The CRN Test Center's 2014 Products Of The Year

The Best Of The Bunch
The high-tech industry continues to thrive, and 2014 has seen no shortage of breakthroughs. As we predicted in 2012, technological leaps such as Intel's 3-D transistor laid the foundation for advances years into the future. Technologies of today -- many of which incorporate Intel's groundbreaking technologies -- form an interwoven mesh of sophisticated servers hosting virtualized systems for access by rugged and powerful mobile devices run by workers seeking data systems stored, executed and backed up in the cloud. Here are the CRN Test Center's selections for Products of the Year and Honorable Mentions, based on its reviews throughout 2014.
Be sure to check out the rest of CRN's 2014 year-end coverage.

Cloud
Winner: nCryptedCloud Enterprise
For the enterprise attempting to eke out a living in the Wild West of today's cloud file storage and sharing, nCrypted Cloud Enterprise is Wyatt Earp. For about $10 per user, the solution puts a user-managed security layer atop Box, Dropbox, Google Drive or One Drive without burdening the IT department with lots of administrative overhead. The service combines cloud-based services with browser, desktop and mobile client apps to automatically add as many as five levels of security to files at the discretion of file owners using that cloud system's own native interface. When the CRN Test Center evaluated the Dropbox-only solution earlier this year, we found a stable, intuitive security layer that's as flexible and easy to use as Dropbox itself.
The nCrypted client implements a virtual view of a Dropbox folder. Normal icons appear with a series of new icons on top indicating security status of the folders within. Special icons indicate encrypted personal data, shared encrypted data, and corporate-owned and encrypted folders that are secured with corporate keys. Encryption policies stay with files, even when they're moved outside the system. To remind workers to be good corporate citizens, the software not only prompts users when an impending action would be insecure or unauthorized, it provides a prompt to secure the file with a single click. If an unauthorized person requests access to a file, the requester is prompted with an equally simple method of requesting permission from the owner, who can also use email to accept or deny. An automated invitation system can help get security up and running quickly. Files placed in a folder with a higher security level automatically inherit the stronger security. And top-secret files are prevented from being viewed offline without a corporate PIN. Offline options include a three-day period during which protected files may be viewed by authorized people.

Honorable Mention: Dell Cloud Connect
Every once in a while a device comes along that makes us stop and say, ’Wow, that's really cool, useful or important.' Even more rare still is one that's all three. One such product is Dell Cloud Connect, an Android-based thin-client device that turns a monitor with an HDMI port into a Web-connected HD workstation. Part of Dell's acquisition of thin-client veteran Wyse, Cloud Connect links with a powerful back-end platform through which users access a set of enterprise-managed applications and corporate data via a secure Citrix client running locally on this Android device. A keyboard and mouse connect via USB or Bluetooth; it also accepts touch input and works with the Android soft keyboard. Windows apps can run remotely on the server through Citrix, Virtual PC or VMware View. It also can store and run local Android apps. A dual-core processor and dual-band Wi-Fi keep performance snappy. The Cloud Connect device lists for $129 and the free management back end handles per-device security policies on up to 25 devices and three admins.

Components
Winner: Intel Haswell-EP
Intel once again finds itself at the top of the CRN Test Center's list of Products of the Year. The company last year won high praise for its Tri-Gate processor technology, which reinvigorated a stagnant laptop market. In 2014, Intel's Haswell technology and 22nm process have begun to permeate server designs. The Xeon E5v3-series Haswell-EP processors bring levels of performance and power efficiency never before possible. Haswell-EP processors with 10 cores or more support cluster-on-die, an operating mode that allows columns of cores to appear to the host operating system as two non-uniform memory access CPUs, thereby reducing latency when accessing on-chip cache. Haswell-EP and it higher-performing Haswell-EX and "enthusiast-class" Haswell-E models also support DDR4 memory, which increases bandwidth to 3,200MHz from 2,133MHz.
Boosts in graphics processing capabilities also were significant. There are now four integrated GPU classes, the highest of which incorporate 40 execution units compared with 16 in the prior generation. Further, the highest-level GT3e in some packages adds to those 40 cores with 128 MB of embedded DRAM, which effectively adds a Level 4 cache that's dynamically shared between application and graphics cores. The new parts also fully integrate the voltage regulator, and support Thunderbolt and the newer Thunderbolt 2.0. The chip also implements two new Haswell low-power sleep states, a variable base clock and close to a dozen new thermal design power processor models. The influence of Haswell can be seen in several of the products covered here, the impact of which will be felt for years to come.

Honorable Mention: Micron M600 SSD (with DWA)
With the September release of its M600 SSD series of solid-state drives, Micron Technology claims to have broken the dividing line between low-cost MLC flash memory and the more durable SLC variety of NAND. New firmware inside the drives, in a feature Micron calls Dynamic Write Acceleration (DWA), can switch between SLC or MLC write modes at will, thereby gaining the speed and durability attributes of SLC flash while incorporating the far less costly MLC NAND in the actual drive. The firmware is able to vary the size and location of SLC NAND so as data starts to age, it can be moved in MLC mode to more efficient locations on the drive, reducing drive wear. Prices range from $80 to around $450 in capacities up to 1 TB.

Data Center
Winner: Dell PowerEdge R730
Haswell processors made their way into servers this year, and Dell's 13th-gen PowerEdge R730 made its way onto the CRN Test Center's Top 10 Servers of all time. With capacities of 768 GB of 2,133MHz DDR4 RAM in 24 DIMM slots, 48 TB of SAS, SATA or SSD storage in 24 bays, and 36 cores across two Intel Xeon E5-2500 v3 series processors, this 2U rack server gives new meaning to high-density. The system also can accept as many as seven PCI cards, including GPUs for servicing virtual desktops with high-performance graphics.
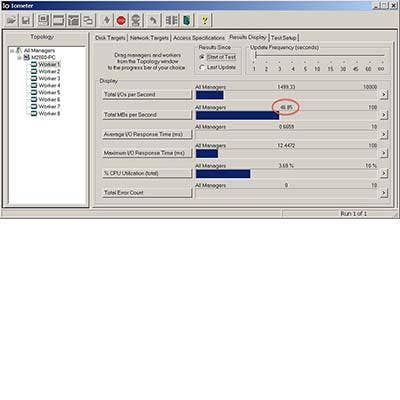
The CRN Test Center evaluated an R730 with two 12-core, 2.6GHz Xeon E5-2690 v3 processors running Windows Server 2012 R2 Datacenter with 64 GB of high-speed DDR4 RAM. For storage, there were five 300-GB 10K SAS drives connected to a PERC embedded RAID controller. IOmeter tests were performed against three drives configured in a RAID-0 array. When serving 32K packets, the system delivered more than 2 GBps serving a single client performing sequential reads, dropping gradually as the number of workers climbed. With 10 simulated clients, the R730 sustained 1 GBps while using just 4 percent of available CPU bandwidth.
Far more power efficient than its predecessor, its dual hot-swap power supplies hovered around 86 watts during testing and settled at 56 watts when idle. Fans were quiet. Simple to service, the unit is documented throughout and features at-server diagnostics via NFC and an Android app. Dell has moved support for PCIe-based SSDs to the new PowerEdge R730XD, a storage-optimized version of the R730 that can combine 1.8-inch SSDs with a layer of 3.5-inch SAS or SATA drives, providing the capability to deploy tiered storage within a server. The R730 also is available in 1U and tower form factors. Base pricing starts at $2,249.

Honorable Mention: Lenovo ThinkServer TD340
Lenovo earlier this year unveiled a trio of powerful new two-socket Xeon ThinkServer models designed for small businesses and departments on a budget. The CRN Test Center reviewed the ThinkServer TD340, a 5U-size tower that supports as much as 32 TB in eight hot-swap storage bays and 192 GB of RAM. List pricing starts at $1,499 including redundant power and cooling systems. The series also includes the 1U RD340 and 2U RD440 rack-mount systems. The tested system, with dual Intel Xeon E5-2440 2.4GHz six-core processors, 32 GB of RAM and three-drive RAID array, sustained a transaction rate in excess of 84,000 IOps, and with 32K packets, a sustained transfer rate of 317 MBps while using between 100 and 130 watts of power.

Desktops
Winner: Lenovo ThinkCentre E93z
Performance numbers from the Lenovo ThinkCentre E93z caused testers to do a double take; no one expected an all-in-one to perform like a workstation. But its 3.1GHz quad-core processor landed the unit in fourth place on the CRN Test Center's all-time performance list for desktops behind three of the fastest workstations we'd ever seen. The successor to Lenovo's E92z comes with a choice of Intel fourth-generation Core i3, i5 and i7 Haswell processors. The tested unit had a Core i7-4770S, and an Nvidia GT720A graphics controller for its 21.5-inch 1,920 x 1,080-pixel 10-point multitouch panel with edge-to-edge glass.
On the right edge are volume controls and an input button, which allows the E93z's display to be used as a monitor for laptop, tablet or other device through its HDMI input port. There's also an HDMI output port for adding a second display. On the left edge are two USB 3.0 input ports (one with standby power), a headset jack and a 7-in-1 multicard reader. Four additional USB 2.0 ports and a Gigabit Ethernet port are on the rear. A pair of down-firing speakers put out clear sound without distortion at high volume. An HD webcam includes a physical shut-off switch.
Service providers and IT staff will appreciate the tools-free assembly of the CPU's VESA mount to Lenovo's new ultra-flexible pedestal base. Handles on either side help reposition the display. The versatile stand easily lowers the bottom edge of the display to desk level and to as high as 5 inches above. The flex stand is a $15 option if ordered with the computer. With a starting price of $839, the ThinkCentre E93z is a solid value for a small business looking for a PC for general productivity. For the higher-end user, the quad-core tested unit with 450-GB hard drive, DVD-RAMBO drive, 4 GB of RAM and Windows 8 Pro carried a list price of $1,329. All systems include a one-year warranty and recovery discs.

Honorable Mention: Lenovo ThinkStation P300
Beyond all-in-ones, Lenovo also is making a name for itself in the PC workstation market, in August adding three new models to its ThinkStation P Series line. Kicking off the line in May was the ThinkStation P300, a single-socket PC that's ready for Haswell. With a base list price of $729 with an Intel Core i3, 500-GB HDD and 4 GB of RAM, the P300 can be ordered with Core i5, i7 or Xeon E3-1200 series processors too, and in small or mini-tower form factors. We tested the 4 x 15 x 13-inch SFF, which delivered impressive results with its Intel Xeon E3-1241 v3 quad-core processor running at 3.5GHz. Also standard are Gigabit Ethernet, six USB 3.0 ports, four PCI slots, VGA and DisplayPort outputs, room for three drives, on-board logic for RAID 0, 1, 5 and 10, and two DIMM slots for up to 32 GB of dual-channel memory.

Displays
Winner : ViewSonic TD3240
The ViewSonic TD3240 is one of the most beautiful displays we've ever seen. The 31.5-inch unit is covered edge-to-edge with 7H-rated scratch-resistant glass, suiting it for digital signage applications in education, retail, transportation centers and other high-traffic kiosk locations. This sturdy unit weighs nearly 36 pounds without the stand, thanks to an all-metal cabinet and 10-point projected capacitive screen and 1,920 x 1,080 IPS panel. It's the largest in ViewSonic's digital signage line, which also includes 23- and 27-inch models.
Out of the box, the TD3240 passed our standard LCD display tests with flying colors. The white saturation and black-level tests were nearly perfect, and gradients of color and black-and-white exhibited no banding. Sharpness tests were all within acceptable parameters. The TD3240 provides inputs for VGA, DVI, audio in, RS-232 in and out, a USB host port for the touch module, and a direct AC power input, all oriented downward for easy wall mounting. The unit's control buttons are located in the rear, out of view of passersby. A pair of 10-watt downward-firing stereo speakers provides adequate sound that's free of distortion but not very loud. The TD3240 lists for $3,059. The 27-inch version lists for $849, the 23-inch model for $619 and the newest 22-inch unit for $489. All include a three-year warranty. A two-footed stand is optional on 32- and 27-inch models. Wired remote is sold separately.

Honorable Mention: Samsung UD970
The UD970, Samsung's first 32-inch ultra-high-definition monitor , sets a high bar. This 32-inch class 3,820 x 2,160-pixel display has four digital inputs: HDMI 1.4, DVI-D and two for DisplayPort 1.2. The DVI port also supports analog (RGB) input. The unit can be driven at full resolution through the HDMI port at 30Hz or the DVI and DisplayPort inputs at 60Hz. The monitor has four picture-by-picture modes, one of which can display all four of the inputs, each at 1,920 x 1,080. Two-input modes include side-by-side and any corner; all feature automatic input detection and manual sound selection. Split screens also can display two different color spaces, catering to someone working on print and online versions of a project, for example. For a list price of $1,999, the unit arrives pre-assembled on its four-way pedestal stand with Mac OS X and Windows drivers, a VESA wall-mounting plate, three data cables and a three-year warranty.
Enterprise Software
Winner: M-Files DMS
Document management doesn't have to be expensive, complex or resource-intensive. Starting at $495 plus $39 per user is M-Files DMS, an easy-to-use document management system for Windows Server that supports about a million files and can run physically or virtually on a non-dedicated server or in the cloud. A quick setup for Windows clients automatically maps a drive to the system's central repository. Each user's own repository appears as a drive or network share, guiding them into DMS though the familiar Windows Explorer UI.
Opening the M-drive brings up their local Cloud Vault, where a well-organized environment imposes a simple and logical structure to documents, tasks and peer interactions. The system is built on the Firebird open-source database but also can use Microsoft SQL Server. Depending on permissions, documents can be checked out of a folder for viewing or editing, or can be assigned to other system users for editing, approval or other tasks based on the organization's individual workflow. All file versions are preserved and activities tracked for later audit or regulatory compliance. There's a native client for Windows; other platforms can access the system and all its functions through a browser.
The system keeps track of files and eases later searches through the use of metadata. Prior to creating any document, the user is presented with fields for entering metadata to classify what's being created. Labels for metadata appear in drop-downs, can trigger additional lists and can vary from one company to another. For example, creation of a marketing document might present a list of Word templates for a company press release, data sheet or other standardized marketing materials. Permissions also can be set here or edited at any time later.

Laptop
Winner: HP EliteBook Folio 1040
One would never know to look at it, but the EliteBook Folio 1040 from Hewlett-Packard is durable enough to be certified for MIL-STD 810G but without looking like a bumper car. It's also fast, offers long battery life, is reasonably priced and can be serviced by resellers with the right training and tools. A machined aluminum shell gives the handsome 13 x 9-inch unit a sturdy feel. The tested unit and its Intel Core i7 dual-core Haswell processor performed well and ran for more than four hours on battery. There are Core i5 and touch-screen options. Standard in the unit are DisplayPort 1.2 output, Wi-Fi a/b/g/n, Bluetooth 4.0, USB 3.0, a microSD slot and a backward-compatible docking port. The newest feature of the Folio 1040 is a 4 x 2.5-inch Synaptics ForcePad, a new type of multigesture, pressure-sensitive touchpad that's comfortable and responsive, but takes some getting used to.
Software innovations abound in EliteBook and are sure to spark interest from enterprise IT and security departments. A BIOS feature called Embedded Sure Start provides hardware-based boot-block protection that's invisible to the CPU and therefore to viruses. At boot time, the tool determines whether the BIOS has been tampered with and can restore the last known good BIOS. This also enables administrators to conduct system BIOS updates that can resume in the event of a power interruption. HP also adds also extra password protection and management, a secure shred feature, an optional biometric scanner with fingerprint enrollment, and full-drive encryption. The razor-thin, 3.3-pound Folio stays slim and light by moving wired Ethernet and VGA ports to a dongle. List pricing starts at $1,299.

Honorable Mention: Dell Precision M2800
Dell is so confident in the performance of its Precision laptops that it submitted one model for CRN's Tech Innovators award consideration in the workstation category. Dell Precision systems are designed to deliver the performance of a tower in the form of a laptop for people working with large media files or running applications for scientific, oil and gas exploration, medical, CAD/CAM, and other vertical markets that need high-performance computing. The M2800 was the best-performing laptop to ever pass through our labs, faster even than some servers. A MIL-STD 810G rating means that it can take a pounding, and it's significantly smaller, lighter and faster than its predecessor, the Precision M6600. It's also about half the cost. The $1,199 base unit comes with Gigabit Ethernet, VGA and HDMI outputs, USB 3.0, Wi-Fi ac, Bluetooth 4.0, an SD card reader and SSD and HDD storage options from 128 GB to 1 TB.

Mobile
Winner: Samsung Galaxy S5
Protection from the water and dirt, iron-clad security, new UI features and a vastly improved camera experience make the Galaxy S5 Samsung's best smartphone yet, and well worth the investment or upgrade. It's built around a 5.1-inch super active-matrix organic LED (AMOLED) 1,920 x 1,080 screen at 450 nits, Qualcomm's Snapdragon 801 2.5GHz quad-core SoC with Adreno 330 GPU and 2 GB of RAM. It's available with either 16 or 32 GB of built-in storage, and can add as much as 128 GB more via microSD. A 16-megapixel camera takes incredible 5,312 x 2,988 pictures, Ultra HD video and slow and fast motion.
An IP67 ingress protection rating means it's totally impervious to dust and can be submerged in 10 feet of water or sprayed with water from any direction for three minutes without harm. In other words, it's protected from the events of normal living. The only thing making it visibly different from any other phone is a cover for its USB 3.0 Micro-B charger port. The headphone jack, mics and speakers are all exposed to the elements, yet still waterproof. Thanks to USB 3.0, data-transfer rates scream along at up to 5 Mbps and MHL 2.0 support allows connections to monitors and other devices. Other communications include infrared, NFC, 802.11 ac with two antennas, plus Wi-Fi-4G bonding for download speeds up to 450 Mbps. It also can bond 4G channels from multiple towers. It's available for approximately $200 with a contract from AT&T, Sprint, T-Mobile or Verizon. It comes with a fingerprint scanner and security software, runs Android 4.4.2 Kit Kat and Samsung's TouchWiz overlay, which allows multiple apps to run simultaneously.

Honorable Mention: Samsung Galaxy Tab S
The Samsung Galaxy Tab S delivers PC-like power in a tablet form factor. The CRN Test Center reviewed the 8.4-inch model; there's also a 10.5-inch unit that shares the same internals and display resolution. The Galaxy Tab S is by far the most responsive Android tablet we've ever tested. Samsung's flagship slabs are built around its flagship SoC: the Exynos 5 Octa 5420, an eight-core powerhouse with four 1.9GHz ARM A15 Cortex cores and another four 1.3GHz A7 Cortex cores. GTS devices come with 3 GB of LPDDR3 RAM and either 16- or 32-GB internal storage plus another 128 GB via microSD. Both pump out 2,560 x 1,600 pixels on the largest Super AMOLED screens ever produced. The 10.5-inch Galaxy Tab S lists for $499 with 16 GB of storage, Wi-Fi, 8-megapixel and 2.1-megapixel cameras, the usual array of sensors, Android 4.4 Kit Kat and Samsung's TouchWiz UI. Configured the same way, the 8.4-inch unit lists for $399.

Networking
Winner : Linksys LGS552P 52-Port Managed PoE+ Switch
The Linksys LGS552P 52-port Managed PoE+ Gigabit Switch proves that high-density managed Ethernet can still come at a manageable price. For a street price of approximately $1,050, the device offers Layer 2 and Layer 3 capabilities for the enterprise typical of switches costing far more. And it's managed through the same intuitive browser-based interface that made Linksys a household name.
The LGS552P provides 50 Gigabit Ethernet ports, 48 of which also supply up to 375 watts of total power to PoE (802.3at or 802.3af) devices. This makes the device well suited for deploying IP-based phone systems, video surveillance, Wi-Fi access points and quantities of other PoE devices. It includes Layer 3 static routing and security policies, link aggregation and quality-of-service capabilities often found on products costing far more. Basic QoS policies are enabled by default, and include queue scheduling for strict or round-robin access and direct control of bandwidth. Advanced QoS provides class mapping, aggregate policing, port policies and other policy mapping.
The scalable device also incorporates two 10-Gbps Ethernet ports and two ports for small form-factor pluggable option modules for making uplinks via fiber-optic, high-speed copper or other media and high-speed protocols and two combo ports. There's also a dedicated console port with RJ45-to-DB9 cable and mounting hardware for a 19-inch rack. For a small office, the Linksys LGS552P 52-port Managed PoE+ Gigabit Switch is a low-cost PoE solution that can expand along with the needs of a growing business and is easy to set up and maintain. For the enterprise, Linksys delivers Layer 2, Layer 3 and manageability features to make it suitable for even the most demanding of corporate environments.

Honorable Mention: ION SpeedServer SR-71mach 4
Since ION Computer Systems in 2011 developed the first machine in its class to sustain a million transactions per second, engineers at the Long Island-based white-box builder have been hard at work to improve their winning design. The result was the Speed Server SR-71mach 4, an all-SSD 2U RAID server that delivers sustained IO performance on par with multiserver spinning arrays encompassing thousands of disks. And it does so with half-millisecond latency, about a quarter of what's typical of spinning-disk arrays. Under the hood is an Intel Grizzly Pass two-socket motherboard with a pair of Intel Xeon E5-2690 v2 10-core 3.0GHz processors running Windows Server 2012 R2 with 64 GB of 1,866MHz ECC RAM. A well-equipped mach4 costs around $47,000.

Office Equipment
Winner: Epson PowerLite 4855WU projector
Epson last summer unveiled its PowerLite 4000 series of industrial-grade projectors, supplementing its line of video projectors for the boardroom, classroom and home media room with one designed for auditoriums, large conference rooms and other high-usage settings. The CRN Test Center tested the PowerLite 4855WU, the high-end model that generates 4,000 lumens to project a maximum resolution of 1,920 x 1,200 pixels. The versatile unit can be set on or affixed to a table or cart, mounted upside down on a ceiling and used to project from the front or rear of the screen.
The rear panel is home to a small group of projector menu controls and a wide variety of inputs. A lighted remote operates all projector functions. There are inputs for HDMI, DisplayPort, VGA, component (BNC) and composite (RCA), the latter three with accompanying audio. There's also an S-video input and a VGA output. A split-screen function permits two digital video sources to be displayed at once in any of three layouts. An Ethernet port affords network remote control, content delivery, monitoring, maintenance and health alerts via email. If something fails in the boardroom, a help button can make anyone the hero thanks to choices such as "The image is small" and "There is no audio." The remote also has dedicated controls for each input, volume, split screen and digital zoom, plus three user-programmable functions. The remote works from a variety of angles to a distance of about 50 feet, The projector can be set to accept remote input from the front, rear, both or neither. The Epson PowerLite 4855WU lists for $2,999 and uses the $200 260 W UHE lamp.

Honorable Mention: Oki MC562w Multifunction Printer
Starting at $750 list, the Oki Data MC562w 27- to 31-ppm color printer, 1,200 x 1,200 scanner, copier and fax delivers ease of setup, speed of output, warranty and low cost. It also satisfies secondary considerations such as overall size, paper capacity, a two-sided printing option, Wi-Fi and OCR. The MC562 delivers 1,200 x 600 laser-quality output thanks to Oki's LED imaging engine, which consumes less power than a laser engine and requires fewer moving parts. In tests, the printer drew a maximum of 1,034 watts when cycling up, settled at 14 watts while waiting for something to do, and bounced mostly around between 370 and 720 while printing. It can be shared on wired or Wi-Fi, serve walk-ups through USB and takes jobs from AirPrint, CloudPrint and Oki's own MotionPrint.
Rugged
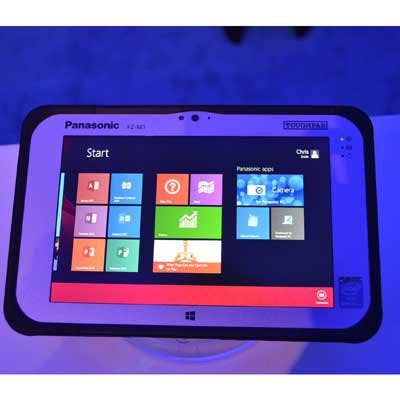
Winner: Panasonic Toughpad FZ-M1
Rugged computing pioneer Panasonic this year unveiled the Toughpad FZ-M1, a 7-inch version of the original Toughpad G1 Windows tablet platform. Just as rugged and versatile, the pocket-sized partner is easier to handle and is a solid platform that can withstand the hammering of construction sites, wrenching conditions of a mechanic's shop, soaking at a spa and other field conditions that would simply destroy an iPad or other naked tablet. Behind the 7-inch 1,280 x 800 IPS panel is a 500-nit LED backlight that's viewable in bright sunlight from any angle. The M1 is certified compliant with the MIL-STD 810G and IP65 specs, plus 461F for electromagnetic protection.
Performance never lagged thanks to an Intel Core i5 dual-core 1.6GHz Haswell processor running 64-bit Windows 8.1 Pro on 8 GB of RAM. A Celeron option shaves about $800 from the starting price. Its 10-point touch screen and auto-rotation are super-responsive. The unit's standard battery is rated at about eight hours. In our tests, which disable screen dimming, it delivered about three and a half hours. An optional extended battery doubles the rated life to 16 hours, and a bridge battery option keeps the M1 running for about 30 seconds while swapping batteries. The battery automatically locks when inserted. A capacitive stylus provides excellent precision for app and Windows navigation, and compensates for the smallish screen. In addition to standard Wi-Fi ac, Bluetooth 4, USB 3.0 and slots for micro SIM and micro SD, the customizable M1 can be outfitted with Gigabit Ethernet, 4G, GPS, a 1-D and 2-D barcode reader, mag-stripe reader, RFID, a serial-port module and a 128- or 256-GB SSD. Most option modules also include the bridge battery. Celeron-based models start at around $1,299; a Core i5-based unit comes in at around $2,099.

Honorable Mention: GammaTech SA14
Also worthy of mention this year is the Durabook SA14 from GammaTech. This durable notebook outperformed all but the highest-end laptops we've seen in the Test Center. It's a sturdy, secure and configurable laptop from an established company that gives public-sector resellers a lower-cost option. In our tests, its Intel Core i7 dual-core processor landed it in third place on The CRN Test Center's all-time list, second only to a pair of quad-core units. Standard equipment includes a 14-inch 1,366 x 768 touch screen with 500-nit backlight, USB 3.0 and 2.0 ports, Gigabit Ethernet and VGA and HDMI outputs. The SA14 also is available with Core i5 CPUs starting at $1,499 with a two-year warranty.
Storage
Winner: ioSafe 1513+
Once victimized by theft, flood, fire or another type of disaster, the value of irreplaceable data can really come into focus. The ioSafe 1513+ NAS RAID is one of a line of simple and elegant fire- and flood-proof NAS devices from ioSafe that provides a local bulwark to disaster starting at just $1,600 without drives.
In this 15 x 9 x 12.5-inch tiny fortress, up to five drives are protected by an endothermic layer that releases water vapor to counteract temperatures up to 1,550 degrees for 30 minutes (per ASTM E119 specs), according to the company. The system also can protect data from submersion in fresh or salt water as deep as 10 feet for as long as three days. ioSafe backs up its claims with a one-year data recovery pledge on drives it provides. While above water, dual hot-swap fans keep the insides from baking. It can be bolted down, mounted in a rack or secured with its Kensington slot. Like a small safe, it weighs nearly 60 pounds fully loaded.
The system's Synology embedded software is feature-complete and centers around a browser-based control panel and app center. The 1513+ has four Gigabit Ethernet ports for connection to multiple LANs or for aggregating to increase bandwidth or provide fault tolerance. A traffic control function also permits minimum and guaranteed bandwidths to be assigned to one or more applications. For example, if the NAS is being used for telephony using the included Asterisk app, bandwidth can be reserved to minimize lag for voice-bearing traffic. The NAS itself can be backed up to other Synology or rsync-compatible systems on the network, to an Amazon S3 destination or to local volumes attached to its USB or eSATA ports with multiversion backups, deduplication, scheduling and automatic restoration creation.

Honorable Mention: Drobo Mini
The Drobo Mini hits every sweet spot for a user's local storage needs at a street price of approximately $300 plus drives. About the size of a small textbook, it incorporates four 2.5-inch caddyless hot-swap bays to thin-provision up to 16 TB of storage using spinning or SSD media for Mac OS X or Windows machines via USB 3.0 or Thunderbolt. Both cables are included. A second Thunderbolt port allows for daisy-chaining with displays and other storage devices. An internal battery neutralizes brief power interruptions and a twist-on power plug prevents accidents. Clever LEDs indicate capacity status and drive health. Mini supports HTFS or HFS+ with support for Time Machine. If more capacity is needed but all four bays are filled, Drobo's proprietary protocol allows any single drive to be replaced with a higher-capacity one without data loss.

Wearable
Winner: Zebra Technologies HC1 Headset Computer
With Zebra Technologies' HC1 Headset Computer, service organizations tap into the knowledge of veteran field technicians without the expense and risk of sending them into the field. Available for about a year now, these head-worn computers cost about $4,500 each but can save many times that amount each year in travel costs alone. They're currently being used in manufacturing, field service, trauma-care, construction sites, nuclear facilities, military operations, for power line maintenance and other scenarios in which workers benefit from having both hands free.
The HC1 combines a voice-controlled smaprtphone-caliber computer with an 800 x 600 microdisplay that's the equivalent of a 15-inch monitor. When added to an HD camera, noise-canceling microphone, 4G, Bluetooth and Wi-Fi communications, the result is a Borg-like device that's futile to resist trying out. Modular peripherals attach easily for left- or right-dominated orientation and a user-assigned Velcro-and-foam harness is fully adjustable and machine-washable.
For technicians in the field, the HC1 can make schematics or parts diagrams visible while leaving both hands free to perform the service. The microdisplay is designed not to block one eye, but to act as a reference just as an actual document would. Unlike Google Glass, which relies on a separate smartphone to do its job, the HC1 is a stand-alone computer that can think for itself and work independently of any other hardware.

Honorable Mention: Samsung Gear 2
Samsung Gear 2 came out this year, and the company's latest smartwatch is now more stylish, more versatile and works far more logically than its predecessor. Despite some software kinks, Gear 2 has great potential not just as an add-on to a smartphone or tablet, but as a trailblazer into wearable technology that stands alone to provide specific sets of communication capabilities. Samsung was first to market with the smartwatch concept, which extends the host device for notifications, texting and phone calls. For starters, the watch is now waterproof and dustproof. There's also an IR emitter for remotely controlling TVs, cable boxes and other electronics. Its 2-megapixel camera is now housed in the watch's metal body rather than in the now-replaceable strap. An improved charger clips onto the back of the watch and accepts a micro-USB connector. Gear 2 lists for $299.