How To Hack An Election Machine And How Partners Can Help Stop It

The Threat Is Real
With the election coming in 35 days, one critical question emerges: How secure are new electronic voting systems? That threat is now a very real concern, FBI Director James Comey said recently, revealing that investigators had found attacking attempts in more than a dozen states' registration sites. Every year, Symantec holds what it calls, "Cyber War Games," where it builds a critical infrastructure target environment and gives employees the chance to attack it and better learn how attackers work and think. In past years, the targets have been a realistic hospital, as well as financial services and bank environments. This year, Symantec looked to take on election machines to help raise awareness of the security concerns facing those systems.
"Putting awareness and a spotlight on this gives people the ability to choose [whether they want to use these systems]," Samir Kapuria, senior vice president and general manager of Symantec's cyber security group, said. "It raises the understanding of the risks of something so critical for a government."
Take a look at what they found.

Procuring An Election Machine
To acquire the election machine tested in its Cyber War Games, Symantec went out, not as a security company, but as an attacker might: to the Internet. Acting as an adversary, the company was easily able to acquire two machines on an online auction site for between $150 and $200. In doing this, Brian Varner, security researcher, said Symantec was able to demonstrate how easy it would be for a hacker to get access to an election machine for testing or reverse engineering.
"We have all the components of the modern-day election system," Varner said.
Symantec also simulated other election system components, including the backend databases, ID cards and how the machine pushes information to the media.

Evaluating Security Technologies
Once Symantec had the devices in house, the next step was reconnaissance, Varner said, starting with gaining access to the operating system and pull out the hard drive and the memory of the machine. From there, Varner said Symantec discovered the device wasn't using full-disc encryption. He was then able to re-open the previous election poll run on the machine, where now President Barack Obama won, and insert the name Kapuria. While the machine did have a paper trail that printed out the ballots cast, to then be certified by a poll volunteer, the hacked device now spit out 821 votes for Kapuria against Obama. Varner said Symantec also found the operating system was very old, from around 1997, and was not running any antivirus solutions.

Attack Type 1
Symantec found three main types of attacks that can be carried out on election machines. The first is centered around the idea of "chaos," Kapuria said. The attack works by using the chip cards inserted into the voting machines, which are intended to validate a voter's identity. However, with a $15-or-so chip coder with malicious code, Kapuria said a hacker can reset the card and submit another vote. From there, hackers can either submit a few extra votes for a candidate or even hard code a voter name onto the card, which could result in thousands of votes from the same person in a day and potentially nullify a day of voting for confusion.
"That creates chaos and distrust in the system," Kapuria said.

Attack Type 2
The second type of attack involves removal of the data from the election machine after a day of voting. The way the system works, Kapuria said, election volunteers remove a storage device (like the one pictured) from the machine to extract the votes for tallying in a database. If someone were to destroy that physical storage device or insert tailor-made malware, a hacker can "corrupt the correlation" of the election voting data.
"That would be the equivalent of digital ballot stuffing or a denial of service attack," Kapuria said.
Attack Type 3
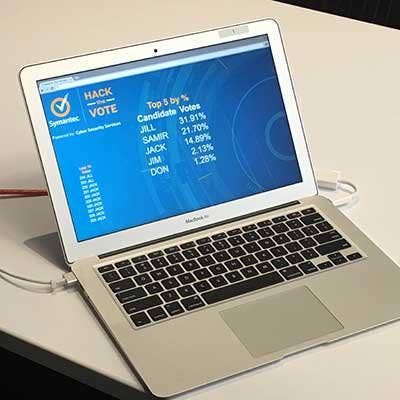
The third type of attack comes down to behavioral science, Kapuria said. He said the herd mentality of voters tend to follow the poll leader or might not go through the trouble of voting if it looks like the election might be a landslide. He said if hackers are able to influence the data that is being pushed to the media or on social media through the election machines, they can potentially influence the election. He said Symantec demonstrated this capability by connecting the machine to a YouTube account and posting misinformation.
"That misinformation, that social engineering, there is no recourse in that situation because I've influenced the masses," Kapuria said.

What Security Technologies Should There Be
After simulating the election machine environments, Kapuria said Symantec found that multiple key security technologies and protocols were missing. First, there lacks a uniform set of standards between states as to how the machines work or what security technologies they should have in place. Second, Kapuria said the machines should have technologies like DLP, endpoint protection, certificates and encryption to ensure the information coming from the machines can be validated. Finally, he said there are technologies to protect the tallying database, including proxies to monitor data ins and outs and a 24/7 monitoring from a Security Operations Center.