Tech 10 Security Products: Advanced Threat Protection

Advancing Advanced Threats Requires Comprehensive Strategy
Far too many businesses deploy technology but lack the processes or skilled IT security professionals to analyze alerts and dial down the white noise to rapidly respond to the most significant threats to the corporate network, say solution providers. Businesses often fail to proactively manage new technology and lack the budgeting for an in-house incident response team to investigate and contain security incidents, said Terry Kurzynski, a senior partner at Halock Security Labs. Kyrzynski said he uses a variety of tools when providing incident response and forensics services to clients and said there are more than two dozen security controls that should be part of a complete strategy against advanced threats. CRN pulled together security vendors from across the spectrum that can detect threats and bolster incident response. These 10 security vendors are gaining traction in the market with a variety of strategies to address advanced threats and aid incident response and digital forensics investigators.
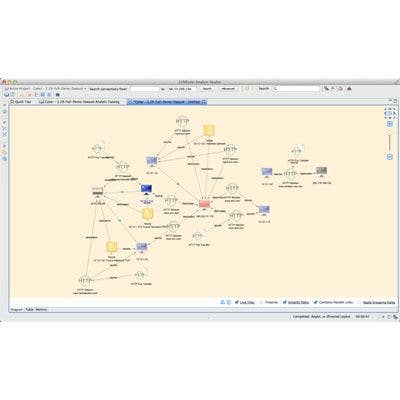
10. LYNXeon Crunches Data For Predictive Analytics
21CT is among a group of emerging vendors that focuses on security data analytics to aid detection and remediation of endpoint systems. The company believes its data set crunching can uncover patterns that bring incident responders a step closer to predictive analytics capabilities. 21CT's LYNXeon is network behavior analysis and visualization software that brings together data from traditional network and endpoint security systems, identifies relationships and can detect abnormal behavior.
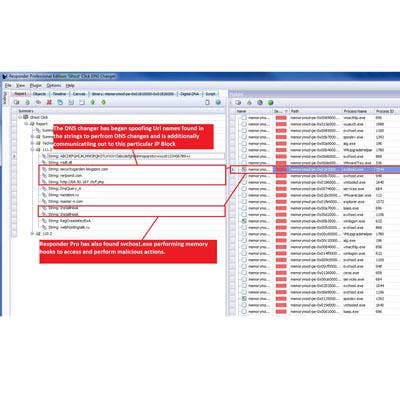
9. Responder Pro Scans Memory To Uncover Malware
ManTech International acquired advanced threat detection software in 2012 from HBGary. ManTech, which provides communication, systems engineering and security incident response services, is well known in defense sector circles. The company added the HBGary software to its portfolio to aid incident responders. HBGary Responder Pro software can probe Windows physical and virtual memory for information, such as chat sessions, passwords, encryption keys, Internet browsing history and other data.
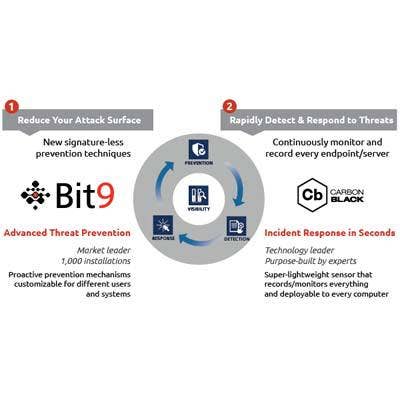
8. Carbon Back Adds Proactive Monitoring
Application whitelisting vendor Bit9 acquired Carbon Black in a $38 million deal that integrated advanced threat protection capabilities into its software. Bit9's security platform adds a sensor and data recorder on every endpoint, server and device on the network to enforce white-listing policies and analyze suspicious files. Carbon Black monitors file behavior for suspicious activity at the endpoint.

7. SilentRunner Sentinel Monitors Systems
AccessData sells forensics tools used by investigators to triage security incidents. SilentRunner Sentinel can monitor and analyze network traffic during an audit or forensics investigation. The visualization software can help determine the scope of a security incident and has a mobile component for passive network monitoring. It can capture VoIP calls, examine browsing activity, and reconstruct chat and webmail application traffic.
6. EnCase Aids Response, Assists Investigators
Guidance Software doesn't detect or prevent attacks, but it has developed data discovery software to identify sensitive information, including intellectual property, and plan appropriate incident response processes to rapidly contain and remediate an attack. It also is known for its computer forensics software. EnCase Enterprise software provides tools to enable digital forensics investigators to search, preserve and analyze data from servers and workstations.

5. XPS Network Security Appliance Scrutinizes Traffic
Fidelis Cybersecurity Solutions, a General Dynamics subsidiary, sells the XPS Network Security Appliance designed to detect advanced threats using deep packet inspection. Its product uses a collector server to store, query and correlate sessions on the network. Network sensors monitor and enforce policies on traffic flows. An email sensor can inspect email traffic and a Web sensor can monitor and enforce policies against proxy server traffic. An internal sensor can monitor data center and internal traffic.
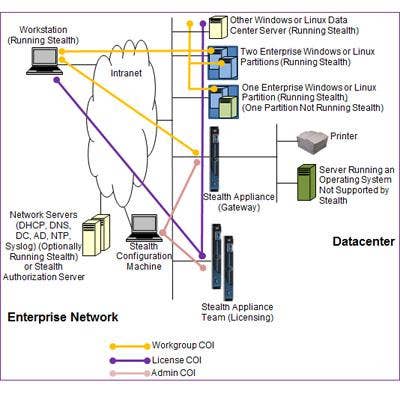
4. Stealth Cloaks Systems From Attackers
Unisys Stealth uses a data cloaking technique to mask endpoint systems and shield network traffic from external attackers. Unisys said its product is unique by creating segmented networks based on user identities and making endpoints appear dark on the network. Stealth software protects endpoint communication through an encrypted tunnel to a Stealth protected server.

3. Apex Identifies Zero-Day Exploits, Prevents Phishing
Trusteer was acquired by IBM for $1 billion last year. Its antifraud capabilities enable banks to prevent customer account session hijacking and detect phishing attacks on customer endpoints to prevent identity theft. The company's Apex software prevents phishing attacks at the endpoint and can detect custom malware designed to exploit zero-day vulnerabilities in commonly used applications by breaking the attack chain.
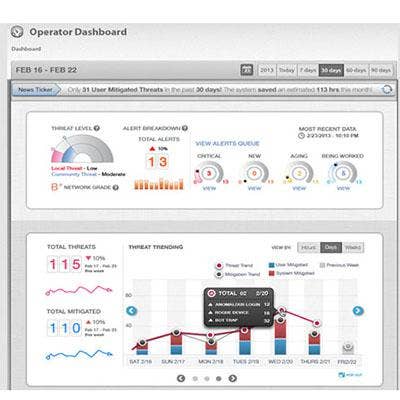
2. HawkEye Combines Endpoint Monitoring, Analytics
Hexis Cyber Solutions, a subsidiary of KEYW Holding Corp., sells an advanced threat detection platform that combines the capabilities of a security log management system for data warehousing and analytics and automated threat investigation and removal capabilities. Its HawkEye G product profiles uses sensors to profile "normal" system behaviors and then detect suspicious activity.
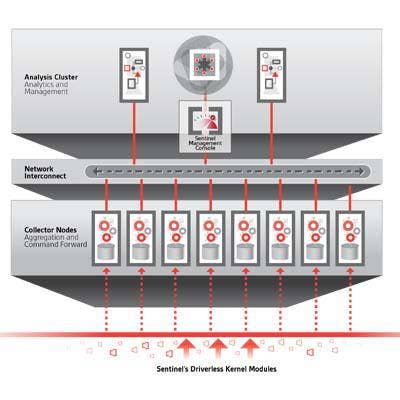
1. Sentinel Goes Deep Into Windows
Countertack Sentinel is an advanced endpoint threat detection and response platform. The company uses lightweight agents embedded into the Windows operating system kernel of endpoint systems to monitor for malicious behavior without impacting performance or stability. The company then adds the endpoint threat visibility into its Cloudera Enterprise-based analytics server for automated threat detection to give IT analysts visibility across the enterprise.