Windows 11 Security: 10 Key Updates From Microsoft
With numerous improvements on security from Windows 10, the launch of Windows 11 is a ‘huge, huge win’ in the effort to secure customer environments, Microsoft’s director of OS security tells CRN.
Windows 11’s Biggest Security Updates
While Windows 11 brings an eye-catching new design and some handy productivity features, that’s not all that Microsoft changed in the new operating system, which entered general availability this week. For businesses, the even bigger updates are under the hood—particularly when it comes to security. Windows 11 is a “huge, huge win” on security because it sets a far stronger baseline through a number of adjustments, said David Weston, Microsoft’s director of OS and enterprise security, in an interview with CRN last week. Major security updates from Windows 10 include raising the TPM and CPU requirements and turning key security features on by default in Windows 11 without hobbling PC performance, Weston said.
Solution providers have told CRN that they agree Windows 11 is a massive step forward on security. “I’m able to know, walking into an environment with Windows 11, that the endpoints can be easily secured,” said Marc Menzies, president and CTO of Overview Technology Solutions, a Ronkonkoma, N.Y.-based Microsoft partner, in a previous interview with CRN. “It just makes it a heckuva lot easier to know what your baseline is, and that you can implement some of the security features that are really, at this point, fundamentals.”
Several of Microsoft’s security-focused changes in Windows 11 have been unpopular with some users, including the CPU requirements. But there, too, many solution providers have said they’re siding with Microsoft. “I’m fine with them prioritizing security over being able to roll this out to every computer,” Menzies said.
Using Windows 11 security features in combination on test devices—including device encryption, secure boot, virtualization-based security such as HVCI and Windows Hello facial recognition—reduced malware by 60 percent on those devices, according to Microsoft. Some of those features can only be enabled by default because of the TPM 2.0 requirement and higher CPU requirements for Windows 11, Weston said.
With Windows 11, “there was performance tuning, reliability tuning and compatibility tuning that made it possible for us to enable [certain security features] by default on the vast majority of its systems,” he said. “And that is the big difference between 11 and 10.”
At Altamonte Springs, Fla.-based managed services provider Blacktip, CEO Matthew Bookspan said it’s clear that Microsoft is “prioritizing security first” with Windows 11. “And I’d say that’s the prudent thing to do, given what’s going on in this environment,” Bookspan said in a previous interview with CRN.
What follows are 10 key updates from Microsoft on Windows 11 security.
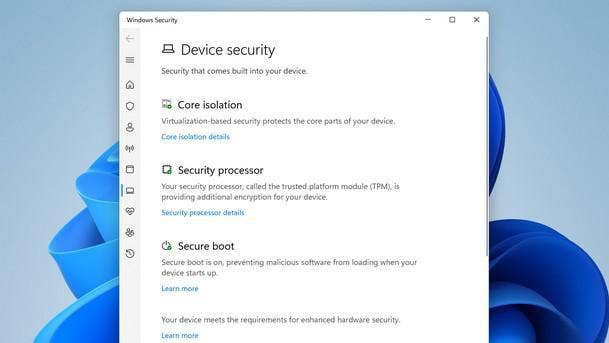
Security Features Running By Default
In Windows 10, powerful security features such as virtualization-based security (VBS) are optional and don’t run automatically—and have seen “very low usage” as a result, Weston told CRN. “The strategy for the initial release of Windows 11 is very simple: raise the baseline. Turn on the things that were optional in Windows 10 by default,” he said.
What Microsoft learned from Windows 10 is that “if you make things optional, people don’t turn them on,” Weston said. “They assume that if it was necessary, it would be on. And so I think that’s a big learning. What we put into 11 is [that] we are going to secure you by default.”
Getting VBS to be turned on by default in Windows 11 was not something Microsoft could do unilaterally—it required collaboration with chip makers to do this, Weston noted. “We spent many, many resources and hours on working with silicon partners to get it to the point where it’s on by default,” he said.
Other security features turned on by default in Windows 11 include secure boot, which blocks malware from loading during PC boot-up, along with BitLocker device encryption.
Windows 11 will enable solution providers “to do a good job consistently” for their customers because of the higher security baseline, said Menzies, of Overview Technology Solutions. With Windows 11, Microsoft’s approach on security is that “a rising tide raises all ships,” he said.
Hardware Security Focus
While security was a focus for past Windows releases as well, of course, the emphasis on tightening hardware security is much greater with Windows 11, industry analysts have told CRN.
“What I think is new is the recognition that it’s not just about fixing the OS, but rather looking at the entire stack from the hardware up through the applications and the user experience and trying to make the entire stack work better and more securely,” said Stephen Kleynhans, research vice president at Gartner, in an interview with CRN. “There are some things you need to do that you can’t do solely in the operating system, which needs the newer hardware.”
The security environment that Windows 11 is launching into has also changed dramatically in the six years since Windows 10 debuted, while Microsoft itself has been ensnared in some of the highest-profile cyberattacks. Those include the massive breach of the SolarWinds Orion network monitoring platform that was first revealed last December.
“Now, you have to prioritize security,” said Zach Saltzman, senior director for the Microsoft platform at Carlsbad, Calif.-based FMT Consultants. “It’s not like when Windows 10 came out when, sure, Microsoft talked about security. But they were just trying to get away from Windows 8.”
Since the new hardware requirements will prevent many PCs from installing Windows 11, the rollout of the operating system is highlighting a major shift in Microsoft’s strategy—with the company putting a higher priority on improving security than on enabling the most PC upgrades possible, solution providers and analysts have told CRN.

TPM 2.0
One of the notable (and much-discussed) new hardware requirements in Windows 11 is for a Trusted Platform Module (TPM) 2.0 security chip.
A TPM chip is used for carrying out cryptographic operations, and includes “multiple physical security mechanisms to make it tamper resistant,” Microsoft said in its documentation on TPM. “Malicious software is unable to tamper with the security functions of the TPM.”
Advantages of TPM include the ability to generate and store cryptographic keys, as well as enabling device authentication, the company said.
The security chip is necessary for enabling BitLocker encryption, which is turned on by default in Windows 11. BitLocker encrypts all data on a device, ensuring that the data cannot be accessed in the event the device is lost or stolen.
For solution providers, when every PC in a customer fleet has Windows 11, you can know that they’ll all have TPM 2.0, Menzies said—and thus can be “brought up to some level of security standard easily.”

Higher CPU Requirements
Whereas TPM 2.0 has been around since 2014, the CPUs that Microsoft is requiring for Windows 11 are largely those that have been made in the past four years.
The CPU requirements for upgrading to Windows 11 include—with just a few exceptions—having a processor from Intel’s eighth generation and newer, or AMD’s Zen 2 series and up.
Microsoft set its minimum CPU requirements at those generations because the chips enable several important security features to be turned on by default in the operating system, Weston said.
For instance, Intel’s eighth-gen chips and up support the use of virtualization-based security, while also providing optimal performance when automatically running VBS, he said. “The major demarcation line is security, performance and reliability,” Weston said.
A key part of the equation is a feature called mode-based execution control, which maintains performance while running certain VBS protections, he said.
Some earlier CPUs do support mode-based execution control, including Intel’s seventh-gen processors. But the seventh-gen chips are excluded because they don’t meet all of the performance and reliability requirements that Microsoft has for Windows 11, including for running VBS processes by default, Weston said.
In addition to mode-based execution control, Intel’s eighth-gen chips also ensure that TPM encryption and secure boot capabilities are present, Weston said.
“Some lower generations [of processors] also have those features, but then they are missing reliability and performance optimization,” he said.
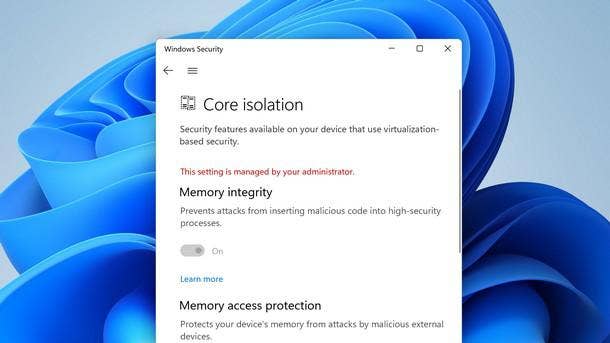
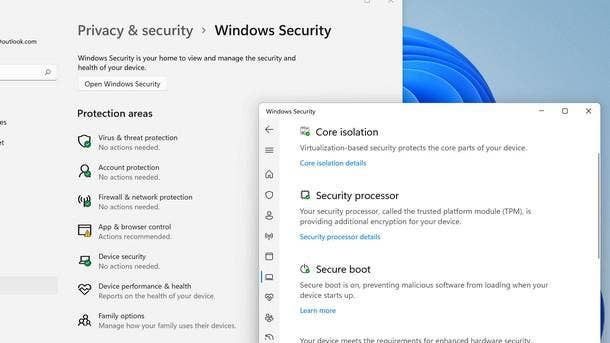
HVCI
Another part of the equation is hypervisor-protected code integrity, or HVCI. Virtualization-based security enables HVCI, also known as memory integrity, which disables any dynamic code that a hacker is trying to inject into the Windows kernel.
Mode-based execution control is a critical underpinning to the optimal use of HVCI. The feature is what ensures that running HVCI doesn’t deliver a major hit to performance and user experience.
HVCI can still work with processors that don’t support mode-based execution control—but those processors depend on an emulation of the feature, “which has a bigger impact on performance,” Microsoft said in July documentation about HVCI.
In short, support for mode-based execution control is one of the keys to why CPUs made in the past four years meet the Windows 11 requirements—and why older processors, which don’t support the feature or provide optimal performance for HVCI, are largely excluded from the list.
“Mode-based execution control is the target,” Weston said. “Virtualization-based security is what we need to secure folks. And [to do that] we needed a performant feature set.”
VBS works by creating a separate virtual machine that stores the most sensitive credentials and policies, which is isolated from the operating system.
“Even if someone gets admin-level privileges—the highest level of privilege—they still can’t read what’s in this separate VM,” Weston said. “It’s the exact same premise as how the cloud works today—you can be on a hardware machine with your bitterest rival, and you cannot read coded data across. We use that exact same technology shrunk down [for Windows 11].”
Container Isolation For Office, Edge
Another security feature that was available in Windows 10—but is now “better” in Windows 11—is providing container isolation for applications that are frequent targets for cyber attacks, Weston said. In Windows 11, commonly targeted Office applications (Word, Excel and PowerPoint) as well as the browser that Microsoft defaults to for opening links (Microsoft’s Edge browser) are run in separate, hypervisor-based containers, Weston said.
“That means even if that browser is compromised by a zero-day, it cannot mess with the host – there’s no access to the host,” he said.
With Windows 11, “there was performance tuning, reliability tuning and compatibility tuning that made it possible for us to enable that by default on the vast majority of its systems,” Weston said. “And that is the big difference between 11 and 10.”
Maintaining Performance Is Key
Turning certain security features on by default has required Microsoft to ensure that the features will not lead to a drag on performance—which is why mode-based execution control is a crucial piece of the equation. “If you turn something on by default, it better not be slow,” Weston said.
All in all, “I think folks are looking for this very binary decision [about the CPU requirements]. It’s actually a complicated engineering equation—where it’s like, ‘OK, so we turned on security, did performance tank?’” he said. “So, that is the focus.”
Ultimately, Microsoft looked at multiple considerations in combination to arrive at the minimum CPU requirements for Windows 11, he said.
“We could have chosen many lines,” Weston said. “But we used data analysis around reliability, performance and security to get there, and that is how we landed on that particular bar.”
The Windows 11 CPU requirements also ensure that most PCs running the operating system will have hardware protections against the Spectre and Meltdown processor vulnerabilities. However, hardware mitigations against Spectre and Meltdown were actually “not a significant factor” behind the CPU requirements for Windows 11, he said.
“From a feature perspective, there are two things that [Intel] eighth-gen and up really give us—and that is mode-based execution control, which is on the Intel platform as an optimization for virtualization. And then the assurance that TPM and secure boot are there,” Weston said.

Security For Unsupported PCs
Microsoft says that security updates will not be guaranteed for users that opt to install Windows 11 on an unsupported PC.
While Microsoft is not condoning methods for bypassing its minimum Windows 11 hardware requirements, the company is not forbidding these methods—such as using the Windows media creation tool—outright.
However, doing so could cause compatibility issues, while also posing a security risk in the future, Microsoft said on a support page posted this week.
“Devices that do not meet these system requirements will no longer be guaranteed to receive updates, including but not limited to security updates,” the company said on the page.

Zero Trust Security
With many workers shifted to hybrid and remote work, the job of securing a business has become much more difficult, Weston noted. In response, one of the goals with Windows 11 has been to make life easier for security teams through automatically turning on security features, Weston said.
“That can actually become the basis for a zero trust strategy—especially for Microsoft shops,” he said. “So [security professionals] can say, ‘Because these features are on, that should limit the funnel of things I need to care about. There are now more things prevented, which means I should have to do less chasing around and detecting.’”
A common scenario Microsoft has heard from customers is that “even if our detection is great, we don’t necessarily have enough human beings to go investigate everything and respond fast enough,” Weston said. “So Windows 11 helps with reducing that funnel.”
Additionally, since it’s possible to determine whether a PC has these features enabled, the security properties of a system can be measured “almost like a vaccination card,” he said.
An enterprise can therefore say, “show me your device security ‘vaccination card’ before I let you have access to the data,” Weston said. “We made that really easy with Windows 11. And that makes things like endpoint detection better because there’s less to look at. And the endpoint detection is harder to undermine because it’s starting from a very clean, high-integrity state.”

Future Updates
Another motivation for the hardware requirements with Windows 11 is to enable Microsoft to boost security even further in future releases of the operating system, according to Weston.
“A lot of this initial release of Windows 11 is not the end goal—it’s the first click stop on our journey. We’re saying, ‘we can now guarantee you have a TPM. That means I can go and make sure every app developer is now storing credentials and keys in hardware,’” he said. “I can’t do that on Windows 10 when just a percentage of folks have that. So it’s allowing me to set a baseline that I can now move the ecosystem to take full advantage of. And that’s a huge, huge win for us.”
What that means is that “more applications can support passwordless by default. More applications can do data encryption. More applications can have zero trust protections, because we’ve got that virtualization-based capability to report on their integrity,” Weston said. “What you’ll see in the following versions of Windows 11 is us exploiting that to a much better extent to increase security. So I think this is just the stage setting. This is act one. Act two and three, I think, are going to really bring some massive increases in security.”