Review: Covertix's Remarkable 'Agentless' Security Locks Data Tight

Smarter Data Protection
How does it do that? A clever company based in Israel has developed a security solution that can actually apply security rules to files and data payloads after they've moved beyond the company's firewall.
Security vendor Covertix this week unveiled SmartCipher 3.0, the latest version of its agentless file protection software, which adds support for smartphones, integrates with Microsoft SharePoint, and gives end users the ability to assign security policies from their own desktop. Covertix was among CRN's 2012 Emerging Vendors, and emerge it has.
SmartCipher works with individual files or groups of documents, which can be selected based ordinary criteria. "We are a data-centric solution," said Michael Kasan, sales director. "I don't mind how you got my information; what I care about is what you can do with it. We don't protect your database or the contents of an email. We're a file solution." How does it work? The CRN Test Center investigates.
Policies
While most end-point security solutions monitor email, Web browsing and other end-user activities and attempt to prevent movement of sensitive or protected data through those channels, Covertix focuses on file contents. "Our product sits on the data itself," said Kasan, "and if you don't have privileges or if you got the file illegitimately, it won't be usable." SmartCipher also monitors movement of files within an organization by employees, visitors, contractors or other temporary workers.
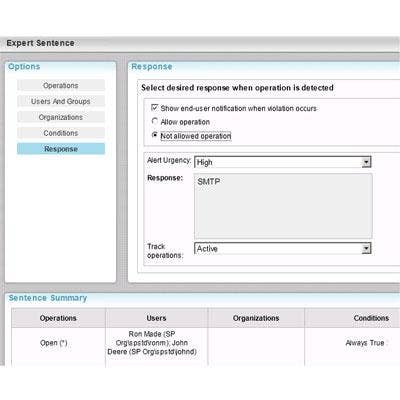
Through a browser-based admin console, files are assigned security levels according to extension, file size or property, location, specific content, people, groups, domain and other attributes, times or conditions. Custom responses (shown) can be tailored to fit the situation. There are no agents to install; security follows the file.
Rules
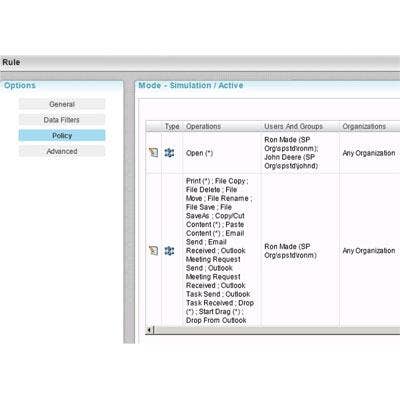
Living up to its name, SmartCipher also permits the creation of rules for operations permitted on data within protected files. For example, users might be granted the ability to view a list of names and addresses but prevented from copying, deleting or printing the list, copying, renaming or forwarding the file, or saving it with a new name. The software can even prevent printing or capturing the screen while a protected file is visible. Files also can be protected based on their network or domain of origin, device or MAC address on which they reside, and other factors. Rules also can apply if certain content is added to a file at any time during its lifetime. "Regardless of the location of the file, if I created a policy that [kicks in] if the words 'top secret' appear [in the file], that file is automatically protected," said Kasan.
User Alerts
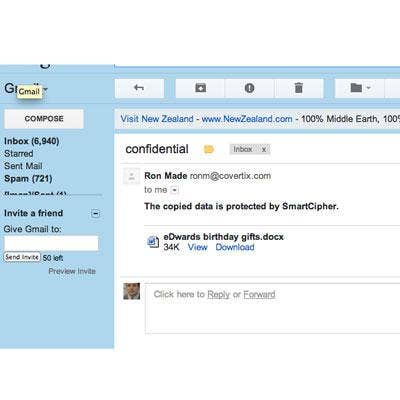
When a file that's protected by SmartCipher arrives in someone's inbox, the user is alerted to that fact but is otherwise unimpeded from opening the file and accessing its contents based on a rules set that it carries. According to Kasan, the security rules add little to the file's overall payload. "In active mode, it adds 16K[bytes]. But with today's file capacities, that's almost insignificant," he said. There's also a simulation mode, which lets IT departments determine whether the policies being considered are going to be adequate for the organization. In this mode, the security payload is even smaller.
No Paste
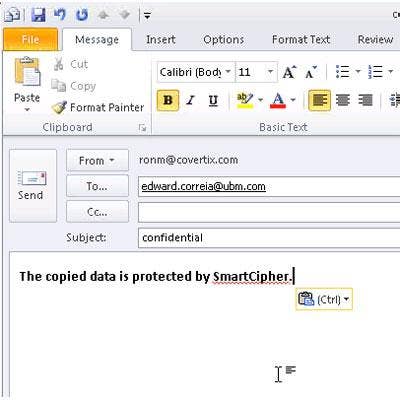
If data is copied from a protected file, a custom message is displayed (like the one shown) to inform the user that the operation being attempted has failed. Perhaps most fascinating, the security policies not only travel with the file, but also with the file's contents. For example, if the rules applied to a particular file permit copying of its data and pasting it into a new file, the data in the new file also will be protected. If a policy created later is to prevent copying, then the new file will no longer be accessible.
"We could prevent copying period, but you have to allow some sort of workflow," explained Kasan of this remarkable retroactive protection. "So we allow copying and pasting of permitted data between ordinary applications, but can prevent it if the policy changes later." The software also can exercise dominion over how applications relate to each other. "We can allow copying from Word to Word or from one Office app to another, but prevent copying from Word to Outlook, Notepad or a browser," he said.
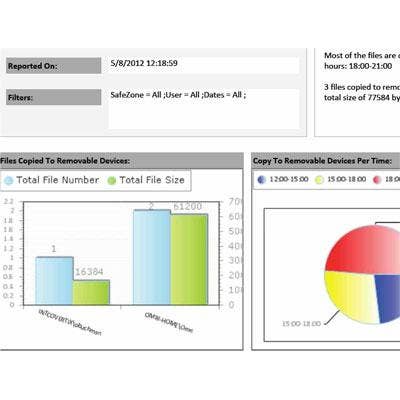
Reports
There are reports too, of course, as SmartCipher monitors, logs and potentially controls thousands of transactions and interactions on a given network or domain. "For compliance and reporting, everything is logged and audited, [including] who saves files, when they were saved, violations, authentications, file creation, emailing and printing of documents, even printing the screen," a feature that Kasan said he prefers not to make widely known. "We prefer [employees] not knowing this instead of not being able to do it, so you have evidence [of wrongdoing when necessary]." For highly secure organizations, certain reports can be instantaneous. "As soon as someone prints a screen, I can get an alert," he said.
Operating in the U.S. for just a few months now, Covertix is seeking channel partners targeting financial institutions, insurance companies, government agencies and other security-conscious organizations. SmartCipher requires a non-dedicated Windows Server with Microsoft SQL Server and can run virtually.