10 Hottest DevSecOps Tools You Need To Know About
Here's a look at how companies like Aqua Security, Red Hat and Veracode have centralized control, enhanced automation, and infused security into the application development process.

Security Gets A Seat At the Development Table
Growth in the DevSecOps market is being driven primarily by the increased need for highly secure continuous application delivery as well as an increased focus on security and compliance. DevSecOps enables security teams to efficiently align with DevOps team to deliver required security changes, resulting in the continuous monitoring of attacks and defects.
Cloud deployment of DevSecOps offerings helps organizations with deploying code during the production process, providing enhanced security, performance and scalability. Adoption of DevSecOps offerings is highest among large enterprises due to faster development and release cycles, as well as the need for early integration of security tools into the DevOps process.
The DevSecOps market is expected to expand at a compound annual growth rate of 31.2 percent from $1.5 billion in 2018 to $5.9 billion in 2023, MarketsAndMarkets projected. Much of the adoption will take place in the retail sector since it cherishes improved operational efficiency and productivity, reliable and secure IT environments, faster time-to-market, and enhanced customer experiences.
Here's a look at 10 DevSecOps tools that have piqued the market's interest in 2019.
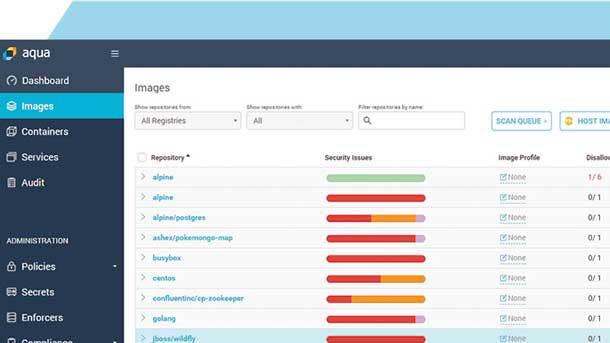
Aqua Container Security Platform
Aqua enables organizations to automate secure development and deployment of applications in their DevOps pipelines by embedding comprehensive security testing and powerful policy-driven controls early on. The tool comprehensively scans container images and serverless functions for known vulnerabilities, embedded secrets, OSS licensing issues, malware and configuration issues.
The product prevents unapproved images and functions from being deployed in an organization's environment, pre-empting operational errors, image sprawl and rogue deployments. Aqua provides real-time actionable information on vulnerability and configuration remediation, fed back to developers within their continuous integration or continuous delivery (CI/CD) tools.
Aqua leverages a company's existing secrets vaults to securely deliver, update and rotate secrets in containers with no container restart, and no exposure outside the container, both in transit and at rest. The tool natively integrates with Jenkins, Azure DevOps, Bamboo, GitLab, TeamCity and more to scan images as they are built, providing actionable feedback to developers.

Continuum Security IriusRisk
IriusRisk is a single integrated console to easily create threat models and manage application security risk throughout the software development process. It provides a self-service approach to managing software security requirements without slowing down a firm's development team, while at the same time enforcing the standardized countermeasures and security policies agreed upon by the security team.
The product creates a threat model and derives security requirements in minutes using a straightforward questionnaire-based system. IriusRisk measures, views and responds to application security risk through all of the software development and delivery steps.
IriusRisk reduces the number of security vulnerabilities in applications caused by weak security design and inadequate controls. The product manages security risk throughout the software development life cycle by choosing a risk response and synchronizing security requirements with issue trackers.
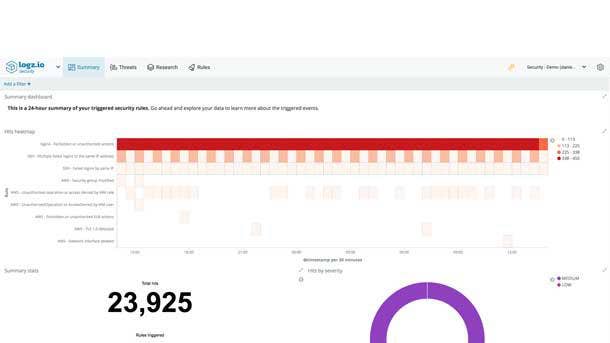
Logz.io Security Analytics
Logz.io Security Analytics provides a unified platform for security and operations that combines enterprise-grade log analytics with artificial intelligence to help organizations identify and remediate threats faster. The tool is easy to deploy and cloud-native and makes it possible for businesses to easily integrate security into their cloud and DevOps environments.
The product uses popular open-source log analysis platform ELK Stack for security analysis so that businesses don't have to worry about installation, maintenance and scalability. Logz.io Security Analytics provides built-in integrations for any data source and allows companies to use premade monitoring dashboards for a variety of security use cases to start identifying threats immediately.
Logz.io Security Analytics uncovers malicious activity with an extensive rule set complemented by machine learning and anomaly detection. And in the future, the product will leverage machine learning to uncover security threats handled by other experts around the globe.
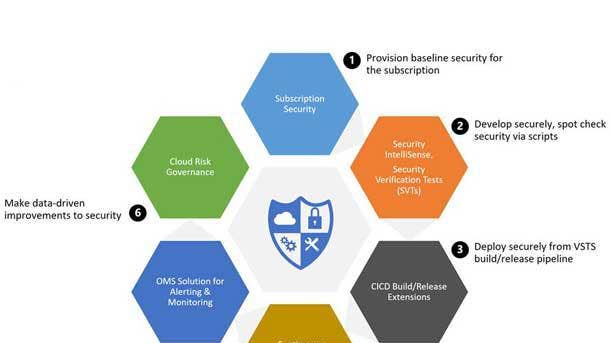
Microsoft Secure DevOps Kit For Azure
The Secure DevOps Kit for Azure is a collection of scripts, tools and extensions that caters to DevOps teams using extensive automation and smoothly integrating security into native DevOps workflows. A secure cloud subscription provides a foundation upon which subsequent development and deployment activities can be conducted, and the kit enables developers to configure security in the subscription.
The kit introduces the concept of security verification tests, which can check for security of various resource types in Azure. These tests can be used to ensure that the target subscription used to deploy a cloud application and the Azure resources the application is built upon are all set up in a secure manner.
The kit spans across all stages of DevOps, generating a single, integrated view. Underlying all activities in the kit is a telemetry framework that generates events capturing usage, adoption and evaluation results to allow for measured security improvements targeting areas of high risk and maximum usage.

NowSecure Auto
NowSecure Auto makes it easy to integrate security testing into a firm's mobile software development life cycle by automating static, dynamic and interactive analysis of Android and iOS apps. Auto is used by security, quality assurance and development teams to rapidly certify mobile application security during build cycles, prior to initial release and based upon the attributes most important to each organization.
The product's advanced testing engine is powered by an aggressive attacker point of view, and drives static, dynamic and behavioral testing of iOS and Android mobile apps. This makes it possible for NowSecure to deliver fast and accurate analysis of mobile application security, compliance and privacy risks.
NowSecure Auto collapses mobile application security testing time from days and hours to minutes, delivering high-quality, deep analysis with near-zero false positives. The product also enables fast resolution by pinpointing issues and providing detailed remediation instructions.
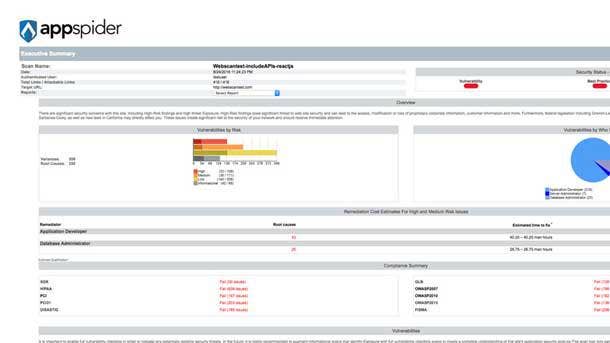
Rapid7 AppSpider
AppSpider automatically finds vulnerabilities across a wide range of applications and includes unique capabilities and integrations that enable teams to automate more of the security testing program across the entire software development life cycle, from creation through production. The tool has a universal translator that can interpret the new technologies being used in today’s web and mobile applications.
The product includes interactive actionable reports that prioritize the highest risk and streamline remediation efforts by enabling users to quickly get to and analyze the data that matters most. With a single click, organizations can drill deep into a vulnerability to get more information and replay attacks in real time.
AppSpider enables centralized control, automation and interoperability over all aspects of a firm's web application security program, including continuous scanning configuration, user permissions, scheduling and monitoring. The product's defensive capabilities help security professionals patch web application vulnerabilities in a matter of minutes rather than days or weeks.

Red Hat Ansible
Ansible’s easily understood Playbook syntax allows users to define and secure any part of their system, from setting firewall rules to locking down users and groups or applying custom security policies. The product comes with a library of more than 750 included automation modules, allowing users to quickly perform tasks without complicated scripting.
The product's command support allows organizations to get things like applying a vendor security patch done across their infrastructure with one simple command. Ansible works with a company's existing SSH and WinRM infrastructure and doesn't require separate security policies for automation.
Once organizations have defined their security configuration, they need to be able to verify it on a consistent basis. Ansible’s idempotent nature means businesses can repeatedly apply the same configuration, and it will only make the necessary changes to put the system back into compliance.

Synopsys Coverity
Coverity gives businesses the speed, ease of use, accuracy, industry-standard compliance and scalability needed to develop high-quality, secure applications. The tool identifies critical software quality defects and security vulnerabilities early in the development process to reduce the time and expense associated with a fix.
Precise actionable remediation advice and context-specific eLearning from Coverity helps developers understand how to fix prioritized issues quickly without having to become security experts. Coverity seamlessly integrates automated security testing into a company's continuous integration and delivery pipelines and supports existing development tools and workflows.
The product can be deployed either on-premises or in the cloud with the Polaris Software Integrity Platform, a highly scalable, cloud-based application security platform. All told, Coverity supports 20 languages and more than 70 frameworks and templates.

Veracode Greenlight
Veracode Greenlight finds security defects in an organization's code and provides contextual remediation advice to help companies fix issues in seconds, right in their integrated development environment (IDE). The product makes it possible for businesses to find issues early, reduce development costs, and release their code on time.
The tool provides immediate feedback as soon as a flaw is introduced and contextual remediation advice to help companies quickly fix the issue. Veracode Greenlight scans passively in the background without taking up resources on a user's machine.
Greenlight has scanned code through the Veracode Static Analysis engine, which has improved its accuracy with every one of the 2 trillion lines of codes scanned thus far. Greenlight and Veracode Static Analysis are based on the same time-tested engine, giving companies more consistent and accurate results and enabling applications to pass compliance much faster.

WhiteHat Scout
WhiteHat Scout is a fully automated static application security testing product that enables developers to scan their code for security vulnerabilities as a part of their iterative, fast-paced, Agile Software Development Life Cycle processes. The product brings early visibility into the security flaws to the individual developers as code is being written, leading to a continuous feedback loop.
The product quickly obtains accurate scan results in minutes to assess common, but easily overlooked, security flaws.
WhiteHat Scout is a fully automated tool that brings together machine intelligence, 16 years of data on verified application vulnerabilities, and more than 100 million attack vectors. Businesses can incorporate security advice earlier in the software development life cycle process by allowing clear guidance on vulnerabilities while remaining in binary.