2010: A Decade Of Malware

The first decade of 2010 has gone by in a blink, but the last 10 years have been a lifetime in the evolution of malware. Researchers at ScanSafe, now part of Cisco, found that what started with innocuous e-mail attacks and public viruses eventually gave way to botnets such as Storm, stealthy information-stealing Trojans and other sophisticated iFrame and SQL injection attacks. Going forward, cybercriminals appear to be leaning toward corporate and political espionage, with sophisticated malware designed to disrupt civil infrastructure and swipe intellectual property from competitors. Here is a brief time line of the past decade, with research provided by ScanSafe, of the threat landscape from 2001 to 2010.

In 2001, hackers started to see the benefits of using malware for commercial gain. Up until the millennia, hackers launched viruses and attacks for notoriety. But instead of ego, 2001 attackers used malware to generate money. The May 2000 Loveletter worm was a harbinger of things to come, combining social engineering (love letter for you) with a password-stealing trojan designed to harvest ISP usernames and passwords. However, malware's intent was somewhat benign -- Loveletter worm was created to provide free Internet access to the worm's author.

In mid-September 2001, the Nimda worm began its rapid spread around the globe, pioneering malware's eventual migration to the Web. Nimda's proliferation was facilitated by multiple propagation methods, including an ability to modify any .htm, .html, or .asp pages found on infected systems. The worm also spread by exploiting several vulnerabilities in Microsoft IIS, which increased its ability to infect Web pages.

January 2003 ushered in the Sobig worm, a significant threat that security experts at ScanSafe say was not fully appreciated until Sobig.E and Sobig.F appeared in the summer of that same year. Computers infected with the Sobig worm were outfitted with a spam proxy, which enabled mass mailers to send large volumes of unwanted e-mail using the victims' computers as a conduit. Sobig even harvested the victims' own e-mail contacts, adding them to the spammers' mailing lists in order to propel the malicious spam propagation.

Financial gains from harvesting e-mail addresses became even more apparent during the subsequent e-mail worm wars in early 2004, subsequently heightening tensions and escalating all-out territory wars between malware authors. 2004 began with MyDoom and the Bagle worm. Then an interloper (Netsky) quickly was introduced into the mix and began encroaching on other worms' turf. The authors of Bagle then began coding variants that, in addition to dropping their own malware, gave the worm the ability to remove Netsky. In turn, the Netsky author began neutering the MyDoom/Bagle infections with variants of the worm, while adding his own malicious code on the system. This prompted a response from the Bagle authors. Hidden in Bagle.K's code was the message, "Hey Netsky, f*ck off you b*tch, don't ruin our business, wanna start a war?"

The worm wars eventually fizzled out. Named threats became fewer as attacks became more stealthy, overtly criminal and financially motivated. To bypass security technologies, clever attackers began incorporating a much higher degree of social engineering in their attacks. In January 2005, scammers exploited the previous month's tsunami in the Indian Ocean by targeting people's fear and curiosity through phony breaking news alerts. Links in the spam e-mail that appeared to direct users to headline news and videos actually pointed to malicious Web sites and video codecs that downloaded malware and turned victim computers into bots.

By 2006, the Storm botnet was formally under way, though not named as such until January 2007, after a bogus breaking news alert claimed, "230 dead as storm batters Europe." Coincidental to the alert, a very real storm in Europe did cause loss of life, thus earning the Trojan family (and its associated botnet) its new name, Storm. And true to its name, the botnet took the cyberworld by storm, wreaking havoc on users' computers from 2006 through 2008. The botnet was responsible for a barrage of malware and spam campaigns that pummeled users with Trojans, keyloggers and other malicious code, enabling the authors to take control of their computers, and subsequently incorporate them into the bot network.
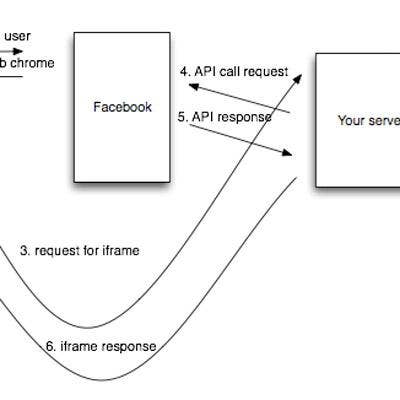
In 2007, publicity around MPack led to heightened adoption of exploit iFrame attacks in general, which subsequently laid the groundwork for managed Web attacks. Hackers also propelled the upsurge of free or low-cost SQL injection tools in the fall of 2007.

In 2008, Web-based attacks took hold when remote discovery tools such as Goolag further cemented cloud-based malware delivery via the Web. These attacks quickly proved profitable and shifted the attack of choice from spam and phishing to stolen FTP credentials and intellectual/financial property theft. Cloud-based distribution of malware also increased the sophistication of malware-creation kits, which allowed cybercriminals to double the volume of malware with exponential year-over-year increases, and as such, rake in the profits.
Security experts say that the 2009 Gumblar attacks were the culmination of a decade's evolution of criminal/profit-motivated malware. Gumblar is notorious due to the fact that it creates two sets of botnets: client-side traditional backdoors and a second, never-before-seen botnet compromised of thousands of backdoored websites. Among Gumblar's many talents is its ability to force a redirected revenue stream for the Gumblar creators, which provides instant monetization, as well as long-term potential profits, via its ability to intercept, tamper with and steal Internet and network communications. Gumblar also incorporates the ultimate in social engineering techniques -- infusing legitimate, reputable Web sites with malicious code and turning them against their visitors.

Going forward, security researchers can only speculate on what lies ahead. The poorly coded and fairly innocuous Loveletter rung in a decade that ended with the highly sophisticated, multipronged Gumblar. Looking ahead, security experts have speculated that there will certainly be more splintered and targeted attacks designed for industrial and political espionage, as well as more attacks targeting social networking sites, cloud servers and mobile platforms. But one can only wonder what the next 10 years may bring.