16 Hot New Security Products Launched At Black Hat 2016

Security Solution Overload
The security industry turned out in force to Las Vegas this week to attend the annual Black Hat Conference. Vendors used the opportunity to showcase their latest and greatest technology releases. Those releases included new updates for threat detection, product integrations, security services, threat intelligence and much more. Vendors said the new solutions will help customers step up their game against attackers and cope with new threat vectors, many of which were presented by hackers at the show. Take a look at 16 solutions that were launched at the show this week.
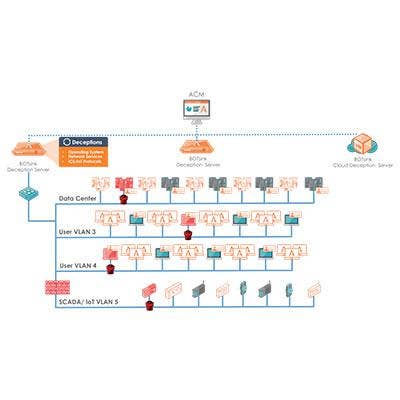
Attivo ThreatMatrix Deception And Response Platform
Just in advance of the Black Hat event, Attivo Networks unveiled the enhancement of its Attivo ThreatMatrix Deception and Response Platform, adding capabilities around vulnerability visibility and assessment, automated responses to misconfigured systems or credentials, routed network support, and extending the platform to protect against Microsoft Active Directory attacks. These added capabilities expand Attivo's capabilities beyond detection to also include protection capabilities, the company said.
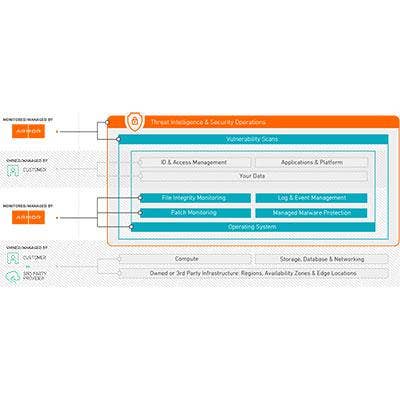
Armor Anywhere
Armor, formerly FireHost, Monday rolled out Armor Anywhere, a solution to provide data security across all infrastructures, including cloud infrastructures from Amazon Web Services and Azure. Capabilities of the new solution include managed security, visibility, controls, threat intelligence, patch monitoring, log management, malware protection, file integrity monitoring and external vulnerability scans for workloads, assets and applications, the company said.
"The modern threat landscape presents sizable challenges for companies managing sensitive data, particularly those facing strict compliance requirements," said Chris Drake, founder and CEO of Armor, in a statement. "Armor Anywhere is a battle-tested security solution backed by threat expertise that complements our customers' unique needs. It simplifies security so they can focus on growth and driving revenue, not defending against sophisticated cyberattacks."

RiskIQ Security Intelligence Services
San Francisco-based RiskIQ expanded its External Threat Management platform at Black Hat 2016, announcing it has added Security Intelligence Services. The new services, now generally available, arms security teams with critical data sets for threat forensics and incident remediation, the company said. Specifically, the data sets include Passive DNS data for insight into how a domain name or IP address changes over time, WhoIS data about domain and IP address ownership, and newly observed domains.
"Security teams spend so much time gathering all the information they need to respond to cyberincidents, it limits their efficacy," Arian Evans, vice president of product strategy at RiskIQ, said in a statement about the launch. "The new data services offering puts global internet data sets at researchers' fingertips to enrich analysis, inform decision-making and reduce the time it takes to investigate and respond to new threats."

Trustlook Sentinel
San Jose, Calif.-based mobile device security vendor Trustlook launched Trustlook Sentinel Monday to help provide an additional layer of mobile device protection. Different from other mobile device security solutions, which center around antivirus applications, Trustlook Sentinel is based on the operating system, providing threat monitoring, behavioral analytics and protections across applications, the company said.
"Sentinel represents the next evolution in mobile device security," Allan Zhang, founder and CEO of Trustlook, said in a statement. "Tightly integrating security through an on-device, behavioral-based model makes detection much faster and more effective, and ultimately affords better protection against malware and other threats." The solution is expected to be available in the third quarter.

Ironscales Federation
Israeli security startup Ironscales is looking to tackle the phishing problem, unveiling at Black Hat the launch of Federation, a phishing threat intelligence network. The Federation solution will provide businesses with threat intelligence on zero-day attacks, ransomware, malware, bots, spam, spoofing, pharming and more to arm them with the data they need to protect their own organization. The launch adds to Ironscales' portfolio of anti-phishing solutions, including user training and an employee-based intrusion prevention system, where users flag questionable content for an automatic scan and threat mitigation.

Kudelski Security
Switzerland-based Kudelski Security used Black Hat 2016 to officially launch into the U.S. market, offering a cybersecurity service and managed security services. The launch was made possible by the company's May acquisition of Arizona-based MSSP Milestone Systems. Kudelski brings capabilities around consulting, security technology, managed services, training, technical support and custom innovation to the U.S. market, as well as a strong reputation in the European market. Kudelski said it is focused on next-generation technologies and growing services capabilities.

Deloitte ThreatConnect Platform
Just before Black Hat, Deloitte Cyber Risk Services unveiled an alliance with ThreatConnect to boost the capabilities around its Vigilant Managed Services. By integrating ThreatConnect's threat intelligence platform with its own intelligence and analytics services, Deloitte said it will be better able to tackle threats with deeper intelligence from a single platform. Specifically, Deloitte said key benefits include a united defense against threats, automated aggregation and analysis of threat intelligence, optimized management capabilities and a community to share intelligence with.
"We're focused on providing a portfolio of tightly integrated cyber operations services. … By teaming with ThreatConnect, we can further enable organizations to maximize the value of their security technology investments, combat the fragmentation of their security organizations, and enhance their infrastructure with relevant threat intelligence across a scalable, integrated platform, said Adnan Amjad, cyber threat risk management practice leader for Deloitte Advisory cyber risk services and partner at Deloitte & Touche LLP.

Demisto
To help businesses develop incident response procedures, Demisto Tuesday launched an open industry standard to build and share incident response playbooks. Under the new standard, businesses can collaborate and share their own incident response procedures to help build better standards for the industry overall, the company said. Demisto has set up a platform for companies to automate and code the playbooks, as well as allow security analysts to collaborate over Slack.
"While cybercriminals collaborate to attack and steal from organizations, our industry until now has lacked a means for sharing best practices around incident response and community development of playbooks," said Dan Sarel, Demisto co-founder and vice president of product, in a statement. "At Demisto we believe that the only way to combat cybercrime is through collaboration and we are proud to offer today a major step in this direction."

Endgame Hunt Platform Version 2.0
Arlington, Va.-based endpoint security startup Endgame unveiled a new version of its Hunt platform just before the event, adding capabilities to speed time of detection and response. Specifically, the Hunt Platform Version 2.0 adds capabilities around hardware-assisted control flow integrity to monitor program execution in real time, signature-less malware detection, and automated investigation. Endgame also announced a partnership with Accenture, No. 2 on the 2016 CRN SP500 list, for a threat hunting-as-a-service offering. The offering brings together Endgame's security solutions with Accenture's cybersecurity team for continuous endpoint monitoring, exposing and eliminating both active and dormant adversaries, and actionable lists of vulnerabilities and remediation procedures to limit future attacks.

Pwnie Express Blue Hydra
Just before Black Hat, Boston-based Pwnie Express announced the general availability of two of its solutions to provide Bluetooth detection and user-defined penetration testing mobile devices. Specifically, the open-sourced versions of its Blue Hydra and Android build system software, announced July 27, provides a tool to discover Bluetooth-enabled devices and associated threats and perform mobile penetration testing. These capabilities will be especially helpful to the open-source community around Internet of Things technologies, Rick Farina, Pwnie Express director of R&D, and co-inventor of Blue Hydra, said in a statement.
"Developing and releasing open-source tools reinforces our commitment to give back to the security community and make it easier for security teams to address the growing device threat landscape. These tools will help security professionals with Bluetooth detection, which is key to effective mobile device detection in our increasingly connected and IoT world," Farina said.

Domain Sentry, Brand Sentry
Farsight Security, a San Mateo, Calif.-based threat intelligence company, announced just before Black Hat the launch of two new security solutions. The first, called Brand Sentry, helps identify phishing, counterfeiting and other cyberthreats that might be using (and therefore harming) a client's brand. The solution works using Farsight's Security Information Exchange to track specified domains and hostnames on the Internet. Farsight also launched Domain Sentry, a tool to help companies monitor and be alerted to any changes to their domain or IP addresses that might signal an attack, such as moving to a new IP address, using different name servers, or using a new mail exchange. Farsight said businesses can use this tool to detect compromised hosts, domain hijacking, domain theft and monitor infrastructure changes.

Cybereason
Cybereason unveiled Wednesday the launch of three new security services offerings that provide companies with military-grade solutions: the Adversary Hunting Service, the Active Monitoring Service and the Incident Response Service. The Adversary Hunting Service provides a service for businesses to know if they are currently under attack, which includes deploying sensors across an environment, correlating data and having security experts dive into the findings. For long-term security needs, the Active Monitoring Service offers a round-the-clock active surveillance service, including continuous monitoring and response. Finally, the new Incident Response Service adds services capabilities around incident response planning, simulation, education and incident response.

SECDO
Endpoint detection and response company SECDO announced Wednesday the integration of the company's solutions with SIEM providers, such as HP ArcSight, McAfee Enterprise Security Manager and Splunk Enterprise Security. The company said this move to have two-way integrations with major SIEM providers and alert validation will help clients better detect, investigate and respond to threats. The two-way integration, in particular, allows SECDO to analyze alerts coming into the SIEM solution for severity, as well as provide its own alerts to the system.
"As many organizations increasingly rely on SIEM solutions, investigating the overwhelming amount of alerts is a critical, yet time-consuming and painstaking process that has become a serious bottleneck," said Shai Morag, CEO and co-founder of SECDO. "With our new two-way SIEM alert validation, SECDO enables security teams to focus their efforts on high-priority incidents and eradicate breaches quickly." The solution will be generally available in October, the company said.

IOActive Advisory Services
Seattle-based IOActive unveiled just before Black Hat the launch of a new Advisory Services practice, which it says will offer security consulting, testing, and research to clients. The security services company said the new Advisory Services will look to move beyond compliance needs and help clients get ahead of threats with program efficiency assessments, threat scenario analysis, data security mapping, secure product development and adversary emulation services. The services will be launched this year, the company said, with some proofs of concept already out in the market.

Digital Guardian, CounterTack Integration
Digital Guardian and CounterTack announced on Tuesday a planned integration between the two companies that will bring together Digital Guardian's data protection platform with CounterTack's Digital DNA solution. The launch extends Digital Guardian's data protection capabilities to the memory level, with in-memory threat analysis, behavioral detection and forensic capabilities. The partnership will start as a product licensing agreement with CounterTack and will turn into a full product integration in 2017.

StealthAudit
Hawthorne, N.J.-based Stealthbits Monday launched StealthAudit, an auditing, compliance and governance framework for unstructured data and critical applications. The solution includes capabilities for comprehensive data collection, analysis, remediation, workflows and reporting. The latest launch, in particular, adds capabilities around privileged accounts for Unix and Linux infrastructures and a new workflow for sensitive data governance.
"This release is all about securing credentials and data; the two things every attacker is targeting, regardless of how they got it, or if they were on the inside to begin with," Adam Laub, Stealthbits' senior vice president of Product Marketing, said in a statement. "We're continuing to place a high priority on allowing our clients to lock down the information that matters most to them, and the accounts that provide access to that information."