Spam Turns the Big 3-0

May 3, 1978: A Marketer Sends the First Spam Message
It had to start somewhere. Little did anyone know at the time that a relatively small-scale marketing idea would later set a precedent for future spammers generating millions of dollars in profit by targeting end users around the world. In 1978, however, Gary Thuerk, a marketing manager for Digital Equipment, paved the way for the spam industry with a program that sent a single e-mail message to numerous users over a network of government and university computers known as ARPAnet.
Initially, Thuerk send the message with the intention to publicize open houses in the Los Angeles and San Mateo areas where the company would be releasing its new computers. Thuerk reportedly wanted to send invitations to hundreds ARPAnet members, but realizing the enormity of that undertaking, innovated a way to send out one e-mail to everybody on the list. Despite the fact that this new marketing technique was extremely effective at generating sales, Thuerk received strong rebuke from his company and members of the network community, who criticized him for abusing e-mail technology for advertising purposes.
For a period of about 16 years following its introduction, spam was mainly relegated to fund raising and other promotional announcements via university networks, experts say.
"A lot of early spam (consisted of) people throwing up fliers trying to drum up some business or trying to make money or trying to get a message out about a social issue," said David Cowings, senior manager of operations for Symantec Security Response. "It was an annoyance."
In fact, the term "spam" didn't enter the vernacular for the intrusive, financially motivated mass e-mail until more than a decade after the infamous 1978 e-mail.

April, 1994: First Commercial Spam Business
Taking Thuerk's success one step further, immigration attorneys Laurence Canter and Martha Siegel, a husband and wife lawyer team, were credited with developing the first massive commercial Usenet spam business advertising their Green Card services, as well as creating the first spamming tools. The duo solicited business by enrolling thousands of clients in a Green Card lottery.

1998: Proliferation Of Homemade Spam
Throughout the late '90s, most spam messages were generated manually, sent through an individual's at-home, ISP outbound mail server. During this time, spam was created with tools to obfuscate and forge e-mail headers, which were delivered via bulk mailing software.

1999: Growth in Obfuscation Techniques
This year saw a huge growth in HTML spam. While the messages remained virtually unchanged on the user side, this technological development allowed attackers to use modem pools and to randomize IP origination.
"It separated the lines between spam being a simple annoyance, to a security threat for a lot of companies," said Dave Cowings, senior manager of operations for Symantec Security Response.
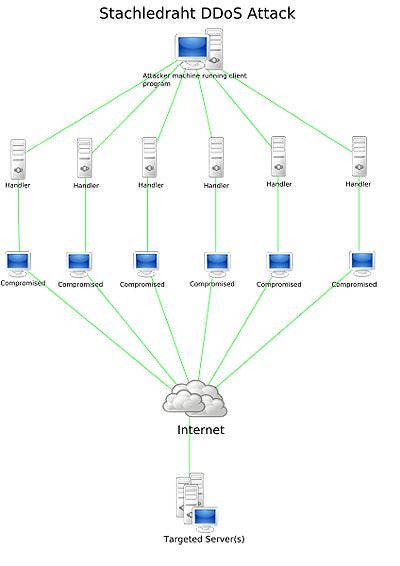
2000: Spam Crackdown Leads To Denial of Service Attacks
As spam became more of a problem, reaction was swift and harsh. Spammers who hacked open mail relays began being blocked by blacklisting sites and services, resulting in numerous Denial of Service attacks.
"The problem with that technology was it was using a sledge hammer to stop spam and you lost a lot of legitimate mail," said Dave Cowings, senior manager of operations for Symantec Security Response.
Consequently, spammers began to use non-secure, open-proxy servers to create and distribute spam.

2001: First Spamming Viruses Appeared
These viruses included Melissa, and the notorious "I Love You" virus, which, when opened, contained code that wreaked havoc on millions of end users' computer.
Meanwhile, security experts start to notice more financially driven spam, as well as some of the first mass mailing worm viruses that crawled through an unsuspecting user's address book in order to send out more e-mail, or plant Trojans, to everyone on the list.
2003: Spammers Branch Out and Get Creative
Users are treated to more spam variations, such as image spam, PDF spam, and NDR spam, which attackers piloted in varying amounts to test its effectiveness. And with varying results. While PDF spam initially spiked in effectiveness, often the files were too large to successfully make it past filters. Meanwhile, attackers found success with image spam as photos continually took up less bandwidth.

2003/2004: Trojans and Zombies and Bots (oh my)
A veritable monster's ball. Spammers begin to refine attacks by installing Trojans and other malware on mail servers.
In addition, broadband connectivity becomes less expensive. Naturally, increased bandwidth capabilities allowed a broader base of spammers to execute attacks more efficiently -- instead of deploying millions of messages from one machine, a series of smaller attacks could be conducted from numerous machines.
And further adding to the spammers' arsenal, the lifespan of attacks become progressively shortened to a matter of hours. Keeping attacks relatively brief and mutable enables attackers to successfully avert many reactive spam technologies that often day days to develop.

2005: Automatic Spam
Really, how else are you going to unleash an attack on millions of PCs? Automation makes it so much easier for spammers.
Going one step further, botnets become the major delivery source for spam while attackers refine paraphrasing and text randomization techniques.

2004/2005: IM Spam Takes On a Life Of Its Own
Any new vector for communication is going to open up an array of possibilities for spammers. And IM was no exception. While IM spam has been around for a while, it recently experienced a resurgence, as IM became more ubiquitous in the workplace. Attackers could use the address books from the acquired victim to further generate spam attacks.
Or, since many workers use the same credentials for numerous functions, spammers often attempted to harvest usernames and passwords from their victims in order to infiltrate other corporate and personal applications.

2006-2007: Event Spam Takes Center Stage
Superbowl Website. Benazir Bhutto's assassination. Valentine's Day. And tax season. Like the paparazzi, spammers are waiting to exploit any high profile event that will draw a wide base of users. Despite being a global medium, researchers say that they have seen the localization of spam only in the last one to two years. This trend will likely continue, they say.
"It's all about localized malware," said Dave Marcus, security research and communications manager for McAfee Avert Labs. "It comes down to certain fact. If there's money in a certain part of the world, you have to know the language."
And Today: Spamming For Google
No doubt, Google has mass appeal, even for spammers. Last year marked a milestone for spammers who mastered the art of using reputable brands to trying and deliver spam and phishing messages to victims via the popular search engine. Last November, researchers reported the emergence of a technique where spammers manipulated Google's advanced search engine queries, as well as the " I'm feeling Lucky" option to put phishing or spam Websites at the top of the search engine's ranking system and mislead users to clicking on a spamming site.
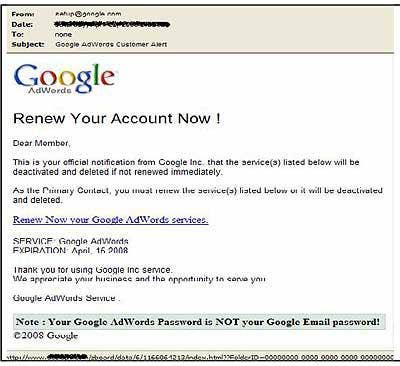
Meanwhile, Symantec reported that spammers had also found ways to manipulate Google URLs used from AdSense and redirected users to phishing sites. Google AdWords is a service that allows advertisers to intelligibly connect with individuals who search using Google. Unsuspecting users are enticed to access a malicious link to allegedly update or renew account information. However, the link leads to a phishing Website that requests users to provide personal indentifying information that will eventually be harvested and/or sold by the attackers.
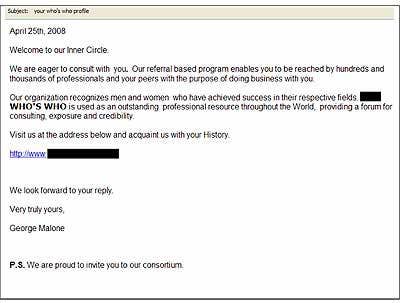
Spammers Love To Network
Well, who doesn't really? With the explosive growth of personal and professional networking sites comes the increase in spam e-mails that promote even more "new" networking sites. In one such example, the recipient is invited to join an organization that claims to recognize, "Men and women who have achieved success in their respective fields." The user is then asked to join the "inner circle" and enticed to click on a link leading to a registration page and asked to provide personal history and identifying information. Unbeknownst to the victim, however, this information intended for later identity theft and future spam and mass mailer attacks.
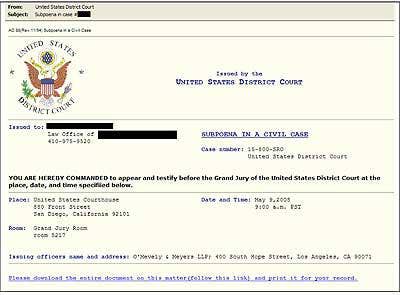
Spear Phishing
Recently, spear phishers have upped the ante on their attacks. In their most recent endeavor, attackers targeted thousands of government executives who received an official-looking email that purported to be from a United States District Court. The message appeared to be a subpoena, commanding the recipient to testify before a Grand Jury. A fraudulent link was embedded in the body of the message along with instructions requesting the user to download the document and fill in personal information such as name, address, and passwords. Once the fake registration form was downloaded, the personal information submitted by the user was recorded by a keystroke logger Trojan and sent to a database for the attackers to harvest.

You Wanna Be A Movie Star spam?
A tried and true technique -- capitalizing on users' dreams of becoming a movie star -- never seems to die. In this recent spam, attackers solicited users to provide names, mailing addresses and telephone numbers in order for them to obtain information about becoming an extra in a movie -- very appealing to those with big dreams about becoming the next big thing. However, once the user clicks on the URL, the link redirects them to the spammer's Website. Instead of a movie contract, most of these users will be treated to identity theft and a lot more spam.

Tax Time Phishes
Tax Time phishing is nothing new. And make no mistake -- most tax spam will either install keystroke loggers or entice unsuspecting users to submit sensitive information such as credit card and social security numbers to use or sell on the black market. This recent version of the IRS scam offers an interesting twist. Instead of an information-stealing bot, the user is subjected a popular Web-based game in which you incarnate as a vampire that gains more power every time end users click on his link. And while this IRS fraud won't steal your credentials, users won't receive the whopping tax refund of they had been promised.
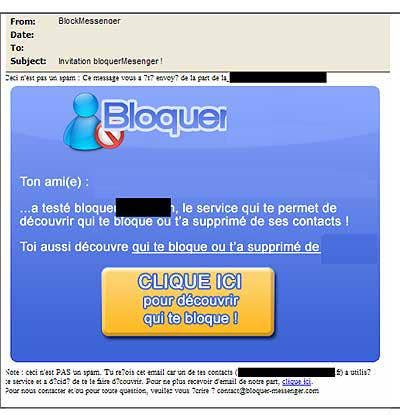
With Friends Like That
Spammers are not above exploiting people's deep insecurities -- particularly when it comes to knowing who has shut them out of their IM buddy lists. In this attack, spammers offer users the opportunity to scan through their messenger buddy list and highlight who they would like removed from it. The attack invites the user to click on a URL in order to find out who has blocked their name on their instant messenger buddy lists.
Before this can be accomplished, the spam asks the poor "blacklisted" users to provide their username and password -- a not so discreet attempt to acquire login credentials. Once this information is obtained, attackers bank on the fact that they can often use these same passwords to gain entry into banking and other financial accounts as most users use the same password for multiple applications.