IBM CEO Arvind Krishna: 10 Boldest Statements From CRN’s Exclusive Interview
IBM CEO Arvind Krishna, who will celebrate his first year at the helm of the 110-year old company on April 6, sounded off on everything from the blockbuster SolarWinds breach, IBM’s Red Hat share gains and why IBM’s AI is more ‘trusted’ than any other company.

Capturing The Trillion-Dollar Hybrid Cloud Opportunity
IBM CEO Arvind Krishna has his sights set on making IBM and its partners the No. 1 provider of hybrid cloud and AI in what he calls a trillion-dollar market opportunity.
“I want our partners to be the best at establishing a hybrid cloud architecture and an AI footprint at our clients,” said Krishna in an exclusive interview with CRN. “Look at the market opportunity. If I look at that intersection, let‘s just call it a trillion-dollar addressable market.”
IBM is investing $1 billion in “rapidly expanding” its partner ecosystem as it sharpens its focus on hybrid cloud and artificial intelligence AI, said Krishna. “To accelerate consumption of our hybrid cloud platform, we are also rapidly expanding our ecosystem by adding hundreds of new partnerships with global systems integrators, independent software vendors and major third-party software partners, and also elevating the role of partners,” said Krishna. “We are investing $1 billon in our ecosystem so that our partners can play a much bigger role in fulfilling the many needs of our clients.”
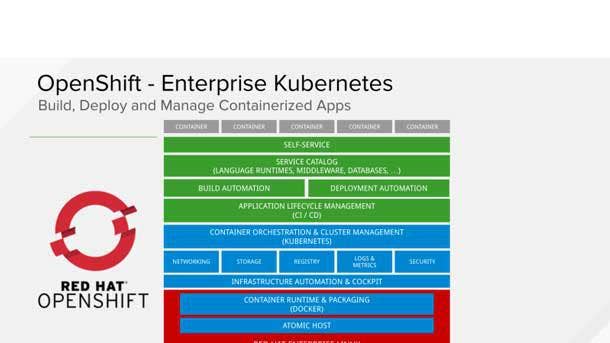
Krishna said his “maniacal focus” on hybrid cloud is focused squarely on the Red Hat OpenShift platform. “You have to have an architecture with which you‘re going to go do this,” he said. “If you don’t have an architecture you’re just doing ad hoc services. So we begin by saying the hybrid cloud platform, aka Red Hat OpenShift, is at the heart of what we want to do.”
That commitment to OpenShift has resulted in IBM putting its onetime proprietary software on top of OpenShift with IBM Cloud Pak for Data, IBM Cloud Pak For Business Automation, IBM Cloud Pak For Watson AIOps, IBM Cloud Pak For Integration, IBM Cloud Pak For Network Automation, IBM Cloud Pak For Security and IBM Cloud Pak System.
Krishna said Red Hat OpenShift is flat out the best architecture for a Kubernetes-based container platform on-premises or in a public cloud. That architecture, he said, provides a “massive advantage” for partners and their customers.
The goal, Krishna said, is for IBM to double its revenue with partners over the next three to five years. “I want our partners to be the best at establishing a hybrid architecture at our clients and establishing an AI footprint at our clients,” he said.

The SolarWinds Attack
I don‘t want to get deep into SolarWinds. Let me just put it this way: First of all, I feel sorry for them because it was a really sophisticated and a vicious attack. It went on over a long period of time. So, to the best of our knowledge, we were not impacted. I’ll just leave it at that.
Do we all have to do a lot of work? You always should be paranoid. You always should be very, very careful. Now that said, we have done secure engineering practices for multiple decades.
You’ve got to make sure that your code supply chain is really, really secure. Because when you are a provider to banks and governments and health-care providers, you don‘t want to be the source of carrying infections and malware and all those things in there.
Secure engineering practices are well known. It gets into all kinds of practices around code signing and encryption, not just of data but of actually how you build your code. You have got to be careful of what components are brought in.
There are some products that in turn have 30,000 other packages embedded in them. Now, whenever something happens, you‘ve got to grab the latest version of one of those packages and put it in there. So you’ve got to have the discipline to make sure that you’re not getting lazy and letting something filter in.
The way a classic threat functions [is the bad actors] wait for the one open door or window, and they use that and then they have access to the whole building. That‘s exactly what happened here.
Secure engineering practices are fundamental to us [at IBM]. It‘s how we build our mainframe. It’s how we build our software. It’s how we build Linux. So you’ve got to go do that. And we work very deeply, by the way, with all of the agencies, both government and private sector, who do these things to try to make sure they stay ahead of it, and stay ahead of the vulnerabilities.

Cybersecurity: The Biggest Issue Of The Next Two Decades
[Cybersecurity is] a massive investment, by the way. If I took away that investment I would probably add multiple points to IBM‘s bottom line. But I would be then afraid that if something happens maybe he whole business goes away. So, it’s a huge cost of doing business. I think cybersecurity is going to be the biggest issue of the next two decades.
The world goes through these phases around what is valuable. So, why did people fight physical wars? You fought physical wars because you wanted land and the factories, the land to grow crops and maybe by the World War II you wanted the economic benefit of the factories and the people. Today, that‘s irrelevant. What you want is that IP and the data.
So you don‘t fight physical wars anymore. You fight cybersecurity wars. So if that’s the case, we all have to step up. We all spend money on policing. We all spend money on locks and gates and doors. You’re going to have to spend a lot more on cybersecurity because all that other stuff is not that important anymore.
We have one of the biggest security businesses when you look at our combined software and services. We intend to keep investing in that. I see a lot of opportunity for growth in there for us.

IBM’s New Customer Segmentation: The Biggest Change In 30 Years
I think it is the biggest change we have made in our go-to-market in my living memory. If you think about how we pay our people and how we have got clarity on the partners, it is the single biggest change in 30 years on the go to market. It is massive.
It comes from a recognition and an observation. The world is moving really fast. So let‘s recognize that. Just bringing the knowledge of a product to a customer no longer has got a lot of value. They can read that on the website. Everybody has Googled who you are and what is your product and your capability before you enter the room. So what used to be of value 30 years ago is no longer of value.
Today what [customers] want is for you to show them how it works in their environment. That‘s is what is of value. That means you’ve got to embrace the bigger ecosystem because they’re the people who will do that. And so we [at IBM] should turn into enablers of those people, as opposed to trying to be a big frontline by ourselves directly, all the time. The world evolves and you have got to go along with that evolution.
Red Hat Share Gains: Linux, Ansible And OpenShift
The IT market is growing roughly speaking 5 [percent] or 6 percent. 2020 was not going to be 5 [percent] or 6percent with COVID-19. But let’s take the long-term view that it grows at 3 [percent] to 6 percent. Red Hat was doing about 12 [percent] or 13 percent growth before we acquired them in 2017 or early 2018. The last few quarters revenue growth has climbed up to 17 [percent] or 18 percent [growth] and bookings growth has climbed up into the 20s.
That means by definition we are taking share. You can say from whom are you taking share, Red Hat? One is that Linux is going to win over all other operating systems. There is obvious share there. The second is there is an automation platform called Ansible, which I think is the best automation platform for doing lots of routine scripted tasks. I think there is a lot of share to be taken there. From whom? Actually I don‘t think it’s from anybody. I think it’s from homegrown script kiddies. That’s great because you are not actually competing with anybody out there.
You can guess who all the other operating systems are out there. That share is going from them to Linux. Within Linux I think Red Hat gets more than its fair share of operating systems.
The third category is the hybrid cloud platform. The product there is Red Hat OpenShift. I think Red Hat OpenShift has the leading position in container Kubernetes platforms. There the numbers are clear. We‘ve gone from 800 to 2,600 clients. So that means you are taking share.

Running Fast To Stay Ahead With Kubernetes: The StackRox Acquisition
Once people realized there was a container Kubernetes platform, everyone and their brother came out with their own version of one. This is a question of running fast. Normally in this technology world where you have a lead and you‘re willing to invest and you’re willing to have a good product, and you’re willing to put the sales and distribution behind it and get it deployed, then you can keep your lead and keep growing. And that is why, for example, we announced that we were buying StackRox because that now layers in security as well.
So not only did we appeal to developers that this is the best-to-use platform to build new applications. You can now say it‘s more secure, and you’re coupling it to other services. You can expect that movie to keep going on and on and on.

Red Hat OpenShift: ‘The Heart Of What We Want To Do’
If I begin with the basic story of why I have a maniacal focus on hybrid cloud, it’s because you have to have an architecture which you‘re going to go do this.
If you don‘t have an architecture you’re just doing ad hoc services. So we begin by saying the hybrid cloud platform, aka Red Hat OpenShift, is at the heart of what we want to do. We have taken our software—I would call it proprietary, it’s not open source, unlike OpenShift—and we have put them on top of OpenShift.
So the Cloud Pak for Data, the Cloud Pak for Automation, the Cloud Pak for Applications, they all run on OpenShift. That includes by the way things like Maximo [enterprise asset management software]. As they run on OpenShift that is now a very consistent deployment layer.
So we can deploy on the IBM Cloud. We can deploy it inside a data center. We can deploy on Azure. We can deploy on AWS. So the software can instantiate stuff everywhere.
We put Watson on OpenShift [too]. So you can take it wherever you want to. We are not going to prohibit that. Anywhere you can run OpenShift you can run the Watson capabilities. That is a huge advantage to us in terms of opening up the aperture of all of IBM and also making us a lot easier and friendlier to work with.
This is not just taking the software in like a virtual world and just wrapping it up with a bow and a tie and putting it there. It means when you do this you worry about scaling. You worry about elasticity. You worry about disaster recovery. All of that is capability you bring in that takes costs and complexity out at the end of the road.

IBM’s IT Automation Advantage: A Call To Action
Look at our automation and go get familiar with Cloud Pak for Automation and our Watson AI Ops portfolio …. They happen to run on Red Hat OpenShift, but that’s like saying they run on Red Hat Linux. Of course they do. What that gives you is you get a little familiar with containers and Kubernetes because it converts what used to be 100 units of complexity in standing up all of that stuff and running it and makes it just 20 units of complexity.
So you can pour all that energy into giving your client value on top of that. So learn how our RPA [Robotics Process Automation] works, learn how our integrations works, learn how our AIOps can bring value to a client and go get all of that done.
So what will we do around it? We have got to invest in the certifications. We have got to invest in the sales training. Then we’ve got to invest in how do I lead pass with you? Where do you want to be? How do I co-market with you? How do I bring you into my events? So that you can get those leads and it looks like we are endorsing you. By the way if you run into trouble in an actual implementation, we want to help. … We will put some experts on it to help you through it so that you succeed. Not for money. Just for you to succeed.

IBM Analytics Intellectual Property Advantage: The Hidden Secret
The hidden secret has been that 80 percent of the money and 80 percent of the problem still lies in collecting and cleansing all the data. Actually doing analytics or AI is that final 20 percent.
It begins with Cloud Pak for Data.
It runs on OpenShift. Then you can go ahead and do that, deploy it, work with us. We’ll help you with training. We’ll help you with certification. We’ll do lead passing. We’ll work with you. We are happy to bring you into our events. By the way call on us for help, By the way those last two things we never did in the past.

Watson Studio: IBM’s AI Data Pledge
We have Watson Studio. You can use that as a partner to construct with your own expertise an AI model—a machine learning or deep learning model.
If you use it for a call center, you build the models, do all the hard work, create it using my questions and answers. Then we are one up. We build a solution that knows how to do, let’s call it chat- based questions and answers. Now you as the partner have to create it with what is the intention of what the customer is doing. The secret sauce is the answers. That is yours. We are never going to ask you for that. That is yours. That is between you and your client.
We have actually built out Watson to be used to build the models completely as an AI platform or for a few verticals like call centers, email, etc.
We are not asking you for all the data and all the training. That is yours. You can keep it. We are never going to suck it back from you. I can look you in the eye and say, ‘Our AI is more trusted than anybody else because I am not taking your data. I will give you a hard commit. I am not going to learn from your data. I am not going to take what you might do at Joe’s Plumbing and then I’ll take it and then give it to Sam’s Plumbing.’

The Size Of The Hybrid Cloud Platform Opportunity
Mainframe was a platform and a lot of people made a lot of money on it, including a lot of partners. Our middleware stack was a platform and a lot of people made a lot of money on things like WebSphere, DB2 and Informix. If we made tens of billions of dollars, partners made hundreds of millions in aggregate over the decades.
I would like to see our hybrid cloud platform be as big or bigger than any of those. If you take the mainframe, by the way, over its 50 years, that‘s hundreds of billions. You could debate whether it’s trillions. I would like to see our hybrid cloud platform be that big and that sustainable. That means sustainable for decades, not just for a few years. That is my vision for us and our partners together.
I would like to see in a short number of years, we can debate whether it‘s three years or five years, I would like to see our revenue with our partners double, to put a simple number on it, which means their revenue doubles. That’s what I’d like to see in three to five years.