Mobile Device Security: Inside Mobile Malware Threats

Malware Threats And Mobile Devices
From Google Android devices to the Apple iPhone, there is no shortage of mobile devices making their way into the enterprise. So far, mobile malware has remained a nascent threat next to the flood of Trojans, rootkits and viruses targeting PCs. But that doesn’t mean the iPhone in your pocket isn’t being targeted, or that enterprises don’t need to factor mobile threats in to their security assessments. On the contrary, the growing consumerization of IT means businesses are under increasing pressure to meet the demands of managing and securing mobile devices.
So what do some of the latest malware threats to your smartphone look like? We have gathered some examples to paint an image of recent threats that have knocked on the digital doors of smartphone users around the world, as well as what businesses should consider when crafting policies to protect their employees and their data.

Show Me The Money
Cyber-criminals have a number of techniques for turning your infected money into their personal ATM. For example, by calling or sending an SMS message to a premium rate number, scammers can jack up a person’s phone bill. The attacker gets their payday by first setting and registering the premium number, then when the infected phone calls or sends a SMS message to the number, the device owner is billed at a higher than normal rate – and the attacker pockets the difference.

Show Me The Money...Continued
There is no shortage of spyware in the cyber-underground. On mobile devices, these malicious applications can allow someone to track and monitor the usage and location of the phone, giving attackers the power to record and export SMS messages, emails, call logs and GPS locations. These apps aren’t cheap. According to Symantec, some of these applications have been advertised for up to $400 on the black market.

Mobile Malware Market Share
By mid-August 2009, Kaspersky Lab had noted 106 mobile malware families and 514 variants of malicious programs targeting mobile devices. By the end of 2010, those numbers had grown to 153 families and more than 1,000 variants. To put it another way - in 2010, the company detected 65.12 percent more new malicious programs targeting mobile devices than in 2009, and the threats nearly doubled in number during a 17-month period.

Stealing Your Data
Just like on your PC, there are pieces of malware that are aimed at stealing user data. One better known example of this is Geinimi, which targets Android devices. Geinimi emerged in China in December 2010. The Trojan, which Lookout Mobile Security called the most sophisticated Android malware the company has seen to date, sends the data it steals to remote servers, and is the first Android malware to display botnet-like capabilities such as receiving commands from a remote server.

Banking Trojans Gone Mobile
In September, security researchers noted the appearance of Zitmo, a mobile version of the Zeus Trojan targeting Symbian and BlackBerry devices. The malware is designed to steal mobile transaction authentication numbers sent to banking customers’ phones in order to verify someone’s identity. In February, the malware was seen targeting customers of a bank in Poland.

Jail Broken Apple iPhones Targeted
A worm aimed at Apple iPhone users with jailbroken devices known to Kaspersky Lab as Net-Worm.IphoneOS.Ike.b was used by cybercriminals in 2010 to launch a targeted phishing attack against customers of a Dutch bank. When users attempted to visit the bank’s Website from an infected iPhone, they were redirected to a phishing site.
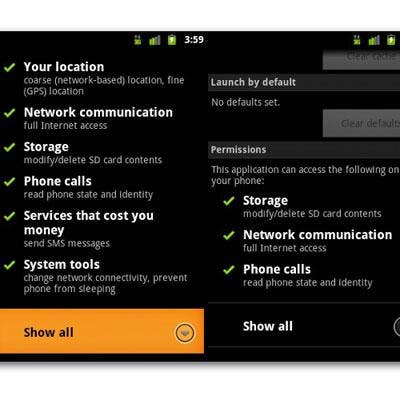
Fake Android Market Security tool
Not long after Google published its Android Market Security Tool – which removes malicious applications infected with the Droid Dream malware – a Trojanized version of the tool appeared in third-party Chinese application markets. "A suspicious user will immediately notice the difference between the fake and the real Android Market tool if they check the permissions required at installation," according to Vanja Svajcer, principal virus researcher at SophosLabs. "While the original tool only requires three permissions, the Trojanized version requires additional permissions for "Services that cost you money" as well as the device location."

Video Game Trojan
In 2010, a malware author created a Trojanized version of the Windows Mobile video game ’3D Anti-Terrorist action.’ The attacker then uploaded the malicious program to sites distributing free versions of the game. Once on a device, the malware makes phone calls to several premium numbers at expensive rates.
Mobile Device Security Tips
For businesses, deciding what devices to support and having clear, enforceable policies for those devices is key. That means understanding what your company’s goal is from a security management perspective. Best practices include having the ability to wipe a device remotely, as well as policies around encryption and passwords. Education for end users is also important. For example, security experts advise mobile users pay attention to the privacy permissions applications ask for on their Android phones, and have noted that jailbreaking iPhones can increase the potential threat level because it circumvents Apple’s security approach.