10 Hot Identity And Access Management Products You Need To Know About
These 10 identity and access management products secure internal and external identities, authenticate users through multi-factor authentication or single sign-on, and safeguard privileged accounts.

Securing Workers Wherever Work Is Happening
The vision for identity and access management had always been remote-work-centric, and the COVID-19 pandemic made this a reality worldwide more quickly and more definitively than any conventional technology or business driver could have. It has long been within the capabilities of identity and access management to facilitate this approach to work, and the market has begun embracing this long term.
The identity and access management market now supports more diversity in user authentication models and flows and can also manage basic access to IoT devices, contextual and comprehensive adaptive access, mobile computing and API target services. More than 90 percent of North American clients are seeking SaaS-delivered models for new purchases in the access management space, Gartner found.
Identity and access management vendors are providing ever-advancing security controls, from more-advanced identity proofing approaches and other sources of risk to allow more visibility and control during session authorizations. And vendors are turning to artificial intelligence and machine learning to sort through massive amounts of data and provide visibility and control for identity and access management practitioners, Gartner found.
Here’s a look at 10 identity and access management (IAM) products that secure internal and external identities, authenticate users through multifactor authentication or single sign-on, and safeguard and manage privileged accounts and identities.
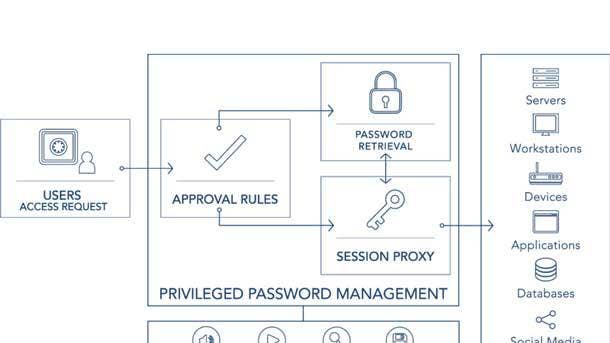
BeyondTrust Privileged Access Management
The BeyondTrust Privileged Access Management portfolio provides visibility and control over all privileged accounts and users to simplify deployments, reduce costs, improve usability and reduce privilege risks. Privileged Remote Access allows customers to secure, manage and audit vendor and internal remote privileged access without a VPN. And Password Safe gives users complete control over privileged accounts by helping them reduce the risk of privileged credential misuse through automated privileged password and session management.

CyberArk Identity Security
CyberArk isolates and stops privilege attacks before they can do harm by safeguarding critical assets and providing users with native access to everything they need. The company empowers workforces and customers with easy, secure access across any device, delivering seamless access through a strong password-less experience and keeping threats out using AI. CyberArk can also help customers secure non-human identities across application and automation tools in the DevOps pipeline without sacrificing business agility.
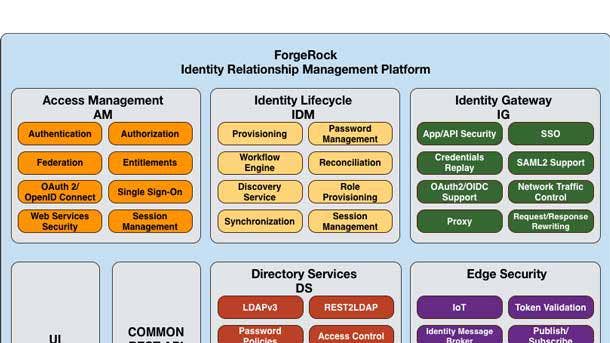
ForgeRock Identity Platform
The ForgeRock Identity Platform includes full-suite identity and access management and identity governance and administration capabilities and can be implemented across an organization for both workforce and consumer identities. It offers feature parity across all delivery options, including on-premises, any cloud environment, multi-cloud, hybrid and as a service. ForgeRock can also manage and reduce the risk that comes with excessive or unnecessary access of users to applications, systems and data.

IBM Identity And Access Management
IBM’s identity tools deliver a friction-less and secure experience for every user, asset and data interaction, providing the foundation for a zero trust strategy. The technology enables customers to grant access rights, provide single sign-on from any device, enhance security with multi-factor authentication, enable user life-cycle management and protect privileged accounts. IBM ensures that the right people have the right access by discreetly verifying user identities when they log in and throughout the session.
Microsoft Azure Active Directory
Microsoft Azure Active Directory is a complete identity and access management offering with integrated security that connects 425 million people to their apps, devices and data each month. It protects access to resources and data using strong authentication and risk-based adaptive access policies without compromising user experience. Azure AD also allows customers to manage all their identities and access to all their apps in a central location, whether they’re in the cloud or on-premises, to improve visibility and control.

Okta Identity Cloud
The Okta Identity Cloud is an independent and neutral platform that securely connects the right people to the right technologies at the right time. Okta offers companies one place to manage all their users, groups and devices and can automate all life cycles and any business process for external and internal users. The company can embed secure login and single sign-on for custom applications and also enhances the security of applications with contextual step-up authentication using a broad set of second factors.
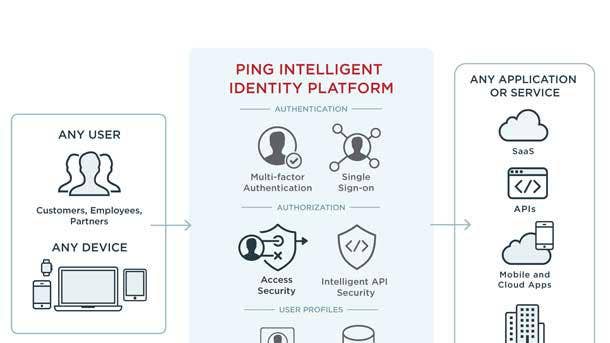
Ping Intelligent Identity Platform
The Ping Intelligent Identity Platform allows users and devices to securely access any service, application or API from any device. The platform can be deployed on-premises, in the cloud or both and provides centralized control to optimize the balance of security and convenience. The platform provides single sign-on and intelligent access to authorized services, and allows customers to orchestrate a wide range of authentication use cases with policy-based controls that leverage diverse contextual attributes and signals.
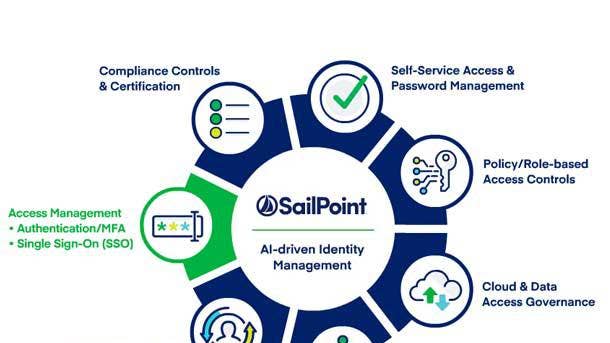
SailPoint Identity Security
SailPoint Identity Security gives businesses unmatched visibility while automating and accelerating the management of all user identities, entitlements, systems, data and cloud services. The technology provides a complete view of all access across an organization, including those hidden or unknown that may pose inherent risk. SailPoint can also replace manual processes with automated workflows to deliver, manage and secure access to every application, system, file share and cloud platform across a customer’s hybrid environment.
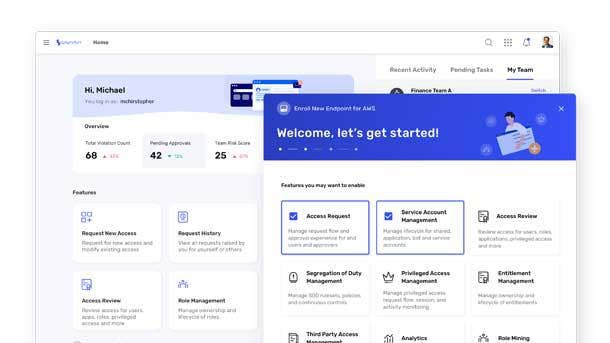
Saviynt Enterprise Identity Cloud
The Saviynt platform centralizes controls and risk management for every human and machine identity across an organization’s hybrid ecosystem, while advanced analytics contextualize risk and automate remediation. The technology automates application provisioning, access reviews, role-based access, and life-cycle and privileged session management to improve security posture and lower costs. Customers can deploy Saviynt’s privileged access management to any application in their IT ecosystem, including cloud and on-premises infrastructure.
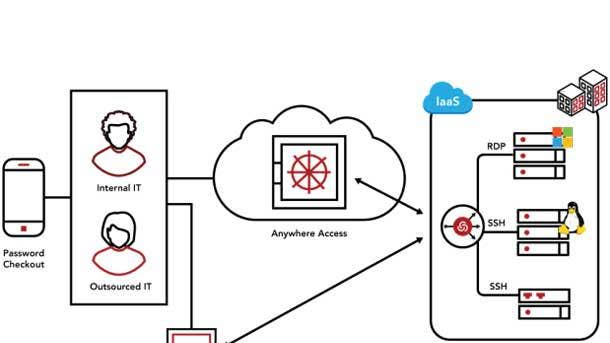
ThycoticCentrify Privileged Access Management
The platform is designed to grant least privilege access just-in-time based on verifying who is requesting access, the context of the request, as well as the risk of the access environment. Secure remote access minimizes cyber-risk exposure for IT admins when accessing IT infrastructure remotely, and privileged users can have granular preventative access enforcement measures implemented. The technology also identifies all service, application, administrator and root accounts to curb sprawl and gain full view of a customer’s privileged access.