Network Access Control Made Easy
Network access control technology was the darling of the security industry in 2006, as vendors spent much of their time squawking about how their NAC offerings could do just about everything but cure cancer. Yet now that the hype around NAC has quieted, a clearer picture is emerging about what the technology means for the channel.
So far, the news is good: Solution providers that have made time and financial commitments to learn how to deploy NAC are seeing steady services revenue before and after the actual implementation. Driven by compliance pressures, NAC itself has become a household term, although some solution providers still find they need to educate consumers as to why they need the technology and how it can help their security posture.
There appears to be lots of room for growth in the NAC market, which IDC expects to jump to $3.2 billion in 2010 from $526 million in 2005. So far, most of that is being driven by verticals such as finance, health care and education—all of which have compliance-related reasons for compartmentalizing their networks through access policies.
Universities are one of the fastest adopters of NAC—a result of their open networks and students bringing notebook PCs in and out of their networks on a regular basis, leaving the digital equivalent of muddy footprints all over the network at the start of every semester.
Yet, VARs will find that NAC readily extends well beyond the education and financial markets. The very concept of controlling access to the network is tantamount to security practices. Basically, the size of the business becomes immaterial when it comes to protecting information, and the best way to protect that information comes of knowing who has access to the network and if that access is appropriate.
Many solution providers believe the key to cutting through the hype around NAC is to understand the nature of what the different solutions are designed to achieve and be able to clearly explain to customers how it will benefit them.

Perhaps the most important concept to grasp is how NAC differs from traditional security measures. In the past, security was built around file access—in other words, who could access which files. While that proved to be effective for protecting intellectual data, file-level security did not offer any control over what was done with that data.
With security needs growing to encompass endpoints and connectivity, it quickly became clear that controlling file access was not enough to protect a network, which is where NAC comes into play. In short, NAC unifies security controls and focuses on the controls in place to allow access to the network. Of course, file-level security remains a key tenet of data protection, but NAC enhances security by keeping unauthorized persons and devices from connecting to the network in the first place. That translates to building file-level security to handle the needs of the trusted insider, while NAC solutions keep every one and every thing else out of the network to begin with.
"The primary aim of NAC is endpoint risk mitigation from notebook PCs, flash drives, wireless devices and endpoints in an open environment, which have a much bigger risk footprint than environments that are more locked down and restricted," said Peter Bybee, president and CEO at Network Vigilance, a San Diego-based solution provider.
Next: Flash The Skills
Flash The Skills
Solution providers that have several years of deploying NAC under their belts say the biggest challenge and cost is getting the right people to do the work.
Tim Hebert, CEO of Atrion Networking, a VAR in Warwick, R.I., said the first mistake he made with NAC was having Cisco Systems-centric people handling NAC implementations. "They were strong in networking and security, but the challenge with NAC is you start dealing a lot with end users for things like desktop and application issues," he said.
So Atrion decided to start having people with Microsoft skill sets handle the implementations, he said, because they could bring something that was a very important part of the NAC puzzle—an understanding of Active Directory and desktops.
Atrion gave its NAC staff a weeklong refresher course on basic TCP/IP skills, with emphasis on setting up virtual LANs, followed by a week of NAC product-focused instruction with formalized training and lab trials, Herbert said. After that, training concluded with a couple of days showing staff how to optimize the NAC solution.
While NAC touches both networking and security, VARs have to be especially good at discussing security issues with customers in order to close deals or at least be able to articulate common problems that companies struggle with that NAC can fix, Bybee said. "You have to have that firmly in your grasp before knocking on the door of any CIO or CSO," he said.
Preston Hogue, chief security officer at Network Computing Architects, a Seattle-based integrator, said the key to success with NAC is to have a strong security practice, because developing and enforcing policies are the armor that gives NAC solutions their effectiveness. "Implementation of NAC begins with making sure the network is architected properly, with the right switches and routers installed. But after you've done that, then it's all about policy," Hogue said.
Like other emerging technologies, VARs should expect to absorb some cost to get their staff trained on implementation. Cisco offers its channel partners discounted NAC training courses that help ensure that staff involved in deployments have the skills necessary to do it right, Hogue said. Network Computing Architects has sent four staff members through the training thus far, at a cost of $2,500 per person. "People that do NAC implementation work for us are generally more senior people because you need to have a deep understanding of switching and routing, which means it's not a good idea for entry-level people to be doing it," Hogue said.
VARs need to remember that profits from NAC implementations don't just end with the sale of a NAC solution. NAC can be treated as yet another layer of an overall security plan. Truly secure networks are built from various pieces of security technology, and NAC is only one piece of the puzzle.
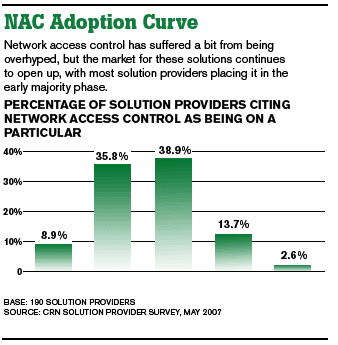
VARs looking for opportunities can use NAC as a starting point to building unified security solutions, which encompass technologies ranging from secure remote access to anti-malware technologies to single sign-on solutions. In other words, NAC offers a huge integration opportunity for the security-savvy VAR. The lists of add-ons can be quite extensive and includes technologies such as endpoint control, patch management and security auditing. The idea here is for a VAR to build a product matrix of security technologies that uses NAC as a foundation. First, control who enters the network, then control what they can touch or do, all the while keeping unauthorized users, applications and devices at bay. It's a significant undertaking, to say the least, but one that brims with margins and service revenue.
VARs looking to get into the NAC market must evaluate vendors' technology as well as keep track of which vendors have taken channel-friendly routes to market, said Brian Haboush, vice president of business development at Intelligent Connections, a Royal Oak, Mich.-based solution provider.
But there is significant differentiation that exists between the channel programs of vendors in the NAC market, Haboush noted. "You have to evaluate several vendors to figure out what horse you're going to ride—that can be anything from testing a single product to [evaluating] multiple vendors," he said.
Next: At Your Service
At Your Service
NAC is a services-rich technology that quickly pays dividends for solution providers that make the necessary investment in training. However, VARs need to be aware that the sales cycles for larger projects can be as long as a year, and several solution providers told CRN that for those who are just getting into the NAC game, smaller projects are best.
Integrating NAC with Active Directory and developing access policies are examples of the types of services that have helped VARs such as Paul Graffeo, vice president of sales and marketing at RBTi, Atlanta, develop healthy NAC practices.
A high level of integration is required for health monitoring, the portion of NAC technology that ensures that devices accessing network resources and applications meet policy-based criteria for virus definition levels and quarantines non-compliant devices, according to Graffeo.
"You should be able to get 20 [percent] to 25 percent in services dollars for every NAC product you sell," Graffeo said. "Plus, you have a lot of project planning and post-implementation support services, and you can provide that augmentation for help desk, password reset and systems maintenance."
At this stage in the market's development, some solution providers have found NAC to be a complementary add-on technology to wireless or remote-access projects. These types of deployments also tend to have the shortest sales cycles due to their relative simplicity, Hogue said.
"We always try to get customers to focus on putting in NAC for remote access or for wireless to keep the scope limited, and then expand it later to more users and through the rest of the enterprise," he said.
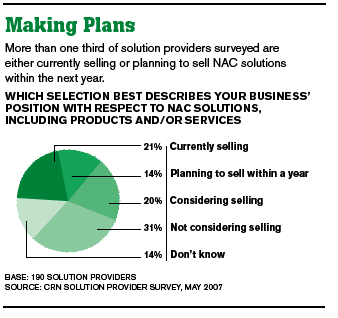
For larger projects, especially ones that involve overhauling the network with 802.1x compliant infrastructure, solution providers need to gear up for sales cycles from six months to a year in duration.
"If you try to do the entire thing from the outset, you're going to have issues with cost, and you'll also need to understand the environment more, which requires more in-depth analysis that will obviously delay the sales cycle," Hogue said.
NAC is an educational sale, and a big part of that involves telling the story of how it can help clients, while also figuring out where it fits into their architecture, said Network Vigilance's Bybee. "Once the light bulb goes on, it's no problem, but takes a whole lot of positioning for that to happen for some customers," Bybee said.
In fact, translating the issue of how to mitigate risk is an area where solution providers often fall short when discussing NAC with customers, Bybee said. "That's an area where solution providers are struggling now, and you have to develop strategic selling skills in order to quantify that risk," he said.
Words Of Wisdom
There's a lot of mistrust in the NAC space today because of the earlier hype and because NAC solutions haven't been perfect. But the technology has come a long way in the past few years, said Atrion's Hebert.
"I think the market understands NAC and the philosophical need for it," he said. "But I don't think a lot of organizations understand how NAC impacts their network and why it would apply to their organization."
Selling NAC also can be difficult simply because it's a technology that requires the input of several different parts of an IT organization. But getting these disparate groups thinking in a federated way can help organizations tackle much of the notoriously thorny work around IT compliance, VARs said.
"Functionally, you have to include department heads to help with what policies their group has and what resources they have access to in order to implement the right access controls. But with NAC installed, you have three-quarters of the compliance puzzle done," Graffeo said.
However, to get NAC installed with a minimum of fuss, it's crucial for solution providers to start off with simple, barebones network access policies—otherwise, organizations can get overwhelmed and even decide to pull the plug.
"You have to scope it out very specifically at first, and you need to get them used to the policy before migrating to more complex policies," Network Computing Architect's Hogue said. "By minimizing what the policy is going to be at the outset, it becomes easier to have a successful implementation and easier to actually close out the project."
As NAC steams slowly toward mass-market adoption, solution providers have a window of opportunity to use their sales and technical skills to convince customers that they need the technology. And the time to act is now, because many solution providers believe that NAC eventually will become integrated into the network infrastructure.
"Now organizations have a choice to buy NAC, but in the future they won't have a choice because it will be integrated," Hogue said. "One thing's for certain, though: We're going to look back and wonder how we ever made it without NAC."
Next: Nine Key Players In The Network Access Control Market
Nine Key Players In The Network Access Control Market
COMPANY:
Cisco Systems
\
San Jose, Calif.
\
\
(408) 526-4000
\
\
KEY PRODUCT:
Cisco NAC Appliance (formerly Cisco Clean Access) is an easily deployed Network Admission Control (NAC) product that uses the network
to enforce security policy compliance on all devices seeking to access network computing resources.
\
\
CHANNEL POINTS:
The Cisco Channel Partner Program consists of Select, Premier, Silver and Gold levels and offers certifications, specializations and incentives. Partners have the option of focusing on being a provider of broad, integrated networking solutions, highly specialized solutions or both.
COMPANY:
ConSentry Networks
\
Milpitas, Calif.
\
(408) 956-2100
\
\
KEY PRODUCT:
The LANShield
and LANShield
support the admission piece of NAC by leveraging an organization's existing authentication, authorization and accounting (AAA) servers and identity stores as well as its host
infrastructure. Where applicable, the LANShield products can actively participate in user
and host posture checks.
\
\
CHANNEL POINTS:
ConSentry will directly distribute products only to authorized partners. The program is divided into three tiers that all offer 15 percent margins on product. ConSentry will limit the number of partners to three Premier VARs per region, and five Alliance VARs per region, with no limit for Associate partners.
COMPANY:
Enterasys Secure Networks
\
Andover, Mass.
\
(978) 684-1000
\
\
KEY PRODUCT:
The Enterasys NAC solution performs authentication,
assessment and assisted remediation of end systems for proactive prevention of security threats. Enterasys NAC is deployed as a distributed in-line appliance for specific network segments or as a centralized resource for the entire network.
\
\
CHANNEL POINTS:
The Enterasys Networks Secure Advantage Partner Program is designed to drive more opportunities to partners that are best qualified to meet expectations. Other elements of the program include additional rebates or financial incentives that reward partners for bringing in new business and selling systems.
COMPANY:
Extreme Networks
\
Santa Clara, Calif.
\
\
(408) 579-2800
\
\
KEY PRODUCT:
ExtremeXOS version 11.6 features enhancements for securing networks using NAC technologies. ExtremeXOS now strengthens policy enforcement to help keep the network free from attacks through switch-based enforcement that allows network administrators to securely deploy NAC using
or 802.1x.
\
\
CHANNEL POINTS:
Extreme backs its partners with a three-tier partner program that accommodates solution providers of any size and provides training and
opportunities.
COMPANY:
Hewlett-Packard
\
Palo Alto, Calif.
\
\
(650) 857-1501
\
\
KEY PRODUCT:
ProCurve's PCM-Plus management
gives customers a single
to set NAC policies rather than jumping from one management application to another as would be the case with a NAC appliance sold by a third party.
\
\
CHANNEL POINTS:
HP is getting ready to capitalize on affordability requirements of midsize businesses, and a robust channel program helps to back partners looking to sell on value.
COMPANY:
Juniper Networks
\
Sunnyvale, Calif.
\
(888) 586-4737
\
\
KEY PRODUCT:
Juniper gives the network manager total control when building a NAC infrastructure. The product is dependent on both authentication and on detailed access control using its firewalls. Under Juniper's NAC control, every connection goes through a stateful packet-filtering firewall, can be encrypted and is explicitly tied to an access-control policy based on a user's identity.
\
\
CHANNEL POINTS:
Regardless of purchase volume, Juniper's J-Partner Reseller program rewards partners for the value they add to selling and supporting Juniper solutions. Specialization and certification options offer partners access to a broad portfolio of networking and security solutions.
COMPANY:
Microsoft
\
Redmond, Wash..
\
\
(800) 642-7676
\
\
KEY PRODUCT:
Microsoft relies on a DHCP server running Windows software to power the Network Access Protection (NAP) solution. NAP uses agents on the host to query other software such as antivirus, patch management, or a personal firewall for health and security status. Then the agent communicates that information to a policy server, which compares the host's current status to a predefined policy.
\
\
CHANNEL POINTS:
The Microsoft Partner Program is designed for all partners who develop and market solutions based on Microsoft platforms, provide consulting or technical services for Microsoft systems, or recommend Microsoft technology purchases to customers.
COMPANY:
StillSecure
\
Superior, Colo.
\
(303) 381-3800
\
\
KEY PRODUCT:
StillSecure's Safe Access 5.0 provides five enforcement options for quarantining endpoints: 802.1x enforcement, DHCP enforcement, endpoint-based enforcement, inline enforcement for VPN and RAS connections, and enforcement through Cisco's NAC architecture. Safe Access also provides three endpoint-testing options that include agentless, ActiveX-based and agent-based testing.
\
\
CHANNEL POINTS:
The StillSecure Cobia VAR Partner Program targets VARs, distributors and system integrators looking to expand their value proposition with their customers. The Cobia VAR Partner Program is aimed at partners looking to differentiate themselves in the competitive network infrastructure industry.
COMPANY:
Vernier Networks
\
Mountain View, Calif.
\
(650) 526-2600
\
\
KEY PRODUCT:
EdgeWall integrates a Continuous NAC Security Model for protection against both pre- and post-admission threats. The model includes four core elements: endpoint compliance, identity-based access control, realtime threat protection with IPS, and enterprisewide visibility and control.
\
\
CHANNEL POINTS:
Vantage Partner Program offers protection on every deal through the Vernier Deal Registration Program that offers margin protection for deals generated and registered by partners.