The 10 Hottest Cybersecurity Tools And Products Of 2023
Whether it’s with GenAI or “traditional” AI/ML technologies, security product launches this year have been dominated by advances in artificial intelligence and machine learning.

Cybersecurity Tools To Know
Here at the end of 2023, it’s clear that this was a breakout year for AI in cybersecurity. In the wake of the ChatGPT-induced explosion of generative AI technologies, just about every security vendor you’ve heard of — and countless others that you haven’t — touted new products and capabilities leveraging GenAI during the year. Those included some of the biggest cybersecurity companies such as Microsoft, CrowdStrike and SentinelOne, which have pointed to the potential for GenAI to help security teams get more productive and respond to threats faster.
Notably, though, it wasn’t just GenAI that played a role in powering the major new cybersecurity tools released in 2023. Many top vendors announced notable product updates this year that had more to do with “traditional” AI and machine learning than GenAI, such as Palo Alto Networks and its popular XSIAM offering.
In terms of running themes, many of the key cybersecurity tools launched in 2023 targeted the fast-growing security operations segment. Those included tools in hot product segments such as security information and event management (SIEM) and extended detection and response (XDR), from vendors including Cisco, Palo Alto Networks and Sophos.
For this post, CRN has selected 10 notable cybersecurity tools and products released in 2023 — most of which come from vendors that made their CEO or another top executive available to answer our questions about the products. (Note: We’re excluding cloud security tools, which we’re planning to focus on in an upcoming post.)
As we continue to track the new technologies that aim to help partners and customers to keep up with the latest threats, what follows are the key details on 10 of the hottest cybersecurity tools and products of 2023.
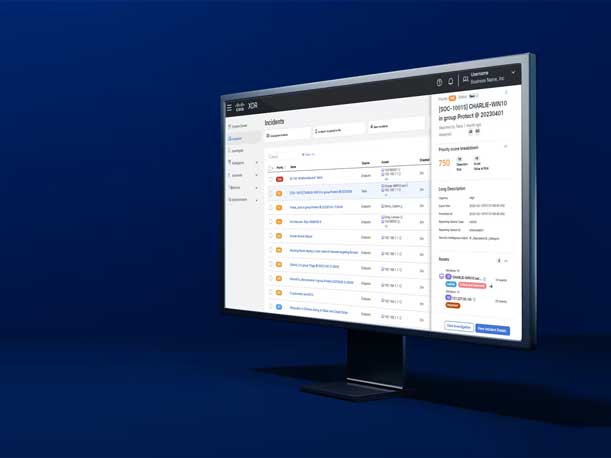
Cisco XDR
Cisco launched a new extended detection and response (XDR) platform that’s been built from the “ground up,” according to Jeetu Patel, executive vice president and general manager of security and collaboration at Cisco. The Cisco XDR platform fuses network detection and response (NDR) and endpoint detection and response (EDR), providing “cross-domain telemetry” in a way that no one else in the market is doing, Patel told CRN. The offering also stands out from security information and event management (SIEM) products by being “near real-time” when it comes to delivering threat detection and prioritization, he said.
In addition, Cisco XDR is differentiated by providing high-fidelity data from across the company’s various security tools, such as Cisco Secure Client for endpoint, he said. The XDR platform integrates a significant number of major third-party security products, as well — including EDR, email security, next-generation firewall, SIEM and NDR.
“This one is one of the biggest security product launches we’ve had in a while,” Patel said, and represents a major step on Cisco’s journey to fulfill its Security Cloud vision of providing a comprehensive, unified platform for modern security.
Looking ahead, Patel told CRN that Cisco’s planned $28 billion acquisition of Splunk will bring a huge influx of data and AI capabilities to the Cisco XDR platform.
“The thesis around Splunk is very simple — in order to be a world-class networking company, you also have to be a world-class security company. In order to be a world-class security company, you have to deal with these breaches at machine scale, not at human scale,” Patel said in a recent interview. “And in order to deal with [breaches] at machine scale, you have to be really good at AI. And you can’t be good at AI if you’re not good at data. And Splunk provides us a massive data platform.”

Securonix Unified Defense SIEM
Securonix unveiled a new SIEM platform that represents “the next wave of the journey that we have in our sim platform,” Securonix CEO Nayaki Nayyar told CRN. Securonix’s Unified Defense SIEM works with data feeds from Snowflake’s data lake, with the aim of better accommodating the massive volumes of security-relevant data that modern enterprises generate through a cloud-native approach. The platform can leverage 365 days worth of “hot” searchable data from the Snowflake Data Cloud, “which no other vendor does,” Nayyar said.
Doing so provides enhanced visibility into potential threats, and also offers a single-tier storage model that can support large-scale searches while eliminating many of the data management issues associated with a standard tiered-storage model, the company said.
Other key capabilities include Threat Content-as-a-Service, which features up-to-date content about the latest threats curated by Securonix, as well as a Threat Content Analyzer capability for helping to understand gaps in threat detection. The Unified Defense SIEM also enables proactive cyberdefense through capabilities such as Autonomous Threat Sweeper, which Securonix called the first product to retroactively look for indicators of compromise as well as adversary tactics, techniques and procedures, according to the company.
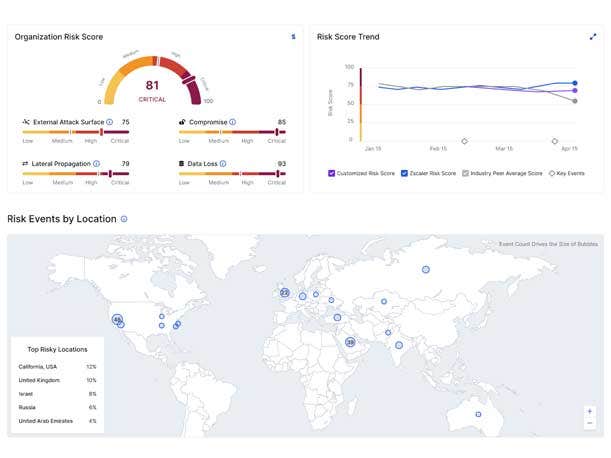
Zscaler Risk360
Zscaler unveiled Risk360, a tool for risk quantification and visualization that aims to help organizations make better — and faster — decisions about reducing their security risk. Zscaler founder and CEO Jay Chaudhry told CRN that the tool is a major step forward because it tells organizations what really matters in their security posture. The tool provides customers with an overall risk score for their entire company and across each of their key risk areas, he said, based on Zscaler’s troves of data.
Zscaler has “tons of these private logs — not to be generally made available — but we anonymously use all the logs to look at the threats,” Chaudhry said. “Because our customers actually happily share anonymized threats data, because it helps them, and because every customer benefits from it. So being able to predict and help them is a unique opportunity that we have.”
Users can utilize Risk360 to obtain risk scores, in real time, for different stages of a cyber incident and visualize risks across four key entities: the workforce, assets, applications and third parties. The framework also offers visualization and reporting capabilities, highlighting the biggest drivers of cyber risk and providing an estimate for financial exposure, Zscaler said. Additionally, Risk360 provides remediation recommendations and guided workflows to enable the most critical issues to be addressed promptly, the company said.

SentinelOne Purple AI
SentinelOne introduced its GenAI technology, Purple AI, originally as a threat hunting tool. Purple AI offers threat hunters the ability to use natural language to query a system, offering a massive time-savings and enabling security teams to respond to more alerts and catch more attacks, according to Ric Smith, chief product and technology officer at SentinelOne. More recently, SentinelOne has expanded Purple AI to cover additional use cases beyond threat hunting. For instance, the tool can now recommend queries and actions for a security analyst to help expedite the resolution of issues, Smith said. Additionally, analysts can use Purple AI “to drive investigations and ask it questions — and have it actually help you with the triage of a specific case,” he said. “All of that will be learned by Purple and then can be turned into a playbook, which can be used for automation if a similar case were to arise.”
Meanwhile, in addition to serving as a standalone tool, the GenAI technology that powers Purple AI has also been integrated throughout SentinelOne’s latest release of its Singularity platform, dubbed Unity. The technology now provides summarizations throughout the Singularity platform, which can help with contextual awareness, Smith said. “So if you’re looking at threat intel, it provides you with enrichment on that threat intel,” he said. “If you’re looking at a case and it has additional context, there will already be a summarization there to help you with the case.”
CrowdStrike Charlotte AI
CrowdStrike introduced its GenAI assistant for security analysts, Charlotte AI, which CrowdStrike co-founder and CEO George Kurtz said is “going to revolutionize security.” The biggest advancement with Charlotte is its ability to take a Security Operations Center Tier 1 analyst and “[turn] that person into a Tier 3 analyst,” Kurtz told CRN. The tool is going to be “taking their job duties, which may be eight hours a day, and allowing them to finish those eight hours in 10 minutes,” he said.
From what’s been shown so far by CrowdStrike, one of the big advantages for security analysts in using Charlotte AI is that the tool can not only present more data, but “more of the right data,” said Jordan Hildebrand, practice director for detection and response at World Wide Technology. Charlotte also would appear to be especially useful in areas such as threat hunting, which often falls by the wayside with prevention and incident response taking priority, he said.
Charlotte AI also “changes a security workflow from a point-and-click to a generative workflow,” Kurtz said. “[You can] have a conversation with Charlotte — ‘Tell me what the latest threats are? Tell me how that applies to my environment? Tell me the critical assets that they’re on? Generate a PowerShell script, which I can then deploy [as] a patch using Falcon Fusion — and then write a report at the end of the day.’ That would take somebody a whole day to do, that we could do in 10 minutes.”
Meanwhile, CrowdStrike’s latest release of its Falcon security platform, dubbed Raptor, also leverages the company’s Charlotte GenAI capabilities. The Raptor release adds the Charlotte AI Investigator, which can correlate related context around security incidents and provide GenAI-powered summaries of the incidents, the company said.
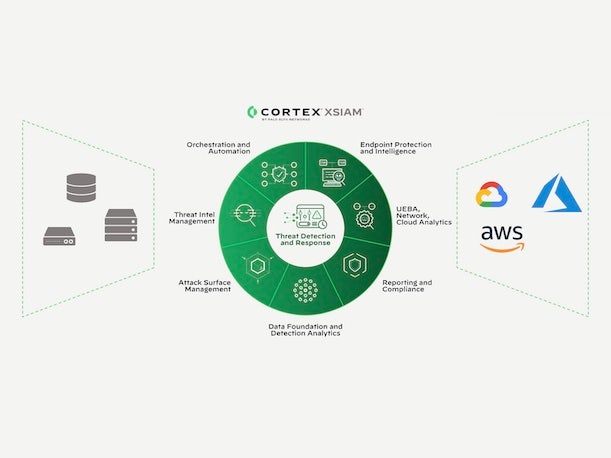
Palo Alto Networks XSIAM 2.0
Palo Alto Networks debuted the second generation of its AI-driven security operations offering, Cortex XSIAM, with improvements around the user experience and support for custom machine learning (ML) models. Originally released in October 2022, XSIAM (extended security intelligence and automation management) has been positioned by the company as a modern replacement for legacy SIEM (security information and event management) systems. With XSIAM 2.0, Palo Alto Networks “did not rewrite the product,” said Gonen Fink, senior vice president of Cortex products. “It was working very well, but we put in additional visibility to [show] what it’s doing for you.”
Key updates include the new XSIAM Command Center, which provides a single view of all activities within an organization’s Security Operations Center — from data ingestion and analytics to rule creation and alert detection, according to Fink. XSIAM Command Center also shows how detections are being grouped into incidents, as well as the automated response and remediation that is taking place to address those incidents, he said.
With the new MITRE ATT&CK Coverage Dashboard in XSIAM 2.0, meanwhile, Palo Alto Networks is providing visibility around how well a customer is covered against each of the different elements of the MITRE ATT&CK framework, Fink said. And in addition to showing how real-world protections are aligning to the framework, the new dashboard also helps customers to “for the first time understand what is in XSIAM,” he said.
XSIAM 2.0 also introduces the new capability to “Bring Your Own ML” to the platform, Palo Alto Networks said. That means that partners and customers are no longer required to replicate their data into another data lake in order to utilize their own custom ML models, the company said.
Tanium Autonomous Endpoint Management
Tanium unveiled its Autonomous Endpoint Management platform, which aims to bring a new level of automation to the work of both security and IT teams. The platform’s Autonomous Insights capability utilizes large language models to improve productivity, including through prioritizing risks using data on the importance of different assets. Autonomous Workflows, meanwhile, bring automation to the generation of workflows around endpoint management. And the platform’s Autonomous Remediation capability produces automated response actions that don’t require human intervention, Tanium said (though partners and customers have options around how much autonomy to give the system).
Tanium CEO Dan Streetman told CRN that Autonomous Endpoint Management is a major leap forward in terms of the ability of organizations to make security and IT decisions based on real-time information. For instance, “if I wanted to roll out a change, previously, and in any other system, first I’d have to go look up what the published impact of that change is and gather that. And that’s stale data already, because by the time it’s been compiled by somebody, it’s already old,” Streetman said. After that, an IT or security team would need to understand the operational impact of the rollout as well as the risk associated with vulnerabilities affecting the systems, he said.
Now, “we will compile all that into a confidence score,” Streetman said. “Then you can say, ‘Anything with a confidence score of X or above, go execute.’ And so our goal is to build our operators’ trust and our users’ trust in Tanium’s ability to deliver [Autonomous Endpoint Management] over time, so that they can increasingly take more and more steps that are supported by Tanium AI.”
ThreatLocker Ops
ThreatLocker announced its first-ever capabilities for detection of malicious activity in a move to help MSPs do even more to protect their end customers. The endpoint security company unveiled Ops, a new threat detection tool that aims to augment the capabilities of the 4,000 MSPs using its platform. Because ThreatLocker’s “application allowlisting” functionality ensures that malware cannot run in customer IT systems, the company hadn’t previously focused on detection of cyberattacks. However, ThreatLocker has recognized that even if it’s just an attempted cyberattack on an IT system, there is still value in being able to detect that activity, since it can often help an MSP to take other cyber defense measures for the customer that’s been targeted, co-founder and CEO Danny Jenkins told CRN.
And while ThreatLocker has already significantly displaced the need for using endpoint detection and response (EDR) solutions with application allowlisting and its other capabilities, the new Ops tool could displace even more usage of EDR by MSPs, Jenkins said. “I think the reliance on EDR is going to be massively reduced by using Ops,” he said.
Sophos XDR Updates
Sophos disclosed a suite of new endpoint security capabilities that will bolster its extended detection and response (XDR) platform, including a capability that the company called “adaptive active adversary protection.” The feature puts Sophos’ endpoint security tool into “breach mode” when it appears that a customer is under attack, said Joe Levy, president of Sophos Technology Group. The tool can then prevent an executable from running, for instance, or can prohibit a connection to a particular endpoint. The capability ultimately offers the ability to disrupt attacks that are in progress and “buy more time for responders,” Levy said.
More recently, Sophos rolled out support in its XDR platform for key products from 21 major technology vendors including competitors such as CrowdStrike, Fortinet and Palo Alto Networks. The Sophos XDR platform now has more than 75 third-party technology integrations, the company said.
Sophos also announced that its XDR platform now supports network detection and response (NDR), which can help with spotting malicious behavior on networks and other threats. The update makes NDR available as a standalone offering to customers, in contrast to just being available to managed detection and response (MDR) customers up until now, said Sophos Chief Product Officer Raja Patel.
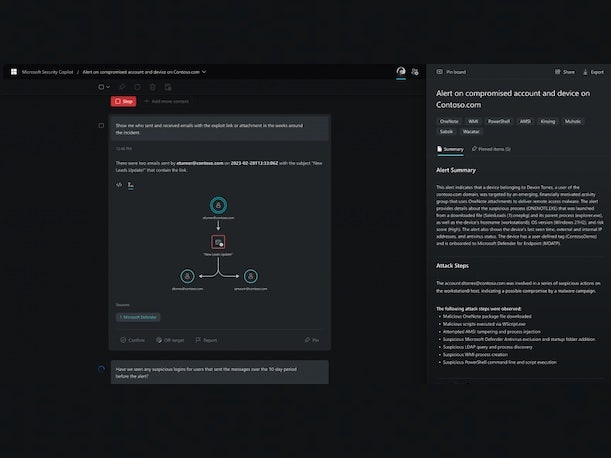
Microsoft Security Copilot
Microsoft unveiled its first GenAI-powered tool for cybersecurity professionals, Security Copilot. The tool tailors the generative AI technology toward cybersecurity by combining GPT-4 with Microsoft’s own security-focused AI model.
Microsoft Security Copilot features a prompt-based user interface akin to generative AI chatbots such as ChatGPT. When a cybersecurity professional gives a prompt to the application, the response will leverage Microsoft’s security-focused AI model “to deploy skills and queries” that are relevant to the prompt, wrote Vasu Jakkal, corporate vice president for security, compliance, identity and management at Microsoft, in a blog post.
“This is unique to a security use-case,” Jakkal wrote. “Our cyber-trained model adds a learning system to create and tune new skills. Security Copilot then can help catch what other approaches might miss and augment an analyst’s work. In a typical incident, this boost translates into gains in the quality of detection, speed of response and ability to strengthen security posture.”
Additionally, Microsoft announced a unified security operations platform that combines Security Copilot with its Sentinel and Defender XDR offerings. The platform will offer a unified incident experience for triaging, with a view of threats across the digital estate, according to Microsoft. Users will have a single set of automation rules and playbooks powered by GenAI and the ability to query all SIEM and XDR data in one place to find threats and take remediation actions, the company said.