25 More Head-Turning Security Products To See At RSA Conference 2011

Tighten It Up, Again
Everyone knows that security isn't a sprint, it's a marathon. And at RSA Conference 2011 there were dozens of security vendors offering hot new security solution designed to encrypt, tokenize, lock down, tighten up and simply secure data, the network and even the cloud.
We've already shown you 25 hot new security products to see at RSA Conference 2011. But that wasn't enough. Here, we present 25 more security solutions that made a splash and caught our attention at the nation's biggest information security show.

Symantec Endpoint Protection 12
Symantec launched the latest version of its Endpoint Protection offering at RSA Conference 2011 this week. Symantec Endpoint Protection 12 targets a host of enterprise endpoint security needs, including malware protection, personal firewall, intrusion prevention, device control, application control and access control.
But Version 12 adds new features including Insight, which offers context- and reputation-based proactive protection against new threats using community-based security ratings derived from more than 175 million endpoints. Insight puts files in context using their age, frequency, location and more to expose threats that may have gone unnoticed. Endpoint Protection 12 also adds SONAR, a behavioral reputation-based engine that monitors and processes threats as they execute and monitors 400 different application behaviors.
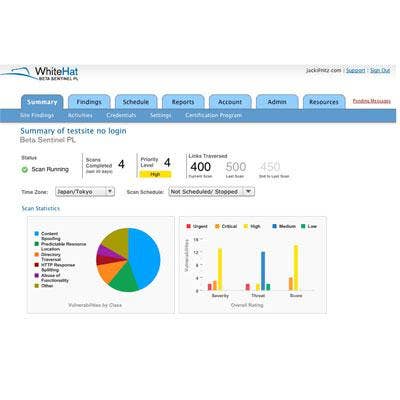
WhiteHat Sentinel PL
WhiteHat launched Sentinel PL at RSA Conference 2011, which leverages WhiteHat's expertise in testing and verifying vulnerabilities in production Web sites and adds capabilities specifically designed to find vulnerabilities throughout the pre-production phases of Web site development. Vulnerabilities identified in the development stage can be remediated by developers at a much lower cost than after the site goes live. WhiteHat Sentinel PL features fast assements, accurate results, seamless SDLC integration and pre-production-focused assessment.
CA Advanced Authentication Cloud Service
CA Technologies launched new capabilities to CA Advanced Authentication Cloud Service (formerly known as Arcot A-OK for Enterprise) and to the CA Arcot WebFort and CA Arcot RiskFort on-premise products. New features include a mobile authentication application to generate one-time-passwords, tagless device identification and new levels of integration with CA SiteMinder that improve Web application and information security. CA Advanced Authentication Cloud Service is a highly scalable, multi-tenant and configurable software-as-a-service application that provides advanced authentication capabilities to organizations in a range of industries including financial services, technology, real estate, pharmaceutical and more. The technology driving this cloud security service currently verifies 150 million identities and helps prevent fraud for about one million online credit and debit transactions each day.
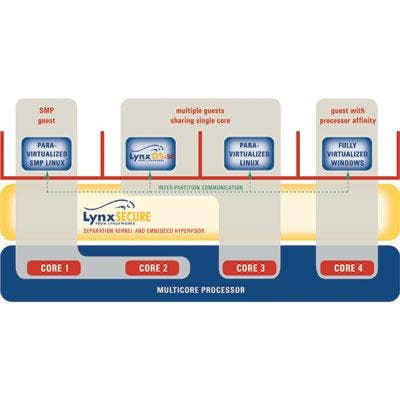
LynuxWorks LynxSecure 5.0
At RSA Conference 2011, LynuxWorks announced that its LynuxWorks LynxSecure virtualization platform allows multiple guest operating systems and applications to run independently on a single device. According to the company LynxSecure can run on a standard laptop with secure Internet access, servers or embedded devices.
IT centers routinely use software virtualization on servers to gain a long list of benefits including equipment consolidation, ease of management, and the support of legacy applications. However, performance limitations of desktop systems have made secure virtualization on clients impractical. LynxSecure 5.0 takes advantage of both the performance and the new features of the 2nd generation Intel Core processors to bring a new level of security to client systems.

SonicWall SuperMassive E10000 Series
SonicWall at RSA launched the SuperMassive E10000 Series Next-Generation Firewall Platform designed for large networks to deliver scalability, reliability and deep security at multi-gigabit speeds. Built to meet the needs of enterprise, government, university and service provider deployments, SonicWall's SuperMassive E10000 Series is designed for securing enterprise networks, data centers and server farms. Combining its massive multi-core architecture and SonicWall's Reassembly-Free Deep Packet Inspection (RFDPI) technology, it delivers application control, intrusion prevention, malware protection and SSL inspection at multi-gigabit speeds.

APCON IntellaFlex
APCON at RSA launched an entry-level aggregation and filtering switch that expands its family of IntellaFlex packet aggregation switches. The latest release in the IntellaFlex family offers 12 1G and two 10G ports, for a total of 14 aggregatable ports. The entry-level switch is designed for applications requiring low port densities distributed across multiple locations.
The new entry-level switch, which pairs a specially designed single-slot chassis with a blade offering an integrated controller, extends the scalability of the IntellaFlex family from 14 ports up to 288 ports in a single chassis. It also provides a reduced-cost solution for data center managers who need to monitor a low number of both 1G and 10G links with a fixed inventory of 1G tools.

Fidelis/CloudShield Application And Content Inspection
Fidelis Security Systems and CloudShield Technologies partnered up at RSA to offer a deep application and content inspection network security solution. The combination of CloudShield's Deep Packet Inspection platform and Fidelis' Deep Session Inspection technology gives enterprises, government agencies and Internet service providers defense against advanced threats and helps prevent data breaches with real-time network analysis, visibility and control.
The Fidelis-CloudShield solution is deployed at the network perimeter or at boundary points between zones of control or different levels of trust in the core of the network. The solution assists network security professionals to visualize, analyze and contain advanced persistent threats and detect or prevent the unauthorized transfer of sensitive or classified information. Leveraging the strengths of each technology, the solution is able to scale up to tens of Gigabits of throughput in a single chassis.
Bit9 Global Software Registry (GSR)
Bit9 Inc. at RSA unveiled the Bit9 Global Software Registry (GSR). The GSR is billed as the first open, cloud-based reputation platform available to assess the trustworthiness of software. The Bit9 Global Software Registry (GSR) is now accessible via an open application programming interface (API) allowing the global cyber security community to easily integrate their solutions with the Bit9 GSR Platform. The company said the Bit9 Global Software Registry is the world's largest and most complete authority on software, providing reputation ratings to help users identify, categorize, authenticate and trust software. The GSR, with its metadata for over 8 billion file records, delivers the threat and trust information needed to filter and stop the next generation of advanced threats.

Endace Application Dock
At RSA Conference 2011, Endace launched the Endace Application Dock, which allows third-party, custom and open-source monitoring and network security applications to run on Endace's 10 gigabit packet capture platform. Endace Application Dock gives organizations the first true multi-application hosting environment for network security and monitoring applications where a 100 percent accurate stream of captured traffic can be shared between a number of different applications running locally on an Endace System. A number of analytics, monitoring, security, forensic and measurement tools have already been approved to run in Endace Application Dock, with more applications to be added during 2011.

Lieberman Software Enterprise Random Password Manager
At RSA Conference 2011, Lieberman Software showcased its Enterprise Random Password Manager (ERPM), which is now integrated with SIEM applications from ArcSight, RSA and Q1 Labs. Previously, SIEM applications could show IT professionals when and where critical events occurred. However, when it came to the actions taken by highly privileged users, SIEM software could never show precisely who was responsible. Now, with Lieberman Software's recent integrations, users can see the added dimension of knowing specifically who took actions through use of privileged accounts, and any corresponding security event ramifications.

MBX Systems SYXMO Remote Monitoring
MBX Systems introduced SYZMO (System Zero Fault Monitoring), a 24x7x365 remote monitoring solution that continually reports on the operating health of MBX-manufactured server appliances to help prevent downtime for deployed software applications. Launched at RSA, SYZMO is customized to operate with each customer application and installed on MBX hardware. It continuously feeds appliance operational data to the MBX data center for detection of anomalies that indicate a risk of component or system failure. Significant changes in CPUs, power, system temperature or other factors trigger automatic alerts, allowing swift intervention to avoid service interruptions. Customers can monitor alerts themselves through a Web portal, engage MBX to advise them when problems occur, or contract with MBX to handle problem resolution with the end user.

Veracode Cross-Site Scripting Detection Service
Veracode at RSA Conference 2011 showcased a pair of new services designed to help the channel boost customers' application security.
First, the company highlighted its Free Cross-Site Scripting (XSS) Detection Service, which enables global developers and security professionals to quickly and easily identify dangerous and costly XSS vulnerabilities, while offering remediation recommendations to produce higher security Web applications.
Veracode also showcased a comprehensive service for independent mobile application security verification that protects enterprises from mobile app risks. Veracode currently provides verification for RIM's BlackBerry operating system (OS) and Windows Mobile. Support for Android OS will be available this quarter with Apple iOS support in the second quarter, Veracode said.
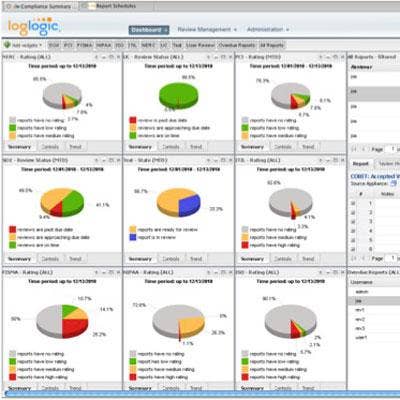
LogLogic Compliance Manager 2.0
LogLogic users RSA Conference 2011 to launch Compliance Manager 2.0, which provides users with an executive view into an enterprise's compliance posture and drastically reduces time and costs required to meet compliance regulations. LogLogic Compliance Manager 2.0 also improves audit speed and accuracy as well as the overall transparency of compliance activities.
New features in LogLogic Compliance Manager 2.0 include custom interactive dashboards and improved usability; support for customizable workflows to ensure reports are properly reviewed; support for multiple compliance regulations including PCI 2.0, SOX/COBIT, HIPPA, ITIL, FISMA, ISO, NERC or user-defined; software only distribution with no appliance needed; support in both Windows and Linux distributions; and Active Directory support for remote authentication of user accounts.

Net Optics Phantom Virtual Tap
Net Optics showcased its newest product, the Phantom Virtual Tap, at RSA Conference 2011. This release delivers dramatically superior network visibility and performance to Virtualized Data Centers. The Phantom Virtual tap is hypervisor-specific and is among the first solution to address both physical and virtual tools. This enables total visibility of inter-VM traffic for unrivaled security, compliance and manageability.
The solution is highly scalable and helps enterprises overcome the challenges of virtual network security, compliance and performance with cost-effectiveness and flexibility, the company said.
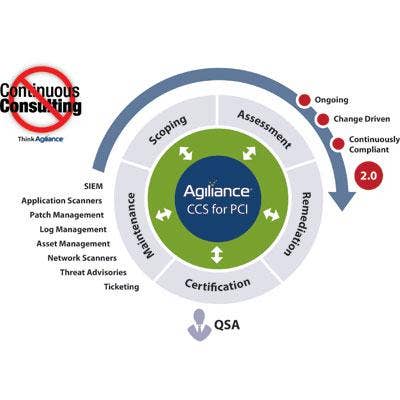
Agiliance Continuous Compliance Service For PCI
Agiliance launched the Agiliance Continuous Compliance Service (CCS) for PCI/PA DSS 2.0/1.2.1 at RSA. Agiliance bills the CCS as the only software solution on the market that provides a complete set of content, tools and reports that an organization requires for all five stages of the PCI compliance life cycle: scoping, assessment, remediation, certification and maintenance. With Agiliance CCS for PCI, organizations can complete PCI certifications over 60 percent faster than traditional means -- at half the cost. In addition to fast and easy certification, CCS for PCI ensures consistent and ongoing compliance as well as real time monitoring of PCI compliance status.
Ixia IxLoad Attack
Ixia at RSA branched out from the testing of just converged IP networks and devices and showed off its new test suite that validates the security of a wide range of devices including firewalls, VPN gateways, intrusion detection and prevention systems, and anti-virus and anti-spam solutions. Ixia's IxLoad-Attack security solutions are fully integrated with its test platforms, performing attacks in conjunction with full line-rate multiplay traffic -- exposing vulnerabilities that are only visible under stress.
Network equipment manufacturers can simultaneously validate the security and performance of their devices. Enterprises can ensure their network security on a continuous basis. Service providers can offer complete outsourced security services to enterprises of all sizes. IxLoad-Attack has a database of over 6,000 attacks and recreates malicious traffic that exploits published vulnerabilities, and generates Internet-scale distributed denial of service (DDoS) attacks in a controlled environment.
Alert Logic Threat Manager, ActiveWatch IPv6 Support
Now that IANA has already assigned all of the available IPv4 address space to the five regional NICs, the time will come where organizations will be unable to get additional IPv4 space and will be forced to accelerate deployment of IPv6 networks. According to Alert Logic, IPv6 represents a significant operational risk particularly in that few have or are able to tackle the security challenges presented with these new networks. Alert Logic at RSA revealed that its Threat Manager and ActiveWatch products now support IPv6, to help service providers and customers build security into their IPv6 plans upfront.
Lumension AppScanner
At RSA Conference 2011, Lumension showed off AppScanner, at tool to inform IT administrators of what endpoints have the most known applications. The tool provides scanning of all executable files across the endpoint network to identify known and unknown files.
Axway SecureTransport 5
Axway highlighted SecureTransport 5 at RSA, which the company said provides visibility into information flows both within and outside of the organization, while ensuring compliance with global mandates. Version 5 adds a new large enterprise clustering feature that extends SecureTransport's standard clustering capabilities, integrates into an external database and scales up to 20 nodes to handle a virtually unlimited number of concurrent connections. Large enterprise clustering also adds policy-based management of server-initiated and server-side tasks, giving administrators finer-grained controls.

IBM Tivoli Endpoint Manager
IBM's showed off its Tivoli Endpoint Manager, a new endpoint management offering that integrates the assets acquired by BigFix into the IBM portfolio. The new software extends IBM's capabilities to manage the security and compliance of servers, desktops, roaming laptops, and point-of-sale devices, such as ATMs. IBM Tivoli Endpoint Managers combines endpoint and security management into a single solution and enables organizations to see and manage physical and virtual endpoints. Now, clients can better secure and manage their IT assets and gain visibility, control and automation into their most time-intensive IT tasks.
SRA One Vault Messenger
SRA International Inc. at RSA Conference 2011 launched SRA One Vault Manager, an SMS (aka text message) encryption service for BlackBerry smarpthones. One Vault Messenger joins SRA's One Vault suite hardware-anchored voice security products for off-the-shelf BlackBerrys.
One Vault Messenger is designed for executives, first responders and government agencies that currently text in the open. The company said it defends from unwanted surveillance and cyber hacking. When used in conjunction with SRA One Vault Voice, which encrypts voice communication, and RIM's built-in e-mail encryption, One Vault Messenger completes the BlackBerry encryption puzzle.
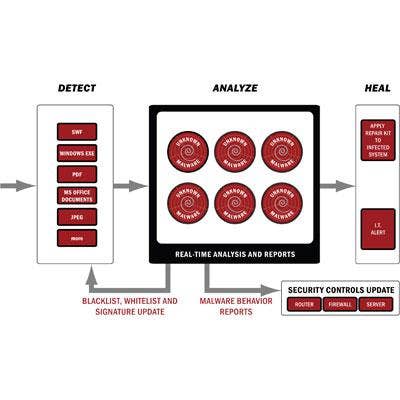
ValidEdge Network Malware Security
ValidEdge at RSA Conference unveiled its new Network Malware Security (NMS) system. The ValidEdge NMS is a combined hardware and software solution that monitors critical networks for any suspect code intrusion. Once suspicious code is detected, the system performs an instant analysis and issues alerts for IT personnel to fix security vulnerabilities and repair infected systems.
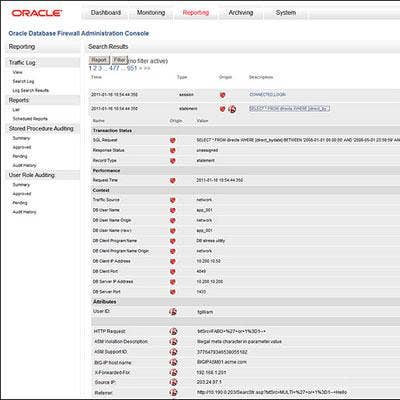
F5 Networks BIG-IP/Oracle Database Firewall
F5 Networks Inc. at RSA Conference announced integration between the F5 BIG-IP Application Security Manager (ASM) product and the Oracle Database Firewall. Building on F5's ability to help simplify database administration and accelerate database replication for Oracle customers, the integration provides improved SQL injection protection for F5 customers and correlated reporting for richer forensic information on SQL injection attacks for Oracle customers.

Black Box Intelli-Pass Biometric Access Control For Cabinets
Black Box Corp. demonstrated its Intelli-Pass Biometric Access Control for Cabinets at RSA Conference 2011. The Biometric Access Control for Cabinets is a complete software-controlled security system that features a fingerprint sensor on the front of the cabinet, allowing access to both the front and rear doors. A key competitive differentiator for the product is its ability to detect "life in the finger." The Intelli-Pass system detects blood flow, eliminating methods for spoofing fingerprints such as making photocopies or transferring fingerprint imprints to gloves. Aimed at military, government, education, financial and health care companies, the device features usage of electric locks, internal batter backup and LED lights.
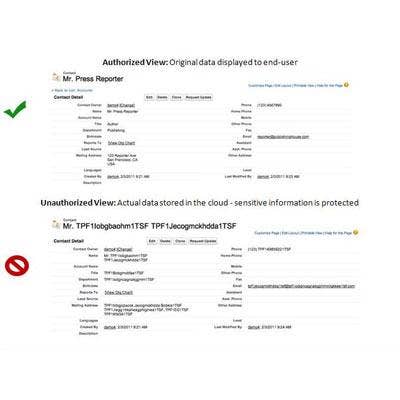
CipherCloud
CipherCloud, which came out of stealth mode the week before RSA Conference 2011, showed off its cloud data protection solution that protects enterprise data in the cloud with full visibility and control. Using patent-pending format-and-function-preserving encryption and tokenization that do not impact application functionality or third-party integration, CipherCloud completely eliminates data residency, privacy, security and compliance concerns associated with cloud applications, and accelerates cloud adoption in the enterprise.