CRN's 2018 Products Of The Year

CRN’s 2018 Products of the Year awards honor the best new products and major updates that made it onto our radar over the past year.
To start, CRN editors selected product finalists among 22 top technology categories for the IT channel. We then asked solution providers to determine a winner based on how the products rate on technology, revenue and profit opportunities, and customer demand.
Here are the winners and finalists.

COLLABORATION
CISCO WEBEX UPDATES
WINNER: OVERALL
Cisco recently debuted a range of notable updates to its Webex collaboration platform, including unveiling a new version of Webex Meetings. The platform provides a modern approach to video meetings through simplified scheduling and joining, with one button to push for joining a meeting from any device. Cisco also launched a new Webex Assistant and a Webex Share device, while announcing that its Spark platform would join the platform under the name Webex Teams. “The brand unification under the Webex name makes perfect sense,” said Ryan Carricato, principal consultant at Exeter, R.I.-based Carousel Industries, in an email. Meanwhile, “the new modern dashboard and video-first UX for Webex Meetings is attractive to Carousel customers continuing to adopt video in meetings, both for remote users and in the conference room,” he said.
Finalist: 8x8 X Series
The X Series from 8x8 brings together voice, video, collaboration and contact center into a single cloud platform. Capabilities include advanced analytics around employee-customer interactions, enabling more intelligent customer engagement for businesses. Plan configurations can include features such as team messaging and additional data analytics options.
Finalist: Intermedia Unite
Intermedia Unite provides voice, video, screen sharing and file sharing, and secure backup on an integrated platform that’s easy to install and manage for solution providers serving small- and midsize-business customers. Intermedia’s cloud-based voice services come together with AnyMeeting videoconferencing in this powerful offering for SMBs.
Finalist: Microsoft Teams Updates
Recent enhancements to the Microsoft Teams collaboration app included a move to make the service available as a free version. The free Teams version can serve up to 300 people and offer unlimited chat, video and audio calling, and file storage.
Finalist: Polycom RealConnect updates
Updates to the Polycom RealConnect cloud-based video interoperability service over the past year have included the addition of support for the Microsoft Teams collaboration app. RealConnect now enables Polycom and Cisco endpoints to join Microsoft Teams meetings, with video users now able to meet “face to face” with Microsoft Teams users.
DESKTOPS
LENOVO THINKCENTRE M920 TINY
WINNER: OVERALL
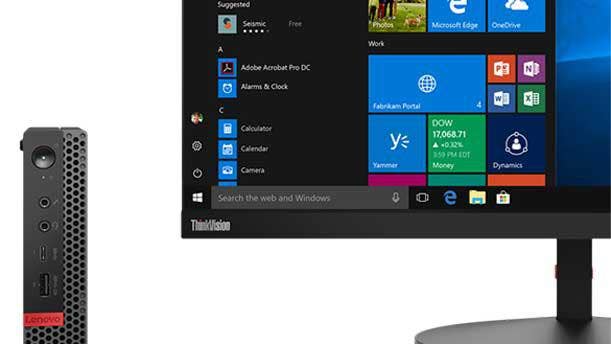
With the ThinkCentre M920 Tiny, Lenovo offers major performance in a one-liter form factor. Measuring just 1.4 inches wide, the company’s new desktop PC offers up to 32 GB of RAM and up to an eighth-generation, six-core Intel Core i7 processor (with clock speed of up to 4GHz). In addition, the Lenovo ThinkCentre M920 Tiny features PCIe storage expansion options and a wide range of ports, including USB-C, USB-A and HDMI. The ThinkCentre M920 Tiny is among the latest entries to Lenovo’s Tiny lineup, which is one of the fastest-growing PC lines at Loganville, Ga.-based solution provider CommQuest. “Overall, it’s a great product,” said CommQuest CEO Mark Sanchez. “With that form factor and the power that it can deliver, that combination is great for customers.”
Subcategory Winner—Customer Demand: Dell Precision 3430 Small Form Factor Tower
Aimed at customers with small work environments, Dell’s Precision 3430 Small Form Factor Tower is just 3.65 inches wide but still offers strong CPU and graphics performance. Processor options include Intel Xeon E and eighth-generation Intel Core, while graphics choices go up to the AMD Radeon Pro WX 4100 or Nvidia Quadro P1000.
Finalist: Apple iMac Pro
The iMac Pro provides performance previously unheard of in the history of the Mac. The all-in-one features Intel Xeon processors— with eight-core, 10-core or 18-core options—along with up to 128 GB of RAM. The iMac Pro also includes AMD’s Radeon Vega graphics, while its 27-inch display features 5K resolution.
Finalist: Dell OptiPlex 7760 AiO
Even with its 27-inch display size, Dell’s OptiPlex 7760 AiO has a footprint more akin to a 24-inch all-in-one thanks its thin-bezel InfinityEdge design. Features include an optional 4K resolution display and an articulating stand so the display can be adjusted to lay nearly flat.
Finalist: HP EliteOne 1000 AiO
HP Inc.’s EliteOne 1000 is an all-in-one PC featuring a 34-inch display and collaboration features such as a dual-facing pop-up webcam for videoconferencing and dedicated keys for launching video and audio calls. The massive display offers sharp and vivid picture quality with WQHD (2,560 × 1,440) resolution.
ENTERPRISE SOFTWARE
HPE ONEVIEW 4.1
WINNER: OVERALL
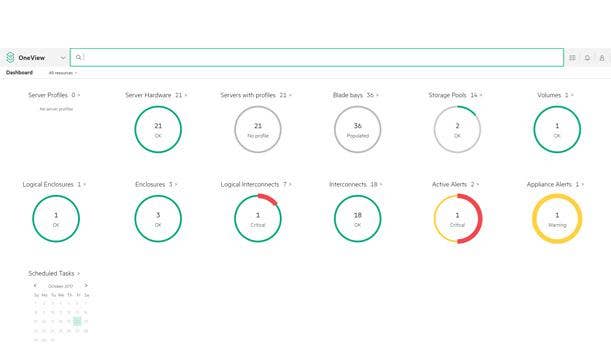
With version 4.1 of OneView, Hewlett Packard Enterprise’s IT infrastructure management software platform, the company has added major enhancements such as the ability to do updates clusterwide on a rolling basis. This is a critical change, said Alan Rogers, chief technology officer at Ottawa, Ontario-based Stoneworks Technologies. “Not having to do the updates on a per-host basis is huge,” Rogers said. “For HPE, this is a big differentiator from its competitors.” OneView 4.1 provides for 50 percent faster firmware updates to HPE’s Gen10 ProLiant servers. The version also adds enhanced Microsoft support, including support for Microsoft Azure Stack Log Analytics and improved integration with Microsoft System Center.
Subcategory Winner—Technology: Splunk Enterprise 7.1
Splunk Enterprise 7.1 brings significantly expanded use of artificial intelligence for monitoring key business information. Updates include an enhanced metrics engine that monitors and issues alerts on numeric data points, such as CPU speeds and available hard disk space.
Subcategory Winner—Customer Demand: Oracle Database 18c
Positioned as the world’s first self-driving database, Oracle Database 18c dynamically provisions itself, patches itself, updates itself and tunes itself—all without human intervention. The system adds resources when needed and takes them back when not in use.
Finalist: Microsoft Dynamics 365 Updates
Dynamics 365—Microsoft’s combination cloud CRM and ERP system—recently received enhancements including embedded intelligence capabilities such as “relationship assistant” (for helping sellers to see alerts and reminders) and “auto capture with Outlook” (for helping sellers save time by analyzing email to find relevant messages).
Finalist: Puppet Enterprise 2018.1
In recent updates to Puppet’s flagship offering, Puppet Enterprise 2018.1 features upgrades including Puppet Tasks role-based access control (for improved defining of node groups), Puppet Bolt Task Plans (for enhanced running and tracking of tasks) and simplified backup and recovery capabilities.

ENTERPRISE STORAGE
DELL EMC POWERMAX 8000
WINNER: OVERALL
Dell EMC’s PowerMax all-flash arrays, formerly known as VMAX, offer a complete architecture refresh of the prior offerings built from the ground up to be ready for the latest storage media technologies—including new NVMe flash storage and future storage-class memory. PowerMax is targeted at next-generation applications such as real-time analytics, genomics, artificial intelligence, the Internet of Things and mobile applications. The arrays implement machine learning to improve performance and provide proactive system health monitoring. The PowerMaxOS storage operating system takes advantage of years of collected performance and maintenance data and real-time data within the array itself. The PowerMax 8000 scales to up to 4 Petabytes of effective capacity, with up to 10 million IOPs of performance.
Subcategory Winner—Technology, Revenue and Profit: HPE 3Par StoreServ 20000
Hewlett Packard Enterprise’s 3Par StoreServ 20000 features stunning scale, availability and performance—with 3.8 million IOPs and sub-millisecond latencies. The flash array also now includes Nimble InfoSight predictive analytics for predicting storage issues and proactively resolving them before they impact the installed base.
Finalist: IBM FlashSystem 9100
IBM’s FlashSystem 9100 introduces the company’s first storage system featuring embedded high-performance NVMe storage capacity. The system supports both IBM’s proprietary FlashCore flash storage modules as well as industry-standard SSDs, and comes with Storage Insights, IBM’s artificial intelligence-powered analytics software.
Finalist: NetApp AFF A800
NetApp’s AFF A800 NVMe array features latency of less than 200 microseconds, with data transfer of up to 300 Gbps and performance of up to 11.4 million IOPs. The AFF A800 also offers an enhanced version of NetApp’s Active IQ software that provides predictive analytics for technical support.
Finalist: Pure Storage FlashArray//X90
Pure Storage’s all-NVMe //X90 offers up to 3 Petabytes of effective capacity in a 2U footprint—with latency as low as 250 microseconds and the ability to unite SAN and DAS into a single, consolidated, and shared data-centric architecture.

GENERAL-PURPOSE SERVERS
HPE PROLIANT DL325 GEN10
WINNER: OVERALL
Joining the 10th-generation version of Hewlett Packard Enterprise’s popular ProLiant server platform this year is the ProLiant DL325 Gen10, which features major performance thanks to its use of AMD Epyc processors. Leveraging the chips means that HPE can deliver the economics of a single processor, but with more performance than competing solutions that feature two processors. That ultimately results in 25 percent better price performance with the ProLiant DL325 Gen10. The server “reduces price in two ways,” said John Kolimago, executive vice president and general manager of cloud solutions at Blue Bell, Pa.-based Anexinet. “There’s the acquisition cost of the technology itself—that’s a big benefit. But where the rubber really meets the road is with the licensing models that many ISVs have, where they pay by the processor. If you can do the same amount of work on one processor, where previously it took two, you’ve effectively halved your licensing cost with your ISV.”
Subcategory Winner—Customer Demand, Revenue and Profit: Cisco UCS C4200
Cisco’s Unified Computing System C4200 targets compute-intensive, scale-out workloads with its high-density, multi-node server that maximizes application performance and operational efficiency. Each node contains 16 DDR4 DIMM slots for up to 2 TB of DRAM capacity.
Finalist: Dell EMC PowerEdge R940xa
Dell EMC’s four-socket PowerEdge R940xa server is purposebuilt to tackle performance bottlenecks with improved response times. The PowerEdge R940xa combines up to four CPUs with four GPUs in a 1:1 ratio, and enables low latency with directattached NVMe drives.
Finalist: Lenovo ThinkSystem SR950
Lenovo’s ThinkSystem SR950 is designed for demanding, missioncritical workloads. The 4U server can scale from two to eight Intel Xeon Scalable processors with up to 12 TB of memory in 96 slots, and the server’s modular design provides rapid upgrade and servicing.
Finalist: Supermicro SuperServer 4029GP-TRT
Supermicro’s SuperServer 4029GP-TRT supports eight Nvidia Tesla V100 32-GB GPU accelerators with maximum GPU-to-GPU bandwidth for cluster and hyper-scale applications. The 4029GP leverages Intel Xeon Scalable processors with up to 28 cores, while including 24 DIMM slots and up to 3 TB of memory capacity.

HYBRID CLOUD
VMWARE CLOUD ON AWS UPDATES
WINNER: OVERALL
The next era of VMware Cloud on AWS has arrived with a long list of features recently unveiled including new entry-level pricing, custom CPU licensing capabilities and application-centric security with NSX. Customers can now gain control over east-west traffic between workloads running in VMware Cloud on AWS through micro-segmentation provided by NSX. VMware also reduced the entry price for VMware Cloud on AWS by 50 percent and created new custom CPU core count capabilities that allow businesses to specify the number of CPU cores they need. Overall, VMware Cloud on AWS offers lots of new opportunities to solution providers, said Brendan Caulfield, co-founder and managing partner of Chicago-based Turing Group. Along with the familiarity of VMware and “not having to retool your staff,” the offering also provides “the ability to take your VMware infrastructure and now tie in all of those really cool services you hear about on AWS,” Caulfield said.
Subcategory Winner—Customer Demand, Technology: Amazon RDS On VMware
Amazon has armed VMware partners with its database-agnostic Relational Database Service (RDS) that allows them to easily set up, operate and scale databases in VMware-based environments—such as Oracle and Microsoft SQL Server—that are on-premises or on the Amazon Web Services public cloud.
Finalist: HPE GreenLake Hybrid Cloud
Hewlett Packard Enterprise’s GreenLake Hybrid Cloud is a breakthrough pay-per-use offering that combines on-premises private cloud with AWS, Microsoft Azure and Azure Stack. The offering provides performance optimization, cost controls, security and compliance, leveraging a toolset from HPE’s OneSphere multicloud management Software-as-a-Service platform.
Finalist: IBM Cloud for VMware Updates
With version 2.5 of IBM Cloud for VMware—which enables the extension of VMware environments to the IBM cloud—IBM is providing enhancements including the introduction of private networking, so that IBM’s CloudDriver and CloudBuilder components don’t need a direct connection to the public network.
Finalist: Microsoft Azure Stack Updates
Recent additions to Microsoft’s Azure Stack hybrid offering included the release of Azure Stack for Government. The solution provides government customers with access to the same infrastructure and services that are available on Azure— including the same APIs, DevOps tools and portal—while meeting strict regulatory, connectivity and latency requirements.
HYPER-CONVERGED INFRASTRUCTURE
NUTANIX ERA
WINNER: OVERALL
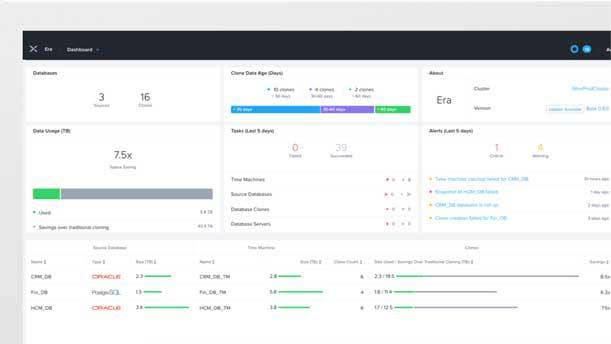
Nutanix’s innovation engine is roaring as the hyper-converged infrastructure pioneer recently launched new offerings for channel partners to drive recurring revenue, which includes Nutanix Era. The Platform-as-a-Service system provides automated database provisioning and life-cycle management, extending Nutanix’s Enterprise Cloud OS software stack beyond core Infrastructure-as-a-Service capabilities for private cloud environments to platform-layer services that bring one-click simplicity to database operations. The product gives partners the ability to move up the stack with Nutanix, said Clive Anthony, senior partner and business manager for software-defined data center at Merrimack, N.H.-based Connection. “Nutanix is coming out with some really game-changing, groundbreaking technologies. They’re making their customers rethink how they buy, procure and utilize IT,” Anthony said.
Subcategory Winner—Technology: HPE SimpliVity 2600
Joining Hewlett Packard Enterprise’s SimpliVity 380 is the HPE SimpliVity 2600, a hyper-converged offering that is optimized for space-constrained deployments. The system provides everything needed to run virtual machines in a compact chassis, enabling simplified scale-up of storage and compute.
Finalist: Cisco HyperFlex 3.0
The 3.0 software release for Cisco HyperFlex features upgrades such as support for Microsoft Hyper-V, stretch clusters and containers. The software also provides new multi-cloud services for enabling the deployment, monitoring and management of applications in any cloud.
Finalist: Dell EMC VxRail Updates
Recent enhancements to Dell EMC’s VxRail hyper-converged infrastructure offering included a move to synchronize the release of updated versions with releases of VMware vSAN, along with the introduction of new VMware-validated designs to support disaster recovery on VMware Cloud-based infrastructures.
Finalist: Scale Computing HC3
Scale Computing’s turnkey HC3 hyper-converged infrastructure offering allows users to mix and match different nodes in a highavailability cluster that scales from three to eight nodes, with the ability to centrally manage up to 25 clusters.
INTERNET OF THINGS
SCHNEIDER ELECTRIC ECOSTRUXURE IT EXPERT
WINNER: OVERALL
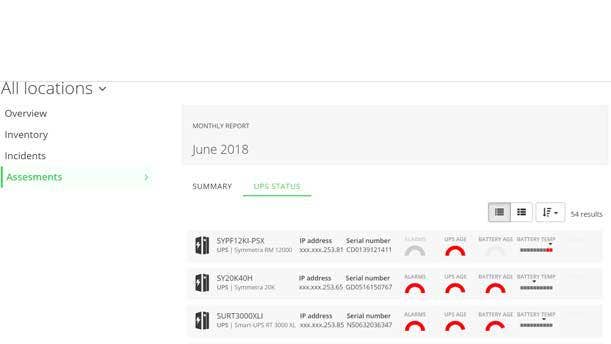
Thanks to its IoT-enabled architecture, Schneider Electric’s EcoStruxure IT Expert cloudbased monitoring offering aids with management of edge computing systems and with management of the data center. The service provides partners with real-time insight about devices, as well as visibility into historic performance. Key capabilities include live data for 24/7 visibility, data-driven insight into the health status of connected devices, and smart alarming—all of which can be delivered to a smartphone or tablet. Andrew Isch, account executive for Towson, Md.-based Vision Data Center, said he sees major potential for the use of EcoStruxure IT Expert in the IoT realm. “There’s a need for predictive analytics for IoT devices out there,” Isch said. “That’s where this is going.”
Finalist: AWS Greengrass Updates
Amazon Web Services bolstered its capabilities for IoT edge applications with the launch of Greengrass ML Inference, a feature of the AWS Greengrass edge service. Greengrass ML Inference enables devices to run machine-learning models to perform inference tasks locally, get results, and then make smart decisions quickly—even when they’re not connected.
Finalist: Cisco UCS C480ML
A server capable of providing artificial intelligence and machine learning out to the edge, Cisco’s UCS C480ML comes loaded with eight Nvidia Tesla V100 data center GPUs, up to 24 drives able to support 182 TB, up to six NVMe drives and the ability to handle up to four 100-Gb network switches.
Finalist: HPE Edgeline EL4000
With the Edgeline EL4000, a converged system for IoT, Hewlett Packard Enterprise integrates compute, storage, data capture and control along with management of systems and devices. The system is highly durable, able to handle challenging IoT environments with protection against shock, vibration and extreme temperatures.
Finalist: Intel OpenVINO Toolkit
Intel’s OpenVINO toolkit helps accelerate development of highperformance video analysis in edge devices for IoT deployments. Geared toward developers that have been training neural networks in existing frameworks like TensorFlow and Caffe, the toolkit offers simplified ways to bring inference capabilities to the edge for vision computing applications.

LAPTOPS
LENOVO THINKPAD X1 CARBON, SIXTH GENERATION
WINNER: OVERALL
For the sixth generation of Lenovo’s ThinkPad X1 Carbon, the popular business notebook gets an enhanced 14-inch display with brightness of up to 500 nits and optional support for Dolby Vision HDR technology. Other new additions include USB-C mechanical side docking, improved microphones (that reach a farther distance), and eighth-generation Intel Core processors. In addition, the new X1 Carbon offers up to 15 hours of battery life, optional LTE connectivity, and—perhaps best of all—a weight of just 2.49 pounds. The sixth-generation X1 Carbon offers a killer combination of “light, durable and fast,” said Michael Goldstein, president and CEO of Fort Lauderdale, Fla.-based solution provider LAN Infotech. “It’s amazing how much power they pack into that small unit.”
Subcategory Winner—Customer Demand: Microsoft Surface Book 2
Microsoft’s Surface Book 2 features a high-resolution display that fully detaches from the keyboard for use as a Windows 10 tablet. The Surface Book 2 also features major horsepower with up to an eighth-generation Intel Core i7 processor and optional discrete Nvidia GeForce GTX graphics, along with up to 17 hours of battery life.
Finalist: Apple MacBook Pro 2018
Apple’s 2018 update to its MacBook Pro with Touch Bar improved the performance, keyboard and display of both the 13-inch and 15-inch models. Along with adding eighth-generation Intel Core processors, the MacBook Pro is now configurable with up to 32 GB of RAM—twice the previous maximum amount.
Finalist: Dell Latitude 7390 A
long with being one of the lightest business laptops on the market at 2.59 pounds, Dell’s Latitude 7390 offers strong performance and battery life; a bright 13.3-inch display with optional touch screen; Microsoft’s highly responsive Precision Touchpad; facial recognition sign-in from Windows Hello; and an appealing carbon-fiber design.
Finalist: HP EliteBook x360 1030 G3
For HP Inc.’s latest EliteBook x360 1030 convertible notebook, display options go up to 700 nits of brightness and can include an optional Sure View integrated privacy screen. The notebook features a 10 percent smaller footprint overall, while the weight has been kept to 2.76 pounds. The notebook also offers eighthgeneration Intel Core processors and up to 18 hours of battery life.

MIDRANGE STORAGE
HPE NIMBLE STORAGE ADAPTIVE FLASH CS1000
WINNER: OVERALL
The latest Nimble Storage Flash Arrays from Hewlett Packard Enterprise, including the CS1000 hybrid array, are designed to take advantage of both NVMe flash storage and storage-class memory—and are backed by a guarantee to deliver the best storage efficiency of any all-flash array. The all-flash arrays also include a 99.9999 percent guaranteed availability along with the company’s InfoSight predictive analytics—enabling solution providers to quickly pinpoint the source of application performance issues. “InfoSight is the secret sauce,” said Dan Molina, chief technology officer at San Diego-based Nth Generation Computing. “In general, when applications have a performance problem the first place customers look is storage, but that is often not the issue. InfoSight provides visibility into exactly where the storage application IO bottleneck actually is.”
Subcategory Winner—Technology: Dell EMC Unity 650F
Dell EMC’s Unity 650F brings all-flash storage to mixed workloads with low latency and ultra-fast performance via 14-core Intel processors. Raw capacity ranges from 10.6 TB up to 16 PB, while new features include inline data reduction.
Finalist: NetApp FAS2700
Along with providing high performance with NVMe flash and capabilities for servicing systems during business hours, the FAS2700 offers a compact, 2U footprint accommodating up to 24 internal disk drives that midsize businesses and small enterprises should appreciate.
Finalist: Nexsan Unity 4400
Nexsan’s Unity storage platform, including models such as the Unity 4400, received recent enhancements including the certification of ATTO Technology’s 16-Gb Celerity host bus adapters—bringing improved capabilities for offering high-performing storage.
Finalist: StorageCraft OneXafe 5410
With its OneXafe platform, including the OneXafe 5410 object-based storage offering, StorageCraft combines scale-out storage with data protection for both physical and virtualized environments. OneXafe ultimately provides converged, integrated data management and data protection tailored to the needs of midsize businesses.
NETWORKING
CISCO CATALYST 9000 UPDATES
WINNER: OVERALL
Following Cisco’s launch of its Network Intuitive platform last year—an intent-based networking system used in tandem with switches such as the Catalyst 9000 series—Cisco this year updated the Catalyst 9000 once again with a number of major advancements. Newly introduced capabilities include Cisco’s Network Assurance Engine and DNA Center Assurance, components of Cisco’s intent-based networking platform that promise predictive analytics and insight into customer networks. The capabilities enhance the Catalyst 9000 by allowing for “much more of a phased approach” toward intent-based networking, said Greg Stemberger, technical director for the NextGen networking practice at Herndon, Va.-based Iron Bow Technologies. Implementing the assurance capabilities “is becoming the first step to enabling this intelligent stack on top,” Stemberger said—which allows customers “to take advantage of the Catalyst 9000 but doesn’t dramatically change how they operate the network.”
Subcategory Winner—Revenue and Profit: Ruckus E510
With the E510, Ruckus has developed an 802.11ac Wave 2 access point to target space-constrained and hard-to-reach areas with strong-performing Wi-Fi. The access point offers data rates of up to 867 Mbps along with a design that allows it to blend aesthetically into outdoor deployment sites.
Finalist: Aerohive 802.11ax Access Points
As the first vendor to offer access points on the 802.11ax standard, Aerohive Networks has developed these access points to dramatically improve Wi-Fi efficiency. Enhancements such as new channel-sharing capabilities enable Aerohive’s 802.11ax access points to provide strong performance to a far greater density of users.
Finalist: HPE Aruba 8400 Core Switch Series Updates
Following the groundbreaking launch of the HPE Aruba 8400 Core Switch Series last year, the company has brought significant updates including the addition of the IntroSpect UEBA (User and Entity Behavioral Analytics) offering—which integrates with Aruba ClearPass to enable policy-based attack response.
Finalist: Juniper EX4300 Multigigabit Ethernet Switch
Along with strong performance, availability and security, Juniper Networks’ EX4300 Multigigabit Ethernet Switch provides key capabilities for branch location and campus deployments including centralized management in the cloud and hot-swappable components such as fans and power supplies.
POWER MANAGEMENT SOFTWARE AND TOOLS
APC BY SCHNEIDER ELECTRIC SMART-UPS WITH APC SMARTCONNECT
WINNER: OVERALL
APC SmartConnect ties the APC by Schneider Electric Smart-UPS to the APC cloud via a secure web portal to provide customer notifications and alerts such as battery issues or other problems, along with firmware updates and support. Channel partners can use APC SmartConnect as part of a managed services offering and integrate it with remote monitoring and management software. Channel partners can also configure SmartConnect to pass them alerts to provide proactive management for customers. Josh Gradwohl, inside solutions architect for power and cooling at Auburn, Wash.-based solution provider Zones, said that many of Zones’ customers have asked to get access to their UPSes through the cloud. “To have it hosted in the cloud and available for access from any location [is] much easier,” Gradwohl said.
Subcategory Winner—Revenue and Profit: Eaton Visual Capacity Optimization Manager
Eaton Visual Capacity Optimization Manager offers intuitive power management and business intelligence by monitoring the power infrastructure of both IT and facilities—reducing operational expenses for data centers and improving the reliability of systems and applications, while also using data analysis to help mitigate risk.
Finalist: Tripp Lite Three-Phase PDUs With LX Platform
Among Tripp Lite’s latest power protection and connectivity products is a lineup of three-phase monitored and switched PDUs featuring a mobile-friendly, HTML 5-based LX Platform interface along with an easy-to-use LCD touch screen—ultimately offering improved load monitoring capabilities to users.
Finalist: Vertiv Liebert EXS
Aimed at small spaces, Vertiv’s Liebert EXS is a compact-size UPS system. The system fuses the UPS with batteries, maintenance bypass, distribution and communications; offers capabilities for supporting single and three-phase critical loads; and delivers strong power-per-unit results.

PRINTERS
HP PAGEWIDE ENTERPRISE COLOR FLOW MFP 785Z+
WINNER: OVERALL
HP Inc. continued to push the envelope with its PageWide technology for speedy, low-cost color printing, with the past year’s release of the PageWide Enterprise Color Flow MFP 785z+. The multifunction printer delivers print speeds of up to 75 pages per minute for either color or black and white. The device also comes with HP’s promise of the lowest color print costs in the industry thanks to the company’s advancements in PageWide printing and toner, along with HP’s robust print security capabilities including Sure Start self-healing BIOS. “I think the PageWide technology is a game-changer,” said Skip Tappen, CEO of Waltham, Mass.-based NWN. “Combined with the security of their devices, [it] really sets them apart from the competition.”
Finalist: Brother MFC-L2750DW
Brother recently introduced new laser MFPs including the MFCL2750DW and MFC-L2750DW XL, which offer print speeds of up to 36 pages per minute, paper capacity of 250 sheets, improved productivity via a 50-sheet automatic document feeder, and cloud connectivity through a 2.7-inch touch screen.
Finalist: Epson WorkForce Enterprise WF-C17590
Epson recently launched a new high-performance A3 inkjet multifunction printer, the WorkForce Enterprise WF-C17590, targeted as an affordable color option. The WorkForce Enterprise WF-C17590 offers print speeds of up to 75 pages per minute along with a paper capacity of 5,350 pages.
Finalist: Lexmark CX620 Series
Lexmark’s recently released CX620 Series of A4 color multifunction printers offers impressive speeds (up to 40 pages per minute) and scanning (up to 100 pages per minute for two-sided scanning). Other key features include a steel frame for added durability.
Finalist: Xerox Iridesse Production Press
Xerox says it has achieved a “first in the world of print” with the Iridesse Production Press—a six-station color press combining four-color printing with up to two specialty dry inks in a single printing pass. The press also offers rapid print speeds of up to 120 pages per minute.

PUBLIC CLOUD
MICROSOFT AZURE PLATFORM UPDATES
WINNER: OVERALL
Major upgrades to Microsoft’s Azure cloud platform over the past year have included improved capabilities for helping customers meet compliance standards, with templates offered for each customer’s compliance needs and a report on whether those standards are being met—along with changes to configurations that will help meet the compliance standards. “There used to be a significant level of effort to document and determine whether you are compliant,” said Bob Ballard, principal cloud strategist at Germantown, Md.-based Planet Technologies. “Basically, it’s starting to become plug and play.” Microsoft’s launch of Windows Virtual Desktop—which reduces desktop virtualization complexities with a new virtualized Windows and Office experience on Azure—has also been a key addition. It provides customers with the long-sought after “zero-touch desktop” solution, Ballard said. In conversations, “almost every customer has talked about it,” he said.
Subcategory Winner—Customer Demand: AWS Elastic Compute Cloud Updates
Recent updates to the Elastic Compute Cloud from Amazon Web Services include a greater choice of EC2 instances—such as compute-intensive instances (which run at up to 4GHz), memory-optimized instances (which run at up to 3.1GHz) and memory-optimized instances paired with local NVMe storage.
Subcategory Winner—Technology: Google Cloud Platform Updates
Recent enhancements for the Google Cloud Platform have included a new SAP solution set (for tasks such as automated invoice processing), new distributed ledger technology solutions and a new VMware plug-in for vRealize Orchestrator, which lets customers use GCP alongside their on-premises VMware environment.
Finalist: IBM Cloud Updates
IBM Cloud’s recent expansion included the addition of 18 new availability zones—isolated instances of cloud inside a data center region—with new U.S. availability zones in Washington, D.C., and Dallas. Other IBM Cloud upgrades have included new capabilities to deploy Kubernetes clusters across multiple availability zones.
Finalist: Oracle Cloud Platform Updates
New services introduced for the Oracle Cloud Platform over the past year included the world’s fastest compute processors and world’s fastest graphics processors for machine-learning workloads, according to the company. Oracle says its cloud also now offers the industry’s fastest block storage for I/O-intensive applications, such as databases.

SECURITY-CLOUD
SYMANTEC CLOUD WORKLOAD PROTECTION SUITE
WINNER: OVERALL
Symantec’s Cloud Workload Protection Suite offers advanced capabilities for securing and monitoring critical workloads wherever they are—public clouds, private clouds and on-premises data centers—from a single intuitive console. The suite works with the three major public cloud platforms—Amazon Web Services, Microsoft Azure and Google Cloud Platform. At Torrance, Calif.-based Aurora, CEO Philip de Souza said that “many of our customers have been aggressively transitioning to the benefits of cloud-based infrastructure like AWS, Azure and Google Cloud.” But security teams are wondering how to implement the same kinds of security measures that are protecting their on-premises systems, he said in an email. “This new announcement from Symantec offers the tools our customers need to extend that protection to the cloud,” de Souza said.
Subcategory Winner—Technology: Check Point CloudGuard
Check Point Software Technologies’ CloudGuard can protect enterprises against cyberattacks on cloud infrastructure workloads, as well as Software-as-a-Service applications. CloudGuard integrates with Infastructure-as-a-Service cloud platforms and cloud-based SaaS providers to protect any cloud, service or application against sophisticated breaches, malware and zero-day attacks.
Finalist: McAfee Cloud Security Platform Updates
Recent enhancements to McAfee’s cloud security offerings have included the introduction of the McAfee CASB Connect Program, which the company says is the first self-serve framework in the cloud security industry. Service providers and partners can build API connectors to the McAfee Skyhigh Security Cloud within days without writing code.
Finalist: Netskope Cloud Security Platform Updates
Cloud access security broker Netskope has expanded its platform with added Infrastructure-as-a-Service security through the introduction of enhanced capabilities for continuous security assessment and monitoring. The updates help tackle issues such as infrastructure misconfigurations and vulnerabilities that can lead to compromised security.
Finalist: SonicWall Capture Cloud Platform
The SonicWall Capture Cloud Platform tightly integrates security, management, analytics and real-time threat intelligence across the company’s portfolio of network, email, mobile and cloud security products. Machine-learning algorithms are used to analyze data and classify and block known malware before it can infect the network.
SECURITY-ENDPOINT
SOPHOS INTERCEPT X UPDATES
WINNER: OVERALL
Sophos Intercept X now incorporates deep-learning technology to boost malware detection rates—making it the only product in the world to combine machine learning, malware and exploit blocking, and ransomware protections into a single offering. The addition of deep learning makes it possible for Sophos Intercept X to curate and label data even more accurately. It also provides an additional safety net by ensuring that anything that matches known malware will not be allowed to execute, said Tim Foley, information security director at Rockville, Md.-based Dataprise. “Customers don’t want to hear that I gave them one chance to stop something,” Foley said. “They want me to give them four or five chances to stop it.”
Finalist: CrowdStrike Falcon X
With Falcon X, CrowdStrike enables the automation of threat analysis while helping to deliver customized intelligence and Security Operations Center automation. The product brings together malware sandboxing, malware search and threat intelligence into an integrated offering that can perform comprehensive threat analysis in rapid fashion.
Finalist: CylanceOptics Updates
CylanceOptics by Cylance offers zero-latency, artificial intelligencedriven threat detection and response for the endpoint. The product brings automated incident prevention to the Security Operations Center by incorporating artificial intelligence-based incident prevention targeting fileless attacks, malicious one-liner commands and suspicious application behavior.
Finalist: Kaspersky Endpoint Security For Business Updates
Recent updates to Kaspersky Endpoint Security for Business brought enhancements around machine learning for real-time detection of malicious behavior, along with advancements in exploit prevention and automated vulnerability elimination. Kaspersky has also done a full redesign on the product’s user interface for improved visualization of protection layers.
Finalist: McAfee Endpoint Security Updates
Updates to McAfee’s endpoint security offerings include MVision Endpoint, a new product for Windows 10 designed to leverage the native Microsoft security capabilities of Windows Defender. Security settings can be managed from the company’s Software-as-a-Service management offering, the ePolicy Orchestrator.
SECURITY-NETWORK
SOPHOS XG FIREWALL UPDATES
WINNER: OVERALL
Sophos XG Firewall Version 17 stands out by filling gaps in areas that firewalls traditionally have lacked visibility or capability around. A marquee feature is the new Synchronized App Control capability, which leverages information from the endpoint to classify previously unclassified network traffic and applications through the firewall. Sam Heard, president of Lakeland, Fla.-based Data Integrity Services, said Synchronized App Control helps fill a gap for customers around application classification. “That feature will be a game-changer,” Heard said. “I don’t think anyone else can do what they are doing with the endpoint and the firewall.”
Subcategory Winner—Technology: Fortinet FortiOS 6.0
Fortinet’s FortiOS 6.0 offers centralized management across the entire portfolio from a management analytics and SIEM perspective. The company’s SD-WAN toolset leverages path-aware intelligence to ensure customers are getting appropriate service to crucial applications. FortiOS 6.0 also expands its cloud connectors to include visibility into private, public and SaaS clouds.
Subcategory Winner—Customer Demand: Palo Alto Networks PAN-OS 8.1
Recent enhancements in PAN-OS 8.1 from Palo Alto Networks include key capabilities such as easier adoption of SSL-decryption in multivendor environments; simplified management and operations for large, distributed deployments; advanced threat detection and prevention; and collection of rich data for analytics.
Finalist: Cisco Meraki Insight
Leveraging advanced technologies in deep packet inspection and network performance monitoring, Cisco Meraki Insight enhances the security of networks by enabling IT administrators to more quickly isolate network or application problems that originate outside the local-area network.
Finalist: Forcepoint Dynamic Data Protection
Through leveraging human-centric behavior analytics, Forcepoint Dynamic Data Protection continuously assesses risk and automatically provides proportional enforcement that can be dialed up or down. The product’s automated enforcement capabilities ultimately free up security analysts to focus on higher-value activities.

SECURITY-WEB AND EMAIL
PROOFPOINT TARGETED ATTACK PROTECTION UPDATES
WINNER: OVERALL
Proofpoint’s Targeted Attack Protection Isolation offering separates web content to provide corporate users with safe and anonymous access to web and internet browsing while protecting the endpoint and the corporate network. Recently introduced Targeted Attack Protection sandbox environments feature enhanced phishing detection capabilities that catch a wider variety of phishing attacks while speeding up scanning and response times. Notably, Proofpoint’s Targeted Attack Protection also integrates with the Palo Alto Networks’ WildFire malware analysis service. Chuck Crawford, co-founder and chief strategy officer of Kansas City, Mo.-based Fishtech, called the integration a “big differentiator” for Proofpoint. Targeted Attack Protection provides “holistic visibility” to security teams, Crawford said, giving a “far more consolidated view of what else is going on in their network.”
Subcategory Winner—Revenue and Profit: SonicWall Email Security 9.2
With version 9.2 of SonicWall’s Email Security offering, the company has introduced new capabilities for quarantining and blocking emails with malicious URLs while also integrating with Google G Suite for improved data loss prevention and advanced threat protection.
Subcategory Winner—Technology: Barracuda Cloud-Delivered Web Application Firewall
The recent release of Barracuda’s Cloud-Delivered Web Application Firewall (WAF)—which the company describes as “WAF-as-aService”—offers protection for web applications and websites against attacks such as DDoS, zero-day and SQL injection, while enabling a self-managed approach and simplified deployment.
Finalist: Mimecast Domain Name System Security Gateway
The Mimecast Domain Name System (DNS) Security Gateway guards against malicious activity initiated by user action or malware while blocking access to websites deemed unsafe or inappropriate. Combining Mimecast DNS Security Gateway with the Mimecast Secure Email Gateway services, the offering is easy to deploy and protects against the prevalent cyberattack vectors of email and web.
Finalist: Trend Micro Writing Style DNA
Trend Micro Writing Style DNA sounds the alarm when emails are suspected of impersonating an executive or another high-profile user as part of a business email compromise attack. The product uses artificial intelligence to “blueprint” a user’s style of writing—and sends out warnings when an email is suspected of impersonating a high-profile user.

SMARTPHONES
SAMSUNG GALAXY NOTE9
WINNER: OVERALL
Samsung’s productivity-focused Galaxy Note9 features a large 6.4-inch Super AMOLED display along with a new version of the S Pen that connects to the Note9 over Bluetooth. Now, the button on the S Pen can be used to open apps and take certain actions within apps, such as scrolling through PowerPoint slides. Also with the Galaxy Note9, Samsung has made it easier to use its DeX Android desktop by building the technology right into the smartphone. The Note9 “offers desktoplike capability through DeX, which allows for widespread enterprise usage,” said Marco Nielsen, vice president of managed mobility services at Norcross, Ga.-based Stratix, in an email. “This feature is paramount for enterprise mobile devices and begs the question, ‘Do you really need a laptop with DeX?’”
Finalist: Apple iPhone X
Along with pioneering the nearly edge-to-edge iPhone display (aside from the camera notch), the 5.8-inch iPhone X has offered notable features such as wireless-charging capabilities and a dualcamera setup. The iPhone X also introduced Apple’s FaceID facial recognition technology for unlocking the device, taking the place of TouchID fingerprint recognition.
Finalist: BlackBerry Key2
With the BlackBerry Key2, the biggest differentiator is the inclusion of a physical keyboard, which doubles as a trackpad for tasks such as scrolling. Other top features include the first-ever dual-camera setup on a BlackBerry device and battery life of up to 25 hours per charge.
Finalist: Google Pixel 2 XL
Google’s 6-inch Pixel 2 XL offers a small bezel around its OLED display, while its 12.2-megapixel rear-facing camera comes with features including improved autofocus and a new type of portrait mode. Importantly, the Google Assistant is also built into the Pixel 2 XL.
Finalist: OnePlus 6
Along with a sizable AMOLED display (6.28 inches) featuring high resolution, the OnePlus 6 brings terrific performance thanks to its Snapdragon 845 processor and up to 8 GB of RAM. Other key elements include a dual rear camera system with features such as automatic photo enhancement.
SOFTWARE-DEFINED NETWORKING
CISCO SD-WAN
WINNER: OVERALL
With the integration of the acquired Viptela software-defined widearea networking onto Cisco’s IOS XE software, Cisco is bringing SD-WAN to 1 million existing routers—and many more new devices to come. Key capabilities of the end-to-end platform include centralized management and visibility, optimized connectivity and automated workflows. Historically, WAN has been among the “worst offenders” in creating overhead complexity, said Greg Stemberger, technical director for the NextGen networking practice at Herndon, Va.-based Iron Bow Technologies. With Viptela offering “an intelligent software stack that simplifies and automates how you manage all of that— and at the same time delivering that on [Cisco’s] best-of-breed hardware—that’s a very compelling story. And we’re seeing a lot of interest,” Stemberger said.
Finalist: Big Switch Networks Big Cloud Fabric
Big Switch Networks recently enhanced its Big Cloud Fabric with the addition of support for VMware vSAN, Dell EMC ScaleIO and Nutanix hyper-convergence offerings—making major strides in visibility and simplicity for Big Switch’s software-defined networking switching fabric.
Finalist: HPE Aruba Software-Defined Branch
HPE Aruba’s Software-Defined Branch offering combines branch gateways and headend gateways with existing HPE Aruba technology—including ClearPass policy management software—to form an integrated SD-WAN, WLAN, LAN and security solution. Key benefits include the ability to simplify rules enforcement within the branch.
Finalist: Silver Peak Unity EdgeConnect Updates
For the new generation of its Unity EdgeConnect SD-WAN, Silver Peak has introduced powerful new capabilities including segmentation—enabling organizations to segment users, applications and wide-area network services into secure zones while also automating the steering of application traffic to meet security and regulatory policies.
Finalist: VMware NSX Updates
Recent updates to VMware NSX have included the introduction of NSX Cloud, which provides consistent networking and security for applications running in both private VMware-based data centers and natively in public clouds. Meanwhile, NSX SD-WAN by VeloCloud provides assured application performance from the data center to the branch to the cloud with end-to-end segmentation.
SOFTWARE-DEFINED STORAGE
VMWARE VSAN 6.7
WINNER: OVERALL
VMware revamped its software-defined storage portfolio this year with the launch of vSAN 6.7, offering new features including an HTML 5 user interface and the ability to integrate its performance and capacity monitoring capabilities with VMware’s vCenter management platform. Version 6.7 was designed to bring more workloads to the platform with an emphasis on cloud-native applications. The integration of vSAN to vCenter is a welcome move, said Michael Strong, co-owner and partner at Lubbock, Texas-based Blue Layer IT. “VMware administrators spend the bulk of their time in vCenter,” he said. “That’s why so [much] third-party software is written to vCenter. This is eliminating silos. The Holy Grail for admins is everything within a single pane of glass.”
Subcategory Winner—Technology: Microsoft Storage Spaces Direct Updates
Microsoft recently enhanced its Storage Spaces Direct offering with upgrades including the ability to pool up to 4 PB of drives per cluster (up from 1 PB previously), as well as built-in detection of drives with abnormal latency and a larger number of validated hardware choices.
Subcategory Winner—Customer Demand: NetApp Cloud Volumes
NetApp Cloud Volumes is a fully managed, cloud-native service that allows quick access to data in the cloud. Cloud Volumes allows customers to take advantage of enterprise file services natively on public clouds—like NetApp’s OnTap operating system does—but does not require customers to use OnTap.
Finalist: Dell EMC Elastic Cloud Storage Updates
Dell EMC’s Elastic Cloud Storage is a cloud-scale object storage platform that brings the availability and serviceability of traditional storage arrays to commodity server infrastructures in a private cloud offering. The platform provides comprehensive protocol support for unstructured object and file workloads on a single platform that lets customers manage globally distributed storage infrastructure under a single global namespace with access to content anywhere.
Finalist: IBM Spectrum Storage Updates
Recent updates to the IBM Spectrum suite of software-defined storage products include new data deduplication features for the Spectrum Virtualize data management offering and the expansion of Spectrum Virtualize for Public Cloud to support eight-node clusters.

TABLETS
SAMSUNG GALAXY TAB ACTIVE2
WINNER: OVERALL
Aimed at verticals including manufacturing and transportation, Samsung’s Galaxy Tab Active2 is a rugged 8-inch Android tablet that is the first LTEenabled tablet from the company to be sold exclusively by the channel. The Tab Active2 is water- and dust-resistant and meets a variety of military ruggedness standards, while also enabling use with many types of gloves. The Tab Active2 offers high brightness on the display of 480 nits, as well, along with a removable battery for extending the tablet’s battery life. “The Galaxy Tab Active2 has increased durability for optimal usage on nearly any job site,” said Marco Nielsen, vice president of managed mobility services at Norcross, Ga.-based Stratix, in an email. “Adjacent technologies with vendors like ScanIt make the Tab Active2 a strong play for multiple use cases.”
Finalist: Dell Latitude 5290 2-in-1
Dell’s Latitude 5290 2-in-1 tablet weighs just 2.64 pounds with its keyboard, offers up to quad-core Intel Core processors, and has both USB-C and USB-A ports. The tablet also includes a highly adjustable kickstand. For the 12.3-inch display, the tablet features FHD resolution and Gorilla Glass 4 for durability.
Finalist: HP Elite x2 1013
HP Inc.’s Elite x2 1013 stands out from other 2-in-1 tablets by offering advanced security capabilities such as HP Sure Start selfhealing BIOS and the Sure View integrated privacy screen. The 13-inch tablet also features eighth-gen Intel Core vPro processors and a keyboard with dedicated keys for launching meetings.
Finalist: Lenovo ThinkPad X1 Tablet, Third Gen
Lenovo’s latest X1 Tablet has been redesigned to have a 13-inch display, compared with the 12-inch display of the previous version. The display features 3,000 x 2,000 resolution and includes Gorilla Glass for durability while offering up to 9.5 hours of battery life—as well as a sturdy detachable keyboard.
Finalist: Microsoft Surface Go
At 10 inches, the Surface Go is Microsoft’s smaller and more affordably priced addition to the Surface lineup. The display resolution on the Surface Go is 261 pixels per inch—on par with the Surface Pro—while the tablet promises up to nine hours of battery life.