all the bases. Vontu takes the approach that if all information access is cataloged, it becomes much easier to control who accesses the data and where that data is going.
Another consideration is the vendor's channel orientation. Websense, which bought PortAuthority last December, and McAfee, which acquired Israel-based DLP startup Onigma in October, are two of the largest early movers that sell DLP solutions through channel partners. Symantec provides a subscription-based DLP service through an OEM agreement with Vontu.
Vontu has taken a more direct route to market, with less than a third of its revenue going through channel partners, said Steven Roop, vice president of products and marketing. However, Vontu works with 18 channel partners in North America that provide services around its DLP products, Roop said.
At this early stage, solution providers need to be aware that many vendors are startups and some have chosen a direct route to market. In order to survive, smaller players are going to take deals however they can get them, including direct, Code Green's Ravi said. But despite the direct-sales orientation of some vendors, Ravi insists that DLP is a channel-friendly technology. "This was the case with the firewall until the appliance came along and removed much of the complexity," Ravi said. "But the DLP market hasn't reached that stage yet."
Completing The Puzzle
DLP vendors initially focused on network-based protection, but the ability to prevent data leaks from desktops and notebooks is fast becoming a must-have for companies with large numbers of mobile workers. "In the mobile world, where people aren't well connected to the corporate network, it kind of drives you to the host-based approach, to make sure data is protected everywhere," Bjerke said.
While some vendors offer host- and network-based protection, there still isn't a single solution that protects both data at rest and data in motion, Adamonis said. "Our customers seem to be focusing on one over the other because there is no real complete DLP solution right now," he said.
As the market consolidates, Adamonis expects to see acquisitions aimed at filling the gap and yielding a comprehensive solution. In the meantime, the good news for the channel is that DLP technology is still developing and is a long way from becoming commoditized, which means there's still time for early movers to grab a piece of the market. As Dannemiller put it: "You won't see CDW selling this stuff."