5 Recent Mac Vulnerabilities Partners Should Know About

Be Aware
Reports emerged earlier this year that OS X was the "most vulnerable" software of the year, based on a study by CVE Details. However, Mac environments in general remain more secure than their Windows counterparts, despite an increasing number of attacks, Thomas Reed, director of Mac offerings at Malwarebytes, said. Specifically, he said adware, malware and potentially unwanted programs pose a threat to Mac security down the road. That security lead won't necessarily last forever, Reed said, as Macs present a tantalizing target to hackers as they gain a broader reach in the market.
For partners with Macs in their client environments, here are five recent vulnerabilities they should know about to stay ahead of the curve on OS X security.

Ransomware
In March, researchers from Palo Alto Networks found evidence of ransomware, called KeRanger, targeting Mac operating systems, in particular going after files such as photos, videos, Excel spreadsheets and Word documents. The researchers found the software usually penetrated a user's environment through downloads of Transmission. The Bit Torrent file-sharing company's website had been compromised to include download links for both its software and the ransomware in question, prompting 6,500 people to accidently download the infected software. As of March 5, Apple had revoked the certificate for the software and Transmission had removed the infected software from its website.
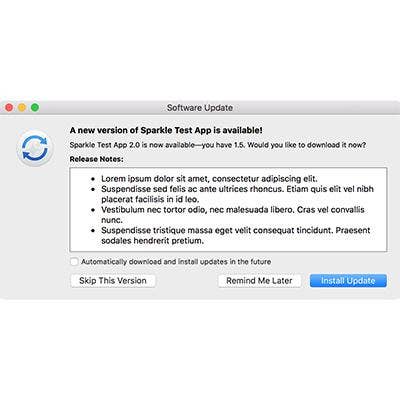
Sparkle
A vulnerability in Sparkle emerged in February that put third-party applications on high alert. Sparkle is a tool that many applications, such as Camtasia, uTorrent, DuetDisplay and Sketch, use to push updates to users when they are not in the App Store. Discovered by security researcher Radek, the vulnerability, if exploited, could allow hackers to execute a Man in the Middle attack, intercepting traffic between the user and the application. Since the vulnerability was disclosed on a blog post, Sparkle, as well as many of its app developers, have closed the vulnerability.
System Integrity Protection Flaw
In March of this year, a vulnerability could have allowed hackers to bypass System Integrity Protection, which is "designed to prevent potentially malicious software from modifying protected files and folders," an advisory by SentinelOne researchers said. The vulnerability, which occurs in all versions of OS X, could have allowed hackers to bypass restrictions on root account actions and allow for local privilege escalation and execution of code. Apple has issued a patch for the vulnerability.

Thunderstrike 2
Thunderstrike 2 emerged in August of last year, using infected Thunderbolt accessories to spread malware to any attached device. The accessories became infected when plugged into a device that was affected by a phishing attack or malicious website. What set the new vulnerability apart from its predecessor, Thunderstrike, is that it can be spread remotely. The vulnerability was proven through a proof-of-concept attack presentation by security researchers Hudson and Xeno Kovah at the 2016 Black Hat conference.

Symantec Vulnerability
Most recently, in May a vulnerability was discovered in Symantec antivirus software that compromised Linux, Mac and Windows environments. Discovered by Google researcher Tavis Ormandy, if exploited, the vulnerability could allow for root-level control over a system by triggering memory buffer overflow when an infected email is scanned by the antivirus engine. Symantec has already issued a patch for the vulnerability.