Mac Attacks: Top 10 Bugs Targeting Apple

More Secure, Or Maybe Not
According to conventional wisdom, malware and similar types of exploits are reserved for the Windows community -- not for their slightly more hip cousins who, through the years, have remained committed to the Mac. While some people claim that Macs are more secure, others maintain that they merely present a lower profile, given that most businesses for a long time standardized almost exclusively on the PC -- except, of course, for a smattering of artsy folks who were allowed to use Macs. But all has not been quite so easy in Macland. Please join us for this brief tour examining Mac attacks through the years.
For a closer look at Apple's standing in the security community, see a preview of our exclusive report, "The Paradox Of Apple Security: Does Secrecy Make You Safer." The full article is available exclusively on the CRN Tech News app, available now in the Apple App Store.
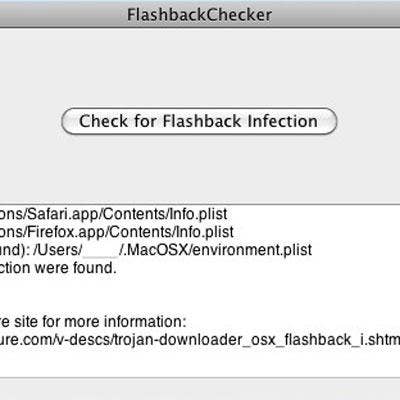
Flashback
Flashback was arguably the biggest threat to hit Macland. Hitting the headlines in April, the infection volume landed somewhere around 600,000 machines. And though the bug was not completely unheard of among PC users, the vast majority of victims were running OS X, according to security vendor Kaspersky Lab. Masquerading as a browser plug-in, the bug typically leveraged Java vulnerabilities to steal passwords and other sensitive information. Apple issued various patches over subsequent weeks that appear to have done the trick.

HellRTS.D
In 2010, this little ditty arrived on the scene in the form of proof-of-concept malware, and it's arguable as to whether HellRTS.D actually made it out into the wild. The bug, which actually targeted both Macs and PCs, could open a back door that would grant access to hackers who might be looking longingly at your data. It was also designed to replicate and rename itself for the added ability to slip through the cracks. But its effects would have been limited based on the fact that it required physical access to the targeted machine. Its threat was further limited by Apple, a short time after it was discovered, when the company built preventative features into Snow Leopard.
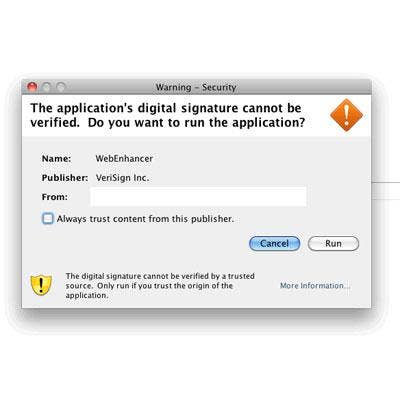
Crisis
People who name their bug Crisis have some high aspirations. And since they didn't want anybody to feel left out, they devised a multiplatform that invited both Mac and PC users to their party. The malware, which deployed over the summer, gets carried in by a Java archive file masquerading as components of Adobe Flash Player. At that point, a file called WebEnhancer determined whether it has hit Windows or Mac OS X, and then deploys the attack best suited to its host. For Mac users, that included config changes plus a back door and root kit.
Patient Zero
You'll need to turn back the clock more than a few laps in order to remember Patient Zero. In 2004, it was one of the first bugs for Mac OS X to gain any real degree of notoriety, mostly for being Apple-related at a time when such things simply did not happen. The malware authors used the Mac's hidden file extensions to camouflage their executable file, which was made to look like something else entirely -- usually an MP3. Once the user clicked the icon, the Trojan could commit all sorts of antisocial behavior, such as deleting files, spreading the infection within the machine, and sometimes invading the email software so it could go visit the host's friends. But the bug was presented as a sample of what could happen, and there's no indication that it ever made it into the wild.

Backdoor
This one is a variant of a previous bug known as LuckyCat. It arrived on the scene in April of this year as a Trojan that meets new victims leveraging a Java exploit through corrupted Word documents. In at least one case, the Trojan kept a low profile for nearly two months before being activated. But a number of variants already have been identified, leading to speculation that we have not yet heard the last of Backdoor. Potential victims, however, just might have seen the last of the data that the bug tends to steal.
Mac Guard
Mac Guard was about keeping your machine safe. For them. Not for you. The year was 2008, and Fake AV was posting a profit in the world of PCs, thank you very much. So malware authors -- usually an equal opportunity bunch -- decided to make the same kind of offer available to Mac users. Various virus alerts would appear, and users would be urged to part with credit card information as the first step in making it all go away. The scam used a slightly adjusted version of a similar scam aimed at Windows users, and therefore did not fool a whole lot of people. But after picking themselves up and dusting themselves off, cybercriminals came back with a much more convincing pitch, sold as Mac Defender.
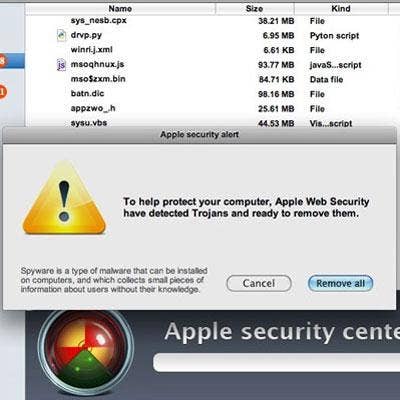
Mac Defender
Like a couple of its Fake AV predecessors, Mac Defender has a tendency to pop up when you least expect it, waving its virtual arms in a presumably critical warning about malware that has supposedly been found on your machine. Of course, it has a solution to your problem in the form of bogus antivirus software that actually lets loose a torrent of porn websites that automatically get loaded onto your computer. The number of victims was listed in the hundreds. The bug achieved brief notoriety in spring 2011, and was apparently spread by tricking people to open an image on a search engine. Mac Defender came across as a pretty convincing offer, according to several sources. Apple solved the problem through a software update.
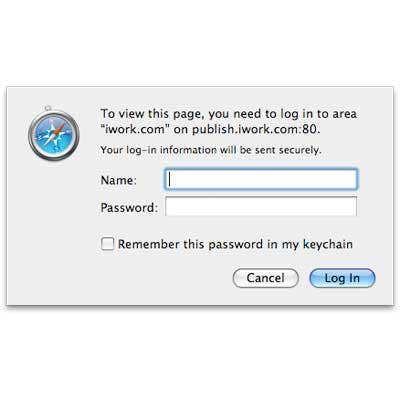
Mac Protector
Also during spring 2011, Defender variant Mac Protector arrived on the scene, popping up and telling users that their machines were heavily burdened with a whole slew of software nasties, and then offering to sell a cleanup tool that would put things back on the straight and narrow. All you needed to do was trust them with your credit card number and your troubles would be over. Wouldn't they? OK, probably not. But this was a Mac, and not a PC where ploys such as this one were pretty commonplace. Similar to Mac Defender, Mac Protector would ask for the root password, and included quite a bit of subterfuge to make itself look like a genuine, legitimate response to malware. Once installed it would conduct an imitated scan, and then request that the user register in order to clean up the purported mess. At that point, credit card information and similar details would be requested. Apple eventually released an OS X update to protect against the "protector."

OSX.Trojan.iServices
Howdja like some popular software on the cheap, and on the semi-down-low? Never mind what we might do behind the scenes. That was basically the value prop behind OSX.Trojan.iServices, which went live around the time of Macworld 2009, just as iWork '09 was formally introduced to the market. While the Trojan promised to deliver the Apple productivity suite for less money, it also installed a back door through which all kinds of malware could be introduced. A similar version was subsequently targeted at Adobe Photoshop. Neither exploit was all that successful in terms of the numbers of people who fell for the ploys, but somewhere north of 20,000 users were affected.
RSPlug.A
This Trojan arrived on the scene in 2007, offering to function as a QuickTime codec supporting the videos posted on specified porn sites. But the malware would launch a DNS attack that would send users to bogus mock-ups of eBay, PayPal and similar sites where loading in one's credit card information wouldn't be viewed as particularly fishy. But people who were at least reasonably on the ball usually had little trouble recognizing the attempt for what it was. A scam! Only a small handful of users actually got tagged with this one.

Honorable Mention: Find And Call
We didn't want malware authors to have to write something particularly sinister just to crack a top 10 list. (They care about these things, don't they?) So we're giving a shout-out to Find and Call, which presented itself as a phone book application -- and kinda was -- except that this one also carried a piece of malware that would upload contacts to its friends in the spam community who would then try to propagate the app in the apparent hope of building the most fantabulous text spam list, ever. This is believed to be the first time that Apple needed to deal with malware that slipped past the much-vaunted cyber-goalie in front of its App Store.