13 Hot Endpoint And Network Security Tools At RSA Conference 2020
Here's a look at 13 products released around RSA Conference 2020 that boost security by illuminating network blind spots, blocking connections to known malicious IPs, and derailing attackers with decoy endpoints.

From The Core To The Edge
See the latest entry: 20 Hottest Cybersecurity Products at RSAC 2022
Vendors attending RSA Conference 2020 have made significant advancements around network and endpoint security, adding managed detection and response capabilities to their portfolio, decoy endpoints to derail attackers, and the ability to check documents against known risk and threat profiles.
On the network security side of the equation, cybersecurity companies have made efforts to replace the legacy VPN, automatically define network access policies at scale, illuminate network blind spots, and better detect and response to network-based threats.
As far as firewalls are concerned, suppliers are debuting devices with robust capabilities around internal segmentation, encrypted traffic analysis, detecting cloaked malware, blocking connections to known malicious IPs, and filtering out age inappropriate search results in child-heavy settings.
Here's a look at what 13 RSA Conference 2020 endpoint and network security vendors are doing to block lateral movement by intruders, remediate sophisticated malware attacks, and provide fast and secure access to services hosted in public clouds or enterprise data centers.
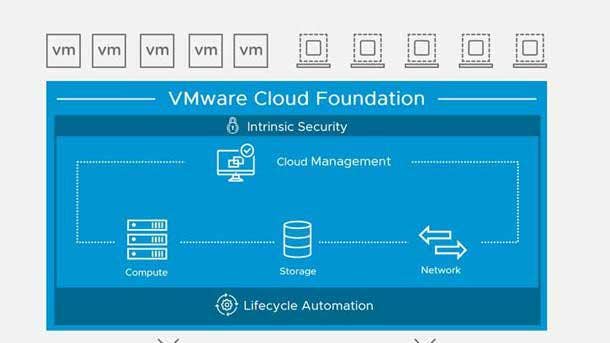
VMware Advance Security For Cloud Foundation
VMware Advance Security For Cloud Foundation will address internal data center security challenges and deliver unified protection across private and public clouds, according to the company. The offering will include VMware Carbon Black Workload Protection, VMware NSX Advanced Load Balancer with Web Application Firewall capabilities and VMware NSX Distributed IDS/IPS, VMware said.
The offering will manage and gather endpoint telemetry through built-in sensors protected by the hypervisor, meaning that attempts to gain root access and tamper with the product will be detected by the hypervisor. Meanwhile, the NSX Web Application Firewall uses a rich understanding of applications, automated learning, and application-specific rules to provide strong security with lower false positives.
In addition, VMware said the distributed architecture of NSX Distributed IDS/IPS will enable advanced filtering to be applied to every part of the application, eliminating the blind spots associated with use of traditional perimeter security products. Policies will be automatically generated and enforced on an application-specific basis, which VMware said will lower false positives.
Digital Guardian Managed Detection & Response
The Digital Guardian Managed Detection & Response (MDR) service secures data, systems and users by combining cloud-delivered endpoint detection and response (EDR) technology with cybersecurity experts. These experts can detect, respond and remediate sophisticated malware attacks that could put systems, users and sensitive data at risk, according to Digital Guardian.
The offering can fill gaps for in-house security operations centers (SOCs) by solving detection challenges that pose a risk to enterprises, Digital Guardian said. The service is managed by seasoned cybersecurity professionals with expertise in threat detection, incident response and proactive threat hunting, according to the company.
Digital Guardian MDR includes deployment of the company’s EDR technology that continuously collects system, user, and data telemetry and blocks behavioral indicators of an attack in real-time. Incident response and threat neutralization support is also provided as part of the service, providing customers with executive-level reports, root-cause analysis, and indicators of compromise tracking sheets.

Fortinet FortiGate 1800F
The FortiGate 1800F next-generation firewall is powered by the company’s seventh-generation network processor and enables large enterprises to achieve true internal segmentation as well as scale, performance, detection and enforcement capabilities, the company said. It offers firms the ability to segment and launch services, manage internal and external risks, and preserve user experience.
Fortinet said the firewall intelligently adapts to segmented users, devices, and applications – regardless of their location, whether on-premise or in multiple clouds – providing automated threat detection and enforcement. It also delivers the required speed, scale, and availability organizations need when on-ramping to the cloud, according to Fortinet.
The FortiGate 1800F offers the industry’s highest SSL inspection performance, Fortinet said, helping to eliminate network blind spots by enabling full visibility of clear-text and encrypted network flows. Plus the firewall’s performance capabilities allow research organizations to perform big data analysis and natural language processing at unprecedented speeds, according to the company.

Attivo Endpoint Detection Net
New capabilities within the Attivo Networks ThreatDefend Detection Platform aim to anticipate the methods an attacker will use to break out from an infected endpoint and ambush them. This unique approach to detection focuses on reducing the time an attacker can remain undetected and the amount of effort required for an organization to restore environments to normal operations, according to Attivo.
Specifically, the Attivo Endpoint Detection Net product closes detection gaps and facilitates automated incident response by making every endpoint a decoy designed to disrupt an attack’s ability to break out and further infiltrate the network. Attivo said it’s able to do this without requiring agents on the endpoint or disrupting regular network operations.
Attivo used historical attack data and the MITRE Att@ck framework to understand the various methods attackers use to spread laterally from an endpoint and then designed the Endpoint Detection Net offering to stop them. The tool elevates security control by accurately raising alerts and taking proactive measures to derail attackers, according to Attivo.

CenturyLink Rapid Threat Defense
CenturyLink Rapid Threat Defense protects network traffic and identifies and stops threats based on customer-set policies. The network-based threat detection and response capability is powered by CenturyLink’s advanced Black Lotus Labs, and offers unique advantages, according to the company.
With Rapid Threat Defense, customers set policies based on threat criteria they specify, allowing for actions such as automatically blocking a malicious IP address at the firewall or blocking a malicious domain through DNS (Domain Naming Services). It also reduces the workload imposed on security incident responders and analysts to detect and respond to daily threats, according to CenturyLink.
Rapid Threat Defense offers a seamless security experience for customers struggling to integrate disparate security systems, CenturyLink said. Plus it helps enterprises automate threat detection and response by deploying defensive actions based on Black Lotus Labs threat intelligence, according to CenturyLink.
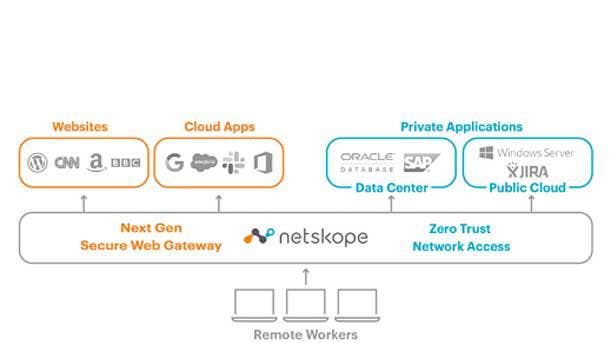
Netskope Private Access
Netskope Private Access provides fast and secure access to private applications, databases, file shares and servers hosted in public clouds and large data centers. As enterprises have increased deployments of private applications in the public cloud, legacy VPNs have failed to keep up and continue to offer access that is blind to applications, overly complex and slows down employees and business partners.
In contrast, Netskope’s zero trust network access approach allows internal applications and resources to be protected from external threats while allowing application-level access control based on user identity and device security posture. Zero trust network access also addresses demand from customers who expect a network that makes their experience with applications to be fast and reliable, Netskope said.
Netskope Private Access delivers zero trust network access through a single client and is managed through the same console that provides data protection, threat protection and incident management for websites and cloud apps, according to the company.
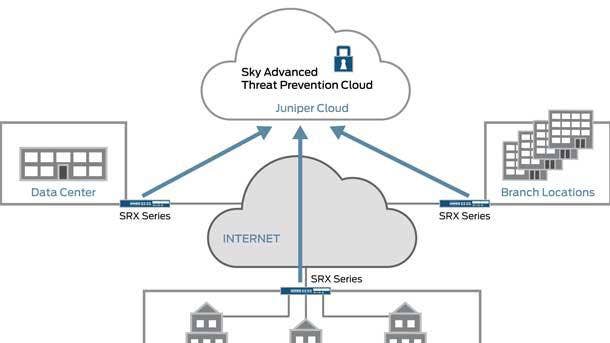
Juniper ATP Cloud And SRX Series Firewalls
The introduction of encrypted traffic analysis for the Juniper Advanced Threat Protection (ATP) Cloud and SRX Series firewalls will help secure traffic in more areas of the network, Juniper said. Encrypted traffic analysis detects malicious botnet traffic that is “going dark” via encryption, giving firms greater visibility and policy control over encrypted traffic without requiring resource-intensive SSL Decryption.
To effectively detect threats such as botnets hiding within encrypted traffic, Juniper said meaningful inspection of traffic patterns is needed. In combination with other technologies, Juniper said encrypted traffic analysis can help provide a layered security approach that helps organizations reduce and manage risk.
In addition, Juniper said Mist customers can now get threat alerts detected by Juniper SRX Series Firewalls and ATP Cloud. This allows administrators to quickly assess security risks when users and devices connect to wireless networks and take appropriate action via the Mist cloud or APIs such as quarantining or enforcing policies, according to Juniper.

Sophos XG Firewall
The new “Xstream” architecture for Sophos XG Firewall offers high performance Transport Layer Security (TLS) traffic decryption capabilities that eliminate significant security risk associated with encrypted network traffic. The new XG Firewall provides critical visibility into an enormous blind spot while eliminating frustrating latency and compatibility issues, according to Sophos.
New FastPath policy controls in the Sophos XG Firewall accelerate the performance of SD-WAN applications and traffic, including Voice over IP, to up to wire speed, Sophos said. In addition, the newly enhanced Deep Packet Inspection (DPI) engine dynamically risk-assesses traffic streams and matches them to the appropriate threat scanning level, according to Sophos.
Meanwhile, SophosLabs intelligence provides network administrators with the AI-enhanced threat analysis needed to understand and adjust defenses to protect against a constantly changing threat landscape. Plus centralized management and reporting capabilities in Sophos Central provide customers with group firewall management and flexible cloud reporting across the entire estate, Sophos said.
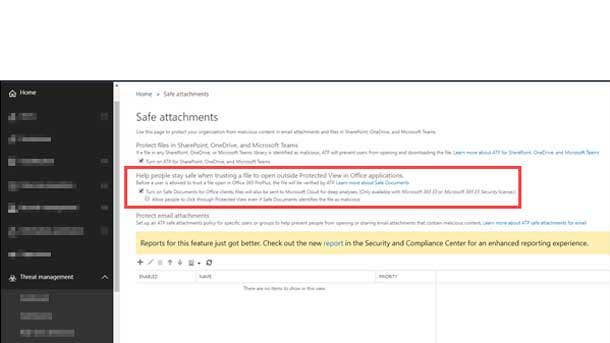
Microsoft Safe Documents
Safe Documents brings the power of Microsoft’s Intelligent Security Graph down to the desktop to verify that documents are safe at the endpoint itself. Although Protected View has helped secure documents originating outside the organization, Microsoft said users would too often exit this sandbox without great consideration, leaving their networks vulnerable.
Safe Documents brings a minimal trust approach to Office 365 ProPlus clients by automatically checking the document against known risks and threat profiles before allowing it to open, Microsoft said. As a result, Microsoft said users can simply focus on their work rather than having to decide on their own whether or not a document can be trusted.
The seamless connection between the desktop and the cloud facilitated by Safe Documents both simplifies the user workflow and helps to keep the network more secure, according to Microsoft.

Zero Networks Access Orchestrator
Zero Networks Access Orchestrator is the first network security platform to automatically define, enforce and adapt user- and machine-level network access policies at scale to create a continuous airtight zero trust network model. With the click of a button, Zero Networks said it can constrain access in the network to only what users and machines should be doing.
The Zero Networks Access Orchestrator observes how users and machines normally communicate to automatically enforce a zero trust networking stance throughout their environment with a two-factor authentication mechanism to allow new or rare access, the company said. Plus least privilege access is established for every user and machine so they can access only what they need and nothing more.
This helps eliminate many internal attack vectors such as network discovery, lateral movement, remote code execution and the introduction of commodity malware, according to Zero Networks. In addition, the company provides a single source for all network access policies, meaning the entire environment is protected from managed and unmanaged devices at scale with the click of a button.
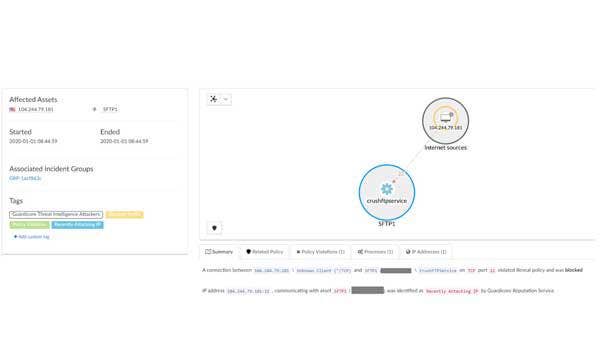
Guardicore Threat Intelligence Firewall
The Guardicore Threat Intelligence Firewall goes beyond traditional firewall measures to help harden security profiles in complex cloud environments, identifying and blocking incoming and outgoing connections to known malicious IPs. This serves to both limit the network attack surface and eliminate attacker activity before it reaches critical assets in the data center, according to Guardicore.
The firewall leverages data consumed from Guardicore’s Cyber Threat Intelligence Feed – a publicly available resource tracking potential threats specific to data center and cloud infrastructure – to eliminate false positives. Instant notifications from the firewall provide accurate and real-time information that a customer environment has been compromised, allowing for a faster response.
In addition, a list of malicious IPs in the Guardicore Threat Intelligence Firewall is updated daily with the latest attack, scan, and command-and-control IPs, according to the company. All told, Guardicore said the firewall dramatically reduces an organization’s attack surface to malicious actors who are attempting to attack, scan, or make a command-and-control connection into the company.
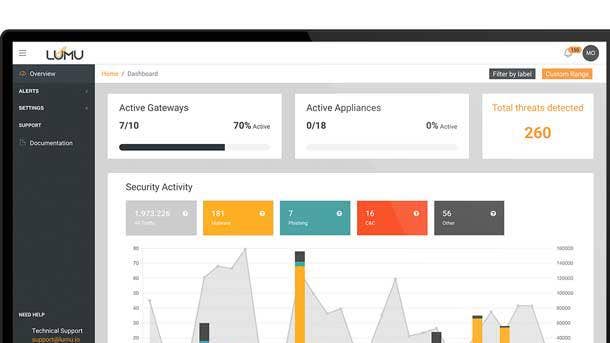
LUMU
LUMU is a cloud-based offering that collects and standardizes metadata from across the network, including DNS queries, network flows, access logs from perimeter proxies and/or firewalls, and spam box filters. It then applies artificial intelligence to correlate threat intelligence from those disparate data sources to isolate confirmed points of compromise, according to LUMU.
The product unlocks the value of a firm’s own data by closing the feedback loop to inform and improve self-learning capabilities while generating actionable insights that security teams can use to proactively detect existing compromises in their network. LUMU has also operationalized continuous compromise assessments, helping security teams measure and snapshot their exposure level in real-time.
LUMU said its offering was designed to complement other network security and incident response tools, providing security teams with real-time visibility into their digital infrastructure while confidently delivering the true picture of their compromise status.
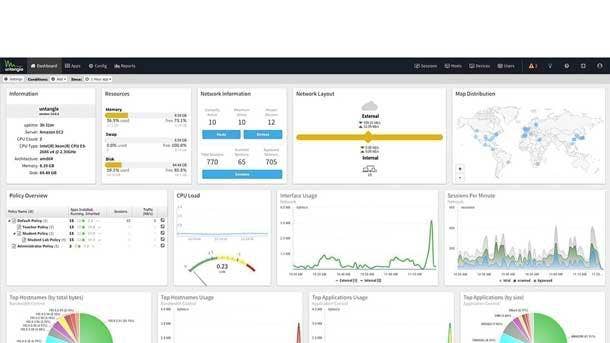
Untangle NG Firewall 15.0
The NG Firewall 15.0 provides an additional layer of security to keep SMBs’ assets safe and secure. Untangle said the firewall’s new features are effective against new and evolving cyberattacks without increasing costs, which provides administrators with more tools while giving business owners the ability to remain within their budget.
The new threat prevention app in the firewall analyzes web pages, web page associations, apps and files to determine what is or is not allowed based on the assessed threat risk level, according to Untangle. And the child-specific Kidzsearch filter ensures that only age appropriate search results are returned in content-sensitive environments such as schools and libraries.
Plus administrators can easily customize or format their NG Firewall email alerts so that they can be easily filtered or flagged for customers in their preferred email client application. And if a user attempts to access a web page that’s blocked by the NG Firewall 15.0, Untangle can display a customized notice with the company’s logo and a description of their internal access policies.