Gutting Superfish: 5 Steps To Remove Lenovo's Pre-installed Malware

How To Gut Superfish
Controversy erupted this week over software that Lenovo started installing on its consumer laptops last year. The software in question is Superfish Window Shopper, and is vulnerable to exploits that include unauthorized JavaScript execution, intercepted communications and NSA-style spying. The company as of late January stopped installing the software. But as the world's number two laptop supplier, millions of Lenovo systems are potentially at risk.
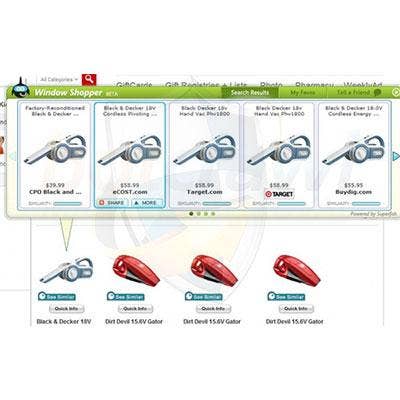
STEP 1: Is Superfish Installed?
The idea behind Superfish is to present online shoppers searching for an item with lower-priced buying options for the same item. Sounds pretty useful. The tool is implemented as an extension to Chrome and Internet Explorer, and works by performing a visual search using the original item's image and displaying buying alternatives like the one shown here. Sounds harmless enough. But to perform this magic, the app takes some liberties with user security that leave the system vulnerable. If the system in question shows a screen like this, chances are it's infected. For a more definitive answer, move on to Step 2.

STEP 2: Stop The Service
Right-click the Windows Taskbar and open Task Manager. Click the Name column to sort the services by name and scroll down to the V section. If there's a VisualDiscovery service (which may or may not be accompanied by the word "Superfish" in the description column), then the system definitely has Superfish. Right-click on VisualDiscovery and select Stop Service. Optionally, confirm that it's disabled by bringing up the browser from Step 1 and refreshing the page. The Window Shopper panel shouldn't appear, but will come back without further steps. Click Next to continue removing the virus.

STEP 3: Uninstall The App
In the Programs and Features Control Panel, locate and click on the app called "Superfish Inc. Visual Discovery" or something similar and uninstall it. It's possible that an administrator password will be required here.
It's not over yet. Once that's done, restart the machine and continue to STEP 4.
STEP 4: Delete The Cert
The magic of Superfish is also what makes it dangerous. In essence, the app creates a self-signed certificate, which deems it a trusted party. That gives it the authority to intercept and modify traffic, to decide which encrypted communications are trustworthy, and most importantly, to generate its own encryption certificates for sites that use secure HTTP. That's the part that could allow malicious actors to gain access to private data, communications or sites. The fastest way to determine the authenticity of the certificate on the system under repair is to run Superfish CA Test, a browser-based scanner with links to removal instructions for infected systems.
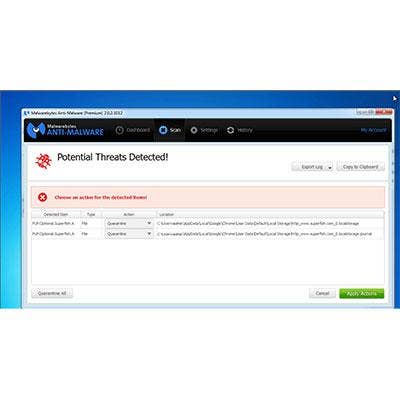
STEP 5: Run A Malware Scan
After completing steps one through four successfully, the system under repair should be out of danger. But we also recommend installing and running a malware scanner on the system to keep it that way. The tool recommended by the CRN Test Center is Malwarebytes Anti-Malware 2.0 Premium, which actually identifies Superfish as malware and would have flagged and recommended quarantine in the first place.