Six Products That Might Have Thwarted The Credit Card Data Heist
Our data is under attack. That was made readily apparent as details emerge following the indictment of several individuals in what is being called the biggest case of credit card data theft ever. How did they do it? It happened because of poor security defenses within the networks of the businesses that got hacked. These companies failed to implement strong defenses against data extraction --- data that contained millions of customer credit and debit card numbers. What's so appalling is that there are security products out there engineered to thwart the types of security breaches that were used in this crime. Here are six products we have looked at in the Test Center that these compromised networks could have used.
Guardium 7.0 Database And Security Management Appliance
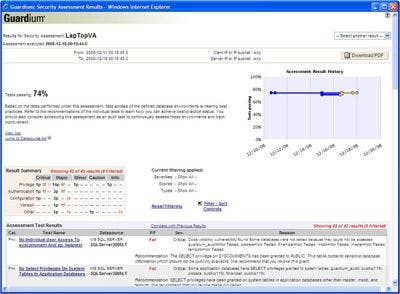
Guardium's Database Security and Management Appliance protects against inside and external threats. Guardium's solution prevents database compromise by offering real-time monitoring and alerting, including the monitoring of privileged user accounts such as those of database administrators. SQL injection attacks are stopped by anomaly detection.
In the event of a detected attack or data compromise, such as an SQL injection, Guardium 7.0 Database and Security Management Appliance will provide detailed monitoring of attacks, pinpointing what IP was used, what was targeted, which tables were accessed and which application was involved. Information on the users who may have been compromised is provided as well. There is also the ability to prevent unauthorized access to sensitive data and to mask sensitive information in tables. This solution features templates and high-level, yet easy-to-work-with, best practice reports for PCI, SOX, OMB and data privacy.
Application Security Inc. offers AppDetectivePro version 6.0, a network-based vulnerability assessment tool. This software scans the network looking for security threats, using application detection and penetration testing. It can perform audits of databases as well, with in-the-box policies tailored to the major compliance regulations.
There also are inherent penetration tests. These tests use a number of tactics to assess how vulnerable data may be. Some of the methods include Brute Force attempts to access a database, Denial of Service attacks as well as a penetration test again, made specifically for compliance regulations. Version 6 of AppDetectivePro comes with an additional feature called User Rights Review. This module takes a snapshot of user rights at the database level. It's a great way to dig deep into who has access to what data.

Intrusion protection and detection have become a crucial part of network security. Although many security products offer some watered-down IPS/IDS functionality as part of an all-in-one security solution, Sourcefire is a leading contender in the IPS space. The creator of SNORT -- the open-source network IPS/IDS system -- is also the founder of Sourcefire and the company's high level of knowledge of this technology is apparent in Sourcefire's 3D system. This IPS/IDS is a three-layered solution, with the components being IPS, Adaptive IPS and Enterprise Threat Management.
Adaptive IPS is Sourcefire's Realtime Network Awareness (RNA). It lets a user understand what they are defending. With RNA, a user can create a network map to gain real-time detailed information on the operating system, ports, services, protocols and a host of other things running on a network. Adaptive IPS also gives potential host vulnerabilities and can distinguish between physical and virtual machines.

Breach Security's WebDefend gives automated, tailored Web application security. It protects at the application layer as opposed to the network layer protection of traditional security. This type of protection guards against forceful browsing, SQL attacks and the type of data extraction that was done in the massive credit card heist.
WebDefend has flexible install options including out-of-line (in which the appliance acts as a transparent bridge) or in-line (by using a mirror port, TAP). Other features include: SSL decryption, Multiple Threat Detection Engines, Application Defect Detection HIPAA, PCI policies, a robust management interface, reporting and event logging.
Fortinet's latest security device can be deemed next-level Unified Threat Management. With additional features not often bundled in your usual UTM and with advanced hardware engineering, the FortiGate 620B represents a new generation of UTM devices. Core applications include firewall, Web content filtering, antimalware, intrusion protection, VPN (both IPSec and SSL) and two additional critical components: data leak prevention and granular application control.
What's attention-grabbing about this device, is that it fights threats that have broken through the security perimeter of the average network, including threats posed by mobile devices that often pass through traditional security defenses.
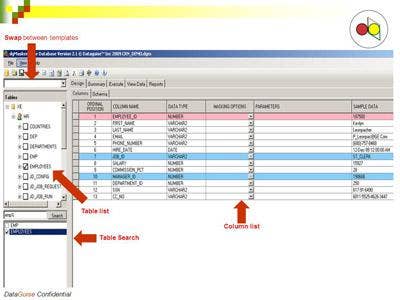
DataGuise's two-layer solution, dgDiscover and dgMasker, provides automated sensitive data discovery and data masking. Features include the ability to identify and protect data across an enterprise in SQL, Oracle, DB2 or MySQL databases. This data can reside in either structured or unstructured repositories.
The software solution scans data sources and identifies which ones contain sensitive data based on predefined and customizable security policies. Database and security administrators can choose from a variety of options to mask data, plus, data does not have to be extracted from the database in order to be masked.