15 New Security Products You'll See At RSA
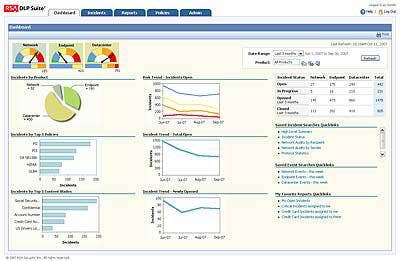
RSA DATA LOSS PREVENTION SUITE
As one of the industry's most comprehensive data loss prevention solutions, the RSA Data Loss Prevention (DLP) Suite is designed to provide customers with a robust database of policies to secure data for both regulatory (PCI, privacy laws) and non-regulatory (intellectual property, business strategy/operations data) security drivers. The suite offers a unified, seamless data policy orchestration, which allows customers to discover and monitor sensitive data and apply the appropriate enforcement mechanisms across the enterprise IT infrastructure.
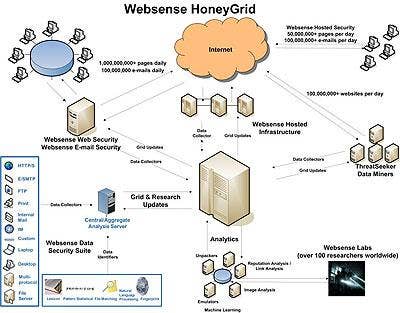
WEBSENSE THREATSEEKER NETWORK SECURITY HONEYGRID
Websense doesn't need supervision to have extensive visibility into the state of Internet content. Made to address the "Webification" of the corporate desktop, the new Websense ThreatSeeker Network features the world's first "Internet HoneyGrid," which combines both honeypots and advanced grid computing systems to parse through more than one billion pieces of content daily to detect security threats. The new system applies more than 50 million real-time data collecting systems across the globe in order to monitor and classify Web, messaging and data content. The Threatseeker Network's unique intelligence allows Websense security products to adapt to the rapidly evolving Internet threats at speeds unmatched by more traditional security solutions.

MCAFEE VULNERABILITY MANAGER 6.5
McAfee has hit a milestone in scanning. Addressing the growing need for businesses to pass IT security and compliance audits, Vulnerability Manager 6.5 has expanded scanning functionality. The Vulnerability Manager 6.5, now generally available, extends the capabilities of agentless scanning by adding policy compliance checks for both Windows and Unix systems. This release automates and simplifies inefficient processes while accurately detecting and prioritizing vulnerabilities and policy violations across all types of networked systems. The Manager's agentless policy compliance auditing functions enable companies to meet stringent compliance requirements such as PCI DSS, FISMA and GLBA.

FORTINET FORTIGATE 310B SECURITY APPLIANCE
Fortinet is raising the bar on its core competency UTM with its new FortiGate 310B Security Appliance, designed for the mid-enterprise segment. Specifically, the increased FW/VPN throughput and high port-density on the FortiGate appliance relieves small- and medium-sized enterprises of constraints that have traditionally prevented internal network security segmentation. Additional benefits include highest-in-class port density of 10 gigabit Ethernet ports, AMC expansion slot that provides flexibility for additional wire-speed firewall ports or embedded storage, and advances to the FortiASIC content processor -- all of which result in significant improvements to intrusion prevention systems and antivirus performance.
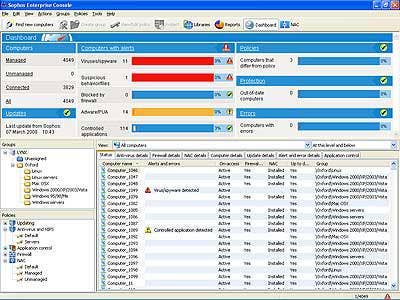
SOPHOS ENDPOINT SECURITY AND CONTROL 8.0
No doubt, the recently released Sophos Endpoint Security and Control 8.0 offers businesses complete, preventive computer protection in one appliance. Executing on its 2007 acquisition of Endforce, Sophos has integrated anti-virus, anti-spyware, host intrusion prevention, application control, firewall and NAC to block a wide range of security threats. In addition, the version 8.0 ensures computers are running authorized, up-to-date software and adhering to company policies with cross-platform preventive security and control for desktops, laptops, file servers and mobile devices. It can also identify computers that fail to comply with corporate security policies, enabling enterprises to either configure automatic remediation to repair vulnerabilities before allowing network access, or simply blocking non-compliant computers.

WATCHGUARD SSL 500 AND SSL 1000
Providing solutions for an increasingly mobile workforce, the WatchGuard SSL 500 and SSL 1000 are the intelligent choice for businesses that want a cost-effective, easy-to-use, secure remote access. Both the SSL 500 and SSL 1000 offer hassle-free VPN capabilities that provide universal access to applications and network resources with no connectors, no modules, no client management issues and no extras to buy.

IRONPORT S-SERIES WEB REPUTATION FILTERS
It's no secret that the Web is increasingly becoming the medium of choice for cybercriminals to distribute malware. Addressing the evolving security threatscape, IronPort, a Cisco business unit, has recently added significant enhancements to its Web Reputation Filters, which now combine URL Outbreak Detection as well as Botsite Defense to provide an even stronger defense against existing Web-based threats. The new layers of malware defense are available on the IronPort S-Series family of Web security appliances and through IronPort's SenderBase Network.
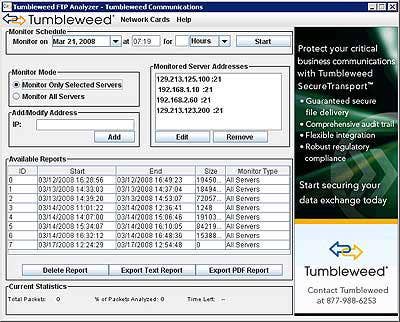
TUMBLEWEED FTP ANALYZER
FTP might the cheapest, simplest and most versatile method for sharing large data files over the Internet, but it introduces large scale challenges for enterprises by compromising security, management and compliance during transmission of business-critical data. Powered by Tumbleweed, the FTP Analyzer is an easy-to-use diagnostic tool that gives IT professionals the visibility into all FTP traffic on the network -- secure, unsecured and rogue. In addition, the Analyzer can audit FTP activity, both on selected servers or across a network, assess security risks by identifying secured and unsecured FTP transmissions, and report results in either an automatically generated PDF executive summary, or as raw data for further analysis.

HP C-SERIES MDS 9000 STORAGE MEDIA ENCRYPTION
These days, more and more businesses are seriously looking to encrypt their sensitive data to protect against data breaches and adhere to federal and auditory compliance regulations. Consequently, HP is taking data protection seriously with its C-Series MDS 9000 Storage Media Encryption, which secures data stored on tape drives and virtual tape libraries in a storage area network environment. The MDS 9000 SME allows HP customers to manage tape encryption and key management for legacy tape devices while ensuring protection of their existing product investments.

eEYE RETINA APPLIANCE 65
With sophisticated cyber-criminal activities on the rise, retinal scanners are hardly the wave of the future. eEye Digital Security released the Retina Appliance 651, a new network vulnerability assessment and tracking device, designed to detect and prevent exploits and data-loss attacks. The solution combines eEye's Retina Network Security Scanner, Iris Network Traffic Analyzer and Blink Professional Host-based Intrusion Prevention solution into a single appliance.
Altogether, the Retina Appliance 651 analyzes specific pieces of the operating system, applications, and policies to detect illegal traffic and fundamental flaws in an environment with advanced auditing techniques that non-intrusively determine vulnerabilities and data loss. The appliance provides multi-platform network discovery and scalable vulnerability assessment for a network environment of any size.
PGP MOBILE
Smartphone users can breathe a little easier with the release of the PGP Mobile, PGP Corporation's newest encryption application that allows enterprise users to easily protect data on smartphone devices. The PGP Mobile is hailed as the answer for enterprise businesses that face the risk of losing sensitive data as they increasingly rely on mobile workers to improve productivity and customer service. To meet these growing security needs, the PGP Mobile encrypts data automatically, which can then be shared securely with other mobile and desktop users.

AVG INTERNET SECURITY 8.0 NETWORK EDITION
This user-friendly solution allows companies to focus on business tasks while minimizing IT staff and resources. The AVG Internet Security 8.0 Network Edition offers businesses comprehensive security protection and provides network safety by scanning documents, files, Web pages and Web links before they are opened. Altogether, the easy-to-use scanner offers protection against viruses, spyware, adware and spam on workstations and file servers. It also includes a new intelligent real-time scanner and comprehensive Web shield, along with high-speed automatic updates and centralized installation and configuration.

ASTARO WEB GATEWAY
Malware will have less of a chance of entering, let alone staying on, corporate networks. The new Astaro Web Gateway provides integrated URL filtering, malware detection, instant messaging and peer-to-peer application control, along with bandwidth optimization to completely secure and control Web access. The Gateway, which will be available during the second quarter 2008, can be deployed as either a hardware or virtualized appliance and managed through a single browser-based GUI.
BIT9 GLOBAL SOFTWARE REGISTRY
Bit9 is launching the next generation of its Global Software Registry, designed to help determine the authenticity and trustworthiness of software. The registry has recently also been redesigned to become a productized tool that customers can access to cross-reference the applications on their systems with the "safe" list in the GSR, which includes new functionality for asset management and more efficient malware detection. The Global Software Registry has thus far accumulated more than 6 billion records, making it one of the most comprehensive inventory of software ever compiled.

BLUE COAT SYSTEMS WEBPULSE SERVICE
Security as a Service just got bigger after Blue Coat Systems announced that its WebPulse service, the real-time cloud computing security service extending Blue Coat WebFilter, has expanded to more than 100 million requests for URL categorization and Web site analysis per day. These requests come from Blue Coat WebFilter customers as well as OEM product users, mobile Internet users where the service provider utilizes Blue Coat products and K9 Web Protection, the company's free Web service for families and individuals. The large number of URL requests helps ensure that the Blue Coat WebFilter product contains and has categorized the latest relevant URLs and understands new sources of potential malicious threats.