10 Hottest Container Security Tools In 2019
Here's a look at how companies like Aqua, Qualys, and Twistlock find vulnerabilities, block threats, maintain compliance, and examine activity to secure containers at their most vulnerable point.

Fortifying Containers
Containers burst onto the scene roughly five years ago, bringing reductions in critical computing parameters such as size, cost, and time when compared to virtual machine-based environments. However, containers were perceived to be less secure than virtual machines since a vulnerability in the host kernel could result in security lapses at the containers that share it.
Specifically, a lack of proactive awareness among IT professionals has resulted in containers being adopted without alignment to enterprise security goals. As a result, there's now an opportunity for vendors to infuse security into the development and operational processes pf containers.
The worldwide container security market is expected to reach $2.25 billion in 2023, according to market research and consulting firm Arcluster. A string of innovative security vendors are now developing platforms with enhanced feature sets that deliver comprehensive security and protection, Arcluster said.
Here's a look at 10 container security tools that have caught the market's eye this year.
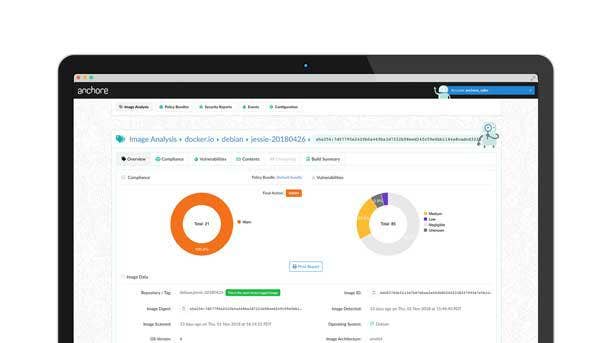
Anchore Enterprise
Anchore Enterprise performs deep analysis on container images, defines policies to certify images, and ensures compliance standards and organizational best practices are met. The on-premise, enterprise-ready tool for container security and compliance is built on the open source Anchore Engine, according to the company.
Anchore’s graphical user interface allows customers to view and browse repositories as well as create and define custom policies to be applied to images. Anchore includes support for role-based-access-controls, as well as a Feed Service that collects vulnerability and package data from upstream sources.
The Anchore Enterprise Feed Service can be run locally or on the Anchore Cloud, providing continually updated vulnerability and package data. Anchore Enterprise plans start at $10,000 per year for up to 50 image repositories and unlimited users.
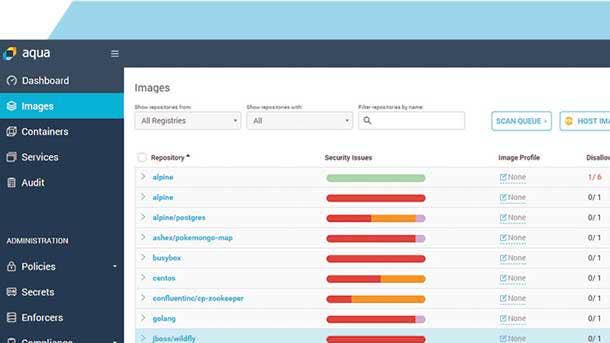
Aqua Cloud Native Security Platform
The Aqua Cloud Native Security Platform provides full lifecycle security for container-based and serverless applications. It secures applications before they are deployed, mitigating risk, enforcing immutability and easily detecting and blocking anomalies based on the application context.
The platform is capable of scanning thousands of images daily, and protecting clusters with thousands of nodes, with minimal performance impact, according to Aqua. It can also manage multiple team deployments or multiple customer tenancies using a central console, ensuring by complete isolation between tenants is achieved by maintaining a separation of data and access.
Aqua runs on-prem or in the cloud, at any scale, and can integrate with the user's choice of infrastructure to deliver comprehensive security and compliance.

Capsule8 Protect
Capsule8 Protect delivers high-performance attack protection for Linux production environments, regardless of if they're containerized, virtualized, or bare metal. It uses distributed, streaming analytics combined with high-fidelity data that detects and responds to attacks the instant they’re attempted, according to the company.
The platform's approach includes highly-technical methods for detecting indicators of common exploitation techniques, while still providing flexible policy-based detection. It also provides relevant, contextual information that makes it easy to perform investigations that determine why alerts fire, and what an attacker does after an attack lands.
Capsule8 Protect can strategically and automatically kill attacker connections, restart workloads, or immediately alert an investigator upon initial detection, according to the company. It provides seamless, easy-to-deploy detection across the entire infrastructure, with support for containers, virtual machines, bare metal, and hybrid deployments.

Deepfence Security as a Microservice
Deepfence Security as a Microservice gets deployed as a lightweight sidecar container on every host, and can be scaled and orchestrated in exactly the same manner as other containers. It is zero-touch, and doesn't depend on third-party kernel modules, manual behavior modeling, or user-defined rules and policies, according to Deepfence.
The product discovers all running containers, processes and online hosts, and presents a live and interactive color-coded view of the topology. It also audits containers and hosts to detect file system, process and network related misconfigurations, according to Deepfence.
Deepfence monitors and performs deep inspection of network traffic, system and application behavior, correlating suspicious events across the entire infrastructure to detect threats with minimal false positives. The tool can also quarantine tainted workloads, Deepfence said, stopping potential lateral spread of the infection.

NeuVector Kubernetes Container Security Platform
NeuVector provides a highly automated Kubernetes and OpenShift container security product that adapts easily to changing environments and secures containers at their most vulnerable point – during run-time. The declarative security policy ensures that applications can scale up or scale down quickly without manual intervention.
The product discovers normal connections and application behavior and automatically builds a security policy to protect container-based services, NeuVector said. In addition, all running containers and host OS’s are automatically scanned for vulnerabilities with scanning tasks distributed across hosts for real-time, highly scalable image vulnerability analysis.
With Layer 7 network inspection, NeuVector detects and prevents application-level attacks on containers such as DDoS and DNS. It can instantly discover running containers and map application behavior, as well as monitor and protect containers from violations, threats, and vulnerabilities.
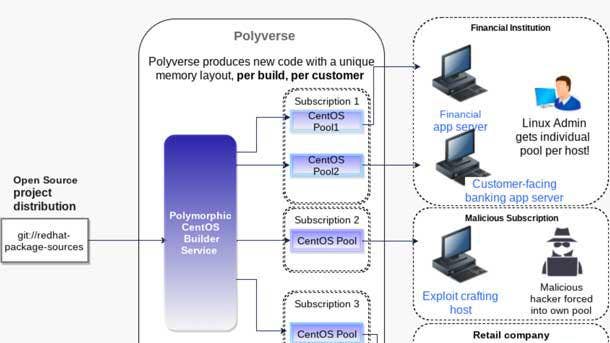
Polyverse Polymorphic Linux
Polyverse takes source code and runs it through a polymorphic compiler, changing register usage, function locations, and import tables to produce individually unique binaries that are semantically equivalent. These binaries are then applied to the totality of the Linux stack.
The product reduces attacker's window of opportunity by increasing their uncertainty, Polyverse said. By harnessing moving-target defense, the company creates strategic entropy in software systems.
Polyverse Polymorphic Linux is immune to memory exploitation attacks, which accounted for 80 percent of the high- or medium-severity incidents in 2017. The product can be deployed in less than five minutes, according to Polyverse.
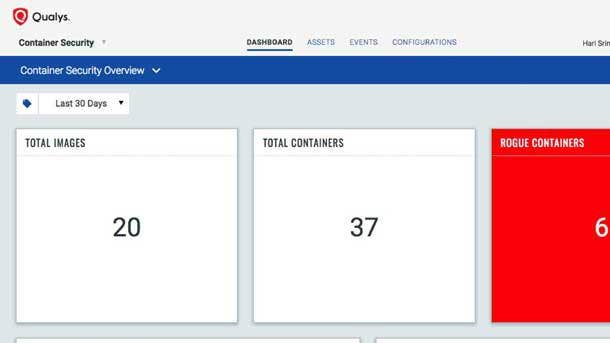
Qualys Container Security
Qualys Container Security provides complete visibility of container hosts whether they are on premises or in the cloud. It gathers comprehensive topographic information about an organization's container projects, including images, image registries, and containers spun from the images.
The product makes it possible for security teams to enforce policies that block the use of images that have specific vulnerabilities, or that have vulnerabilities above a certain severity threshold, according to Qualys. It can also search for images in a company's environment that have high-severity vulnerabilities, unapproved packages, or older or test release tags.
Qualys Container Security lets the user scan, protect and secure the running containers. It also features policy-based orchestration to stop vulnerable images from containers from being spun up in Kubernetes clusters.

StackRox Kubernetes Security Platform
The StackRox Kubernetes Security Platform identifies and visualizes all of an organization's container assets, giving a complete picture of their environment. It maps containers from services to applications, providing context around a company's assets as well.
The product pulls together the widest set of data to build a list of a company's riskiest assets, enabling a business to immediately zero in on the most critical assets to update to improve their security posture. The software stitches together categories of events, with continuous machine learning improving the efficacy of detection so that companies can focus on the incidents that matter.
After distilling and correlating events to identify and alert on attacks, StackRox lets the user determine the response. The platform can take action automatically - such as killing the container(s) involved or removing them from the environment if they violate policies - or alert the business to intervene.
Sysdig Secure
Sysdig Secure brings together image scanning and run-time protection to identify vulnerabilities, block threats, enforce compliance, and audit activity across microservices. It secures the entire software development lifecycle by identifying, remediating, and mitigating vulnerabilities from deployment to production.
The product collects data through system calls, giving businesses more signals about container, host and orchestrator activity in their environment, according to Sysdig. The forensic capabilities make it possible to easily recreate intrusions, data exfiltration events, or lateral movement so that an organization can recover quickly and improve its defensive posture.
Sysdig Secure captures audit trails of every user action taken on their hosts or inside their containers with full command-line arguments, enriched with container and orchestrator context. It also detects violations of external compliance requirements like PCI-DSS and GDPR, and can also enforce custom compliance controls.

Twistlock 19.03
Twistlock 19.03 provides full-stack, full-lifecycle container and cloud native cybersecurity for teams using Docker, Kubernetes, serverless, and other cloud native technologies. It provides vulnerability and compliance scanning and enforcement for a company's container images, hosts, and serverless functions.
As soon as an application is shipped, the product automatically learns the behavior of a company's images, microservices, and network to whitelist known good behavior while preventing anything anomalous. It also protects running applications with firewalls reimagined for cloud native environments, as well as autonomous runtime defense and access control.
Twistlock 19.03 provides vulnerability detection, understanding, and prevention at every stage of the application lifecycle. It integrates directly into the continuous development process to find and fix problems before they ever make it into production.