Olympic Phishing: 11 Scams To Watch
It's a trend that seems to be here to stay -- spammers, phishers and malware writers capitalizing on highly publicized, well-trafficked media events as vehicles to propel and distribute their malicious payloads faster and more efficiently than ever before. No global event is more in the public eye than the 2008 Beijing Summer Olympic Games. And the malware writers, even those with bad grammar, know that just about any subject line with the word "Olympic" is going to be opened by millions of people -- some of whom will receive malicious code instead of news, tickets or any variety of Olympic-themed products.
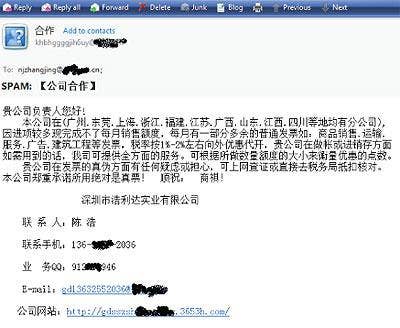
In the last few weeks, MessageLabs Researchers have detected a slew of Olympic spam. Here are a few subject lines to watch out for:
- Beijing Olympics cancelled, moved to Atlanta
- Emailing: Beijing takes dog off the menu for Olympics - Yahoo! News
- Obama buys 10 million Olympics ad
- 2008 Olympic Games will possible not take place
- Athletes ponder wearing masks to fight pollution - Olympics - Yahoo! Sports
- 2008 Olympic Games are under the threat
- FW: Learn Chinese for the Olympics
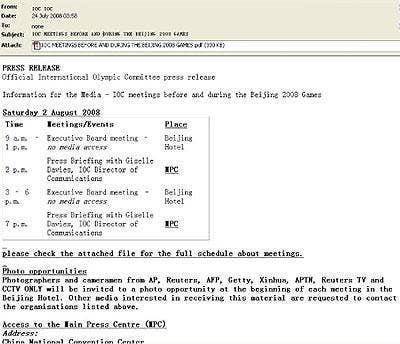
It's not just consumers that are the victims of Olympic spam and cyber attacks. MessageLabs researchers have uncovered evidence of highly targeted malware distributed in legitimate looking e-mails appearing to be from the International Olympic Committee. The e-mails were sent to participating nations' national sporting organizations and athlete representatives.
At least 19 domains have been targeted with 57 e-mails, all of which contain press release and media information relating to the International Olympic Committee that seems to strengthen their validity. The content of the message even appears to contain content directly from the IOC Web site, further legitimizing the malicious spam campaign.
Upon opening the PDF file attachment, a malicious executable is dropped onto the user's computer. The dropped executable presents the viewer with similar information to that contained in the press release used in the body of the e-mail text. Upon closer inspection, however, the original e-mails actually appear to originate from several Google Mail accounts.
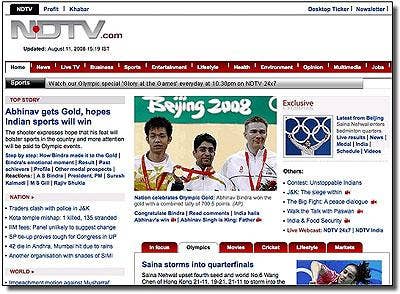
Users are not just in danger of being phished by Olympic cyber scammers. Users can also become infected by visiting seemingly legitimate sites infected with malicious code. In fact, several Web pages of respected news organizations featuring images and stories highlighting the Olympics have been compromised with malicious content. Sophos researchers say that the Indian news Web site NDTV, which was syndicating AFP's Olympic content, became the victim of a SQL injection attack by failing to properly secure their backend ASP/SQL infrastructure. Consequently, Web surfers clicking on this site in search of Olympic news will likely be treated to a dose of malware installed on their computers.

A recent Symantec State of Spam report detected Olympic phishing e-mails, sent en masse to capitalize on viewers' interest in Olympic events. Following recent phishing trends that use high traffic media events to distribute malware, spammers sensationalized Olympic events in spam e-mails in order to entice users to open malicious links.
In the case of these e-mails, the recipients are asked to click on a link that hosts malware. Instead of an annoying spam message or an advertisement for a spam product, these e-mails are designed to infect other computers with viruses and Trojans.
The image to the left contains some of the subject lines found in recent Olympic spam.
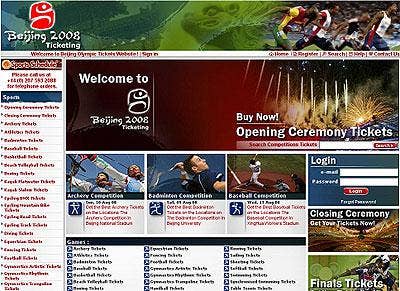
An elaborate scam involving the sale of Beijing Olympic tickets is making its way around the world. However, there's one problem. Victims of the scam never actually get anything once they purchase what they think will be a ticket to the Olympic games. According to Sophos researchers, the International Olympic Committee has successfully shut down a domain involved in the non-existent Beijing Olympic tickets. Yet the scammers remain undeterred.
In this latest scam, the Website advertising Olympic tickets appears to be from a legitimate source. Once you look deeper, however, you'll see that the site contains certain flaws that give it away as a phishing site. The use of e-mail address is the only means of communication with the advertiser, and there is an inconsistent contact informationand#8212;the listed phone number is a UK number, however the office is a hosted U.S. e-mail address.
Remember, if it's an offer you can't refuse, you probably should.
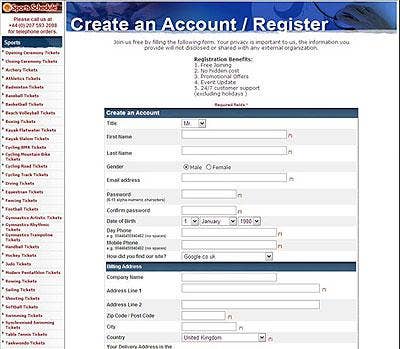
Meanwhile, Trend Micro Advanced Threats Researcher Paul Ferguson detected another site supposedly offering more Beijing Olympic tickets. This and other fake sites are posing as legitimate ticket outlets, only to take credit card numbers away from unsuspecting victims who think they're making an online purchase. However, there are warning signs. Filling out the form should be your first red flag, Trend Micro experts say, because some confidential information is required in the registration. Only when the personal information is filled in can the user log in to purchase tickets.
Trend Micro researchers also tried to enter bogus delivery address and phone number and found that the site accepted all the information, regardless of validity -- a clear indication that the "ticket sellers" never intended to deliver the tickets once the payment is received.

Some phishes try to accentuate the drama as much as possible to exploit people's sense of fear. In this phish that preceded the Olympics, unsolicited e-mails targeted unsuspecting users with a spam campaign claiming that another earthquake has just devastated China and could threaten to derail the upcoming 2008 Beijing Olympic Games.
Sensational subject lines include 'Million dead in Chinese quake" accompanied by a link to a .cn domain Web site announcing that an earthquake measuring 9.0 on the Richter scale has hit Beijing, causing millions of deaths and threatening the 2008 Olympic Games with possible cancelation. Slightly skeptical users might be convinced that the announcement is legitimate by looking at the domain source -- .cn is the official national domain of China. The site contains another link to a video, which advertises that it will showcase additional details of the disaster. However, when the link is opened, users receive the malicious Trojan Nuwar-E on their computers.
"The recent Chinese earthquake is still so fresh in people's minds, that many computer users won't think twice before opening this email and clicking on the link," said Carole Theriault, senior technology consultant at Sophos. "The spammers are using one of the most common tricks in the book in an attempt to spread their malware, and if people continue to open unsolicited emails, unfortunately the spammers will continue. All computer users need to think twice before opening messages from people they don't know -- the chances are it will be spam and could result in your computer becoming infected."
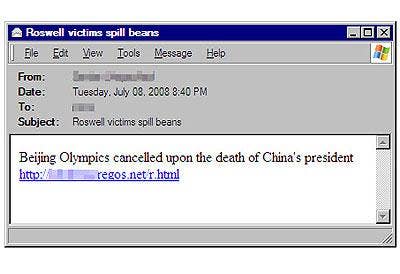
No doubt, spammers have a flair for the dramatic. The subject in these spam messages seems to offer news that appeals to users' morbid curiosity, offering a link that appears to provide more details. Needless to say, the link is likely to be malicious and lead viewers to malicious code.
In this spam e-mail detected by Trend Micro researchers, there are some clear indications that the message is not legitimate. For one, there doesn't seem to be any clear relationship between Roswell victims and the 2008 Beijing Olympics. But then again, who knows?
"This spam is showing unrelated subject heading and email body, possibly the result of using spam templates," Trend Micro researchers say.
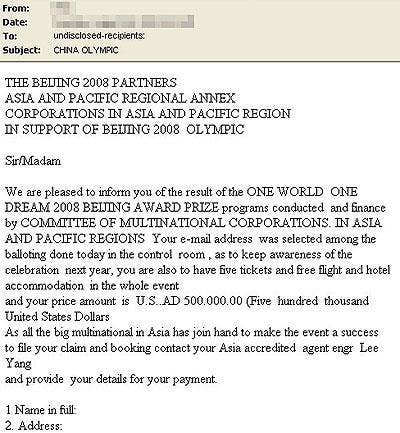
And who couldn't use an extra $500,000? There's just one small catch. Before you can claim your price, you have to first e-mail six contacts to your information agent Mr. Chang Lazarus. Say what?
Trend Micro researchers discovered this Olympic spam several weeks before the 2008 Beijing Olympic opening ceremonies, exploiting both the excitement of the Olympics and users' desire to win lots of money at strange contests they've never entered. But this type of spam got an early start -- phishes announcing Beijing lotto winners have actually been circulating as early as last year, experts say.
"This looks like another variation of the notorious 419 scams we've come to hate over the years," Trend Micro researchers say.

A new set of spam, delivered around the time of the opening ceremony Friday showing images of the amazing architectural feats of the venues from a bird's eye view. Wow.
However, while clicking through a colorful slideshow of awe-inspiring Olympic structures, viewers would also be treated to a BackDoor-CKB executable which will wreak havoc on their computers. The malware will of course be masked by the PowerPoint slideshow. This particular phishing message appeared to be hosted in the city of Henan, near Shanxi, China.
Experts say that while the images might be alluring, users should be wary of what is going on in the background.

While some Olympic phishers and other malware writers aim to fulfill their financial objectives by directly exploiting the 2008 Beijing Olympics, others are targeting issues and events surrounding the games that might capitalize on tragedy and viewers' fear of political atrocities.
Recently McAfee's Avert Labs researchers detected a piece of malware related to the tumultuous Tibetan situation, distributed to users as a simple Flash movie. Once opened by a viewer, the film executes the file called racefortibet.exe, displaying a cartoon with a skilled Chinese gymnast performing a challenging and highly contorted routine on a "vaulting Bbox" only to receive a score 0 by the judges. While the gymnast's performance is "re-wound," several graphic photographs of real events occurring throughout China and Tibet are displayed on the screen as a visual "flashback."
As users watch the drama unfold in the video, a series of malicious executable files are stealthily dropped on their computers -- a rootkit containing data-grabbing keyloggers.