Tech 10: Hot Antivirus Alternatives For 2013

GoodBye Antivirus
Antivirus has a firm grip on endpoint machines for years to come and traditional endpoint security vendors have been building in behavioral analysis and other capabilities to bolster signature-based detection capabilities. A new breed of antimalware vendors is emerging. Some platforms are built on a crowdsourcing model where subscribers are given immediate access when a suspicious threat is detected. Other platforms use even more technical analysis engines to scan and monitor system processes to discover malicious files that may be mimicking normal processes, like a left mouse click.
CRN identified 10 emerging or innovative malware detection and analysis vendors. For now, the emerging technologies are being seen as yet another layer of protection, but over time security experts say traditional antivirus is likely to fade away into the distant past.
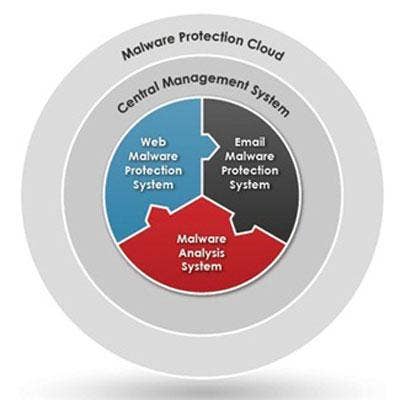
FireEye Malware Protection System
FireEye, Inc., released its next generation platform that combines its threat detection engine and threat intelligence. a, and interoperability with a broad ecosystem of more than two dozen technology alliance partners to secure all major threat vectors and enable rapid detection, validation, and response to attacks. The company's multi-vector virtual execution engine uses a virtual sandbox to capture Web objects, files, suspicious attachments, and mobile applications. An analysis is conducted to determine if any malicious code resides in the captured data. The company also uses a crowdscource intelligence cloud called Dynamic Threat Intelligence to share findings with other subscribers. FireEye APIs connect it to the company's third-party technology partners. This company has the intelligence community's seal of approval, with an investment from the Central Intelligence Agency.
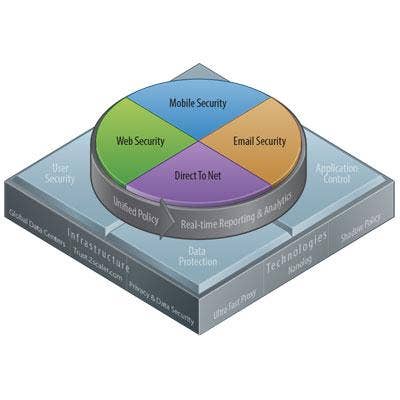
Zscaler User Security Platform
Zscaler Inc. said its User Security platform is designed as a "proxy to the cloud," scanning incoming and outgoing Internet content from any device in any location with near-zero-latency. User Security attempts to detect bots calling a remote command and control center, it looks for malicious destination domains, and maintains a feed of known phishing sites. The company can also detect malware that uses the peer-to-peer protocol going over HTTP and HTTPS. It uses a crowdsourced antivirus and antiSpyware technology and has features to deeply control end user browser sessions.

TaaSera Malware Behavior Detection System
The foundation of TaaSera Inc.'s NetAnalyzer is from funding from the U.S. Army Research Office granted to researchers at SRI International. The company has tuned its system to detect anomalies using a 12-stage lifecycle of malware behavioral activity. The goal is to find previously unknown threats or zero-day exploits. The platform was designed to provide continuous monitoring over endpoints, servers, network devices, virtual machines, and mobile or cloud infrastructure. It combines the malware behavior engine with a feed connecting to a database of malicious IP and URL addresses. The company said it adds more than 10,000 new sites daily.
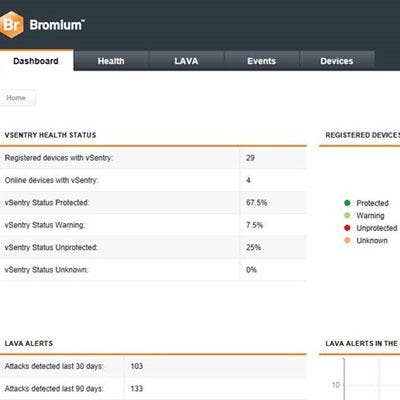
Bromium vSentury Uses Hardware Virtualization
vSentury from Bromium is being overseen by former Citrix gurus Simon Crosby and Ian Pratt. While the product is only in version 1.1, it is turning heads with its ability to isolate vulnerable Windows tasks in a sandbox environment. The company said its Microviser forces tasks to run with strict low privilege rights, minimizing the ability of malware to embed itself on a system. The company said the product currently runs on top Windows XP and the 32 and 64 bit versions of Windows 7. Support for Mac OSX is expected in early 2013. As expected, coming from former Citrix executives, the product works with Virtual Desktop Infrastructure (VDI) scenarios and runs on top of Microsoft Remote Desktop Services on Citrix XenDesktop. It works on VMware View too.

ReversingLabs Threat Intelligence Appliance
ReversingLabs is one of a group of favorite security vendors in government intelligence circles interested in analyzing a large volume of suspicious files to detect malicious code or hidden content. The company's TitaniumCloud threat intelligence database provides local access to malware files for malware analysts to identify and research potential malware. The company also provides a cloud-base model as well. Querying the system is extremely fast using its proprietary database architecture. The product is used by companies that have the budget to support reverse engineers. It gives them the ability to process malware samples using an automatic reverse engineering system.
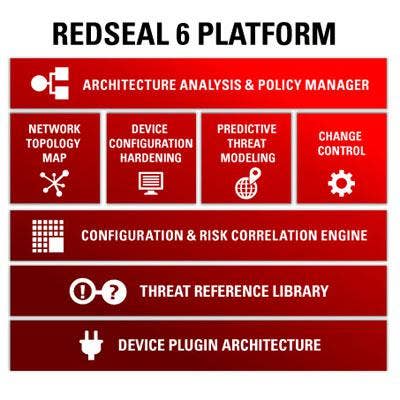
RedSeal Networks Platform For Threat Modeling
RedSeal Networks wasn't designed to provide malware detection; at least, not in a direct way. It helps network appliances perform properly by blocking threats before they enter the network. RedSeal 6 provides a layer over traditional network security appliances, giving enterprises the ability to attempt to conduct predictive threat modeling. The company's platform continuously monitors the configurations of firewalls, routers and other networking equipment to ensure that the rules are set correctly. The company's threat modeling feature can scan a complex network and identify the weak points likely to be targeted by an attacker. The latest version supports wireless networks and can integrate with appliances from several security information event management vendors.

Mykonos Software For Web Security Defenses
Web applications are the biggest targets of cybercriminals and while Web application firewalls have been available to provide protection a next generation technology has emerged. Mykonos Software sells a Web Intrusion Deception System that uses a proactive approach to thwart attacks. The company said it uses a "tar trap" to trap threats during the reconnaissance phase of an attack. Basically it builds situational awareness into Web applications by inserting detection points into the code. The software also fingerprints attackers to detect future attempts to break into a website.
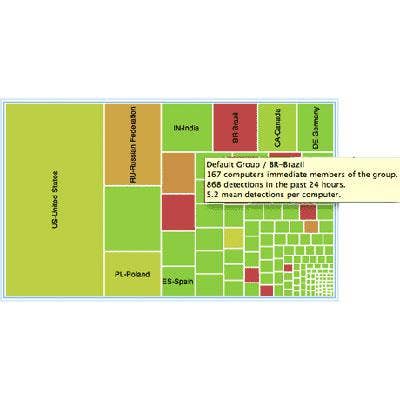
Sourcefire FireAMP for Advanced Malware Protection
Sourcefire appliances were built using the Snort intrusion prevention system developed by Martin Roesch in 1998. Roesch is still with the company, which has built on top of the foundation with the Sourcefire Advanced Malware Protection (AMP) appliance. The company uses a crowdsourcing model to detect threats. Individual files are analyzed, fingerprinted and shared with other FireAMP users. The analysis engine checks suspicious files against 400 characteristics to detect malicious behavior. The appliance connects to blacklist feeds and can extend to mobile devices and virtual environments.

Palo Alto Networks: Next-Generation Firewall With WildFire
Palo Alto Networks has been gaining traction in most analyst market share reports and reviews due to its cloud-based malware analysis system it calls WildFire. The inline firewall, performs…well, like a firewall, blocking unknown files without impeding performance. Threats are offloaded to a crowdsourced, cloud-based engine for analysis and sharing with other WildFire users. The company supports a virtualized sandbox where suspicious files can be submitted and observed for dozens of malicious behaviors.

Triumfant With Remote Monitoring For MSPs
Triumfant Inc. turned heads when it introduced its advanced malware analysis platform in 2008. This year the company introduced a monitored service offering for anomaly detection. Once it detects a threat, it provides a blueprint of the affected files, registry keys, processes and services that are impacted. The platform uses a company's security policies to detect unauthorized applications and can also scan and monitor endpoint systems for unusual states that signal a threat condition. The company claims its detection engine is built with analytics that can hundreds of thousands of state attributes to find anomalous behavior.