How To Tackle Thorny IT Security Issues

7 Security Slam-Dunks
Solution providers are constantly stemming the tide of security breaches. Securing company data can prove lucrative for those VARs that are viewed as trusted partners. The IT security field is being tested repeatedly by new hacks, so the challenge to keep up is great.
CRN's Channel Voices blog looks at security issues and offers how-to advice for implementing solutions that will help lock down customers' most important asset: their data. Here's a look at seven security tips.

Try A Private Cloud On For Size
Private clouds are thought of as more secure than the public cloud option, but that's true only when a best practices approach is followed. Upgrading or creating a security policy that is appropriate for most organizations focuses on five basic security components: Risk Assessment, Data Ownership, Data Classification, Auditing and Monitoring, and Incident Response.
To effectively develop a security policy to help defend your organization from hackers, as well as inadvertent access to confidential data, Von Williams, director of information security for Logicalis, provides five ways for organizations to increase the security of their private clouds.

Be Alert
Social engineering attack-driven threats have gone through the roof in direct response to the surge in the takeup of social networking sites and services. Don't let your IT business or your clients fall prey. For example, using informal communications tools -- like chat -- often creates the appearance of a closer relationship than actually exists.
Don’t be fooled into sharing information with a so-called friend. Cryptzone VP Grant Taylor offers tips on defeating social engineering attacks, and safeguarding your firm from harm.
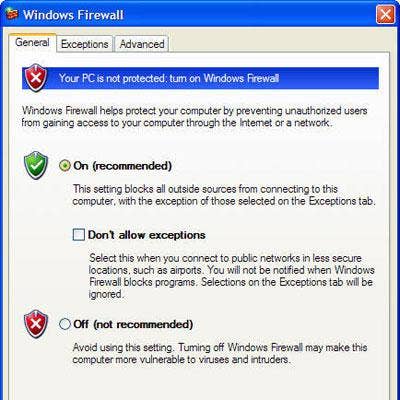
Don't Rely Solely On IPS And Firewalls
Intrusion Protection System (IPS) devices, firewalls and other security products are essential elements of a layered-defense strategy, but they are designed to solve security problems that are fundamentally different from dedicated DDoS detection and mitigation products. IPS devices and firewalls effectively address network integrity and confidentiality, but they fail to address a fundamental focal point of DDoS attacks -- network availability.
Distributed denial of service (DDoS) attacks can be devastating because the end-targeted system, as well as all systems maliciously used and controlled by the hacker, are affected. Bill Lipsin, Arbor Networks' VP of partners and alliances, offers advice on How To Prevent DDoS Attacks.

Create A BYOD Policy
Companies that let employees use their own devices for work benefit from a more engaged workforce. However, the advantages of BYOD policies are often tempered with security concerns and the added pressure on IT to manage and secure a mishmash of devices. Allan Thorvaldsen, CEO and co-founder of Panorama9, outlines ways in which to formulate an easy-to-follow Bring Your Own Device policy to help maintain the security of networks and data.

Use A Remote Monitoring And Management (RMM) Tool
It's tough to keep track of network security for every customer. PCs, tablets, switches, routers and firewalls all need to be constantly updated and monitored to guard against network threats. Solution providers that excel at keeping up with threats can set themselves apart from the competition. RMM tools are available to manage PCs, servers, etc., at multiple sites. Keeping a customer's data private and providing them with secure networks are paramount to success as a solution provider. Jeff Bowes, director of operations for NuWave Technology Partners, offers advice on locking up customers' businesses by building more secure, flexible networks.

Visibility Can Rescue The Network From Intrusion And Theft
Visibility can protect against intrusion and theft, as well as reveal other issues affecting network productivity and value. It also can minimize risk and enable productivity gains from IT applications and services. But, as applications become more diverse and the devices hosting them more pervasive, visibility solutions that look only at the network edge or see only random monitoring data are not robust or comprehensive enough. Net Optics President and CEO Bob Shaw explains how IT pros can sell security solutions and defend networks using fine-grained monitoring and visibility across both the virtual and physical networks.

Customers Must Understand Their Systems' Vulnerabilities
Although they can't do the job alone, antivirus and firewalls should be put into place on Day 1. Information that's saved to a machine rather than a server is lost, so strongly advise customers to set up a server and automate the backup procedure for all the PCs on a network. Senior editor Jennifer Bosavage talks with IT security experts, who offer tips to help customers secure their retail sites.

More From The Channel Voices Blog
CRN's Channel Voices:
How To Gain a Competitive Edge When Recruiting
How To Use Internal Procedures to Protect Your Company
How To Secure Private Clouds In Five Steps