Slammer Points Out Security Flaws
The SQL Slammer worm, also called Sapphire, targeted a known flaw in Microsoft SQL Server 2000 and clogged Net traffic as it searched for vulnerable systems. The vendor released a patch for the flaw in July.
"This just proves people aren't putting things in place. There have been advisories for some time, and they haven't taken notice of them," said Steve Crutchley, chief security officer at 4FrontSecurity, a consulting firm in Reston, Va. "It's like playing Russian roulette. They spin the chamber and cross their fingers they won't be hit."

\
Steve Crutchley; Slammer proves companies 'aren't putting things in place.'
Patrick Mueller, senior security analyst at Neohapsis, a Chicago-based security consulting firm, said he hopes the SQL worm will encourage companies to take a more proactive approach to security. "People just aren't motivated to keep their systems patched until something like [this happens]," he said.
"It's yet another problem that fits into the category of things we can avoid through good maintenance and configuration practices," said Paul Rohmeyer, COO of Icons, a security consulting firm in North Brunswick, N.J. "We'll use this as an example to explain to customers why they want to pay attention to good configuration management."
Slammer, which hit early on Jan. 25 and infected thousands of systems around the world, hit Southeast Asia especially hard. Two days later, the problem appeared to have dissipated and security solution providers said they were handling mop-up situations.
"There were some slowdowns and outages, but it wasn't catastrophic," Mueller said. The worm aggressively scanned for vulnerabilities, but otherwise its payload wasn't significant, he said.
But the worm affects the Microsoft SQL Server 2000 Desktop Engine (MSDE), which is included in many other Microsoft applications, such as Visio 2000 and Visual Studio .Net, Mueller said. That means it can infect laptops and workstations running those apps. "There will be continued fallout," Mueller said.
Slammer is actually very small,376 bytes,and very fast, which makes it different from the complex worms of the past two years, said Ed Skoudis, vice president of security strategy at Predictive Systems, a New York-based security services firm. "This little worm showed that small and fast can really win the race," he said.
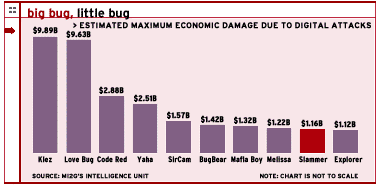
Researchers at the Intelligence Unit of London-based security firm mi2g estimated that the worldwide economic damage wreaked by Slammer totaled between $945 million and $1.16 billion. The worm caused ATMs to fail or slow down, disrupted five of the 13 DNS servers, disrupted airlines' online ticketing systems and credit-card services, and interfered with the phone systems of assorted emergency services, the firm said.
Slammer ranks as the ninth-most-destructive digital attack, or malware, on the mi2g Intelligence Unit's charts since 1995.
The worm showed the surprising number of SQL servers publicly accessible on the Internet and the inadequacy of current vulnerability management systems, Skoudis said.
There's a need for a comprehensive tool that assesses vulnerabilities and implements patches across multiple platforms, Rohmeyer said.
What's more, security specialists expect to see more malicious variations of Slammer in the future.
Successful attacks tend to produce copycats, but a high-profile attack often sends virus writers underground, said Vincent Weafer, senior director of Symantec's Security Response unit.
Because Slammer was a very short and intense event, lasting only about four to five hours, its damage paled in comparison to that of the Klez and Code Red worms, Weafer said. But the speed with which Slammer spread clearly indicates the need for emergency response planning within corporations, he said.