Fighting The Cloud's Biggest Threat: Top Ways To Stop DDoS

Distributed Denial-of-Service attacks, known as DDoS, are considered by many security experts to be the single largest threat to cloud computing. DDoS attacks are reported as comprising 5 percent of all Internet traffic.
The pervasiveness of DDoS is evidenced in recent outages of major Internet services such as Twitter, Facebook and, most recently, Dynamics DNS provider EditDNS.
DDoS attacks are carried out by botnets -- networks consisting of upward of thousands of machines all used to flood packets at targets. These attacks are orchestrated for any number of reasons. They may be launched to take down a business competitor's site, to make political statements or for financial gain. Attempting to understand the reasons for these types of attacks is futile. What is important is being aware that there are products and "best practices" that can be implemented in a network to stop them. A massive DDoS attack can leave a lot of destruction in its wake. It can cost a company revenue loss because of downtime (if that company does significant business online) or it can give a business a reputation for unreliability.
Here is a look at the CRN Test Center's picks for top strategies and products (in no particular order) for fighting DDoS.

RioRey's line of appliances is designed for one purpose -- to detect and stop DDoS attacks against public Web sites, from appliances for SMBs handling 1 GB of network bandwidth to large enterprises running 10 GB of network bandwidth. RioRey's products have Micro Behavioral Analysis technology embedded in them. This allows for the monitoring of suspicious protocols rather than analyzing individual packets, resulting in rapidly identifying and dropping attack traffic without affecting legitimate traffic.
These complex appliances perform the task of scanning, blocking and filtering out DDoS traffic. The devices take inbound traffic, examine and categorize it -- with no effect on network performance. There also is offered a detailed graphical user interface and reporting capabilities in the management console, known as rView.
Although the devices are complex and well-engineered, they can be deployed in a variety of scenarios with no change needed in the network infrastructure -- in other words, no complex integration requirements.
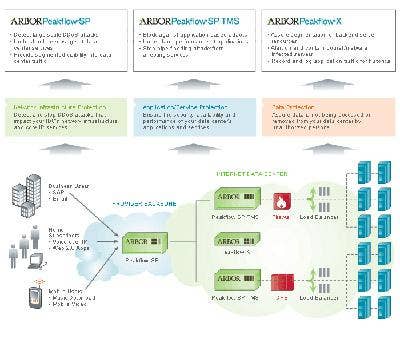
Mass.-based Arbor Networks provides secure service control solutions for global networks. Arbor Networks is considered one of the leading authorities on DDoS and other network-borne attacks.
Arbor employs flow-based and deep-packet inspection technologies to deliver protection against DDoS and other threats. Arbor's security product offerings include the Peakflow platform and the eSeries products.
More than 300 customers, including the majority of the world's service providers and many large enterprises, rely on Arbor's Peakflow SP platform for cost-effective, pervasive and intelligent visibility into network- and application-level traffic, as well as to gain the ability to quickly recognize and mitigate security threats.
Peakflow SP provides infrastructure security by proactively monitoring, detecting and mitigating networkwide anomalies. Peakflow SP is a strategic investment for service providers, allowing them to utilize the same solution for infrastructure visibility and security to deliver new, differentiated, revenue-generating managed services, such as MPLS VPN visibility and DDoS managed security services.
The Arbor eSeries platform is a high-performing deep-packet inspection system that detects and mitigates network-based attacks across an entire infrastructure.

Ireland-based Afilias provides Internet infrastructure solutions, including managed DNS. Afilias' strategy against DDoS attack is "Security though diversity."
This diversity includes several facets. One is geographical diversity: Afilias has 18 global locations. If one locale is knocked out by a DDoS attack, other nodes can still resolve queries. Diversity, in fact, underlies every layer of Afilias' solution. Afilias protects customers against DDoS with multiple bandwidth providers by using different types of hardware and operating systems, a mix of differing firewalls and routers and by using multiple types of DNS resolution software. This platform of diversity means that the entire infrastructure will not be compromised in case of an attack.
Afilias offers customers secondary or multiple secondary DNS servers. This way, if primary operations fail, the secondary provider can seamlessly resolve DNS queries.
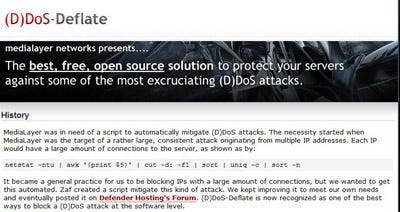
A free and effective open-source tool for protecting servers against DDoS is (D)DoS-Deflate. It is a Unix/Linux script designed by MediaLayer Networks that, in a nutshell, monitors and tracks IP addresses that are sending very large amounts of traffic. When the preset number of TCP connections allowed per node is exceeded, the script will block that IP address. Users all over the blogosphere are praising (D)Dos-Deflate, but keep in mind, it will only protect against small-scale attacks, so it's really for smaller organizations.
Those massive botnets that are responsible for carrying out DDoS attacks usually are composed of unsecured computers owned by innocent users. Malware on vulnerable machines can turn PCs and servers into "zombies" that take part in delivering DDoS attacks. It can't be overstated: It's crucial to keep all nodes and applications in a network patched and updated.

Knowing how your network should be performing is the best way to detect packet overloading from DDoS attacks. A baseline measurement of a network's performance is essential, as is a regular security audit. Audits should be routinely done and consist of checks for software vulnerabilities, checks for Trojans and rootkits, checking and flushing log files, including logged DNS queries, and port checks.
It's important that Web application developers and network security administrators work in tandem to keep Web applications from being vulnerable to DDoS and other Web threats. Check Web app security based on the vendor's recommendation for best practices. For example, Microsoft's MSDN has recommendations for securing IIS and ASP.Net applications such as filtering user input in .Net Web pages to check for HTML tags that may contain scripts, keeping files for Web applications located below the application's root folder, using least permissive security settings and making sure custom error messages do not contain information useful to hackers such as user names.