AWS re:Inforce 2021: CISO Stephen Schmidt’s 10 Top Remarks
‘If we can cut down on flat-out human mistakes, we’ll be more than halfway to a more secure world,’Schmidt said during his keynote address for the security, identity and compliance conference.’

Investing in cloud security has never made more sense than it does in today’s environment where the ability to connect virtually, work online and quickly process and store information in a safe and secure manner is of paramount importance, according to Stephen Schmidt, Amazon Web Services’ chief information security officer.
“Many of the systems and tools that we’ve taken for granted in the pandemic might not have worked out so well as recently as five years ago, but the work that’s been done to improve cloud security has been incredible,” Schmidt said during his keynote address at AWS re:Inforce 2021.
New AWS CEO Adam Selipsky kicked off the virtual event, calling AWS security the cloud provider’s No. 1 priority.
“For us really, it’s actually called ‘job zero,’” Selipsky said. “Nothing is more important. If the right security isn’t in place for our customers, we don’t have an experience that works—we don’t have a business. This work could not be more fundamental or more mission-critical.”
With AWS, partners and customers can build on the “most secure global infrastructure,” knowing that they always own their data, including the ability to encrypt it, move it and manage retention, according to Selipsky.
“All data flowing across the AWS global network that interconnects to our data centers and our regions is automatically encrypted before it leaves our secured facilities,” he said. “We provide the broadest and the deepest security features and capabilities. And security continues to be a top area of investment for us, because that’s how critical it is both for our customers and for us. AWS is working as hard as we can to innovate quickly on security, but we still have a lot of invention in front of us.”
Here’s a look at Schmidt’s top remarks during his keynote, which covered topics including threat detection and response, ransomware, identity and access management (IAM), using “security guardians” and the general availability of AWS Backup Audit Manager, which allows users to audit and report on the compliance of their data protection policies to help meet their business and regulatory needs.

The ‘Quickest Way To A Corporate Network’
Risk is introduced from failing to define, learn and iterate. And that’s really what great threat detection is and the response is based on: the ability to know your normal, good state and react to anomalies quickly. Ideally, of course, your response is happening well before you’re aware of the problem.
When we’re considering threat detection and incident response, what’s changed over the past 18 months? Clearly, this is not a difficult question to answer, because we’ve all faced profound changes in the way that we work and live during COVID times. Maybe we’re used to getting together in physical spaces or sharing a coffee once a week with a peer, and now we’ve gotten completely virtual. Your meetings may all have been pushed online. Work is pulled more and more into personal devices the longer we’ve seen the work-from-home situations stretch on.
It’s also become really difficult to segment your workday activities by certain hours, because in a remote world, schedules shift around more fluidly. It could be childcare concerns have shifted work hours around, or maybe it’s just the new normal, when you’re handling most of your daily tasks in one physical place as opposed to having a clear line of demarcation around ‘these are work hours, and now I’m going home.’ This is one thing that I think everybody should very consciously examine: Do you have the right demarcation between your work life and your personal life? That demarcation is important to your health as an individual and your effectiveness as a security professional.
The numbers bear these trends out. Published surveys indicate a 114 percent increase in remote workers coupled with a 59 percent increase in bring-your-own-device policy adoption, and this has put security teams into places they may not be entirely comfortable operating in. This is a concern that went from a sort of a nice- to-have kind of situation to priority No. 1 in a matter of weeks.
As we think about threat detection and incident response, and what kind of tooling becomes more critical as employees interact across the disparate user interfaces on an ever-growing list of third-party applications, adversaries have certainly noticed this paradigm shift and are attempting to exploit the vulnerabilities that go along with it.
As Verizon indicated in one of their studies recently, mobile phishing attempts … increased by 364 percent in 2020 year over year. We are on our phones almost around the clock these days, and it’s quickly become apparent that the quickest way to a corporate network might be through a well-intentioned human being making a critical mistake and clicking on a link that they shouldn’t have. I think it’s an important point to remember.

Security Is ‘A Human Problem’
People often look at security as a technical problem. It is not. It is a human problem. It’s one where you have human adversaries who exploit human weaknesses to get access to the products of humans in the form of data.
[Schmidt referred to a text that an AWS employee recently received on a personal device. The text warned that the employee’s Amazon account would be disabled and included a phishing link with a URL that indicated it wasn’t a legitimate message.]
Of course, with good training and hygiene, none of your employees should be clicking this link. But someone out there is, or else these types of really low-sophistication methods wouldn’t even be attempted.
In a security-conscious environment, your staff should see only red flags here. Who is cutting off my access? Is this normal behavior? Why have we never seen this phone number before? Is there someone I should ask about this before making this decision? That piece is key. Do they know who to go to and say, ‘Hmm, this doesn’t look right. Have I been trained in how mobile phishing works?’ Because right now, many of the world’s mistakes are coming from unforced errors. This is not supervillain activity or ninjas scaling down from rooftops, this is basic errors. If we can cut down on flat-out human mistakes, we’ll be more than halfway to a more secure world.
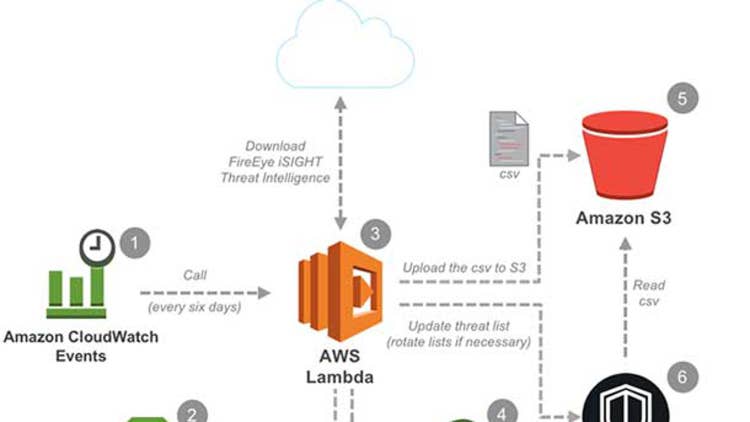
Amazon GuardDuty And Machine Learning
Machine learning (ML) is one of those marketing terms that you’ll hear thrown out as shorthand for’‘really techie and complicated and whiz bang.’ It’s kind of like, ‘Oh, yeah, this is machine learning, so you should trust us that it’s impressive.’
But in the case of [Amazon] GuardDuty [AWS’ continuous security monitoring service], it’s actually pretty simple to define and understand. What we’re talking about here is things like domain reputation models based on behavioral characteristics. That’s one of the elements that goes into GuardDuty alerting. This matters in a real-world scenario, when one of your EC2 instances starts communicating with a domain that’s predicted to be malicious because you will see an alert.
This is where we can use the power of scale to deliver better security results. Based on all the domains that we’re aware of, we can build intelligent models that can very clearly see, ‘Well, this domain is not acting like the rest of our nice normal domain crowd,’ and you get an alert, so then your high-judgment humans can take a look. Now maybe there’s a good reason why this net new domain is interacting with your EC2 instance. Maybe everything’s completely safe, and you’ll note it as such, and then our model gets one more data point for the next time around. The model improves with additional data points, and the model is being leveraged or looking at the things that you would logically expect: domain popularity and history or association with known crypto-mining IPs and things like that.
What does this mean in the real world? It means that because of the ML work that GuardDuty has in place, that our customers will see a four- to six-week head start in protecting themselves against certain activities when compared to traditional threat intelligence platforms. There’s no new action to turn these additions on to our threat library. There’s no additional cost. We report to you on anomalous behavior [and] let you make the call from there.

‘What You Can Do Today’
My favorite part of these talks is always sort of what are the things that you can do today? What are the things you can take home and action, both tactically and strategically? Well, first off, don’t plan your security program around competing with bad actors in real time. I urge you: Don’t do that. Because in the time it takes you to determine you have an issue, figure out who should be involved and begin your process of figuring out what’s broken, that’s a pretty lengthy period where you are not stopping the bad guy, you’re not stopping the exploits.
You do not want an airbag in a car to deploy after a crash, when the car is safe. You want the airbag to deploy during the accident itself, and your computer security processes should be no different—which means turning on Amazon GuardDuty to start here and now. Reduce your remediation and recovery time, and put yourself on the path to automated remediation by tying in Amazon CloudWatch Events and AWS Lambda, meaning the chain goes something more like this: Something happens, GuardDuty detects and alerts on it, auto remediation using Lambda occurs. Then you start your ‘What happened here?’ meetings. All of your AWS user and API activity, your S3 data events, your network traffic data through Amazon VPC Flow Logs—all of this can operate under a much more comfortable blanket of auto remediation. A real-life example here would be an outbound communication to a known malicious IP address that gets noted and logged and shut down automatically—the results delivered to you on a silver-plated security platter.

Ransomware
This is a big topic right now. It gets headlines routinely. What’s interesting about this topic is it’s not new in terms of presenting us with some magical new type of vulnerabilities. An exploit in your system or a failure in your human processes is still an issue no matter what happens afterwards. If you have a malicious insider with the wrong access levels, throughout technology history, they can do a lot of damage to you. What’s new here is the idea that whoever is infiltrating doesn’t actually even need to have access to the data itself to cause harm.
Let’s say you’ve got a great data protection plan: super crisp and well-thought out; encryption everywhere it needs to be; segregated key management, so one identity can’t get to the other identity’s keys; critical intellectual property is stored in a matter that takes multiple users to access—the works. Well, the person on the other end of the line holding your system hostage doesn’t care about any of that, because they precluded you from operating your business. They aren’t necessarily even threatening your business with ‘We’ll sell these credit cards on the dark web.’ What they’re saying is, ‘Hey, if you pay us, you get your access back and can operate again. Until then, you can’t.’
Businesses are more willing to pay this type of ransom because they’re losing money for every second they are down, which makes this new in the sense that it leans more heavily on business resiliency methods—you do have a system that, if hijacked, you can get back to known good rapidly. And so our guidance for ransomware, which actually dovetails pretty nicely with traditional remedies, is overall prevention is far, far better than having to deal with it in real time.
If you want to dive really deeply into prevention ideas around this topic, you can reference something like NIST [Special Publication] 1800-25, which is going to go much deeper into asset management and policies and logging and backups and blacklisting and so on.
But what I want to get into right now is some easy stuff that’s on your to-do list for right now—the basic stuff, like separation of duties. If no one user has the right to lock you out of all of your systems, it‘s going to be tougher for the ransomware actor to get to that point. Your operational accounts and backup accounts should be owned by different identities. That is just security hygiene. And please don’t save the authentication credentials for those identities in the same place.
There are publicly available self-assessment toolkits for AWS, which will run you through the checks that look for public access enablement or IAM roles that haven’t been used in a few months or [Amazon Elastic Block Store] volumes where you don’t have a snapshot saved. You can use a tool like S3 object log to make sure that someone can’t exfiltrate your data, delete your copy and then charge you to get it back. With S3 Versioning feature, you can preserve, retrieve and restore every version of an object stored in your buckets, meaning recovery from both unintended user actions—because let’s face it, your administrators occasionally say ‘Oops’ and make a mistake—and application failure is a smaller lift. With just a bit of rigor, you’ve got an environment where folks can’t delete, where you can restore from backup easily, and where your backup has the ability to start your business up again quickly.
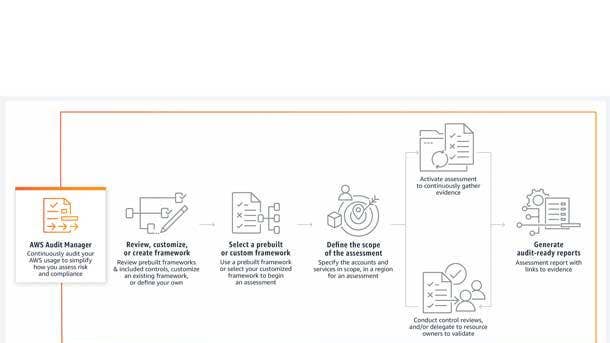
AWS Backup Audit Manager Now GA
AWS Backup Audit Manager is launching with general availability.
This is a great way to provide yourself with additional protections against your data being held ransom. This is also meant to massively simplify data governance management of your backups, because Audit Manager automatically tracks your backup activities and detects when you drift from defined parameters, enabling you to take quick corrective actions. And this kind of concept really rolls up as well. If the resources evaluated by a backup audit manager control are compliant, it reports as such. Similarly, if all the controls in a framework are compliant, then you’re provided with that assurance and reporting as well.
I’d also encourage you, once you’ve got a comprehensive backup plan, to test it. Run a game day. See if you are able to restore and validate that backup as working precisely how you want it. Do not let an incident be the first time you were taking a look at this type of tooling. Making backups is a great first step, but have a runbook around regular testing of recovery as well. My guess here is that we’re headed towards a future where the validation of the backup-and-recovery process is implicitly regulated. And we could quite well see cyber-insurers require this level of rigor shortly thereafter.

Identity And Access Management
IAM is such a critical aspect of a security strategy because it’s the basis for everything.
In a meeting, everyone is going to say, ‘Well, of course, we should have fine-grained permissions and least privilege.’ That’s a nice conversation topic because the correct way is usually so clear and so obvious, but then real life is going to intercede. You are going to get busy. You’re going to think about cutting a few corners, and you’re going to end up with a less effective IAM program as result. And we really, really don’t want that.
As we consider IAM, know that it is still a place where you can pick up huge security wins right now. Today’s action can pay immediate dividends. The reason the potential winds here are so prevalent is … this muddling of work and home resources.
Here’s some stats that should give you enough data points to see how important this topic is. Four out of every five security incidents occur due to weak credentials. A third of employees are sharing their work materials via personal email providers. Another third has the exact same password across all their devices, allowing for one-stop shopping for adversaries. If a password for … your hotel loyalty card gets leaked, but that’s also the password used for your corporate resources, that takes the concern level from minimal to massive very quickly. Plus, almost half of employees are using their personal devices for work purposes, whether it’s calendaring or chat or email.
Forty-two percent of employers haven’t secured their remote employees’ personal devices. Broad access to sensitive items—that is a recipe for a bad day, whether it’s in the cloud or on-premises or anywhere else. With a permissive identity and access policy, you’ve created the environment a bad actor needs to be successful because they can easily find a personal password that you use for a website that may not even be around anymore and try that out against your corporate resources, gain access, use that access, assume an identity and then look around for valuable information. There are always multiple failure points in any accident. It takes many things falling over to get to the point where you’re having tense meetings with your team. Don’t let access and identity be one of those things.

IAM Tips
With IAM, right from the start, you can do things like setting work hours. No one can log in at 2 a.m. from Australia to your business in Des Moines, Iowa. You can restrict services as well. You can require multifactor authentication, meaning, ‘I not only need this password that I’ve remembered, but I need this physical hardware device to be able to log into a particular application or set of infrastructure components. And if someone steals one of my people’s laptops, I want them to have to go past two different access-control systems at least in order to get access to anything that’s interesting.’ That slows down the adversary’s progress and gives us, as defenders, more time to react.
Credentialing contractors for a certain period … and doing that work right up front and higher, so I’m not scrambling around wondering if anyone that’s left at the company holds a grudge—that kind of thing is where you need to build the right muscle memory by repeatable processes and building your identity and access management frameworks to last for the long run. All of this works within the framework of existing identity systems such as Microsoft Active Directory. Again, we’re looking to do the right thing for customers here to help you stay secure, regardless of what tooling you choose to use.
Put on your calendar to review permissions on a regular cadence—monthly, quarterly, you decide, but have a regular idea of who needs access to what and revalidate it on a periodic schedule. Now, of course, the better thing to do really is to automate this process, where you prompt your managers to say, ‘Do these people still need access? Yes or no, if not revoke that access.’ And if you pull a report that says this user type hasn’t accessed the system in 60 days, remove that set of permissions. If an employee doesn’t need access to something, why are you expanding your risk profile?
This is a place to consider how the work is evolving, too. Maybe now credit card numbers are being accepted by your business, and you need an entirely new permissions group to handle that. Don’t have a security program where you are bolting on permissions as the business grows thinking, ‘Well, this is close enough to what they do.’ No, no, no.
If your business is changing, if you’re heading to a new country or a new vertical, that’s awesome—you‘re opening up for new streams of revenue. With that, though, comes re-evaluating your security needs each and every time. This should be put on a regular schedule so that it becomes a normal behavior. This will lead to your employee base being more curious and aware on their own. And next time a new line of business is opening, your partners in operations are going to approach you and the security team prior to launching something. You’re going to get closer to the inception of all the areas that need foundational security if you show that you’re a diligent partner throughout that process.
Use groups for IAM policies. It’s a really simple concept, easy to execute. You can have a user group called ‘senior associates.’ Give that user group the type of permissions that your senior associates typically need. If you promote or hire a new senior associate, you add them to the group. Now if a person changes jobs in your organization, instead of editing all of that individual user’s permissions one by one, you can remove them from the old user groups and move them to the new, appropriate user groups. After that, each IAM identity can be associated with one or more policies. Policies determine what actions a user can take: a role [that] a member of user group can perform and on which AWS resources and under which conditions as well. Now you’ve got a reasonable and agile identity management platform to run with.
And finally, within that plan, be granular. Don’t just take everything your business does and throw it into an ops bucket and call it good. That is the easy way out, and it is probably the wrong thing to do. You never want security to be a ‘department of no,’ so ideally, set this up correctly from the beginning. You, as a security practitioner, want to have people banging on your door, saying, ‘Hey, I need this access to do my job’ No, that isn‘t the best use case, it’s not the best use of your time, and it’s not the best user experience. But that is a lot better than, ‘Oh wait, Jenny had access to what database and what credentials were taken?’ So build the framework, make it easy to use, audit it regularly, confine user access to that which is just what’s needed.

Networking Infrastructure Security And The Supply Chain
This is clearly a biggie where cloud is concerned because large portions of this are controls that we can set up for you on our side of the shared responsibility model, and you don’t have to do the heavy lifting associated with it.
We want to handle the items that are a hassle for your business. You shouldn’t want to build a data center if we are doing our job properly. And we never want security to get in the way of running your core business. The spirit of AWS is one of customer obsession, making security easy for you. There are certain aspects of the equation we should be better equipped to handle given our expertise. One of them is supply chain. We have decades of logistical experience in getting things safely and securely from one place to the next. We have decades of experience in sourcing from suppliers who have been vetted, audited and verified.
There’s a trend of elevated risk among certain supply chains and suppliers, and truly there’s not enough human judgment to cover the expanding risk profile across the industry. As we’ve seen in recent headlines, if an adversary can get into your supply chain, they can potentially operate in a manner that’s going to weaken your overall security. Now, clearly, you should still have checks that identify the risk to your business throughout its particular life cycle, but we’re proud of our efforts here.
We’re proud to say we attest to a level of supply chain controls that allow you to operate with confidence in the cloud, knowing that the broad set of materials that make up our cloud have been thoughtfully considered and checked throughout each step of our boot process. Our goal here is to make the teeter-totter longer to give you leverage, taking more responsibility when we’re able. We’ve made inroads down the supply chain, so that we own more of the process, and the results are surfaced in the end products that you see. In this particular paradigm, the heavy lifting and supplies—building things—are work that’s best left to us.

‘Security Guardians’
I’d also like to take a quick moment to recommend an operational program that we’re seeing tangible results from internally. We all know that security can’t be only the job of your security team, and that truly maintaining a culture of good security hygiene is going to take buy-in from everyone within your business.
This brings me to the concept of ‘security guardians,’ or I’ve also seen it called ‘security champions.’ Essentially, this is a group of people that sit outside the security organization, but who volunteer to help maintain certain best practices within their individual teams. Embedding security champions within your business, and giving them a seat at the table as to how security and their group can work better together within the framework of the business, can really provide huge value. I’d encourage you to consider starting this type of program internally, and we’ll be sharing more about this program at re:Invent in a few months.