12 Hot Cybersecurity Startups You Need To Know About At RSA 2020
CRN asks a number of security CEOs, channel chiefs and technical leaders attending RSA 2020 which cybersecurity startups they believe are best defending emerging technologies or simplifying long-standing protection issues.

Securing The Future
A number of security CEOs, channel chiefs and technical leaders attending RSA 2020 spoke with CRN about which cybersecurity startups they believe are disrupting the industry by developing the first protection tools around emerging technologies or addressing long-standing defense challenges in a less- resource-intensive or more effective manner.
Innovations around application security have caught the industry’s attention, with emerging vendors looking to take on challenges around application telemetry, segmentation and orchestration to support cloud adoption without requiring the use of agents. Workload-based segmentation efforts also were praised for their alignment with efforts to migrate data to the cloud.
The other area where startups received a lot of acclaim was data security, where startups are looking to quickly classify large amounts of cloud-based data, establish access control measures in the cloud and streamline compliance with new data privacy regulations.
From attack simulation to vulnerability management, here's a look at the cybersecurity startups that industry leaders attending RSA 2020 expect to make waves in the months and years ahead.
See the newest entry: The 10 Coolest Cybersecurity Startups At RSA Conference 2022

ReliaQuest
ReliaQuest provides analytics and health checks and excels at teaming with other technology vendors to deliver real-time visibility into organizations, according to Kurt Mills, Mimecast’s vice president of channel sales. The company has done impressive things around sorting through the noise of tens of millions of logs to identify several dozen true vulnerabilities or problems, Mils said.
ReliaQuest has addressed the industrywide talent shortage in an innovative way, bringing in dozens of students from Tampa, Fla.-area universities and putting them in a simulator for a few months to rapidly develop them into Tier 1 or Tier 2 SOC (security operations center) analysts, according to Dave Castignola, BlackBerry Cylance’s chief operating officer.
The company has built a platform that allows other vendors to interoperate and exchange data with them without requiring a difficult API connection buildout, Mills said.
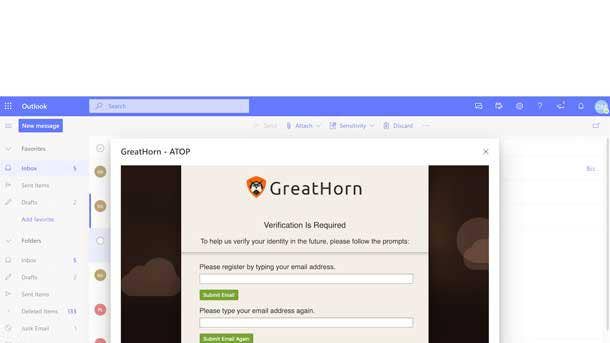
GreatHorn
GreatHorn bolts onto Gmail or the Office 365 mail services and uses threat intelligence and other methods to look for and alert organizations to suspicious emails, according to Allan Liska, a Recorded Future intelligence analyst. GreatHorn is a bolt-on, Liska said, meaning that it doesn’t require the installation of anything in the network and logs information into the customer’s existing console.
Although many other vendors also offer email security, Liska said most of it is appliance-based, meaning that organizations get stuck with yet another box that doesn’t talk to anything else. As businesses move away from setting up their own mail server as the admin, Liska said they’ve struggled to figure out how to easily build security around their cloud-based email services.
Too many enterprise customers assume that Gmail and Office 365 provide sufficient protection for their business on the back end, Liska said. Although Gmail has some good security add-ons that most customers don’t enable, Liska said it still isn’t enough defense for a business.

vArmour
vArmour has brought security into the world of segmentation and can look at application flows without having to put aging technology on desktops, which Gigamon CEO Paul Hooper said is a powerful approach to solve the application telemetry problem. The company is small but growing, Hooper said, thanks to its rejection of a longtime CIO bugbear: agents.
The company’s agentless approach in the space is unique, Hooper said, resulting in lower maintenance and overhead costs for organizations since they don’t have to deal with control and management issues.
vArmour excels at drawing maps of application-to-application communities and figuring out which applications are talking without having to deploy countless agents or countless probes, Hooper said. By identifying when traffic is flowing between applications, Hooper said organizations can understand what in their IT ecosystem is talking to what.

RiskRecon
RiskRecon was built for the purpose of understanding the security posture of a business’ third-party vendors through the automated monitoring of the vendor’s network-facing devices, according to David Walter, vice president of RSA Archer. The tool provides an automated, easy way of capturing third-party risk that is too often overlooked by manual assessments, Walter said.
The company excels at putting technical data into a risk context, Walter said, providing organizations with a risk score and explaining what that number means from a business standpoint. The tool brings its risk findings to users in a format that allows them to easily take action on them, according to Walter.
RiskRecon partnered its risk management with an assessment approach that goes deep to provide broader coverage across a broader time range, Walter said. The data from the assessments can then be used to inform what businesses are looking for from a monitoring standpoint, according to Walter.
Securiti.ai
Securiti.ai has attempted to look at data across an organization and find new ways to profile it and determine who has access to what, according to Ryan Kalember, Proofpoint’s executive vice president of cybersecurity strategy. The company’s ability to take compliance-driven spend and use the dollars to actually better protect data as it shifts into the cloud is a powerful thing, Kalember said.
Securiti.ai has fused cloud-based data into its data classification and natural language processing engine in a straightforward manner, Kalember said. Securiti.ai occupies a market that’s driven by fear of non-compliance with the European Union’s GDPR and California’s CCPA privacy rules, and Kalember expects the company to take items that are just compliance checkboxes and use them to provide better security.
Specifically, Kalember expects Securiti.Ai to take on the challenge of users having more access than is necessary for their role in the organization.

AttackIQ
Attack simulation tools like AttackIQ are effective at verifying an organization’s security posture and providing a quantitative measurement of how the company’s security tools would actually perform in a real-world scenario, according to Michael Martins, Tanium’s vice president of partnerships and alliances.
AttackIQ works closely with the Mitre ATT&CK framework, Martins said, and its interface excels at showing the results that organizations are interested in seeing as well as data on their relevant security posture. The tool helps measure how well a company’s security spend is actually working, Martins said, and pinpoints gaps in protection against compromises, breaches or zero-day exploits.
Through integration with other security vendors, Martins said AttackIQ is able to validate that alerts are being generated after an attack is simulated.

Accurics
Accurics gives businesses the chance to do things differently in cloud security by checking configurations and settings prior to spinning out an asset and offering a level of control that gets things right the first time, according to Unisys Chief Technology Officer Vishal Gupta. Prior to Accurics, Gupta said companies first had to spin out the asset before being able to assess whether the setup was secure and compliant.
The company provides a much-needed control point early in the cloud process, Gupta said, requiring that anyone in an organization looking to spin up an asset into the cloud go through and pass the Accurics check.
In time, Gupta said Accurics can become a cloud database of record, running hundreds of thousands of rules behind the scenes to ensure all the assets are secure.

TrueFort
TrueFort is doing micro-segmentation on applications running in the data center and is delivering application protection in a way that helps customers at scale, according to Matthew Polly, CrowdStrike’s vice president of worldwide alliances, channels and business development. The company has a unique and effective approach to providing application workload visibility and access controls, Polly said.
As applications get spread across the data center and cloud, Polly said being able to protect them at the server level becomes more difficult. The increased adoption of containers and ephemeral workloads means that wall-to-wall server protection would be needed, according to Polly. TrueFort stands apart from others in the space by providing protection at an application layer rather than the server layer.
TrueFort’s application protection also addresses additional use cases beyond security like performance modeling, according to Polly.

ZeroNorth
ZeroNorth has a good leadership team and is one of very few vendors looking to solve problems in the application security space around orchestration, according to Dino DiMarino, Mimecast’s chief revenue officer. Most application security vendors are laser-focused on their own platform, but DiMarino said the industry is suffering from a lack of visibility and orchestration across those multiple vendors.
The industry lacks enough humans to do different work at all of the layers of the application security process, DiMarino said, meaning that vulnerability management just becomes a giant game of Whac-a-Mole if iorganizations aren’t able to look more holistically at application-related issues across the organization.
The nuance of the application development life cycle requires an orchestration tool that’s purpose-built for application security rather than using a more general orchestration tool, according to DiMarino.

ShieldX Networks
ShieldX Networks’ approach to clientless microsegmentation across different cloud platforms puts security around wherever the workload is going, according to Matt Gyde, global security CEO of NTT Ltd. The product is all about workloads and activities, Gyde said, with ShieldX’s engine pulling in microservices whenever they’re needed.
ShieldX benefits from having a fantastic platform sitting behind the client, and the company is moving from an engineering to a sales orientation as it continues to grow and receive more outside funding, according to Gyde. Deployment is simple with ShieldX, Gyde said, since it doesn’t rely on the use of any agents.
As clients move workloads to a shared platform like the cloud to take advantage of cost efficiencies, Gyde said ShieldX can help companies fortify their cloud security posture so that they’re able to make decisions quickly if they’re under attack.

Kriptos
Kriptos excels at classifying millions of cloud-based documents in an incredibly short period of time, dramatically speeding up the time to adoption for DLP (data loss prevention) technology, according to Dave Rogers, Netksope’s vice president of alliances and global channel sales.
Regardless of whether the data is on-premises or in the cloud, Rogers said businesses must classify the data before understanding what rules and policies need to be put in place. Kriptos benefits from a very close partnership with Google as well as its ability to use artificial intelligence and machine learning to ingest and inspect data, according to Rogers.
Rogers said Kriptos has a strong footprint in Latin America, and is well-situated to address the data classification needs of the financial industry in the region. There hadn’t been much innovation in the data classification space for a while, so Rogers said the recent emergence of players like Kriptos should help drive the adoption of DLP among younger organizations.

PrivacyAI
PrivacyAI can help clients fulfill GDPR and CCPA requirements such as capturing consent on the web from the end users, authorizing and auditing who has access to data, and knowing where in the organization personally identifiable information (PII) is located. Although the core DLP technology already exists, Privacy.ai excels at looking and addressing the problem in a holistic way.
Having different sets of rules around data privacy and sovereignty everywhere from California and the European Union to Singapore and India could be a regulatory nightmare for businesses, and Popp said global companies are willing to spend on a tool that keeps them in compliance.
Companies like Privacy.ai and BigID are helping to bring together identity and data protection since so much of their effort is focused on safeguarding the digital identity of individual users, according to Popp. As the two spaces collide, Popp anticipates that gateway and identity players will be brought together.