Who's Who? 10 Hot Authentication Products

Who's Who?
These days, being able to prove that you are who say you are is more important -- and let's face it -- harder to do than ever before.
And not just to defend data against external hacker threats, although those are still in abundance. SMBs and mid-market companies face more pressure to beef up authentication methods, as credit card companies, government agencies and auditors alike have tightened the reins on compliance regulations such as PCI, HIPAA and Sarbanes-Oxley.
From biometrics, to Web sites, the cloud and mobile solutions there are now more ways than ever to prove that you're the real deal. Here are 10 authentication products that caught our attention.

ActivIdentity ActivID Credential Management System Appliance
ActivIdentity’s universal access product aims to help organizations meet their security and compliance objectives and significantly improve their ROI by providing users with a single, secure credential to access computer, network, application and potentially physical resources.
Touting installation in less than 30 minutes, the authentication appliance is a full credential management solution, incorporating preinstalled CMS software, a configuration wizard, HSM, embedded data base and local certificate authority. The device also issues secure credentials for smart cards and smart USB keys, and features tamper-evident audit features that log all event activity, designed for compliance and internal reporting. The device, which can scale to 10,000 users, also touts an automatic encrypted backup and system restore, as well as a Web-based self-service for end users.
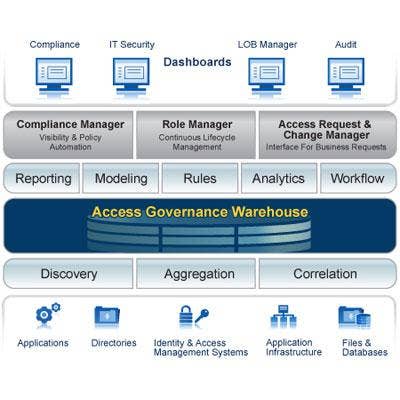
Aveksa Role Manager
Aveksa, which primarily serves enterprise customers, aims to rid companies of orphaned accounts and ensure appropriate security and access controls for the appropriate people. Its flagship products Aveksa Compliance Manager, Aveksa Role Manager and Aveksa Access Request and Change Manager, work collaboratively to offer enterprise IT administrators a user-friendly interface enabling them to request or change access rights once an employee's job has terminated or shifts within the organization.
Specifically, Aveksa Role Manager offers a configurable workflow processes, flexible role structure, and access discovery and pattern analytics to collect, assess and analyze established roles, while defining new ones. The product also touts powerful rules that apply "what if" scenarios, and automated role certification, as well as reporting, analytics and maintenance capabilities.
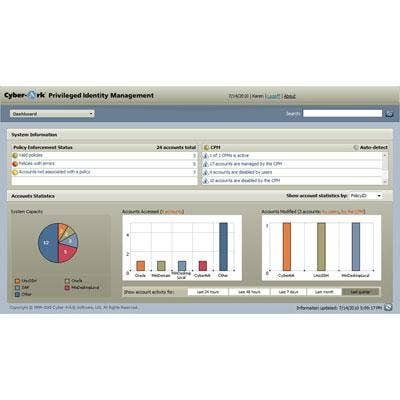
Cyber Ark Privileged Identity Management Suite
Cyber-Ark's Privileged Identity Management (PIM) Suite is an enterprise-class, unified policy-based solution that secures, manages and monitors all privileged accounts and activities associated with datacenter management -- whether they're reside on-premise or in the cloud.
As its name suggests, the CyberArk PIM controls access to privileged accounts, allowing channel partners to monitor and record privileged sessions, manage applications and service credentials and grant granular control to privileged users.
Altogether, the PIM Suite identifies, centralizes and secures privileged policies and accounts, applies policies to privileged identities based on the user's role, personalizes access to privileged identities, and automatically resets access to privileged identities while logging and recording all associated activities for compliance and auditing purposes.
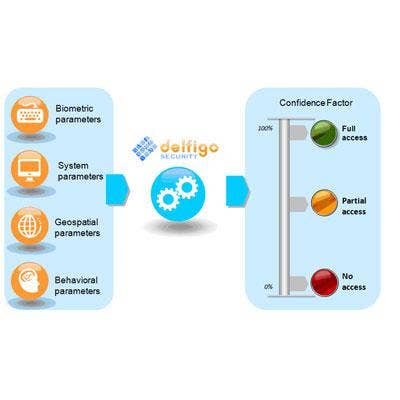
Delfigo DSGateway
Delfigo's DS Gateway combines strong authentication with advanced cognitive capabilities to uniquely answer the question, "Are you who you say you are?" when a user accesses a system. Specifically, the product evaluates 14 individual identity attributes to assign a Confidence Factor (CF), and transparently provide the appropriate level of system access. The identity attributes captured and consumed by DSGateway's decision engine cover authentication factors from each of three categories, which include something you have, something you know and something you are.
DSGateway does not require the distribution of any hardware tokens or smartcards, or require users to download or install any software. In addition, there are no required changes in user behavior. Users simply type their password and they are enrolled in "silent mode." There are no additional steps added to login or transaction procedures, no help desk training requirements and no requirements for installation of supplementary software or regular software updates.
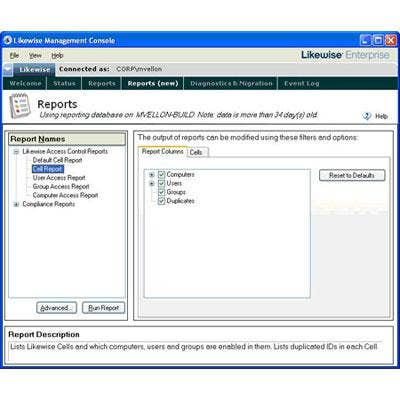
LikeWise Enterprise
LikeWise Enterprise is an enterprise software authentication product that allows seamless integration of Linux, UNIX and Mac systems with Microsoft Active Directory. Organizations of all sizes running mixed networks and mixed identity management systems can use Likewise Enterprise to allow UNIX, Linux and other systems/applications to integrate with Microsoft Active Directory for their authentication needs.
The product, which provides a single user name and password for Windows and non-Windows systems, features centralized administration including user provisioning and deprovisioning for Linux, UNIX and Mac OS X. Meanwhile, the Likewise Administrative Console is a pluggable framework that provides MMC-like functionality and runs on Mac OS X and any Linux platform.
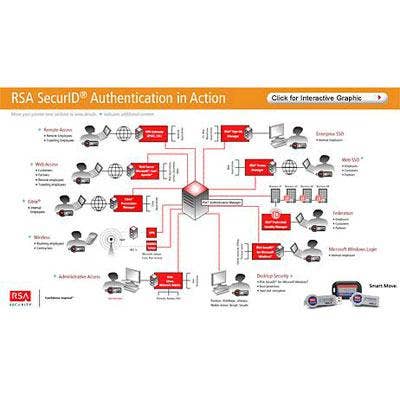
RSA SecurID
One of the most recognized authentication products, RSA's SecurID is a two-factor authentication system used by more 40 million people across more than 30,000 organizations worldwide.
The product is engineered to assure user identities and protect against unauthorized access to applications and resources across numerous physical locations. RSA SecurID technology is comprised of both a broad range of hardware and software authenticators, which provides end users with a one-time password designed to change every 60 seconds. Its software engine -- RSA Authentication Manager -- also scales to support millions of users and provides the benefit of technical certification with more than 300 products.
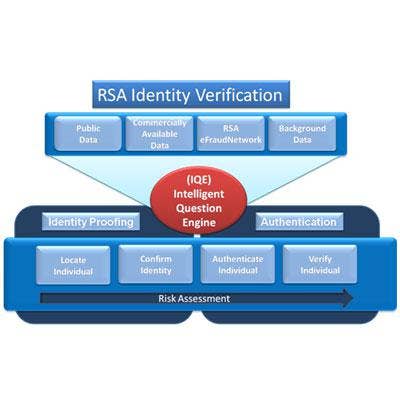
RSA Identity Verification
RSA's Identity Verification is a strong authentication solution designed to assure user identities in real-time and help prevent the risk of identity theft and fraud. Relying upon knowledge-based authentication technology, RSA Identity Verification is engineered to present a user with a series of top-of-mind questions, which confirm a user's identity within seconds without requiring a prior relationship with the user. RSA Identity Verification is used by more than 200 organizations.
SafeNet SafeWord 2008
SafeWord 2008, SafeNet’s out-of-the-box authentication solution, is designed to provide strong security combined with straightforward installation and setup for employees and partners who routinely access their company’s Web-based applications and corporate network via a VPN.
The authentication product offers both flexibility and lower cost of ownership by allowing organizations to use the same management software to deploy both hardware and software tokens side by side. Software solutions include MobilePASS, a mobile authentication solution that allows users to generate one-time Passwords directly on their mobile phones.
MobilePASS is available for iPhone, BlackBerry, Android, J2ME and Windows Mobile devices, as well as the eToken PASS: a small and portable OTP hardware authenticator available in Time-sync and Event-based configurations.

Symantec VeriSign Identity Protection Authentication Service/VIP Access For Mobile
VeriSign Identity Protection (VIP) Authentication Service is a cloud-based authentication service that enables enterprises to secure online access and transactions in order to obtain compliance and reduce the risk of fraud. VIP provides an additional layer of protection beyond the standard user name and password by requiring a dynamic one-time use six-digit security code generated by a user's VIP credential.
Meanwhile, the VIP Access for Mobile (AFM) application is offered for free and transforms more than 600 different types of mobile devices into VIP credentials for strong authentication, including the most popular handsets -- iPhone, BlackBerry, Windows Mobile and handsets supporting the J2ME and BREW platforms.
Symantec VeriSign Web Site Authentication
The VeriSign Extended Certificate triggers high-security Web browsers to display the organization’s name in a green address bar and show the name of the Certificate Authority that issued it. The Certificate Authority uses an audited, rigorous authentication method and browsers control the display, making it difficult for phishers and counterfeiters to hijack a brand and fool customers into providing sensitive information.
For non SSL sites, the VeriSign Trust Seal helps establish business legitimacy by showing that a business has passed an established and proven authentication process. Passing the authentication process shows the world that VeriSign has verified a business's identity and that they are the rightful owner or operator of their Web site.