Go Phish: Watch Out For These 10 Scams
We've come a long way since we first received letters in the mail from a Nigerian refugee prince desperately looking for safe haven to store his abundant stockpile of money. Or have we?
In actuality, while the medium has certainly changed throughout the decades, fraud has remained a constant. Although phishing has certainly been upstaged in the last few years by more sophisticated, and more insidious cyber attacks, phishers are alive and well, filling up our inboxes with unwanted spam.
In fact, spam has never been more pervasive than it is today -- a recent Gartner report indicates that $3.2 billion was lost to phishing in 2007. And while our collective Internet savvy has evolved, so have the creativity of the scams. What started as thinly veiled requests to send money in grammatically incorrect English have progressed to highly targeted, and multilayered spam campaigns that run the gamut from penny stocks schemes to multilayered attacks that employ password stealing Trojans and other malware.
Here are at least 10 ways that otherwise intelligent people will blindly (and willingly) surrender precious credit card and bank info to a perfect unseen stranger. These tried and true scams worked with surprising success in 2007 and experts say that we can expect to see some version thereof in upcoming year.

THE STORM NEVER CEASES
Like any good business, the Storm is diversifying. This time, it's going into the lucrative phishing industry. As if it hasn't done enough damage, security researchers now suspect that portions of the destructive botnet are being rented out to phishers. Lovely.
Of course the advantage is that phishers will have the ability to target even more victims in exponentially less time -- the fast flux botnet is elusive, highly complex and very resistant to takedown or detection. Indeed, a winning combination. "The people who are pulling the strings, they basically went out and did another social engineering run," said Paul Ferguson, network architect for Trend Micro. "It's a game of numbers. Two people out of 10, or two out of 100 for that matter, and it might make it worth their while."
In the multi-faceted attack, users will see an e-mail with a catchy subject line, enticing them to open a message that will typically contain just a few words and a link. Once clicked, the malicious URL will then lead users to a compromised Web site, complete with keystroke logger Trojans, viruses or other forms of malware.
"With malicious code, it doesn't matter who you bank with, they're going to get that data," said Dan Hubbard, vice president of security research for Websense.
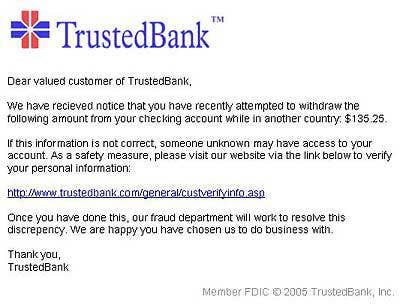
THERE'S SOMETHING WRONG WITH YOUR BANK ACCOUNT
An oldie but goodie. Bank fraud is still one of the most prolific kinds of attacks, targeting everything from major financial institutions like Bank of America and Wells Fargo, to local credit unions. "It hasn't slowed down at all," said Ivan Macalintal, research program manager at Trend Micro.
Phishers will send unsuspecting victims official looking e-mails that seem to come from their financial institutions, requesting the user to verify bank account or password information. Other times the message will request that a user access a call center in what is known as a vishing attack. Once the victim dials, they will be prompted to enter bank account numbers in order to "confirm" customer information.
Of course, that's ridiculous, experts say. Your bank knows this information already. And they don't need to call you to get it.
Yet despite this logic, the scam seems to work. And it's not just the big banks that are targeted -- a recent RSA report showed that criminals are increasingly executing attacks against small or local financial institutions with carefully crafted, socially engineered messages. And chances are the attack will also incorporate some personally identifying information -- just to give it that special touch of authenticity.

DRUGS ON THE CHEAP
With the outrageous price of health care, it's no small wonder that consumers who rely on prescription drugs are prime targets for exploitation. Equipped with this knowledge, scammers are constantly targeting users who are willing to sacrifice personal and financial information for the chance that they'll access affordable drugs from Canada.
"It's an effective and very robust operation, which makes it pretty significant for a blanketed attack," said Derek Manky, security research engineer at Fortinet.
Recent and very official looking pharmaceutical phishes, such as the infamous Xpress Pharmacy ring, have asked users to contact a technical support number or fill out authentic looking forms with personal information followed by promises to supply low-cost medications. But instead of pills, users generally wind up with nothing. If medications are actually delivered from the phish, users are in danger of ingesting placebos, out-of-date drugs or other foreign substances, which pose a major health risk in addition to any information that is lost.
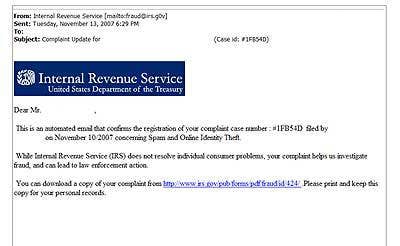
UNCLE SAM IS WATCHING
There are few agencies that U.S. citizens fear and loathe more than the IRS. And of course, this is reflected in the copious amounts of spam that solicits money on behalf of federal agency. Recipients will typically receive an official looking message, allegedly from the IRS, notifying them that there was a problem with their tax return. Or that they need bank account numbers and other financial information in order to make a deposit for the return.
Spammers will generally unleash phony messages around tax time, just when everyone is really nervous, experts say. "Here we have a brand, which is a government agency, that most people don't want to have any complications with," said Jon Orbeton, strategic product manager for Ironport. "They can wield so much power against you if you're not paying your taxes."
There is some good news, however. The actual IRS seems to take a surprisingly unusual interest in scammers emulating the federal agency. "They go after (spammers) as much and as quickly as possible," said Orbeton.

HAPPY HOLIDAYS
We see e-cards every Christmas with cute reindeer. On Halloween, it's dancing skeletons. Valentine's Day, someone is sure to say, "I Love You."
Whenever there's a media event or holiday, phishers are sure to follow. Recently, you might have seen phishing spam soliciting support for the Ron Paul presidential campaign. Last year, World Cup spam flooded inboxes around the world. And you can bet that a barrage of spam will follow in the wake of the upcoming Super Bowl and the 2008 presidential elections.
Any holiday or high profile news item is a target, simply because people are searching the Internet and receiving feeds about these events anyway, experts say. Naturally, event-driven spam remains popular because of its ability to capitalize on a large amount of traffic very quickly.
"A lot of spammers are quick on the uptake. They're very good at hitting the pulse of what people are reading and thinking about," said Dave Marcus, security and information manager at McAfee Avert Labs. "They're just very quick to pick up on high Google events.

A FORCE TO BE RECKONED WITH
Just because spammers know your birthdate, or the last time you bought something at The Gap, doesn't mean it's legitimate. In fact, because phishing works in conjunction with password stealing Trojans and other forms of malware, you can expect to see more attacks that target victims with detailed and personal information, experts say.
One example occurred last November, when Salesforce.com received national attention after a phisher tricked an employee into revealing a password in a well-researched and highly targeted attack affecting 30,000 customers. The password then gave the phisher access to a customer contact list full of customer data such as e-mail addresses and telephone numbers. It wasn't long after the attack that Salesforce customers began receiving bogus e-mails in the form of company invoices.
"It wasn't an exploit. It was just targeting an employee and phishing for a credential," said Derek Manky of Fortinet. "It's a longer staging process, but because of that, it is a lot more efficient."
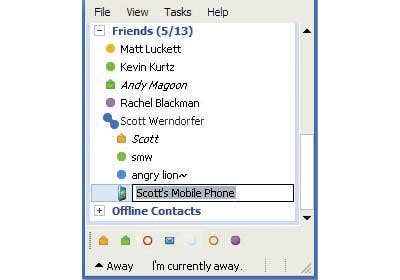
INSTANT MESSAGING
Last year, Yahoo users were the target of a phish propagating through IM contact lists. The attack entailed an IM message, along with a link, requesting individuals log in to their Yahoo account. Upon clicking, users were brought to a phony Yahoo page set up by the attacker in order to obtain login credentials and hijack accounts.
While a password stealing phish might seem like more of a nuisance than anything else, to spammers, it's the door that opens the gate to a playground of valuable information. The reason? More often than not, people will use a single password for multiple accounts, including those from their financial institutions and PayPal.
"E-mail is the crux of all our online activity," said Ramzan Zulfiker, senior principal researcher at Symantec Security Response. "If you own someone's e-mail account, you can often use that to figure out passwords for a whole host of other things' they've been doing."
"It takes a bit more to get that access, but it has a much broader application," he added.
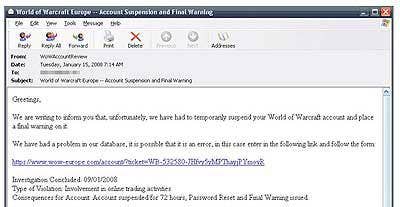
HA! GOT YOUR SWORD
Never underestimate the dedication and obsessive nature of online gamers. Cyber criminals don't. Like real life, the virtual world comes equipped with its own set of laws, commerce and banking. It stands to reason then that researchers have subsequently detected phishing lures that aim to hijack multiplayer online games such as Legends of Mare and Second Life.
Online attackers will enter virtual games and abscond with stolen prized items, (e.g. swords, dragons, crowns, etc...) that have taken players sometimes months to earn. Other times, they access a user's game and threaten to shut it down completely. Then attackers will contact the user with an online ransom note, stipulating a price should they want to get their items back.
"Some of these gamers are very passionate," said Jamz Yaneza, senior threat researcher at Trend Micro. "For some gamers, it takes days and weeks of real world time. Some of them do pay."

A MONSTER IN MY INBOX
Few people check their inboxes more than job seekers, which was why a phishing attack targeting Monster.com users became one of last year's most successful phishes.
The fraud successfully targeted hundreds of thousands of individuals who had fallen victim to the scheme after con artists stole legitimate user names and passwords from recruiters searching for job candidates on Monster. The attackers then used the pilfered logins to access Monster and grab sensitive information from resumes and applications, which they then used to create personal phishing e-mails to the individuals on the site.
"It was relatively targeted, appealing to an audience of job seekers. People who are actively looking for a job are receiving e-mail about any given position," said Mike Haro, senior security analyst for Sophos. "Users are not as unsuspecting."
The recipients that took the bait were treated to malware and malicious code secretly installed on their computers. Even still, security analysts say that the wealth of information that the attackers obtained was could also have been valuable in black-market information sales.

ROCK PHISHING
If it works, don't change it, right? Analysts have noticed a dramatic increase in the number of Rock Phishing-like phishes, made famous by the Rock Phish group notorious for executing this method of attack. These attacks use multiple proxy servers, which communicate with the victims by pushing content from "mother ships." Consequently, there is no direct interaction between the victims and the actual phishing site.
Unlike Storm Phishing attacks, these phishes are not based on fast-flux networks and don't require large botnets of proxies. However a single proxy server can wreak all kinds of havoc, directing victims to attacks against multiple institutions. A recent RSA fraud report stated that researchers had traced one proxy server which was used to initiate phishing attacks against six different U.S. financial institutions.
"With multiple proxies, (the attack is) essentially masking users from the mother ship," said Marc Gaffan, director of product marketing, identity and access assurance group for RSA. "That's really state of the art today."