20 Hot New Cybersecurity Products Unleashed At Black Hat Las Vegas 2019
From inspecting encrypted traffic in real time to using machine learning to build profiles of containers to ranking security gaps by their potential business impact, here's a look at 20 hot cybersecurity products unleashed at Black Hat this year.

Building A More Secure Future
Vendors are taking advantage of Black Hat Las Vegas 2019's bright spotlight to launch new cybersecurity products, features, platforms and partnerships that will set the stage for the months and years to come. For the more than 300 exhibitors typically found at Black Hat, the gathering provides a chance to promote new products and highlight strategic shifts to an audience of more than 19,000.
Some of the more common areas for product innovation this year include risk and compliance, cloud security, email security and application security. CRN broke out the two most popular areas for new product development—network and endpoint security, and threat detection and response—into their own stand-alone slideshows.
From inspecting encrypted traffic in real time to using machine learning to build profiles of containers to ranking security gaps by their potential business impact, here's a look at 20 hot cybersecurity products unleashed at Black Hat Las Vegas 2019.
Sysdig Secure
The latest updates to Sysdig Secure use machine-learning capabilities to provide runtime profiling, anomaly detection and deeper insight into container runtime activity. Within 24 hours of an image being profiled, enterprises will have a learned container profile and insight into all process and file system activity, networking behavior and system calls.
After the model is built, DevOps and security teams can use the learned profile snapshot to create a policy set that can be automatically applied to container images, providing a scalable runtime defense for large-scale environments. Sysdig Secure's machine-learning-based profiling makes environments less susceptible to human error and leaves enterprises with a more complete view of their ecosystem.
The product now includes confidence levels auto-generated from the runtime profiling, giving security teams transparency and assurance into the container behavior. All told, enterprise teams are left with a better understanding of what has been learned, how it is being learned, and how accurate that baseline was.
SafeBreach GRID
SafeBreach GRID (Global Risk Detector) uses correlative analytics to identify security gaps and link them to their potential business impact. The product correlates data from many complex, multistage simulations that run continuously to produce a posture impact score for each security gap found.
The product ranks exploitable security gaps by potential business impact to help security teams prioritize which gaps to address. SafeBreach GRID also provides precise recommendations on how to improve security product configuration to minimize the potential business impact of a breach.
The tool includes a set of risk indicators to help teams track and report on their progress. SafeBreach GRID uses easy-to-understand indicators to quantify business risk, analyzes multiple simulation results to prioritize remediation activities, and advises on security configuration changes based on potential business impact.
Blue Hexagon Encrypted Traffic Inspection Using Deep Learning
Blue Hexagon uses deep learning to enable real-time inspection of encrypted traffic without negatively affecting network speed and performance or requiring additional devices. The feature offers customers a consistent deep learning-based threat detection platform for on-premises and the cloud, detecting threats in all traffic including encrypted web and network communications.
The Blue Hexagon proprietary Deep Learning HexNet architecture detects suspicious patterns that can be observed in the SSL/TLS communications during different stages of the connection. The deep learning models are trained on thousands of observations and characteristics that are used to separate a malicious encrypted tunnel from a benign communications channel.
These characteristics are tightly bound to the core communication functionality of the client and server encryption process. As a result, Blue Hexagon's deep learning can identify and stop threats in these communication channels even when the channel is encrypted.

ReversingLabs Exchange/Office365 AbuseBox
ReversingLabs’ new Exchange/Office365 AbuseBox offering and SMTP Connector identifies hidden malware that existing email tools miss, providing visibility into areas security analysts won't otherwise see and helping to triage high-priority phishing attacks.
The new analysis component is deployed seamlessly to analyze any link that ReversingLabs’ static file decomposition finds within emails, documents, multimedia, archives and programs. By inspecting millions of emails, the product makes the possibility of stopping threats in every email message a reality.
The product can deliver files and metadata to secure data lakes, providing the ability to retro-search and analyze local history to help uncover attacker strategies, tactics and techniques. It can also apply Advanced Search, which leads analysts to faster detection by allowing them to quickly traverse large metadata sample sets.

Spirent CyberFlood Data Breach Assessment
The new reconnaissance mode feature in Spirent's CyberFlood Data Breach Assessment mirrors the activity of an actual hacker to identify the processes, services and applications that compromise an enterprise network security zone. The new feature then automatically creates specific and accurate assessments based on that information.
CyberFlood generates realistic application traffic and security threats within live or production networks, providing organizations with a continual security assessment of their enterprise network infrastructures. The product uses actual attack components, true hacker activity and malware executables to validate an organization's vulnerability to cybercrime.
CyberFlood can assess and recommend policy, rules and heuristics changes to security or network infrastructure based on vulnerabilities, misconfigurations and other weaknesses discovered during a network assessment. And incorporating the NetSecOpen test suite into CyberFlood allows organizations to assess their security systems through performance test standard methodologies.
Qualys Global IT Asset Discovery And Inventory
Qualys’ Global IT Asset Discovery and Inventory application helps businesses track and secure all of their assets, including the ones they don’t know about. As networks continue to grow in size and complexity, actually knowing how many devices are on an organization's network at any given time has become increasingly challenging.
The free app allows users to automatically create a continuous, real-time inventory of known and unknown assets from on-premises, endpoint, multicloud, mobile, containers, operational technology and Internet of Things environments. It automatically classifies, normalizes and categorizes assets to provide fine-grained visibility into the system, services, installed software, network and users.
Qualys's Global IT Asset Discovery and Inventory uses passive scanning technology to instantly detect any device that connects to an organization's network. Upon detecting an unknown device, users can install a lightweight Qualys self-updating agent to launch a vulnerability scan or turn it into a managed device.
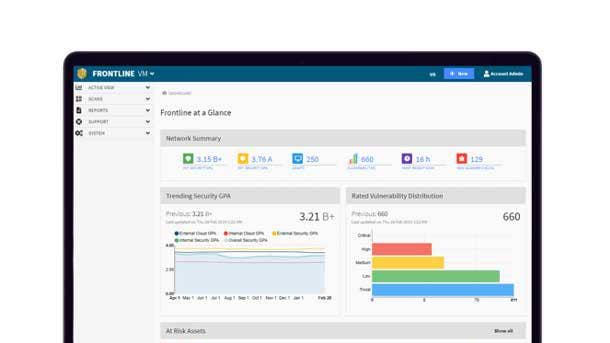
Digital Defense Frontline Insight
Digital Defense’s Frontline Insight provides an array of security analytics through the company's Software-as-a-Service security assessment platform. The product not only helps customers further reduce their security risk, but also helps them determine how best to evolve their information security program to optimize performance.
Frontline Insight offers comparison metrics such as highest risk vulnerabilities and days to remediate vulnerabilities and threats, both of which can serve as important barometers in the establishment of performance benchmarks. The product also offers comparison from an industry perspective, as well as by organization size and number of employees.
The product helps customers evaluate their security practices and successes against like organizations, said Digital Defense President and CEO Larry Hurtado. Organizations used to undertake intensive consultative studies to gauge their success, Hurtado said, but with Frontline Insight they now have that information available to them with just a few clicks.

Kudelski Security FumbleChain
Kudelski Security's FumbleChain project aims to raise awareness about blockchain security and how to protect the various deployments making up the blockchain ecosystem. Many large enterprises have identified the opportunities offered by blockchain technology, according to Kudelski, but struggle with how to secure it.
FumbleChain allows people to test their skills by attacking the chain and the FumbleStore running on top of it, which is a capture the flag (CTF) in the form of a fake e-commerce application. The project is written in Python so that anyone can easily read and modify the source code, and is modular so users can hack and add new challenges to promote continuous learning.
Security often takes a backseat to developing core functionality in blockchain deployments due to the misconception that blockchains are inherently secure, said Nathan Hamiel, Kudelski's head of cybersecurity research. Blockchain technology is actually incredibly nuanced and complex, Hamiel said, and a great deal of attention must be paid to its underlying security and cryptography.
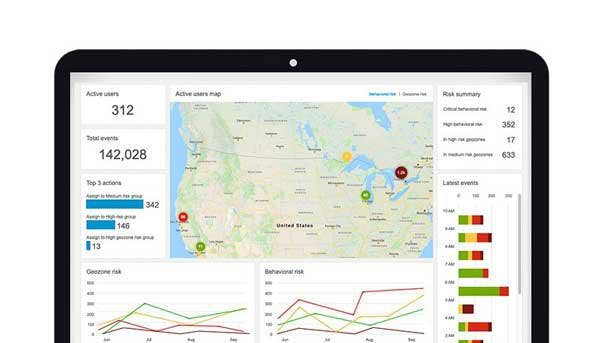
BlackBerry Intelligent Security Risk Score Analysis
BlackBerry Intelligent Security has the unique capability to grant access and issue authentication challenges based on real-time risk analysis, enhancing end-user experience and productivity without sacrificing security policies.
Based on real-time risk score analysis, BlackBerry Intelligent Security can grant access, adopt a policy, issue an authentication challenge, and alert and remediate. The product dynamically adapts its security and policy posture and will apply remediation when needed.
As a result, the BlackBerry Intelligent Security user experience and security/policy posture are mutually and dynamically optimized rather than in conflict. The product integrates seamlessly with other identity providers and systems to enable all data to be securely and easily shared.

Sysdig Falco Rule Builder
Falco Rule Builder is a flexible user interface deployed to create runtime security policies, making it easier for enterprises to utilize hardened open-source rules. Enterprises can visually interact with the Falco engine to create new customized policies that can be applied to hosts and containers based on their security and governance requirements.
Runtime rules are managed at scale and can be scoped and filtered to any aspect of the environment, such as a particular namespace, pod or container. Falco Rule Builder integrates with Sysdig Secure, and doesn't require deep technical knowledge of Falco expressions and commands.
The Falco Rule Library, meanwhile, enables enterprises to adopt rules created by open-source community members without having to spend time building the rules themselves. Sysdig's open-source team regularly hardens community rules to ensure they all meet enterprise-grade standards.
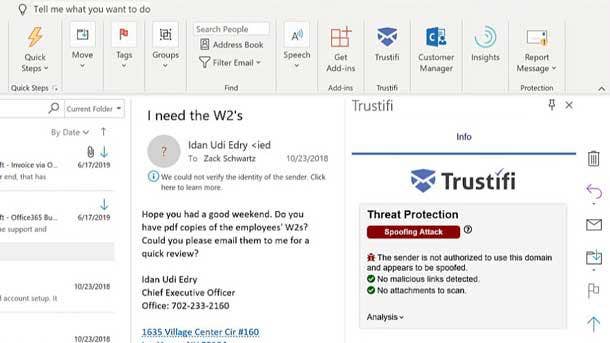
Trustifi Inbound Shield
Trustifi Inbound Shield provides advanced threat protection so that companies can protect the email they send and trust the email they receive in a single, easy-to-use offering. The product scans inbound emails in real time through a proprietary and sophisticated multilayer detection engine to protect against threats like phishing, malicious links and files, viruses, spoofing, and malware and ransomware.
Inbound Shield lets users knows when there is a threat, specifies the nature of the attack, detects malicious links and attached files, and includes a drop-down for details and what to do next. All of the information is logged for fast analysis.
The product uses sandboxing to detonate malicious content outside an organization's network; web scraping to scan URLs for malicious content; proprietary machine-learning algorithms to detect, protect and prevent users from unknown threats; and integration with the world's largest blacklist. Trustifi Inbound Shield works in Gmail, Outlook and Outlook365 add-ins.

Microsoft Azure Security Lab
The Azure Security Lab is a set of dedicated cloud hosts for security researchers to test attacks against Infrastructure-as-a-Service scenarios without risk to Microsoft's customers. Microsoft said it invited a select group of individuals to come and emulate criminal hackers in the customer-safe Azure Security Lab environment.
The lab program will enable participating researchers to engage directly with Microsoft Azure security experts. Accepted applicants will have access to quarterly campaigns for targeted scenarios with added incentives, as well as regular recognition.
The isolation of the Azure Security Lab means that researchers can actually attempt to exploit vulnerabilities in Azure. Those with access to the Azure Security Lab may attempt scenario-based challenges with top awards of $300,000.
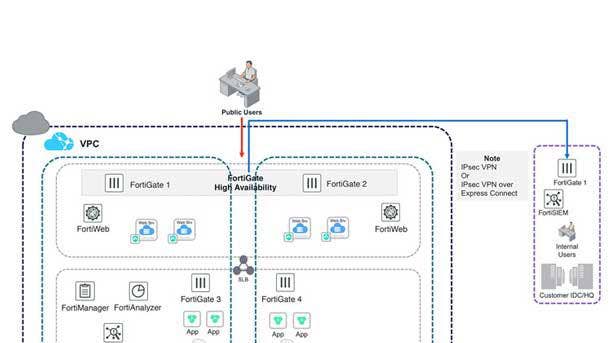
Fortinet Security Fabric For Alibaba Cloud
The combination of Alibaba Cloud and the Fortinet Security Fabric enables organizations to extend security visibility and control from the data center to the cloud, as well as the ability to ensure that organizations employ consistent security policies no matter where their applications are deployed.
By implementing the Fortinet Security Fabric on Alibaba Cloud, customers can apply consistent security policies throughout their hybrid infrastructures, as well as take advantage of multilayer security protection and operational benefits. Alibaba Cloud will integrate its APIs with the Fortinet Security Fabric to provide more consistent and effective end-to-end security to customers.
The Fortinet Security Fabric For Alibaba Cloud addresses a broad set of use cases including protecting cloud workloads, securing hybrid cloud and cloud-based security management. Alibaba Cloud's security functionalities can be managed through the Fortinet Security Management tools across Alibaba Cloud and on-premises deployments to streamline security operations.

Tanium-Chronicle Backstory Integration
The Tanium-Chronicle Backstory integration empowers customers to use Tanium Threat Response to proactively stream enterprisewide telemetry data directly from endpoints to the Backstory platform. This direct streaming provides flexible transmission options and reduces the time it takes to send data to Backstory.
Backstory quickly ingests the data and splices it with other log sources such as firewall, netflow and proxies. This in turn enables rapid exploration and identification of suspicious events for up to a year, Tanium said.
Tanium's platform provides a unified view across customer endpoints as well as the ability to quickly remediate issues at speed and scale. Chronicle's Backstory, meanwhile, provides massive-scale, cloud-based analytics, linking endpoint, network and other types of data into a coherent, context-rich picture.
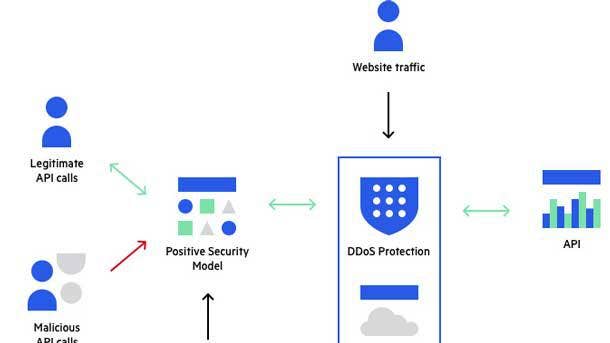
Imperva API Security-Red Hat 3scale API Management Integration
Customers of Imperva and Red Hat benefit from an integrated offering that helps manage, publish and secure their APIs. The integration provides security teams with visibility into all APIs that are externally exposed, as well as to specific threats associated with each API endpoint.
Imperva API Security allows users to see security events for API endpoints and automatically creates and enforces a positive security model layer from the customer's Open API specification document. Every addition or change to the APIs on Red Hat 3scale API management will immediately and automatically update the positive security model for said APIs, the company said.
All told, the integration makes it possible for customers to increase security for their APIs without compromising on business agility. Imperva provides an open-source tool hosted in GitHub and managed by the open-source community to integrate the two products.

Fugue-New Light Technologies Partnership
New Light Technologies (NLT) and Fugue have partnered to deliver public cloud configuration, drift detection, active drift enforcement, and security control gap analysis for NLT's Amazon Web Services and Microsoft Azure customers. The partnership extends Fugue's capabilities to all of NLT's Azure and AWS customers, strengthening the company's cloud service provider and managed service offerings.
Instead of having to write customer scripts, alarms and notifications, Fugue alerts NLT if any of the company's environments deviate in any way from the last build baseline, according to NLT Cloud Architect Dave Williams. Certain production accounts also enjoy self-healing infrastructure, meaning that the environment is automatically rolled back to its desired configuration if an anomaly is found.
Fugue's cloud infrastructure base-lining technologies will help keep NLT's cloud environments secure and compliant with policy, according to Fugue CEO Phillip Merrick. By partnering with Fugue, NLT will be able to keep customer data and applications secure in a highly efficient and scalable manner.

BlackBerry-Synnex Partnership
BlackBerry and Synnex have partnered to bring key cybersecurity services to the U.S. market by training, enabling and managing key reseller partners in the commercial and enterprise markets. Synnex is now responsible for distributing the BlackBerry Enterprise Mobility Suite, which helps enterprises manage and control access to IoT devices as well as secure communications for all messaging and file types.
Synnex also distributes BlackBerry Cylance advanced endpoint security offerings through its reseller network.
Combining the power of Synnex with BlackBerry's Enterprise Mobility Suite and BlackBerry Cylance's machine-learning and AI-based threat detection services will help the company attain new levels of mutual growth and customer/partner value-add in the years ahead, according to Richard McLeod, BlackBerry's global vice president of enterprise software channels.

Digital Defense-University of Texas at San Antonio Partnership
University of Texas at San Antonio (USTA) students and faculty will be able to utilize Digital Defense's Frontline.Cloud platform to evaluate the security posture of applications, systems and networks in classroom and lab environments on and off campus.
Students will not only be able to assess the security posture of software applications and systems they build and run on lab networks, but will also learn how to use industry-recognized tools to establish and execute an effective vulnerability life-cycle management program.
USTA will have access to three different Frontline.Cloud systems, providing students with vulnerability and web application scanning capabilities, as well as testing for hidden threats on target networks. San Antonio is home to one of the largest concentrations of cybersecurity experts and industry leaders outside Washington, D.C.

Intelligent Security Systems-DEFTEC Partnership
Intelligent Security Systems (ISS) has entered into a new strategic technology partnership with solution provider DEFTEC to deliver advanced analytics-driven products that will improve the security and efficacy of U.S. military operations. The partnership is intended to provide the U.S. military with higher levels of intelligence to improve operations and ultimately save lives.
The partnership will allow DEFTEC to tap into ISS' vast experience and expertise in facial recognition, under-vehicle surveillance systems, and license plate recognition. ISS SecurOS FaceX expands the ability to identify and match faces with greater versatility, resolving long-standing facial recognition challenges related to camera viewing angles, facial expressions and diverse lighting conditions.
ISS SecurOS UVSS, meanwhile, combines advanced software and hardware for under-vehicle surveillance, employing a number of ISS' analytics patents. And ISS SecureOS Auto-License Plate Recognition can accurately capture license plates at speeds up to 155 mph in virtually any weather or environment.

New Net Technologies-Greenbone Networks Partnership
New Net Technologies has partnered with Greenbone to leverage its technology for a white-labeled offering and offer vulnerability management to its customers for the first time. Greenbone's technology will enable NNT's customers to identify vulnerabilities in their IT infrastructure, eliminating harmful and costly security breaches.
Vulnerability management is one of the most essential controls in cybersecurity and is a foundational requirement for large and small organizations alike, according to NNT CEO Mark Kerrison. Greenbone Chief Marketing Officer Dirk Schrader, meanwhile, praised NNT for its commercial and technical understanding of Greenbone's vulnerability management product.