Tech 10: Security Products For Data Protection, Email, Web Security

CISOS Focus On Data Protection, Web Security
Data protection, security analytics and modern log and event management systems are topping the list of technologies being considered by chief information security officers, according to a recent study of more than 1,000 senior-level information technology leaders. The survey, conducted by the Ponemon Institute, found that the spate of high-profile data breaches, coupled with news reports about targeted and sophisticated threats, have driven renewed interest in bolstering existing security technologies or considering a growing list of innovative security startups. CRN pulled together these 10 products that focus on increasing visibility and control over sensitive data or help protect some of the systems and applications highly targeted by cybercriminals.
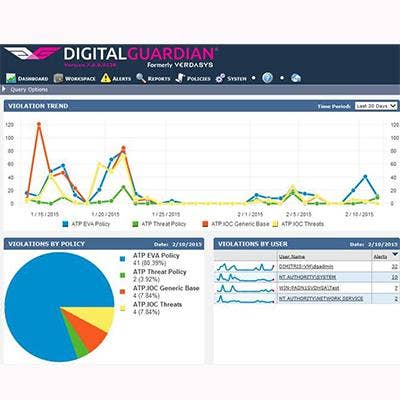
Digital Guardian Adds Threat Detection To Data loss Prevention Platform
Digital Guardian (formerly Verdasys) extended its data loss prevention platform to use agent-based threat detection technology. Digital Guardian 7.0 supports Windows, Mac and virtual desktop environments and has a redesigned product architecture to provide advanced threat detection incident response and protection. The agent resides at the kernel level and uses behavioral analysis to block unknown applications and detect malware. It gains additional support by integrating threat intelligence feeds from third-party network security vendor partners.
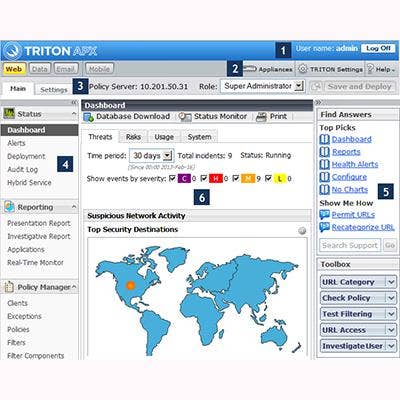
Websense Adds SaaS Services Visibility To Triton APX
Websense released its Triton APX 8.0, integrating its data theft detection engine with its Web and email gateways. The company launched a new ’Drip DLP’ capability designed to identify data theft over time. New character recognition capabilities can identify personally identifiable information and other sensitive data embedded in images. The platform also now supports visibility into files shared through Microsoft Office 365, Dropbox, iCloud Drive, OneDrive and Box. The Triton platform provides customers access to a cloud-based threat intelligence service designed to share threat indicators associated with advanced malware, blended threats and spam.

Fidelis Network Collector Bolsters Incident Response
Fidelis, known for the content inspection and network throughput capabilities associated with its data loss prevention platform, enhanced its XPS Collector with a stronger correlation engine and an improved user interface for incident responders. The collector stores historical metadata and has an analytics layer that can identify relationships that could indicate suspicious activity. Fidelis also recently unveiled a renewed partnership with Bit9, enabling customers to integrate its Carbon Black endpoint visibility and incident response capabilities with Fidelis XPS.
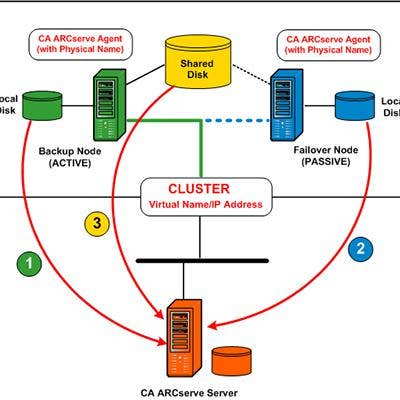
CA Integrates Access Control, DLP Into Broader Data Protection Platform
CA acquired Orchestria in 2009 for data loss prevention capabilities and in recent years has been tightly integrating the data discovery, classification and content-aware access control technology it calls Data Protection into its authentication and access management portfolio. Formerly called DataMinder, the DLP capabilities work with Microsoft SharePoint and can scan the network for sensitive data and classify it. The company’s Data Protection solutions features a central management platform to control access and handling and enable businesses to continue to retain visibility of data flow and control in sanctioned SaaS-based services.
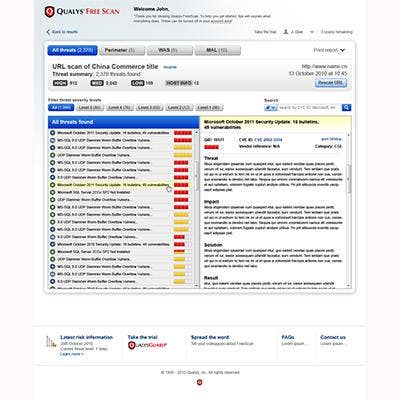
Qualys Adds Deeper Website Inspection Capabilities
Vulnerability management vendor Qualys has bolstered its Web Application Scanning service with the addition of progressive testing and enhanced reporting capabilities. The company can maintain information from previous scans to avoid duplicating work and expand testing coverage of Web applications over time. The progressive testing feature automatically starts, stops and resumes scans without the need for manual intervention. The scan can identify frequently targeted vulnerabilities including cross-site scripting (XSS) and SQL injection errors.

Proofpoint Bolsters Email Security Suite
Proofpoint released the new Enterprise Protection Suite 8.0, adding support for a hosted Webmail portal, which can be used by employees as a failover in the event that the organization’s primary mail server goes down. Proofpoint also added single sign-on through SAML 2.0 and support for the commercial-grade Sendmail message transfer agent. Version 8 adds encryption for data in motion through secure multipurpose Internet mail extensions. Proofpoint has been going beyond antispam and email archiving, adding targeted attack protection by detecting and blocking malicious links and email attachments.

Code Green TrueDLP Supports Virtual Appliance Deployment
Code Green Networks is shedding its requirement for a hardware appliance for its TrueDLP data loss prevention platform. Customers can acquire a software license and run components of the platform in a virtual environment. Code Green has bolstered the reporting capabilities of TrueDLP and made performance improvements to its Cloud Content Control. The company has been building out data discovery capabilities across cloud-based environments.

GTB Launches DLP-As-A-Service
GTB Technologies embeds a Content Aware Reverse Firewall into its data loss prevention products and unveiled a SaaS-based DLP product that can monitor all traffic, including SSL-protected communications that contain sensitive data. The SaaS service can be extended to laptops, desktops and mobile devices to protect data on-premise and with mobile employees. The company’s platform has digital rights management capabilities and the ability to uncover Shadow IT, the unauthorized use of cloud storage applications. The platform is designed to identify sensitive data in popular cloud storage environments including Box.net and Google Drive.

Cyberark Injects Security Analytics Into Intel Security For Privilege Management
Privileged management specialist Cyberark said its analytics can be tightly integrated into the McAfee Enterprise Security Manager to provide more contextual information about attacks. The fully integrated technologies can identify privileged account user behavior that is suspicious and prioritize incidents that involve privileged accounts, the company said. Intel Security’s Threat Intelligence Exchange is being tied into the McAfee Enterprise Security Manager to interoperate with other security products in the vendor’s portfolio and other third-party technology partners. The data exchange layer enables the McAfee security technologies to work together when a threat is identified, extending protection across vulnerable points throughout a company’s corporate network.
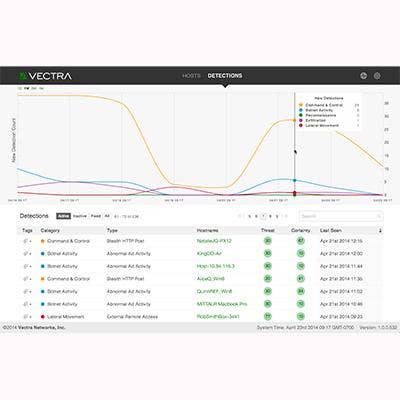
Vectra Networks Launches X-series Platform
Vectra Networks launched its X-Series Platform designed to capture a baseline of user behavior and discover suspicious activity that could signal an insider threat or a hijacked user account. The company said it can identify the proximity and impact of a threat to high-value assets. Rather than focusing on controlling sensitive data, Vectra concentrates on host connectivity and attempts to identify activity that appears to be reconnaissance, lateral movement and unusual data acquisition. Vectra said its platform is deployed in passive mode on the network and monitors traffic to and from internal applications and the Internet. Incident responders are given details on a detected attack and the priority list based on the risk a threat poses to sensitive data.