Q&A: Fortinet CEO Xie On Why The Company Will Beat Cisco, Palo Alto Networks And Check Point As The Network Security Market Evolves

Ken Xie On The Record
The network security market is entering its third generation, Fortinet CEO Ken Xie said. In a recent interview with CRN, Xie spoke about how he's seen the network security market evolve since he started his first security company and how he sees it evolving today, with demands for performance, integration, and automation at the forefront. With that shift, Xie said the market could see a shakeout of some of the market's biggest and best-known vendors, as he said competitors Cisco, Check Point and Palo Alto Networks all face challenges in the new generation. Here's what he had to say about what it takes to succeed in today's network security market, and what challenges the competition and his own company might face in the evolutions to come.

Walk us quickly through the evolution of Fortinet as a company.
Fortinet is my third network security company… The first company we all used the software to do the firewall. My second company [Netscreen] I felt we needed to do better, so I started using not only the software but also complementing it with dedicated hardware, including the dedicated system and dedicated chip. Both companies only did firewall VPN – that's what we called the first-generation of network security, called connection security... We saw the opportunity to IPO the company and later sold it to Juniper for $4 billion…
Then, I started Fortinet in the end of 2000. It was what I call second-generation network security, because second generation models content and applications. The company was initially called App Secure – for application security. When we launched the product in 2002, we called it an anti-virus firewall… That's where basically we found most of our malware comes from permitted connections, so basically the firewall cannot stop the virus, so we have to look inside the connection for the bad content. That's the second generation… Then about two years ago we started preparing for the launch of the third generation of network security. Instead of just looking inside the connection, now we need to do the whole infrastructure.

Why do we need this "third generation" of network security?
In 17 years, the mobile device has started to dominate more than the PC right now. At the same time, cloud and IoT [are growing]. We feel that the data no longer just sits inside the network anymore. It's pretty much everywhere, so infrastructure security is starting to become more important. That's why we started to promote the [Security Fabric] because it is the third generation of network security, which tries to protect the data whether it's in the cloud or on a mobile device or IoT or inside the network.

Take about that evolution of the firewall market – how are you seeing that space changing?
The way to compare this is more like air travel. The first generation - the firewall VPN connection security - is like early days where you buy a ticket and can get on an airplane. That's where the firewall checks who can get in and who cannot. The second generation – what we call UTM or next-generation firewall – looks inside the connection and content application, is more like today where you not only have a ticket but you also need to do the security screening with your luggage and the X-Ray machine to see if you are carrying any bad content. That is the second generation of network security. Now, the third generation – with the infrastructure – they have probably already looked at your background before you even bought a ticket and might also look at your social media, family or background connections. That's the whole infrastructure security. That's where we're starting to get to the third generation of network security.

How far along is your competition in that evolution of the market?
Nowadays 97 percent of companies are competing in what we call the first level, which is detection…But, detection isn't enough. You also need to get to stage No. 2, which is prevention. Detection doesn't have to be in-line, but prevention does have to be in-line to act and stop the traffic and also make sure the good applications can get through… Only about 5 to 10 percent of companies can move to this second stage – the prevention stage. Then, only a few companies can move to the third stage, which is the integration stage. That's where Cisco and Juniper, which bought my previous company, are struggling on the integration. If you keep buying different companies and want to integrate the functions in the product… only like Fortinet, Palo Alto Networks and Check Point, with development capabilities in house, can integrate more easily… The fourth stage is performance… Then, stage five is lowering cost… With high cost, you prevent a lot of the deployment.
Where do you see Fortinet along that evolution?
In the very beginning when we started to develop the ASIC chip and the SPU, it took a long time. Every single chip needs about three years to develop and you also need two or three generations to develop it and get it better and more mature. We've spent over $1 billion in the last 17 years to develop this chip power to give better performance and better cost. That's seeing a lot of benefit right now. We now cover about 25 percent of the total global deployment… That's because of the cost advantage and the performance advantage. We've more than doubled the No. 2 Cisco and Check Point with the number of devices deployed.
Also, we started growing very fast. Last quarter, I think our billings growth was over 20 percent. Palo Alto just announced [the other] week and they're growing at about 12 percent. We're at a similar billing level, so we're now starting to grow faster than Palo Alto, Check Point, and Cisco… When we started the company we tried to compete in all five stages. But, level four and level five need a long-term investment… We are the only one designed from the chip level… That gives us more of an advantage.
Do you see your network security competition moving to close that gap?
The other competitors are hesitant to get in because you need at least ten years of investment and around $1 billion to build that. At the same time, if it's a public company, they're looking at the next few quarters return. That makes it hard to justify the investment… It's moving fast. It's interesting, new features are needed but the old ones never go away. It's about making sure that you're adding new functions and at the same time adding speed to old functions. That's very important. The network speeds up every two years. If we don't keep up the performance and control the costs, it's more difficult to compete long term… Today, it's also no longer just network security anymore. You also have to consider endpoint, web access, applications like email web application and up into the cloud. That's how the Security Fabric covers it. Network is still the major piece, but all of the parts need to be working together. That's how the Security Fabric infrastructure gives us an advantage.

How do you evolve the business in a way that's successful as you need to navigate these changes in the network security market?
It's about integration and keeping improving… There's a lot of smaller companies [in security] and they all have a certain point solution or niche solution and can only address a niche market. But, integration of multiple functions and, eventually, trying to make sure they can address the performance and other issues, then they can address a much broader market. That's why we want to make sure we design the platform – the Security Fabric – so we can keep integrating new functions at the same time that we advance old functions. So far, the space is growing between 7 and 10 percent year over year. We're able to double and triple that growth in this space, while at the same time keep adding additional functions. That's how the competition is growing in the space. We have over 300,000 customers. We have the biggest customer base.
The company has a culture to develop the best technology product and at the same time try to keep improving on the marketing and sales. The space today sometimes feels a little bit over marketed.

What do you think the next wave of change in network security will be?
I think eventually the business is moving more to the infrastructure part. Some parts of the infrastructure when they design it – whether it's switching, routing – they do not quite have security. Eventually they need to consider security from the beginning. That's what I view as the next-generation. Network security will also need to deliver traffic based on the application and the security and the device that its using to leverage it. Today, security tries to make out on the network inside on a high level on application, user and company level. Eventually, if there is a way to address that all together that could be much better. The Fabric connects the different pieces of security together, but that's more on the security front. I think there's an additional layer from the vertical side or layer that can be more efficient. But, now they're different industries. The PC and the networking industries are very separate right now. I think there will be some way to do that.
What markets are you winning in? Where are you struggling?
We're very successful in the Fortune 100 companies and also the telco space… because they are very technical buyers. They do the testing before they make the decision to buy. Also, we are dominating branch office and SMB because the users themselves could also be the owner and have to make sure the device has a good value and is easy to use. But, we are a little bit behind on the mid-enterprise because they often depend on marketing messages to make decisions… That's what's happening in the space because there are no FDA – or regulation or national testing … only a few customers do testing themselves, so everyone is trying to over-market each other… We are very successful in the technical buyer space: the carrier, education, big enterprise, and also the SMB and branch office and owner. Once we enhance the marketing and sales we will grow faster. Last quarter we grew 31 percent in the US enterprise, faster than any competitor. But, I feel the space is still noisy… Customers find it very confusing.

Fortinet has been criticized for under-investing in marketing – how do you look at marketing in security right now?
I think that's one way I feel – today you look in the security space and we have the highest percentage spending on marketing and sales in the industry. On average, companies spend more than 50 percent of their revenue on marketing and sales. For us, it's about 40 percent… It's crazy. I view the same situation like before the FDA regulated the health industry and the drug industry. At that time, if the drug industry tried to sell a drug, they were marketing it because the end user themselves has a difficult time to judge for themselves how good the drug is. It's the same thing for security. I think 99 percent of customers, it is difficult for them to test and they don't have the skill or the environment or the equipment to do the testing. They have to believe the marketing and the sales.

How has the competitive landscape for Fortinet changed?
It's starting to consolidate a bit right now. If you look maybe six years ago, the top six vendors in network security, now the top four account for about half the space right now: Cisco, Check Point, Palo Alto Networks, and Fortinet. Maybe there's still more consolidation going on. The four companies are about a similar size right now. Network security is still the biggest market in security. 10 years ago, it was endpoint security, that's how Symantec and McAfee play there… It will be interesting in the next few years. I think there will be a little bit more consolidation going on. Whoever has the better product and is best able to follow the change will be the most successful. Already, we see Cisco still struggle on the integration. They're now acquiring companies to play in the space. Check Point and Palo Alto Networks have the similar problem where they don't have software on the ASIC, on the chip level. Long term, they will suffer on the performance and the cost issue. We feel we have some advantage, therefore, in the long term. But, it also depends on some other factors like execution, marketing, sales. There's a lot that goes into it.
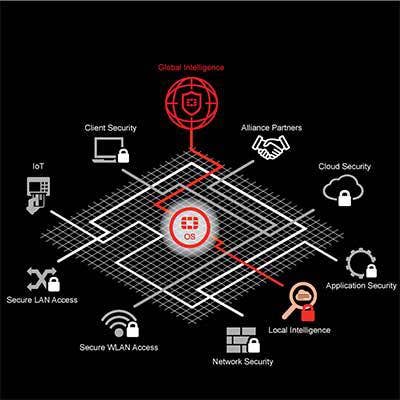
Talk about the Security Fabric – what do you see as the advantages of that approach?
In order to protect the data today, just to look on the network side is no longer enough. It has to be more broad than that… Before, there was a border. There was a trust. Now, that border is gone. We need to make sure that we can secure the data wherever it is, whether it's on the mobile device or in the cloud. At the same time, security still has to deal with a lot of things. It just happens so quickly, so to automate the process you need to make sure you don't slow down the infrastructure… We try to make sure they don't slow down performance and make it comfortable for the user… The third part is you need to automate because there are so many security threats out there and a lot of our reaction today from the time they break in to the time they steal the data might only take a few seconds. A human cannot react that quickly. You have to leverage a lot of automated technology and artificial intelligence to really detect it and take some action automatically.

How have you seen customers' security needs change?
When I started NetScreen, and then Fortinet, the security count of the total IT spend was only 2 to 3 percent. Now, it's over 10 percent and growing. We feel eventually, in another 10 to 20 years, it can grow to 30 percent or 40 or 50 percent… The reason security is getting a bigger and bigger percentage of IT spend because its usage – whether it's e-commerce or social media – has to look at the content. When we built Fortinet, we feel the next version of the Internet 2.0 will be more based on the content of the traffic and applications to deliver the traffic based on the user or mobile device. That's how network security needs to be today… Security needs a very intensive computation. If you can leverage the chip power technology, then that's going to have a huge performance boost and also lower the cost, and, at the same time, add additional capabilities for security.

What role do you see partners playing in the network security market?
We are 100-percent committed to the channel. We are a 100-percent channel company. We think the partner and channel partner and system integrators are very close to customers. They have the customer trust relationship. We can provide them the best technology product to do additional services. Security needs experts to really do the job. Most of the time customers don't have that expert knowledge to handle security issues. Leveraging the partner and leveraging the channel is the best way to build a better ecosystem there… Training, not only for the customer and the partner, but for the end user [is also important]. In this space, there is a big shortage of talent. We created a training program called Network Security Expert… now it has over 100,000 people certified and over 60 universities across the US working with us to offer the training material to their students, most at the graduate student level. It's the biggest training program in the whole industry… The program launched more than three years ago and has become the biggest in the industry… We offer all this for free to make sure people can understand the issues in the cybersecurity industry and also quickly lend themselves [to help].

How do you make sure you stay ahead of all of this and are keeping up with the trends?
That's where there are always new applications coming up. There's also the challenge of securing applications. That's where the constant battle is… That's where security has to step in and build on top of the architecture to protect all of this. Eventually, until the next generation of [the] Internet addresses a lot of these issues, the content, application, user device, and application security has to do the job. That's making security spending go higher and higher – so we all have job security. It's a pretty interesting space. There is so much – as we connect people, applications and devices together you get a lot of efficiency and new spaces like e-commerce. But on the other side the data has so much value inside there are also so many people that are trying to get the advantage and get the data to use in other ways. That's how security is trying to step in and protect the efficiency and also the data… We're all in a pretty exciting space. I've spent 25 years in the space and it's still exciting… The network connection enables so many new business models, but each business model just brings additional security data concerns…