10 Hottest Threat Intelligence Platforms In 2019

Tracking Threats
Targeted cyberattacks and advanced persistent threats (APTs) are on the rise, but organizations are still struggling to derive quality information from huge volumes of threat data. As a result, SMBs have begun deployed threat intelligence platforms to secure their organizations from emerging threats and vulnerabilities.
SMBs tend to be more susceptible to advanced cyberattacks such as ransomware, botnets, zero-day attacks, and APTs due to financial constraints. Asia-Pacific is expected to drive much of the growth in the market with both SMBs and large enterprises becoming increasingly concerned about cybercrime and adopting threat intelligence products and services to combat them.
The threat intelligence market is expected to grow from $5.3 billion in 2018 to $12.9 billion in 2023 at a compound annual growth rate of 19.7 percent, according to ResearchAndMarkets.com. Although Asia-Pacific is growing the most quickly, North America continues to have the largest market share.
Here's a look at 10 threat intelligence platforms that are taking the market by storm this year.
Anomali Threat Platform
The Anomali Threat Platform provides organizations with a unified way to identify cyberthreats, understand the adversary, and automate response. The offering arms security teams with the cyber threat intelligence necessary to identify and prioritize critical threats to their organization.
For starters, the Anomali Threat Platform collects intelligence from premium feeds, and allows users to evaluate and purchase intelligence feeds via the Anomali APP Store. From there, users can reduce false positives by applying machine learning-optimized threat intelligence, as well as normalize and enrich disparate sources with additional threat context.
The offering can be deployed in the Anomali Cloud, hosted in a user's environment, or hosted with an airgap from Anomali and public data. All told, the Anomali Threat Platform is intended to give a company's analysts an advantage when making decisions and improve their situational awareness.
BlueVoyant Threat Intelligence Services
The BlueVoyant Threat Intelligence Services monitors an organization's external attack surface, assesses emerging risks, and deliver near real-time, actionable intelligence that is specific to a particular business. The offering can reduce the risk of attack from malicious IP addresses and domain names with advanced warning of cyberattacks in formation.
BlueVoyant can additionally enrich an organization's alerts with external threat intelligence to prioritize investigations and identify attacker infrastructure. Finally, the platform can assess third party risk based on external monitoring of attacks and vulnerabilities.
Users have access to deep threat expertise when they need it with their own dedicated threat operations center analyst. Customers also benefit from real-time processing of the largest commercially-available internet traffic dataset, coupled with dark web and host-based threat data.

Cisco Talos
Cisco Talos defends customers against known and emerging threats, discovers new vulnerabilities in common software, and intercepts threats in the wild before they can harm the internet at large. Their combined expertise is backed by a sophisticated infrastructure and Cisco's unrivaled telemetry of data that spans across networks, endpoints, cloud environments, virtual systems, and web and email traffic.
The team is focused on correlating and tracking threats so that Talos can turn attribution information into actionable threat intelligence. By identifying threats and threat actors rapidly, Cisco Talos helps protect customers quickly and effectively.
Talos' threat intelligence supports a wide range of security tools including intrusion prevention, firewall, malware protection, email security, web security, Umbrella and ThreatGrid, as well as numerous open-source and commercial threat protection systems. Talos also makes a variety of free software, services, resources and data available to the public, including official rule sets and communities.
CrowdStrike Falcon X
CrowdStrike Falcon X automates the threat analysis process and delivers actionable intelligence and custom indicators of compromise specifically tailored for the threats encountered on each user's endpoints. With this level of automation, organizations can stop picking and choosing which threats to analyze and start analyzing all threats.
Falcon X combines the tools used by world-class cyber threat investigators into a seamless offering and performs the investigations automatically. The integrated tool set includes malware analysis and malware search, and is enriched with threat intelligence.
Falcon X automatically investigate all incidents to learn from the attacks in an organization's environment, with threats analyzed in minutes rather than hours. Organizations can also better orchestrate their defenses with custom indicators of compromise generated by threats on their endpoints, allowing companies to proactively defend against future attacks.
Digital Shadows Shadow Search
Digital Shadows Shadow Search combines expert security research, assessments, threat intelligence reports, structured technical data and content from the open, deep, and dark web into an innovative, precision search engine returning detailed results in context. It delivers threat insight with context hard to find anywhere else, recouping valuable time for security operations teams and threat analysts.
Digital Shadows has amassed historical, evolving and real-time threat intelligence assets, and enabled access to complimentary expert security sources. Shadow Search provides subscribers with the ability to better manage their third-party risk, investigate security incidents, monitor trends and enrich threat hunting of client-specific indicators and threat actors jeopardizing their business, brand and reputation.
Shadow Search enables analysts to quickly identify the most relevant intelligence for their investigations and use it to make faster and better decisions. The tool saves analysts time by putting actionable information instantly at their fingertips when they need it.
FireEye Threat Intelligence
FireEye Threat Intelligence subscriptions deliver comprehensive, actionable intelligence to help users proactively defend against new and emerging cyber threats and align their security program with corporate risk management goals. FireEye tailors intelligence to the firm's security mission and staff, giving both mature and growing security teams critical context on attacker intent and activity.
More than 150 FireEye security researchers and experts around the globe apply decades of experience toward gathering forward-looking, high-fidelity, adversary-focused intelligence. With an unmatched view into adversaries, victims and networks worldwide, the offering delivers visibility across the extended cyberattack lifecycle to all levels of a user's business.
FireEye Threat Intelligence goes beyond the basic information that data feeds provide and adds the forward-looking and highly contextual information businesses need to build proactive defenses, prioritize alerts and resources and improve incident response. The platform includes various consumable intelligence streams as well as direct access to analysts and dedicated client support.
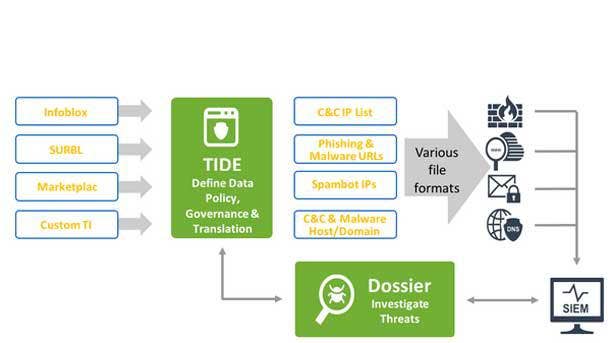
Infoblox Threat Intelligence Data Exchange
Infoblox Threat Intelligence Data Exchange enables the collection, aggregation, and management of threat data from internal sources and multiple external sources including Department of Homeland Security’s Automated Indicator Sharing feeds.
In addition, the exchange empowers users to speed remediation and prevent future attacks by automatically sharing curated threat data, including millions of threat indicies, throughout their existing security infrastructure. It enables security operations to remediate threats more rapidly by sharing normalized data in real-time with third-party firewall and SIEM providers.
Infoblox begins its threat feeds with information gained from native investigations and harvesting techniques, and then combines that with verified and observed data from trusted partners including government agencies, academic institutions, Internet infrastructure providers, and law enforcement. The end result is a highly refined threat intelligence feed with a very low historical false-positive rate.
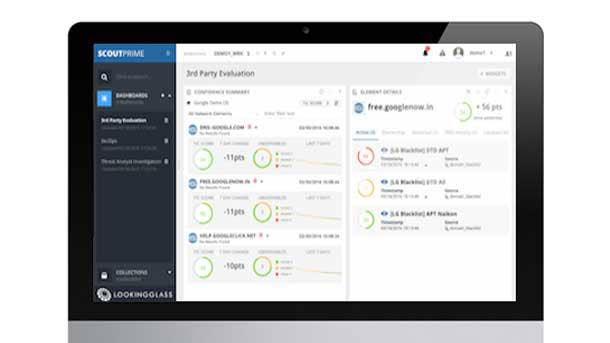
LookingGlass Scout Prime
LookingGlass Scout Prime centralizes the collection and normalization of structured and unstructured data, including 87 out-of-the-box feeds, as well as other commercial data feeds a user may have purchased. It identifies the highest priority threats to a business with Threat Indicator Confidence scoring, which is then fine-tuned based on a firm's risk tolerance profile.
ScoutPrime allows for the exporting of threat intelligence in a variety of formats, via an API that allows for tailored data sets, or a third-party system integration via custom scripts to orchestrate active defense through security appliances.
ScoutPrime delivers insight on threat intelligence that is relevant to a business by categorizing and organizing network elements into a repository called Collections. ScoutPrime’s Collections establish a perimeter around an organization's network and enhances their awareness to any unwelcome malware, viruses, or C2 commands.
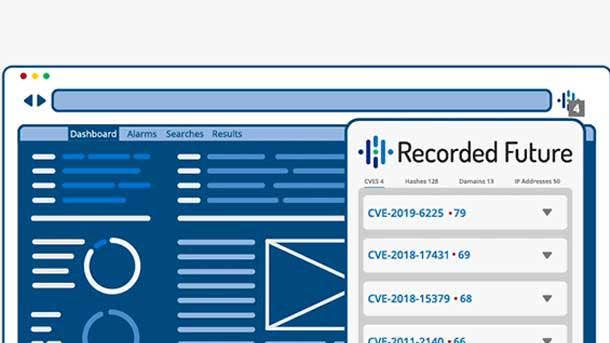
Recorded Future Express
Recorded Future Express layers threat intelligence over existing security workflows through a browser extension, providing real-time intelligence within any web-based application and delivering up-to-the-minute risk scores as well as transparent evidence behind scoring.
Security professionals can use Recorded Future Express to access threat intelligence within SIEM offerings, vulnerability scanners, incident response systems, and other intelligence sources for meaningful context faster. With one click, the browser extension surfaces real-time risk scores and the evidence behind those scores, arming security teams with the intelligence needed to determine action.
By layering threat intelligence over existing SIEM deployments, security professions can assess the alerts that pose the greatest risk and make decisions immediately. Recorded Future Express also instantly identifies and organizes relevant information around hashes, IPs, domains and vulnerabilities when viewing security content to exponentially increase security information consumption.
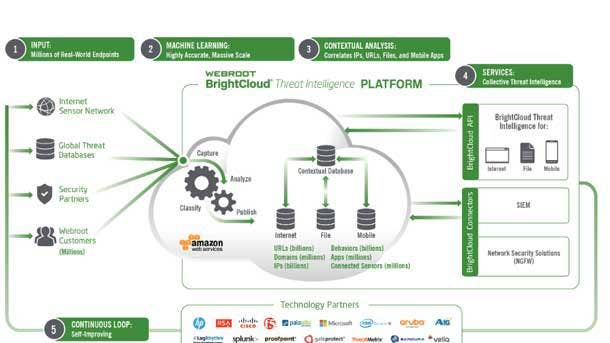
Webroot BrightCloud Threat Intelligence Services
Webroot BrightCloud Threat Intelligence Services protects customers from malicious URLs, IPs, files, and mobile apps by integrating accurate and near real-time threat intelligence into an organization's network and endpoint protection.
The platform scans billions of IP addresses and billions of URLs across millions of domains, in addition to millions of mobile apps, and leverages machine learning to classify and categorize each according to the threat it represents to a company's business.
The platform feeds data into the cloud from millions of global sensors and real-world endpoints, where it is analyzed and correlated with other data points to provide a big-picture view of the threat landscape. Mapping the relationships between different data points enables Webroot to predict how likely an object is to be malicious in the future by its associations with other URLs, IPs, files, and mobile apps.