RSA 2012: 11 Security Products You May Have Missed

RSA 2012: Don't Blink
With the RSA Conference 2012 over, it's worth taking a second look at some of the product releases that may have been overlooked among the hundreds on display at the security show. The following technologies represent a smattering of products ranging from next-generation intrusion prevention systems and endpoint protection applications, to Web gateways and cloud security.
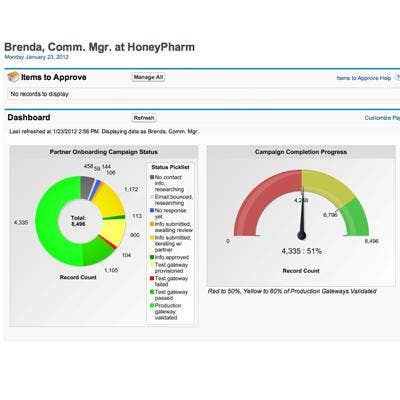
Axway Demos Community Management Gateway
Axway showcased its Community Management Gateway. The profile provisioning service centrally manages communities and partner profiles. The service enables on-boarding of community members and automated updating of partner profile and status information. Leveraging Salesforce.com's Force.com platform, the gateway automates information gathering for secure enrollment, on-boarding, migration, certificate management, software updates and member self-services. Subscriptions start at $36,000, plus a $5,000 setup fee.
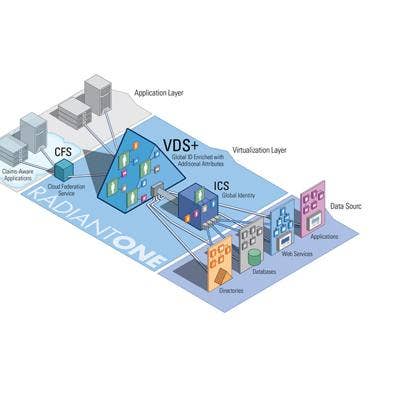
CA-Radiant Logic Releases Upgrade Of Federated Identity Service
CA-Radiant Logic introduced an upgrade of RadiantOne, a federated identity service for connecting users to Web services across multiple authentication protocols, identity sources and applications. Version 6.0 features identity mapping, aggregation, correlation and synchronization. Other features include the advanced virtual directory of VDS+, the Cloud Federation Service for connecting identities with the cloud and an identity correlation and synchronization engine. The on-premise service is based on identity virtualization, the Novato, Calif.-based company said. The system is scheduled for release in April.

Huawei Unveils Network Security Gateway
Huawei launched a network security gateway designed for cloud data centers. The Eudemon8000E-X provides up to 200 Gbps performance and IPv6 attack defense capabilities, the Chinese company said. The device also provides flexible policies to adapt to the changing virtualization needs of a dynamic cloud environment. Security is built into the system for malware detection. The Eudemon8000E-X has been available since the end of last month.

Kerio Adds IPv6 Support To UTM
Kerio Technologies has added IPv6 support to its unified threat management firewall. Kerio Control 7.3 is targeted at organizations preparing for the transition from IPv4 to IPv6. The UTM appliance enables customers to securely test IPv6 traffic over corporate networks. The San Jose, Calif.-based company says the Control upgrade becomes an IPv6 router with a "few clicks." The device currently acts as a stateful firewall for IPv6 traffic. Anti-virus, Web filtering, bandwidth management and an intrusion prevention system will be added later, the company said.

Kindsight Debuts Mobile Security
Kindsight introduced mobile security for networks and devices. The platform, aimed at mobile operators, combines network-based malware detection with a mobile device security app that scans for malicious software before it is installed. The new product is meant to be sold by operators as a value-added security service, the Mountain View, Calif.-based company said.

M86 Previews Upcoming Web Gateway
M86 Security previewed the next release of Secure Web Gateway. Version 10.2 will provide additional networking and third-party integration options, the Irvine, Calif.-based company said. The upgrade also includes hybrid cloud deployment as a standard feature, as support for Amazon Web Services Elastic Compute as an alternative cloud scanner platform. SWG v10.2 is scheduled to be available through channel partners and distributors in April.

Sourcefire Unveiled New IPS
Sourcefire introduced a new version of its intrusion prevention system. The latest version incorporates real-time contextual awareness into its inspection. The technology gathers information about network and host configurations, applications and operating systems, user identity and network behavior and traffic baselines. The hardware running the system provides IPS inspected throughput options ranging from 20 Gbps down to 5 Mb per second. Customers can upgrade to the latest IPS by adding a license to their software.

Systematic Demos Secure Flash Drive
Systematic Development Group demonstrated a LOK-IT secure flash drive with Becrypt's Trusted Client operating system. The combined technologies enable companies to provide employees with a way to connect to a corporate network and access data from a secure environment. Trusted Client is used to boot up a computer, which then launches the hardened, securely configured environment. LOK-IT is a FIPS 140-2 Level 3 secure drive with hardware authentication, Deerfield Beach, Fla.-based Systematic said.
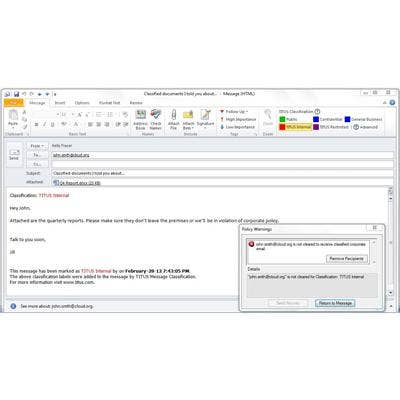
Titus Intros Cloud Data Security
Titus, a maker of information security and compliance products, unveiled Cloud Data Security. The new product enables the control of sensitive data flowing between an organization and a Web service through the use of policies driven by identifying and classifying e-mail and documents. The software ensures that the handling of data is in line with compliance requirements. The product also provides a well-documented audit trail, according to the Canadian company.

Trend Micro Releases Deep Discovery Upgrade
Trend Micro released a new version of its risk management platform, Deep Discovery. The new product is designed to battle advanced persistent threats, the Japanese company said. Improvements include an enhanced threat engine to better analyze and ID potential risks and a new dashboard that provides threat profiles and geo-locations of incoming risks. Deep Discovery also supports the leading security information and event management (SIEM) systems.
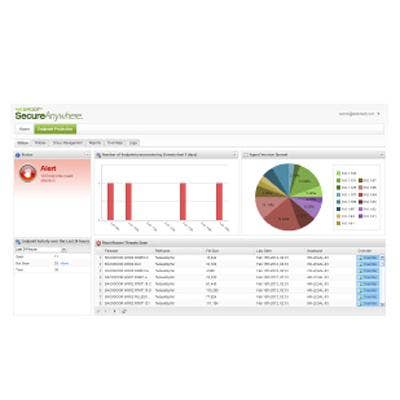
Webroot Launches Endpoint Security-As-A-Service
Webroot introduced endpoint security as a service. Called SecureAnywhere Business - Endpoint Protection, the cloud-based service is based on the company's anti-malware consumer product. The service provides malware detection, identity and privacy protection, firewall and system cleanup. Broomfield, Colo.-based Webroot includes a rollback feature for restoring a system to its state prior to an infection. IT administrators use a Web-based console to monitor security status, remediate infected machines, start scans and set Web and application usage policies.

