The 2019 Tech Innovator Awards
The ability to empower solution providers with truly differentiated offerings is the crowning achievement of our Tech Innovator winners and finalists for 2019.

Powering Tech Transformation
Through digital transformation, every company is becoming a tech company. And it's happening fast: The pace of transition to digital has shown no signs of slowing in 2019. Powering this transition are innovative vendors in sectors across the IT industry—and the solution provider partners who bring these differentiated products to end customers.
But what counts as true innovation in 2019? Every tech company promises innovation, but not all deliver. To help with spotting the difference, the 2019 CRN Tech Innovator Awards showcase major advances in key areas including cloud, software, security, infrastructure and devices. The awards this year honor groundbreaking vendors in 38 categories—along with two Editor's Choice awards, given to deserving offerings that did not fit the other categories.
The ability to empower solution providers with truly differentiated offerings is the crowning achievement of our Tech Innovator winners and finalists for 2019, which appear on the following slides.
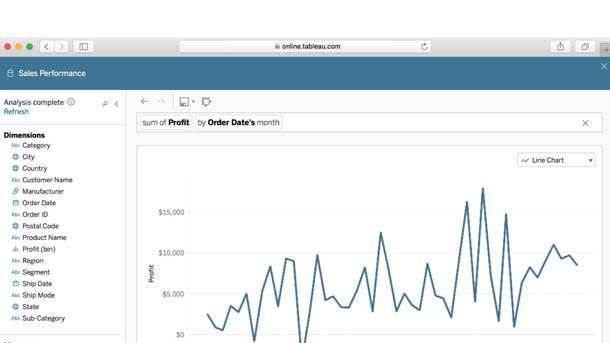
Business Intelligence and Analytics
Winner:
Tableau Software Ask Data
Business analytics firm Tableau, now owned by Salesforce, has added natural language capabilities to its platforms in a move to boost its adoption by a wider audience of business users. With the Ask Data natural language solution, Tableau makes it possible for users to query data in a conversational manner—such as by typing the question "What were our sales in 2017?" and getting an interactive visual response. That makes it easier for more users to engage with the business analytics platform, ultimately developing analytical insight without the need to learn data dimensions, structures or measures.
Finalist:
IBM Watson Studio with AutoAI
Via the addition of AutoAI capabilities to Watson Studio, IBM provides automated analysis of data in order to enable predictive modeling. Model pipelines are generated over time—as the AutoAI algorithms learn about the datasets and uncover transformations and settings that will best address the scenario.
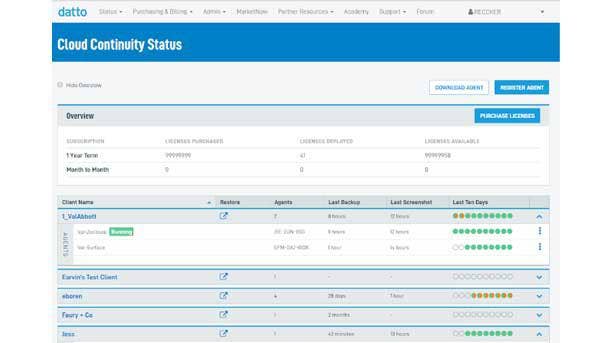
Cloud Data Protection/Disaster Recovery
Winner:
Datto Cloud Continuity for PCs
With Cloud Continuity for PCs, Datto offers an all-in-one business continuity and disaster recovery offering that is image-based and reliable. The offering provides cloud backup, virtualization, screenshot verification and restore capabilities—including locally stored data and files. Key use cases include recovering individual files and folders, rollbacks after ransomware attacks, and restoration following incidents of lost or stolen PCs. Datto's Cloud Continuity for PCs ultimately provides confidence in offering clients protection of Windows 7 and Windows 10 endpoint business data, as well as recovery of the full device configuration, setup and applications.
Finalists:
Quest Software QoreStor 6.0
Quest Software's QoreStor 6.0 provides technologies for high-resilient data deduplication and replication, including cloud tiering for secure long-term data retention. The software-defined offering is capable of running on any appliance, and in any environment whether via cloud or on-premises.
Zerto IT Resilience Platform 7.0
Version 7.0 of Zerto's IT Resilience Platform brings together disaster recovery, backup and cloud mobility into a single platform—a combination of processes that were previously siloed. These capabilities allow for greater efficiency and performance, while also supporting movement between all major cloud providers and private clouds.
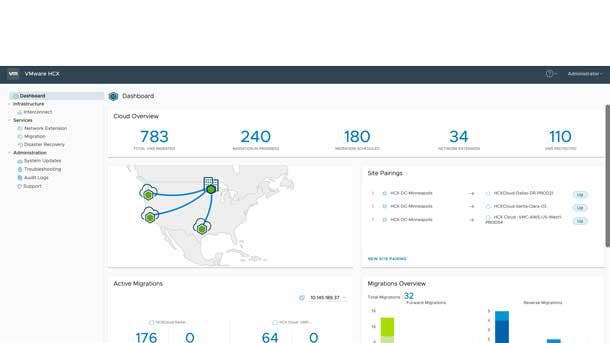
Cloud Migration
Winner:
VMware HCX Enterprise
VMware's HCX provides seamless migration of workloads between public and private cloud environments, without any need for application or configuration modifications. HCX Enterprise marks the introduction of the first stand-alone version of VMware's existing HCX Advanced platform. Key capabilities include migration to VMware vSphere from non-vSphere environments—offering a simplified path to re-platforming applications— along with large-scale bulk migration, enabling the simultaneous migration of hundreds of live workloads without any downtime. Meanwhile, HCX Enterprise features readiness for the Site Recovery Manager (SRM) business continuity and disaster recovery offering—helping to empower customers with their multi-cloud and hybrid cloud transformation initiatives.
Finalists:
BitTitan MigrationWiz
In a recent update to its MigrationWiz solution, BitTitan added capabilities to support migration for the Microsoft Teams collaboration platform. MigrationWiz can now be used to migrate a Teams instance, as well as individual components such as teams, channels, conversations, permissions and files.
iland Cloud iland Catalyst
The iland Catalyst cloud assessment tool improves cloud migrations by avoiding under-provisioning or over-provisioning of cloud resources. Before cloud migration projects even begin, the tool ensures that the target cloud environments will achieve expectations for both application performance and cost.
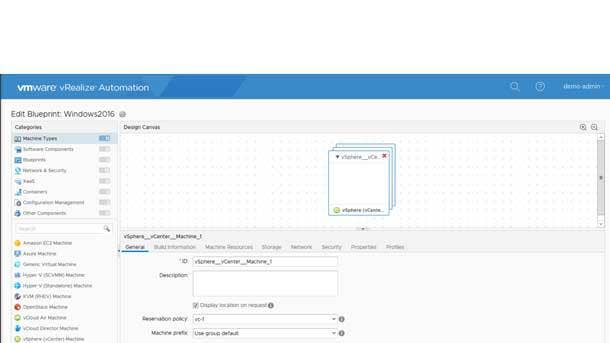
Cloud Platforms
Winner:
VMware vRealize Automation 7.6
VMware's vRealize Automation hybrid cloud automation platform reduces IT complexity in order to increase agility, efficiency and productivity for customers. Version 7.6 of vRealize Automation adds integrations with VMware's software-defined data center stack and management capabilities, enabling simplified automation of hybrid cloud environments. Key elements include an extended integration with VMware NSX Data Center featuring new on-demand support for private networks along with VMware NSX-T and NSX for vSphere configuration for different clusters within a vCenter Server. Meanwhile, vRealize Automation 7.6 makes it easier to build customized and enhanced request forms for catalog items and provides support for multitenancy in vRealize Orchestrator.
Finalists:
Dropbox Business
Recent enhancements to Dropbox Business include integrations with popular products such as Zoom and Google Docs. Other additions include a timelines feature that offers customizable milestones and time frames for team coordination, along with a feature that links video comments to a specific second of the video.
Ivanti Cloud
The Ivanti Cloud platform provides capabilities ranging from real-time intelligence to prescriptive recommendations and the ability to connect data across IT systems. The platform can provide a full view of the current environment while also offering insight such as a reconciled view of devices from disparate data sources.
Sage Intacct Budgeting and Planning
Sage Intacct's Budgeting and Planning cloud offering is aimed at enabling smaller organizations to collaborate on their latest budget or plan in a unified fashion. Capabilities such as bidirectional data synchronization allow for seamless management of actuals, budgets and plans.
Zoho CX Platform
Also known as CRM Plus, the Zoho CX Platform unifies customer touchpoints spanning marketing, sales and support. The platform includes CRM and applications for live chat, marketing automation, project management, customer surveys, customer service, sales-specific email client and sales activity management.
Collaboration Applications and UC
Winner:
Vonage Smart Numbers
Vonage has taken a major step toward enabling businesses to customize their communications applications with the launch of its Smart Numbers offering. Using Smart Numbers, Vonage phone numbers can come with an array of new capabilities by leveraging APIs along with a small amount of coding. By connecting Smart Numbers to a Nexmo voice application, developers can programmatically route calls, create customized apps for communications, easily integrate with third-party systems, and create unique messaging and voice workflows atop UCaaS. The Smart Numbers offering ultimately provides a never-before-seen level of customization and flexibility for modern business communications.
Finalists:
Highfive Premium
For improved videoconferencing, Highfive Premium bundles a 4K HDR camera with WebRTC-based conferencing software. The high-dynamic range camera enables adjustment for difficult lighting, intelligent scene framing and digital pan/tilt/zoom—along with whiteboard framing to provide a clear view of what's been written on a whiteboard.
Intermedia Unite
Recent updates to the Intermedia Unite cloud-based unified communications and collaboration platform have included spam caller protection—for detecting fraudulent and telemarketing calls and allowing users to tag, block or send to voicemail—as well as SMS messaging and two-factor authentication.
PGi GlobalMeet
PGi GlobalMeet's online meetings offering aims to make meetings easier to join, with one-click access from any browser and device. Other key features include high-quality screen sharing, clear audio quality (via PGi's cloud-based audio network) and access to 24/7 global support.
Contact Center Applications
Winner:
8x8 Contact Center
8x8 Contact Center brings together Unified-Communications-as-a-Service and Contact-Center- as-a-Service offerings that are accessible via a single interface. That translates into a single administration portal and single data lake that unifies all reporting—making 8x8 Contact Center a first-of-its-kind collaborative contact center offering. The offering features advanced routing, team messaging, video onferencing and highly intuitive analytics. In addition, quality-management capabilities allow notes to be easily added into interaction recordings along with enabling meaningful insight to be extracted using powerful speech analytics—while customer journey analytics provide greater visibility and expanded coaching capabilities.
Finalists:
RingCentral Engage Digital
RingCentral's Engage Digital offering empowers agents to interact with customers across more than 20 digital channels on a single desktop. Key capabilities include aggregation and filtering of all incoming messages, creation of a unified profile for each customer, and automated allocation of the customer to the correct agent.
Zoom International Eleveo WFM
With its Eleveo WFM (Workforce Management) software for the contact center, Zoom International enables simplified shift planning, improved engagement with agents and, ultimately, happier end customers. The cloud-based product provides streamlined forecasting, offering simplified workflows in place of complex rules engines and input requirements.

Container Technology
Winner:
Pivotal Container Service
Pivotal Software rolled out numerous enhancements in version 1.3 of the Pivotal Container Service, the company's popular enterprise Kubernetes platform. For starters, the update to the Pivotal Container Service, also known as PKS, brings in support for version 1.12 of the Kubernetes container orchestration system. Full production support for the Microsoft Azure and Amazon Web Services cloud platforms is also included—with PKS 1.3 enabling greater flexibility in moving between cloud providers. PKS 1.3 enables self-serve provisioning of Kubernetes clusters that are fully managed and, ultimately, helps to solidify PKS as a go-to enterprise container offering.
Finalist:
Docker Enterprise 3.0
Docker Enterprise 3.0 introduces the Docker Kubernetes Service, which provides a consistent Kubernetes stack from the developer's PC to the public cloud. Other new features include an enterprise version of the Docker Desktop platform and Docker Applications, a service for shuttling applications through the development pipeline.

Data Center Infrastructure
Winner:
HPE Nimble Storage dHCI
With HPE Nimble Storage dHCI, Hewlett Packard Enterprise is delivering the first disaggregated AI-powered hyper converged infrastructure (HCI) offering in the industry—combining the flexibility of converged architecture with the simplicity of hyper-converged. The solution disaggregates compute and storage built upon Nimble storage and ProLiant servers while integrating hyper-converged control, offering easier management of virtual machines. HPE Nimble Storage dHCI extends hyper-convergence to workloads with growth rates that are difficult to predict, as well as to applications that are IO-intensive and business-critical—while also providing resource predictions and prescriptive recommendations from HPE's InfoSight AI technology.
Finalists:
Lightbits Labs LightOS
With LightOS, Lightbits Labs offers improved storage disaggregation using NVMe over standard TCP networks and standard server hardware. LightOS enables high-performance, low latency and composable storage, and offers simplified deployment by not requiring infrastructure or application layer changes.
Robin Storage
A container-native storage offering, Robin Storage offers capabilities including automated provisioning, backup and recovery, point-in-time snapshots, quality-of-service, application cloning and multi-cloud migration. Robin Storage promises faster delivery of new features and products, along with improved application provisioning and management.
WekaIO WekaFS
With an eye toward future-proofing of data centers, WekaIO's WekaFS is a scale-out, NVMe-native file storage solution. The high-performance shared and parallel file system is built on novel architecture that's optimized for flash, featuring storage software designed to accommodate intensive workloads.
Data Management
Winner:
Veeam Availability Suite 9.5 Update 4
Data protection and management company Veeam has gone all in on cloud with Update 4 of the Veeam Availability Suite 9.5. The update offers improved cloud tiering and mobility as well as enhanced cloud replication. Veeam improved the offering's scale-out backup repository to allow for backups to the cloud that are based on capacity or time preferences—along with enabling the easy addition of high-performance capacity on-premises. In terms of cloud mobility, Veeam Availability Suite 9.5 Update 4 adds the ability to recover data to work directly on AWS and Microsoft Azure Stack. In addition, the update provides GDPR compliance and malware prevention.
Finalists:
Aparavi Active Archive
With Active Archive, unstructured data management specialist Aparavi provides direct-to-cloud data transfer as well as enhanced data classification, tagging and search. Multi-cloud management capabilities include bulk data migration across clouds and additional cloud destinations—enabling an easier journey toward multi-cloud deployments.
Datrium Automatrix Platform
Through its Automatrix offering, multi-cloud data platform software developer Datrium provides compute, primary storage, backup and disaster recovery from a single offering. Other key capabilities include making workloads portable across clouds, while the platform also offers high performance and end-to-end encryption.
Igneous DataDiscover
Igneous DataDiscover rapidly provides visibility across all NAS systems inside an enterprise, with the ability to have the offering running within minutes. API integrations are available with NAS devices from NetApp, Dell EMC, Pure Storage and Qumulo, and DataDiscover can scan billions of files within hours.
Reltio Cloud
Reltio Cloud, a cloud-native master data management platform, continuously unifies and organizes data from disparate sources while offering highly scalable storage. The platform also stands out with its ability to enable personalized customer experiences and accelerate new product introductions.

Display—Collaboration/Signage
Winner:
Samsung Flip 2 65-Inch
Following last year's introduction of the 55-inch Samsung Flip interactive digital display, Samsung this year launched a 65-inch model with improved collaboration and usability capabilities. A partnership with Cisco enables support for videoconferencing with Cisco's Webex Room Kit Series, providing high-quality video collaboration across disparate locations. The latest Samsung Flip also includes connection to popular cloud-based offerings such as Office 365 and enhances the usage experience with features such as brush mode, which allows for varying pen thicknesses. In addition, Samsung removed unnecessary space between the 65-inch Flip display and the wall for more-appealing aesthetics.
Finalist:
Userful Visual Networking Platform
The Userful Visual Networking Platform is a software offering that enables delivery of content from multiple sources to a combination of screens, all in real time. The offering leverages a central computing server for enhanced management and enablement of varying visual applications.

Display—Monitor
Winner:
HP EliteDisplay E243p Sure View Monitor
This year, HP Inc. announced the expansion of its Sure View integrated privacy screen beyond the notebook. The company unveiled the EliteDisplay E243p Sure View Monitor as the first 23.8-inch monitor with Sure View, a display technology that enhances privacy by reducing almost all visible light when the screen is viewed at an angle. The display also features FHD resolution and a slim bezel on three sides of the screen. In addition, the EliteDisplay E243p Sure View Monitor is highly adjustable with the ability to tilt, pivot and swivel the display, while also adjusting its height by up to 5.9 inches of variability.
Finalist:
HP S14 Portable Monitor
With the EliteDisplay S14, HP has the first-ever 14-inch USB-C portable display on the market. The display features FHD resolution and runs off USB-C, meaning that users can just connect one end of a USB-C cable to a laptop and the other end into the display.

Edge Infrastructure
Winner:
Scale Computing HE500 Series
Designed to provide easy-to-deploy and reliable infrastructure at the edge, Scale Computing’s HE500 series delivers highly available offerings suited for remote multisite deployments. The series is a set of hyper-converged infrastructure appliances that provide enterprise-class features to remote locations and boost edge computing capabilities with disaster recovery. The HE500 includes Scale Computing’s HC3 HyperCore Software, which provides an automated layer to create simple-to-operate functionality along with the performance to meet modern edge computing requirements. The offerings promise almost instant failover and minimal downtime while also being able to run disaster recovery workloads reliably.
Finalists:
APC by Schneider Electric HyperFlex for the Edge
With HyperFlex for the Edge, APC by Schneider Electric brings together its physical infrastructure with Cisco's HyperFlex hyper-converged infrastructure system. The edge offering is pre-integrated at the factory, while also offering remote monitoring and management capabilities along with physical security.
Opengear ACM7000-L Resilience Gateway
For customers with branch offices, retail stores and other edge sites, Opengear's ACM7000-L Resilience Gateway provides strong network continuity. The offerings global modem offers fast installation while providing capabilities such as smart failover to cellular to reduce network outages.
IT/Application Automation
Winner:
Puppet Enterprise 2019.1
Bringing together both remote agentless and agent-based solutions, Puppet Enterprise offers comprehensive automation of IT systems along with efficient extension of changes across infrastructure. Puppet enables fast movement of workloads across cloud, hybrid or container infrastructure, and allows for scaling of DevOps along with maintaining compliance. With Puppet Enterprise 2019.1, the offering adds capabilities such as impact analysis—which lets IT teams assess the impact of a potential code change prior to deployment. The offering also provides enhanced integration with Puppet's Bolt agentless automation tool for upgrading Kubernetes clusters and making changes to large groups of servers.
Finalists:
AutonomIQ ATOM Platform
With its ATOM (Autonomous Testing and Operations Management) platform, AutonomIQ leverages AI and machine learning to enable autonomous application testing and operations capabilities—leading to benefits such as dramatic reduction in human effort and generation of data sets for validation of application flows.
Bonitasoft Bonita Cloud
Aimed at both professional and citizen developers, Bonitasoft's offerings enable rapid delivery of automation projects and applications using DevOps. The managed Bonita Cloud edition of the company's digital process automation platform is fully operated by Bonitasoft with a dedicated operations support team.
Functionize
Functionize, a cloud-based platform leveraging a variety of AI capabilities, provides autonomous testing that can be harnessed by nontechnical business users to create test cases describing an application. The offering provides test creation and maintenance, along with a full storage and execution infrastructure.
Refactr Platform
A visual application for the creation of software-defined offerings, Refactr Platform focuses on the design and delivery of cloud infrastructure and applications. The platform features minimal setup and easy deployment of solutions, while also enabling users to meet strong security requirements.
IT Infrastructure Monitoring
Winner:
LogicMonitor
This year, LogicMonitor added new capabilities to help MSPs monitor and pull out actionable information on their microservices and containerized applications. LogicMonitor's flagship platform added Kubernetes support—which provides health metrics and performance data for all aspects of the Kubernetes cluster—and added LM Service Insight, which brings together performance indicators across grouped resources to monitor and alert on the performance of the overall container service. The updates ultimately connect the dots for MSPs by providing context around their alerts, so they can see exactly how a hardware or connection issue is impacting services or applications.
Finalists:
New Relic One
New Relic One aims to stand out from other monitoring platforms bringing together all of a business' systems, teams and technology into a single view—enabling distributed teams to centrally manage their software and bring in more automation.
OpsRamp
The OpsRamp platform helps IT teams discover assets across hybrid environments, then manages, monitors and automates service delivery. The multi-cloud infrastructure monitoring platform is optimized with AI technologies, including an inference engine that ingests and correlates alert data from multiple sources.

Mobile Devices
Winner:
Samsung Galaxy Note10
Samsung is continuing to launch new business-friendly features in the smartphone form factor with the latest update to its Note series, the Galaxy Note10. Key features on the 6.3-inch device include easier connectivity from the phone to the DeX Android desktop. With the Note10, users can access their DeX desktop on a PC or Mac by plugging into the computer using a USB-C to USB-C cable that is included with the phone. On performance, the Note10 moves up to the Qualcomm Snapdragon 855, offering performance gains of 33 percent over the Note9. Samsung also opened an SDK enabling third-party developers to create new app features that make use of the S Pen stylus.
MSP Technology
Winner:
Microsoft Azure Lighthouse
As the Azure cloud platform continues to grow as an opportunity for MSPs, Microsoft recently introduced the Azure Lighthouse control plane for managing Azure. The offering allows MSPs to view and manage Azure deployments at scale, and across all customers. Lighthouse provides an improved managed Azure experience--offering enhanced automation, efficiency and security. Azure Lighthouse's capabilities include cross-tenant management of customers with improved visibility and control, enabling MSPs to service more customers and larger workloads. Ultimately, Azure Lighthouse promises to dramatically reduce customer on-boarding time while bringing all customer estates into a single view.
Finalists:
Kaseya IT Complete
Kaseya's IT Complete platform provides offerings for MSPs including remote monitoring and management, security, backup and disaster recovery, compliance, professional services automation and automated IT documentation. The fully integrated suite can be implemented from a single, unified interface.
Nerdio Azure Cost Estimator
Nerdio's Azure Cost Estimator is an easy-to-use tool providing MSPs with a full understanding of the costs of managed services in Azure. The offering factors in customized use cases and tallies the cost of components such as Office 365, VDI and Windows servers.
WatchGuard Cloud
WatchGuard Cloud centralizes security management and reporting of all WatchGuard security services into a single cloud-based interface. The platform simplifies how MSPs protect customers while reducing infrastructure costs and delivering scalability through multitier, multitenant capabilities.
Networking
Winner:
AppDynamics for Cisco Application Centric Infrastructure
With AppDynamics for Cisco Application Centric Infrastructure, Cisco Systems brings together application intelligence from AppDynamics and its software-defined networking offering, ACI. AppDynamics for Cisco Application Centric Infrastructure is a monitoring offering that provides end-to-end transaction tracing and correlated data models that can help users to zero in on issues in the network that are impacting application performance. The offering enables transactions to be followed through the application across multi-cloud environments and all network locations. AppDynamics for Cisco Application Centric Infrastructure provides the IT team with crucial visibility into how network policies impact application performance, offering a faster path to remediation of performance impacts.
Finalists:
Fortinet Secure SD-Branch
For distributed enterprises, Fortinet's Secure SD-Branch provides a unified WAN edge and secure Wi-Fi with switching and network access control. The offering secures the WAN and access edge in integrated fashion from a single console, extending Fortinet's Security Fabric to network access.
Opengear Lighthouse Enterprise
With its Lighthouse Enterprise platform, a centralized out-of-band management offering, Opengear provides end-to-end network control with a focus on scalability and network resilience. Lighthouse Enterprise enables users to automate, monitor and manage both data centers and edge device networks using a single platform.
VMware Smart Assurance
Smart Assurance, part of VMware's teleco mportfolio, is helping enable the migration to 5G with service impact and root-cause analysis capabilities. The offering provides visibility across physical and virtual networks along with multi-cloud environments, and uncovers key information such as how resources are being consumed.
Zyxel Smart Managed Switches for Surveillance
Zyxel's recently launched portfolio of surveillance switches includes the GS1350 series of 5-, 8-, 16- and 24-port managed switches. Internal power supplies for simplified installation and features such as extended range mode allow the switches to help ease deployment and management for IP cameras.
Networking SD-WAN
Winner:
Fortinet Secure SD-WAN
Fortinet Secure SD-WAN brings together SD-WAN with advanced firewall, routing and WAN optimization to drive highly secure networking for customers. Benefits of the integrated offering include improved performance, reduced cost, optimized cloud connectivity and simplified operations. Earlier this year, Fortinet debuted the industry's first SD-WAN ASIC chip, enabling the company's FortiGate 100F firewall to deliver performance that's up to 10 times faster than the competition. The SD-WAN ASIC ensures that applications get to the right place as quickly as possible with a high degree of security and quality. The ASIC chip can run and define applications rapidly while at the same time applying leading security practices, such as SSL inspection.
Finalists:
Infovista Ipanema SD-WAN
Combining sophisticated software and orchestration technology with a versatile delivery model, Infovista's Ipanema SD-WAN offering aims to provide enterprises with full WAN visibility and control. Key capabilities include intelligent, automated directing of application traffic at the session level based upon performance requirements.
Teridion For Enterprise
Cloud-based WAN offering Teridion for Enterprise stands out by delivering performance backed by service-level agreements along with the reliability of MPLS and other legacy WAN technologies, all combined with key benefits of the public cloud such as elastic scale, agility and global reach.
WatchGuard Fireware 12.3
With version 12.3 of Fireware for Firebox Unified Security Platform appliances, WatchGuard provides dynamic path selection capabilities for optimizing WAN resources across complex networks, while also securing branch locations with unified threat management. The offering ultimately supports zero-touch SD-WAN deployments for MSPs and customers.
CyberaOne
A managed application network and security services platform, CyberaOne provides secure, automated SD-WAN capabilities that are purpose-built for highly distributed businesses. The offering is focused on supporting businesses that depend upon IoT devices and remote, small-footprint sites.
Networking —Wireless
Winner:
Cradlepoint NetCloud Service
In keeping with its "pathway to 5G" initiative, Cradlepoint has introduced a series of private LTE offering that leverage the company's NetCloud service, Gigabit LTE edge routers and 3.5GHz Citizens Broadband Radio Service (CBRS) shared spectrum. Through its NetCloud Service with Gigabit-Class LTE Edge Routers for Branch and Mobile Networking, Cradlepoint is blazing the trail on offering cellular network edge offerings that support AT&T and Verizon LTE Advanced networks with Gigabit LTE capabilities. Targeted at primary and failover WAN connections, the wireless network offerings are 5G-ready for locations where 5G services become available.
Finalist:
WatchGuard AP125 with Wi-Fi Cloud
By pairing its AP125 802.11ac Wave 2 access point with its Wi-Fi Cloud management platform, WatchGuard is enabling MSPs and customers with a range of powerful capabilities. Those include wireless intrusion prevention technology, intelligent wireless network visibility, location-based analytics, customizable reports and marketing analytics tools.

PC—Desktops
Winner:
Lenovo ThinkCentre M90n Nano
Lenovo has launched a new desktop product category with the ultra-small ThinkCentre M90n Nano desktop—which is significantly smaller than even Lenovo's small-form-factor ThinkCentre Tiny desktop offerings. While the Tiny features a 1-liter design, the Nano is about a third of that size while still offering strong performance. The 0.35-liter Nano has a height of 0.86 of an inch, a depth of about 3.5 inches and a width of 7 inches—making it not much larger than some smartphones. The Nano offers powerful processors from Intel's Whiskey Lake series and offers up to 16 GB of RAM as well as two SSDs.==

PC—Laptops
Winner:
Dell Latitude 7400 2-in-1
Dell's Latitude 7400 2-in-1 represents not only a design overhaul for the Latitude line, but also a big leap forward in capabilities and features for Dell's commercial notebooks. Dell swaps out the usual black carbon-fiber body for brushed aluminum on the Latitude 7400 2-in-1, while a slim-bezel design around the display reduces the overall size of the convertible notebook, improving portability. Battery life can reach up to 24 hours on a charge, meanwhile, and the notebook offers an option for speedy LTE connectivity. The Latitude 7400 2-in-1 also introduces a new feature called Express Sign-In, which detects when users are near and automatically wakes up the PC.
Finalists:
HP EliteBook x360 1040 G6
HP Inc.'s EliteBook x360 1040 G6 stands out by offering expanded battery life at up to 24 hours on a charge. The convertible notebook is also highly portable with a weight of less than 3 pounds, and offers options for a 4K HDR display and up to 32 GB of RAM.
Lenovo ThinkBook 13s/14s
With the recently introduced ThinkBook brand, Lenovo combines many business-friendly elements of the ThinkPad—including strong performance, durability and security—with a sleeker design and a price level meant to appeal to SMBs. The 13.3-inch ThinkBook 13s and 14-inch ThinkBook 14s are also highly portable for SMB-class notebooks.

Power Management
Winner:
Eaton 5P Lithium-Ion UPS
With a focus on meeting the needs of distributed IT and edge computing environments, Eaton's 5P Lithium-Ion UPS advances the company's 5P UPS platform with the addition of new lithium-ion battery technology. Among the enhancements is an on-board battery management system that can provide insight into charge cycles, battery performance, temperature monitoring and overall state of health. Eaton's 5P Lithium-Ion UPS ultimately enables users to stay better informed of their UPS battery's lifecycle. Meanwhile, added network security capabilities—with an optional Gigabit network card that is compliant with UL 2900-2-2 standards—also provide enhanced cyber protect ion and uptime.
Finalist:
CyberPower Smart App Online High-Density UPS Systems
With its Smart App Online High-Density UPS Systems, CyberPower provides assurance of maximum capacity output with a lower space footprint. The systems are capable of configuration as either a 2U rack unit or as a tower unit—in comparison to competing UPS models that need 3U or 4U rack space allotments.

Printers/MFPs
Winner:
HP OfficeJet Pro 9025
With the OfficeJet Pro 9025, HP Inc, brings advanced features and security—along with improved design and speed—to small-business customers. A highlight is the new Smart Tasks feature, which lets users create custom shortcuts such as automatically sending scanned receipt data to QuickBooks. The design has also been redone to give the device a more modern-looking and compact form factor, with the overall size reduced by 39 percent. On security, the OfficeJet Pro 9025 adds enterprise-level security capabilities such as secure boot with self-healing. In addition, the device can print at up to 24 pages per minute (in black and white) or 20 pages per minute in color.
Finalists:
Epson WorkForce Enterprise WF-M20590
Epson America's WorkForce Enterprise WF-M20590 is an A3 multifunction network printer capable of delivering monochrome print speeds of 100 pages per minute. The WF-M20590 also offers a maximum paper capacity of 5,350 pages and uses up to 50 percent less power than monochrome laser printers.
Lexmark MC3224adwe
Lexmark's MC3224adwe multi-unction device comes with powerful features for small businesses including print speeds of up to 24 pages per minute in color along with scanning, copying and faxing capabilities. Other key features include Ethernet and USB connectivity along with wireless printing and scanning to cloud, network or email.

Processors
Winner:
Intel Xeon Scalable, Second Generation
With its second-generation Xeon Scalable processor series, Intel is taking a major leap toward redefining data center performance. The processor family introduces powerful new capabilities to meet the demands of high-performance workloads such as AI. Via Intel's Deep Learning Boost technology, the second-gen Xeon Scalable processors are the first to feature built-in inference acceleration for AI workloads. The highest-performance member of the processor family is the Xeon Scalable Platinum 9200, which offers up to 56 cores along with a unique design where each CPU core has access to expanded memory interfaces. Notably, the second-gen Xeon Scalable series also represents the most comprehensive Xeon stack Intel has ever delivered, with more than 50 standard SKUs and dozens of custom SKUs.
Finalist:
AMD EPYC, Second Generation
AMD is advancing its fight to win data center market share with its second-generation EPYC processors, which are the first 7-nanometer server CPUs and feature up to 64 cores with base frequencies of up to 3.2GHz. The processors are primed to enable high-performance workloads such as artificial intelligence and machine learning.
Security—Cloud
Winner:
McAfee MVision Cloud
With MVision Cloud, McAfee provides data and threat protection across all cloud environments—Software as a Service, Infrastructure as a Service and Platform as a Service—making McAfee the first cloud access security broker (CASB) to accomplish the feat. Leading use cases include enforcement of data loss prevention policies for cloud-based data; prevention of unauthorized sharing of sensitive data; and the blocking of corporate data downloads to personal devices. Other key capabilities include detection of compromised accounts and insider threats, malware detection, encryption of cloud data and auditing of security settings for cloud services. In additon, MVision Cloud has led the way among CASB offerings in terms of supporting Microsoft Teams.
Finalists:
Barracuda Cloud Security Guardian for Azure
As Microsoft's Azure cloud platform continues to grow, Barracuda Networks has launched Cloud Security Guardian for Azure—an agentless offering for providing full visibility and compliance around public cloud workloads. The offering also offers automated remediation as well as security scores and alerts.
Fortanix Self-Defending Key Management Service
Fortanix's Self-Defending Key Management Service provides encryption for cloud-based applications and data, while ensuring full control for customers over their keys and secrets. The offering stands out by using Fortanix's unique runtime encryption technology that leverages Intel Software Guard Extensions (SGX).
Infocyte Managed Detection and Response for AWS
Focused on serving small and midmarket organizations, Infocyte's Managed Detection and Response for AWS offering exposes, investigates and eliminates threats and vulnerabilities, both in AWS and hybrid environments. The offering provides automated inspection of cloud workloads along with continuous activity auditing.
Sophos Cloud Optix
Sophos Cloud Optix provides continuous monitoring, compliance, analytics and remediation across AWS, Microsoft Azure and Google Cloud. The AI-powered tool offers automatic discovery of all public cloud assets through a single console—ultimately delivering continuous visibility of cloud infrastructures.
Security—Email
Winner:
Mimecast Secure Email Gateway
Mimecast has been augmenting its email security offerings with new threat intelligence capabilities, providing specific threat data and analytics for each organization. The company has integrated threat intelligence into its Secure Email Gateway and Internal Email Protect solutions, with a user-friendly dashboard that offers visualizations for threats facing a business. Examples of possible visualizations include malware detections and malware origin by geo-location, or even a visualization showing the users that are the most at-risk within an organization. Mimecast's threat intelligence offerings ultimately help to pinpoint issues that deserve more attention, enabling users to more easily respond to email security threats.
Finalist:
Vade Secure for Office 365
Designed for MSPs, Vade Secure for Office 365 provides AI-based threat detection and automated remediation—protecting SMB customers from email attacks including targeted phishing, spear phishing, malware and ransomware. AI capabilities include machine learning that can detect previously unknown email threats.
Security—Endpoint
Winner:
Sophos Intercept X Advanced with EDR
With the addition of EDR (endpoint detection and response) to Intercept X Advanced, Sophos brings together intelligent EDR with powerful malware detection and exploit protection. By applying deep learning expertise to the EDR space, the product arms companies with threat intelligence and prioritizes alerts that appear to be the most threatening. The EDR tool can also search across the organization to provide a comprehensive view of everything that happened in an attack. Intercept X Advanced with EDR ultimately makes threat tracking accessible even to businesses with limited resources—providing organizations of all sizes with capabilities that are typically only found in a Security Operations Center.
Finalists:
Attivo Networks ADSecure
Attivo Networks' ADSecure offering defends against Active Directory data gathering through being stationed at every endpoint and intercepting queries that attempt to harvest Active Directory data from compromised systems. Capabilities include replying with deceptive data and hiding privileged credentials from attackers.
Carbon Black CB Predictive Security Cloud
Carbon Black (now owned by VMware) brings together a number of advanced security offering with its CB Predictive Security Cloud offering—including next-gen antivirus, endpoint detection and response, virtualized data center security and managed threat hunting. Key capabilities include bringing event stream processing to endpoint security.
Illusive Networks Attack Intelligence System
With Attack Intelligence System, Illusive Networks accelerates and improves incident response through earlier detection, expedited analysis and identification of risk context to quickly determine the escalation path. Key features include trap servers that interact with attackers at the endpoint, along with authentic and scalable decoys.
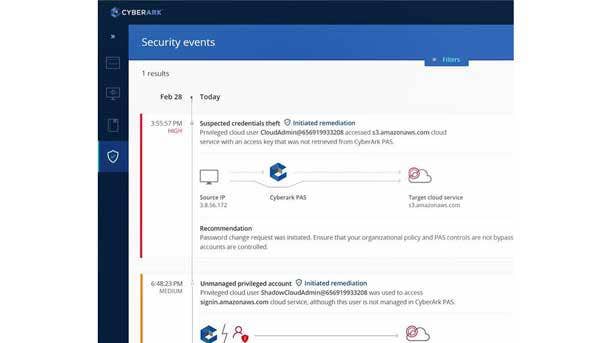
Security—Identity and Access Management
Winner:
CyberArk Privileged Access Security Solution v10.8
Identity and access management specialist CyberArk has upped its cloud game with the latest version of its Privileged Access Security Solution. Key capabilities include detecting and securing access to cloud management consoles, along with securing privileged credentials and applying least privilege to cloud infrastructure. With version 10.8, the offering now enables continuous discovery of unmanaged privileged AWS accounts—and automatically adds to a list of pending approvals to derail misuse. Additional cloud-focused features include securing API keys in a digital vault for cloud applications and workloads. And, CyberArk's offering can apply privileged access security best practices to Software-as-a-Service applications, as well.
Finalists:
Idaptive Next-Gen Access Cloud
A unified platform for identity and access management, Idaptive's Next-Gen Access Cloud offers single sign-on, adaptive multi-factor authentication, user behavior analytics and other capabilities. The platform enables automated on-boarding and off-boarding processes as well as streamlined access provisioning.
Keyfactor Code Assure
For software and firmware developers, digitally signing code is a crucial process to establish trust in the product. Keyfactor's Code Assure enables highly secure code signing, by storing all code signing keys and certificates in a centralized hardware security module with strict access controls.
Okta Advanced Server Access
With Advanced Server Access, Okta is expanding for the first time into infrastructure access with an offering for continuously managing and securing access to Windows and Linux servers—across AWS, Microsoft Azure, Google Cloud and on-premises environments.
One Identity Safeguard
One Identity Safeguard locks down access to privileged account credentials by recording all session data, using machine learning and behavioral biometrics to create a baseline of normal behavior and then halting any behavior that is identified as risky or suspicious.
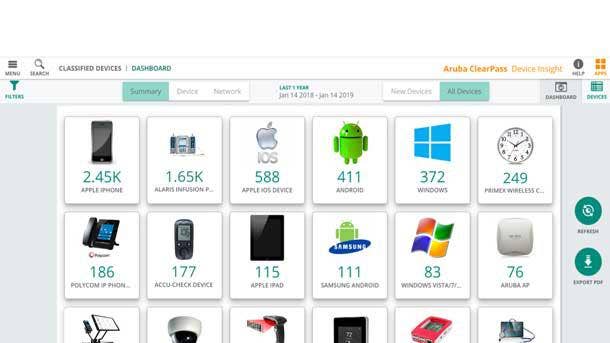
Security—IoT
Winner:
Aruba, a Hewlett Packard Enterprise company ClearPass Device Insight
With ClearPass Device Insight, Aruba uses machine learning to automatically discover and fingerprint all connected devices and IoT endpoints across any wired or Wi-Fi network, regardless of vendor. While businesses could see devices on their networks previously, they often could only see its operating system or behavior—not whether the endpoint was specifically a security camera or a smartwatch, for example. Using ClearPass Device Insight, businesses can now make decisions based on what parts of the network or servers that a device should be able to access (and what parts the device should be blocked from). The cloud-hosted offering gives customers a single, unified vantage point of all endpoints connected to their network.
Finalists:
Extreme Networks Defender for IoT
For endpoints that have nonexistent or limited embedded security capabilities, the Extreme Defender for IoT offering delivers security by adding in-line defense into IoT devices—with simple deployment over any network infrastructure without the need for major network changes.
Forescout Platform
Forescout specializes in providing a device visibility and control platform that covers both IT security and operational technology security, empowering organizations with a complete view of the devices in their environments. Recent updates have included visibility for multi-cloud deployments along with improved auto-classification for industrial and medical devices.

Security—Network
Winner:
Fortinet FortiOS 6.2 and FortiGate E-Series
Fortinet's FortiOS 6.2 update adds hundreds of new features and capabilities, ultimately enabling networking and security to be integrated much more closely together instead of having them positioned as separate organizations or architectures. FortiOS 6.2 automates provisioning and operations to streamline the implementation of new systems and changes to policies, while the offering also now applies AI across all FortiGuard services. Meanwhile, FortiOS 6.2 offers full cloud access security broker capabilities for not only virtual machines, but also for Office 365 and API security components in the cloud. In addition, Fortinet has rolled out the FortiGate E-Series of high-performance, next-generation firewalls—enabling capabilities such as intent-based segmentation.
Finalists:
ExtraHop Networks - Reveal(x) Spring 2019
With its Reveal(x) network detection and response solution, ExtraHop Networks provides full analysis of network interactions in real time, empowering security teams to thoroughly investigate threats. ExtraHop's method includes applying advanced analytics and machine learning to offer improved situational intelligence and automated threat detection.
Opaq Cloud Platform
The Opaq cloud platform offers Security-as-a-Service and hyperscale networking, via a centrally managed cloud service that incorporates next-generation network, application and Software-as-Service firewall, web application firewall and DDoS mitigation. Key elements include software-defined network segmentation and quarantine capabilities.
Sophos XG Firewall
Recent enhancements to the Sophos XG Firewall have included lateral movement protection, which prevents targeted manual cyberattacks from getting inside networks that have been compromised. The capability provides automated isolation of compromised systems—across each point in the network—ultimately helping to enable comprehensive protection.
Zyxel Communications ZyWall ATP Firewalls
With ZyWall Advanced Threat Protection Firewalls, Zyxel Communications brings together signature-based malware detection with capabilities for detection of previously unknown malware. Using cloud-based sandboxing, the offerings can isolate and identify new malware—while also incorporating anti-spam functionality, content filtering and VPN.
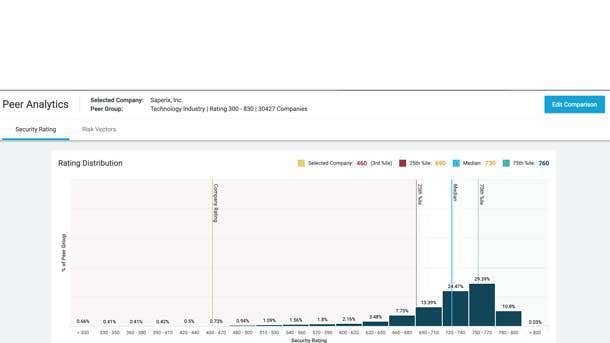
Security—Risk Management
Winner:
BitSight Peer Analytics
Security ratings pioneer BitSight has continued to up its game with its Peer Analytics offering, which provides customers with visibility into how their peers are performing when it comes to cybersecurity programs. This data-driven insight enables continuous monitoring and analysis of security performance—allowing companies to see where they stand on cyber performance within the broader industry in real time. The offering leverages the BitSight Security Ratings platform, which tracks performance data from hundreds of thousands of organizations worldwide. Peer Analytics ultimately empowers customers to set new security performance targets that are achievable, prioritize security initiatives efficiently and better allocate their resources.
Finalists:
Arctic Wolf Managed Risk
With its Managed Risk portfolio, Arctic Wolf quantifies risk-based vulnerabilities by providing continuous scanning of a customer's networks and endpoints. Meanwhile, the company's Concierge Security Team offers an understanding of cyber risks in real time to enable improvements in the customer's security risk posture.
AttackIQ Platform
The AttackIQ Platform brings continuous security validation through ongoing testing of security controls, processes and people. The automated validation platform provides capabilities such as attack emulation and real-time reporting, enabling simplified identification and remediation of security issues.
Defendify
Defendify's platform provides defense, program management, risk scoring, alerts and reports, paired with recommendations and a suite of security tools. The platform ultimately delivers everything from a foundational understanding of an organization's security posture, to establishment of cybersecurity awareness in the organization's culture, to monitoring and protection from cyberthreats.
ID Agent, a Kaseya company: BullPhish ID
ID Agent goes beyond uncovering the theft of sensitive data with its offering for preventing future compromises, BullPhish ID. The offering uses simulated phishing attacks—which leverage real-world social engineering tactics—combined with security awareness training in order to educate employees.
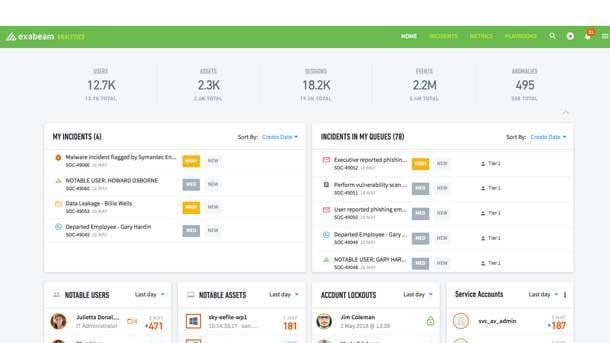
Security—SIEM/Security Analytics
Winner:
Exabeam SaaS Cloud
As the hosted cloud version of the Exabeam Security Management Platform, Exabeam SaaS Cloud provides a comprehensive offering for attack detection, investigation and response as a cloud-based service. Key benefits include reduced deployment time and operational overhead, with capabilities ranging from automatic software upgrades and capacity management to 24/7 health monitoring. Meanwhile, prebuilt integrations allow for easy data ingestion from cloud services, and the platform provides for behavioral analysis from cloud or on-premise data sources, as well. Exabeam SaaS Cloud ultimately frees up security analysts from managing infrastructure to focus on more-sophisticated work such as threat hunting.
Finalists:
Jask ASOC Platform
The JaskASOC platform, a cloud-based SIEM, pulls together data sources such as network traffic metadata to offer enhanced context during incident analysis. The platform automates numerous repetitive tasks,and is powered by Jask technologies that deploy machine learning to mimic the SOC analyst.
Cymatic UEBA Platform
Cymatic's UEBA (user and entity behavior analytics) platform protects web applications by preventing threats from reaching beyond the browser. The platform works by autonomously verifying the security standing of a user in real time, allowing security risks to be identified and threats to be mitigated.
Security —Threat Detection
Winner:
WatchGuard Threat Detection and Response
The latest version of WatchGuard's Threat Detection and Response offering brings significant updates such as accelerated breach detection and threat analysis powered by AI. The offering provides automated identification of unknown processes that are connecting to malicious destinations, allowing advanced threats to be quickly remediated. Meanwhile, new ThreatSync capabilities leverage AI to automatically identify files that possess suspicious characteristics, and then send them to WatchGuard's APT Blocker cloud sandbox for further analysis. The latest updates enable MSPs to dramatically reduce breach detection and containment time frames while automating the remediation of zero-day malware and improving defense against targeted threats.
Finalists:
Cohesity CyberScan
With its CyberScan offering, Cohesity provides the ability to scan offline backup data for security threats. The offering boots the backup snapshot within Cohesity's runtime environment and runs a scan, then connects to a partner platform, Tenable.io, to check against published vulnerabilities.
Darktrace Antigena
Darktrace Antigena brings an AI-powered, autonomous approach to detecting and derailing cyberattacks. Antigena learns the typical patterns of every user, machine, cloud environment and IoT device in an organization—allowing it to pick up on subtly anomalous behavior that other offerings would miss.
Security —Web And Application
Winner:
WhiteHat Security Essentials Product Line
WhiteHat Security's Sentinel Essentials product line includes automated, high-speed static application security testing (Sentinel Source EE) along with automated software composition analysis (Sentinel SCA EE), which identifies open-source and third-party components used in applications to deliver a software bill of materials. The Essentials products enable development, build and test teams with security throughout the software development life cycle—with automated security testing that leverages built-in AI and comprehensive code coverage. Rapid detection and remediation can be easily integrated into the software development life cycle with WhiteHat offerings, ultimately providing customers with a faster, more-secure way to get to market.
Finalists:
Aqua Security Aqua Cloud-Native Security Platform
With its cloud-native security platform, Aqua Security offers a mature platform for securing container-based and cloud-native applications through the entire process from development to production. The platform provides organizations with end-to-end visibility along with protection for their applications against attacks.
Contrast Security Contrast OSS
Leveraging automation capabilities, Contrast Security's Contrast OSS offering stands out by continuously identifying open-source components that are vulnerable; determining how the application is using the components; and preventing the exploitation of the vulnerable components at runtime.
TrueFort
With its application security behavior analytics platform, TrueFort provides visibility into behavior such as traffic and communication flows and detects behavior that represents a threat. The platform secures business applications whether they're running in a data center, cloud or hybrid infrastructure.
ZeroNorth Platform
The ZeroNorth Platform provides orchestration of all application scanning, reporting, remediation and retesting—both during software development and production. Platform capabilities include integrating numerous application security tools, centralizing the management of tools and enabling a focused effort on high-risk threats.
Servers
Winner:
HPE Servers with InfoSight
Hewlett Packard Enterprise has taken its HPE InfoSight cloud-based AI management platform beyond its original storage focus with the expansion of the technology to the company's server business. HPE has extended its InfoSight platform to the company's ProLiant servers, Synergy compute modules and Apollo servers. By bringing HPE InfoSight management capabilities to its servers, HPE provides improved visibility into the health and status of servers and offers predictive analytics to help reduce maintenance issues—while also improving security by monitoring rogue login attempts. InfoSight's powerful AI-based technology ultimately helps to complete the visibility needed to effectively manage the modern data center.

Storage —Enterprise
Winner:
HPE Primera
With the new HPE Primera storage platform, Hewlett Packard Enterprise combines the InfoSight-based predictive analytics technology from its Nimble family of arrays with the reliability of its 3Par array family. The all-flash HPE Primera leverages InfoSight to take away much of the complexity that continues to challenge enterprise IT infrastructures. Primera brings InfoSight to on-premises environments, even to data centers that are not connected to the cloud. The platform was also designed with simplicity in mind and can be installed in less than 20 minutes with storage provisioned within seconds. HPE Primera ultimately combines agility and resiliency for mission-critical applications with a system that can manage itself.
Finalists:
DataCore Software-Defined Storage PSP9
The PSP9 update to DataCore's software-defined storage offering features DataCore Insight Services, a cloud-based predictive analytics engine that delivers actionable insight across multiple vendors and data centers, including primary, secondary and hyper-converged storage. It provides problem detection, best-practice recommendations and capacity planning.
NetApp AFF C190
With the AFF C190, NetApp combines the performance of all-flash storage with its full range of enterprise-class data services, cloud connectivity and integrated data protection. Notably, the all-flash array comes in a limited number of entry-level configurations that are comparatively low in cost.
Qumulo P-184T All-NVMe File Storage
Qumulo's P-184T All-NVMe File Storage provides high performance—scaling to 225 GBps throughput in a single cluster—along with 184 TB of raw NVMe storage capacity in 2U of rack space. Key capabilities include predictive caching that rapidly accelerates the movement of data.
Wasabi Hot Cloud Storage
Recent enhancements to Wasabi Hot Cloud Storage have included the addition of the Wasabi Partner API—which allows Wasabi to stand out from other public cloud object storage providers by enabling MSPs and other solution providers with fully automated on-boarding and management of new customers.

Storage—Midrange
Winner:
Dell EMC Unity XT
In a major update to its midrange Unity storage line, Dell EMC unveiled its Unity XT platform with an eye toward enhanced performance and efficiency—as well as helping customers to move more quickly to multi-cloud infrastructures. Unity XT features a combination of software enhancements and the latest generation of Intel processors to double the performance of the previous generation. Unity XT is also NVMe-ready, meaning that customers will be able to receive a non-disruptive software upgrade in order to take advantage of the high-performance NVMe protocol. In terms of data reduction, Unity XT features a 5-to-1 data reduction capability.

Storage —SMB-Class
Winner:
Dell EMC PowerVault ME4
With its PowerVault ME4 block storage array, Dell EMC provides an entry-level, purpose-built array that's optimized for SAN and DAS environments that are price-sensitive. The offering delivers major features from high-end storage offerings to small-medium businesses, such as an all-inclusive software model providing all necessary data storage, management and protection features. Key software capabilities include distributed RAID, auto-tiering and SSD read cache. PowerVault ME4 ultimately delivers four times more IOPS, a 122 percent increase in raw capacity, significantly improved back-end connectivity and 75 percent more drive support compared with preceding models.
Editor's Choice
Winner: IGEL OS 11 Workspace Edition
IGEL OS 11, the latest update to the company's software-defined endpoint management operating system, can be deployed on any x86-based hardware device into a device for connecting to centralized workloads—either on-premises or in the cloud. The IGEL OS 11 Workspace Edition combines all the capabilities needed to create a managed IGEL endpoint, including a multimedia codec pack for good-quality audio, video and graphics; high availability for the UMS server; and a RESTful API management interface to easily exchange reporting information with other applications.
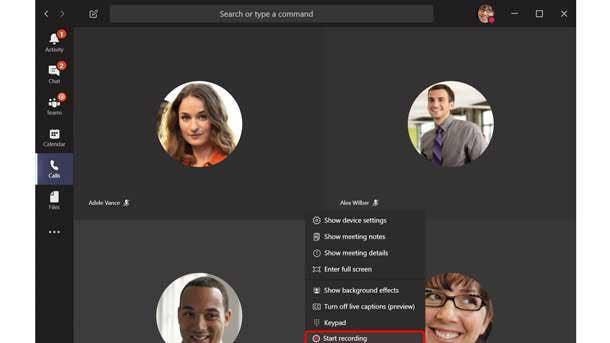
Winner: Microsoft Teams
Recent updates to the Microsoft Teams collaboration platform included the addition of major new AI capabilities to enhance meetings and better enable first-line and health-care workers. Teams—which combines chat, meetings and calling, file collaboration and workflow management—over the past year added more than a dozen new capabilities aimed at first-line workers as well as features for health-care workers such as secure messaging. Other key updates to Teams have included live captions and meeting recording, along with automatic transcription and translation. Microsoft also debuted a mobile-first feature that enables customization of the Teams experience based on an employee's role.