The 25 Tech Bug Bounty Programs With The Biggest Payouts

Reaping The Spoils
Vendors across the cybersecurity and IT landscape have in recent years embraced bug bounty programs, or the compensation of outsiders for uncovering and reporting flaws in their hardware, software or applications.
Fifteen technology vendors selling through the channel operate at least one public bug bounty program, according to CRN research, with Google running four and Microsoft running eight. Eleven of those vendors operate a digital 'hall of fame' to recognize security researchers for their findings, while two suppliers also provide hackers with goodies such as t-shirts for finding a bug.
Seven of the vendors run their own bug bounty program, with six companies managing their programs using Bugcrowd and two companies using HackerOne. Bugcrowd and HackerOne provide organizations with a SaaS platform and access to the security researchers necessary for running a successful bug bounty program.
Here's a look at how much the 25 programs compensate security researchers for their findings.

25. AVG Technologies
Headquarters: Brno, Czech Republic
Top Bounty: $1,000
Minimum Payout: $50
Program Managed By: Bugcrowd
AVG Technologies said it strives to keep abreast on the latest state-of-the-art security developments by working with security researchers and companies. The initiative is targeted purely on client-side applications, with any server or back-end testing falling outside the program's scope.
AVG had paid out rewards on 32 vulnerabilities as of early February, with an average bounty of $200 over the past three months. Some 230 hackers have joined AVG's bounty program, with 18 security researchers being recognized by Bugcrowd for having reported important security issues.
Targets for the bounty program include: AVG AntiVirus FREE; AVG Internet Security for advanced protection against viruses and ransomware; AVG Antivirus Protection FREE; AVG Antivirus Protection PRO; and AVG AntiVirus for Mac.
24. Cylance
Headquarters: Irvine, Calif.
Top Bounty: $1,000
Minimum Payout: $50
Program Managed By: Bugcrowd
Cylance rewards reports according to their severity on a case-by-case basis as determined by the company's security team. The company said it may pay more for unique, hard-to-find bugs, and less for bugs with complex prerequisites that lower risk of exploitation. Critical bugs will receive rewards of up to $1,000.
Three-quarters of vulnerability submissions have been accepted or rejected by Cylance within 13 days, according to Bugcrowd. Cylance had paid out reward on 56 vulnerabilities as of early February, with an average bounty of $170 over the past three months.
Targets for the bounty program include: the CylancePROTECT endpoint security platform; the CylanceV malware detection tool; the CylanceINFINITYENGINE embeddable malware detection tool; and the CylanceOPTICS endpoint detection and response (EDR) offering.

23. Malwarebytes
Headquarters: Santa Clara, Calif.
Top Bounty: $1,000
Minimum Payout: $100
Program Managed By: Company
Malwarebytes said its coordinated vulnerability disclosure program incentivizes external researchers to work with the company responsibly by promoting an open communication channel with the company's engineering division.
The company determines the size of its bounty awards based on the bug severity and exploitability and reserves the right to increase the amounts on a per-case basis. Additionally, submissions flagged by Malwarebytes's research team as being particularly innovative are entered into the Malwarebytes Hall of Fame and get cool company swag.
The scope of the bounty program includes remote code execution vulnerabilities in Malwarebytes's products and disclosure of private user information in the www.malwarebytes.com domain. The company is also interested in vulnerabilities in its web services which may result in compromise or disclosure of confidential or personal information.

22. Bitdefender
Headquarters: Bucharest, Romania
Top Bounty: $1,500
Minimum Payout: $100
Program Managed By: Bugcrowd
Bitdefender said that being proactive rather than reactive on emerging security issues is one of the company's fundamental beliefs. The company relies of Bugcrowd's vulnerability rating taxonomy for prioritization of findings, but reserves the right to either downgrade or upgrade findings' severity based on the criticality of the underlying risk to the company.
Three-quarters of vulnerability submissions have been accepted or rejected by Bitdefender within three days, according to Bugcrowd. Bitdefender had paid out reward on 87 vulnerabilities as of early February, with an average bounty of $370 over the past three months.
Targets for the bounty program include: the Bitdefender Total Security 2017 anti-malware software; the Bitdefender GravityZone Business Security anti-malware offering; bitdefender.com; and bitdefender.net.

21. Cisco Meraki
Headquarters: San Francisco, Calif.
Top Bounty: $2,500
Minimum Payout: $100
Program Managed By: Company
Cisco Meraki said its vulnerability rewards program is an important component of the company's security strategy, encouraging external researchers to collaborate with the company's security team to help keep networks safe.
Cisco Meraki-operated web properties, Systems Manager client applications, and Cisco Meraki hardware devices are in scope of the bounty program. Any bug that substantially affects the confidentiality or integrity of user data is likely to be in scope for the program, according to the company.
Bugs are rewarded based on the severity of the vulnerability found, as determined by the Cisco Meraki reward panel. The panel consists of the members of the Cisco Meraki Security Team as well as Chief Technology Officer Bret Hull.

20. Sophos
Headquarters: Oxfordshire, England
Top Bounty: $3,000
Minimum Payout: $1,500 (critical vulnerabilities only)
Program Managed By: Bugcrowd
Sophos began offering monetary rewards in December for critical submissions on Cyberoam, a network security appliances provider purchased by Sophos in February 2014. Non-critical submissions or reports on other targets are rewarded with kudos only.
Three-quarters of vulnerability submissions have been accepted or rejected by Sophos within three days, according to Bugcrowd. Sophos has rewarded 466 vulnerabilities as of early February, with an average bounty of $1,500 over the past three months.
The scope of the program is limited to technical security vulnerabilities in Sophos-owned websites, applications, products, and software. All testing is to be performed using self-provisioned credentials against legally-obtained Sophos products.

19. Avast
Headquarters: Prague, Czech Republic
Top Bounty: $10,000
Minimum Payout: $400
Program Managed By: Company
The Avast bug bounty program is designed to reward security researchers for finding issues in consumer Windows versions of the software. Only bugs in the latest shipping versions of these products will be considered, according to the company.
The following bugs will qualify for a reward: remote code execution; local privilege escalation; denial-of-service; and straightforward, clear bypasses that lead to direct infection without any additional user input. Each bug is judged independently by a panel of Avast experts, with remote execution bugs paying at least $6,000 to $10,000 or more.
A good bug report needs to contain sufficient information to reliably reproduce the bug on Avast's side. Researchers should include their exact environment, a detailed bug description, sample code, and a decent analysis, the company said.

18. Okta
Headquarters: San Francisco, Calif.
Top Bounty: $15,000
Minimum Payout: $50
Program Managed By: Bugcrowd
Okta said it believes that community researcher participation plays an integral role in protecting the company's customers and their data. The company said its security team will determine the nature and impact of bugs to identity the appropriate payouts.
The company offers $15,000 for a full remote code execution and $10,000 for a full privilege escalation from one Okta org to another Okta org. Conversely, forced browsing, insecure direct object references, URL jumping, business logic issues, and other security issues will receive a bounty of just $50.
Three-quarters of vulnerability submissions have been accepted or rejected by Okta within three days, according to Bugcrowd. Okta has rewarded 52 vulnerabilities as of early February, with an average bounty of $225 over the past three months.

17. Netgear
Headquarters: San Jose, Calif.
Top Bounty: $15,000
Minimum Payout: $150
Program Managed By: Bugcrowd
Netgear encourages and rewards contributions by developers and security researchers who help make the company's products more secure. The company's cyber security team, at their sole discretion, determines the nature and impact of the vulnerabilities to identify the appropriate payouts.
The company offers $15,000 for unauthorized access to Netgear customer cloud storage video files or live video feeds, as well as remote unauthorized access to administer another customer's device with default settings. A $10,000 reward is provided for remote unauthorized access to a single customer's live video feed or cloud storage video files, as well as remote access to the full Netgear customer database.
Three-quarters of vulnerability submissions have been accepted or rejected by Netgear within 29 days, according to Bugcrowd. Netgear has rewarded 331 vulnerabilities as of early February, with an average bounty of $1,618.94 over the past three months.

16. Qualcomm
Headquarters: San Diego, Calif.
Top Bounty: $15,000
Minimum Payout: $200
Program Managed By: HackerOne
Qualcomm's vulnerability rewards program is designed to expand collaboration with researchers who improve the security of Qualcomm Snapdragon processors, LTE modems and related technologies.
The company offers $15,000 for critical cellular modern vulnerabilities, $9,000 for critical trusted execution environment (TEE) vulnerabilities, $9,000 for critical bootloader vulnerabilities, and $8,000 for critical application processor software and other qualified component vulnerabilities.
Vulnerabilities affecting the Snapdragon chipset family are in the scope of this program, as well as privileged user space programs, bootloader, cellular modern, WLAN and Bluetooth firmware, Qualcomm secure execution environment on TrustZone, and Linux kernel code that is part of "Android for MSM."

15. Microsoft Cloud Bug Bounty
Headquarters: Redmond, Wash.
Top Bounty: $15,000
Minimum Payout: $500
Program Managed By: Company
Microsoft launched the first phase of its online services bug bounty program in September 2014, and expanded it in April and August 2015 to include various Azure and additional Office 365 properties. Bounties will be paid out at Microsoft's discretion based on the impact of the vulnerability.
Bounties will be paid for significant web application vulnerabilities found in eligible online serve domains, Microsoft said. In order for submissions to be processed as quickly as possible and ensure the highest payment for the type of vulnerability being reported, submissions could include concise repro steps that are easily understood.
Eligible submissions include: cross-site scripting; cross-site request forgery; unauthorized cross-tenant data tampering or access; insecure direct object references; injection vulnerabilities; authentication vulnerabilities; server-side code execution; privilege escalation; or significant security misconfiguration not caused by the user.

14. Microsoft .NET Core and ASP.NET Core Bug Bounty
Headquarters: Redmond, Wash.
Top Bounty: $15,000
Minimum Payout: $500
Program Managed By: Company
Microsoft launched this bounty program on Sept. 1, 2016, and invites researchers to submit vulnerabilities found on .NET Core and ASP.NET core running on Windows, Linux and MacOS.
The company offers up to $15,000 for remote code execution vulnerabilities with high-quality reports and functioning exploits. Up to $10,000 is provided for security design flaws or privilege elevations with high-quality reports and functioning exploits. Up to $6,000 is available for remote code execution vulnerabilities with high-quality reports but no functioning exploits.
Payment amounts are dependent on the quality and complexity of the vulnerability as determined by Microsoft. Users are asked to include complete and easily-understood instructions to reproduce the vulnerability.
13. Microsoft Office Insider Builds on Windows Bug Bounty
Headquarters: Redmond, Wash.
Top Bounty: $15,000
Minimum Payout: $500
Program Managed By: Company
Individuals across the globe can receive monetary rewards for submitting security vulnerabilities found in Microsoft Office Insider slow build shipping on the latest, fully patched version of Windows.
The company offers up to $15,000 for high-quality reports on elevation of privilege via Office Protected View sandbox escape. High-quality reports on Macro execution by bypassing security policies to block Office macros in Word, Excel, and PowerPoint can also receive rewards of up to $15,000.
The vulnerability must reproduce on the most recent Office Insider to qualify for a bounty, Microsoft said. Researchers must also include concise reproducibility steps that are easily understood so that submissions can be processed as quickly as possible.

12. Microsoft Edge Web Platform on Windows Insider Preview Bug Bounty
Headquarters: Redmond, Wash.
Top Bounty: $15,000
Minimum Payout: $500
Program Managed By: Company
Microsoft launched this program on Aug. 4, 2016, allowing individuals to submit vulnerabilities found in Microsoft Edge shipping on the latest Windows 10 Insider Preview slow ring.
The company offers up to $15,000 for remote code execution vulnerabilities with high quality submissions, up to $6,000 for violation of same origin policy with high quality submissions, and up to $5,000 for information disclosure with high quality submissions. Remote code execution vulnerabilities with low quality submissions can also receive up to $5,000.
Eligible submissions must identify an original and previously unreported vulnerability in the current Microsoft Edge on WIP slow, Microsoft said. They must also include concise reproducibility steps that are easily understood so that submissions can be processed as quickly as possible.
11. Microsoft Windows Insider Preview Bug Bounty
Headquarters: Redmond, Wash.
Top Bounty: $15,000
Minimum Payout: $500
Program Managed By: Company
Microsoft launched this program on July 26, 2017, allowing individuals to submit vulnerabilities that reproduce in the latest Windows Insider Preview fast ring.
The company offers up to $15,000 for remote code execution vulnerabilities with high quality reports, and up to $10,000 for elevation of privilege with high quality reports. Remote code execution vulnerabilities without high quality reports are eligible for up to $7,500, Microsoft said.
Vulnerability submissions must identify an original and previously unreported critical or important vulnerability that reproduces in WIP fast to be eligible for a reward. Researchers should include the impact of the vulnerability, the attack vector, and the build and revision string in the revision key, Microsoft said.

10. AT&T
Headquarters: Dallas, Texas
Top Bounty: $20,000
Minimum Payout: $250
Program Managed By: Company
The AT&T bug bounty program applies to security vulnerabilities found within the company's public-facing online environment such as websites, exposed APIs, mobile applications, and devices.
On a quarterly basis, AT&T will evaluate all valid bug submissions that have been remediated during that quarter and award bounties for those we consider to be the top 10 bugs. Only those bug reporters included in the top 10 will receive a bounty and top 10 Hall of Fame recognition.
The company's bug bounty program board members will, at their sole discretion, determine which bugs are considered as candidates for a reward, as well as the final reward recipients. These will typically be high impact bugs; however, any vulnerabilities that could realistically place the company's online security at risk is in scope and might be rewarded.

9. Google Patch Reward Program
Headquarters: Mountain View, Calif.
Top Bounty: $20,000
Minimum Payout: $500
Program Managed By: Company
Google announced a new, experimental program in October 2013 that rewards proactive security improvements to select open-source projects. Any patch that has a demonstrable, significant, and proactive impact on the security of one of Google's in-scope projects will be considered for a reward.
The company offers up to $20,000 for ideal integration with OSS-Fuzz, $10,000 for complicated, high-impact improvements that almost certainly prevent major vulnerabilities in the affected code, and $5,000 for moderately complex patches that offer compelling security benefits.
In order to qualify, researchers must first submit their patch directly to the maintainers of the project and have it accepted into the repository without reverts for one month. Researchers should be sure to explain the project-specific benefits of the patch, Google said.

8. Microsoft Windows Defender Application Guard Bug Bounty
Headquarters: Redmond, Wash.
Top Bounty: $30,000
Minimum Payout: $500
Program Managed By: Company
Microsoft announced a new program in July 2017 that rewards researchers for submitting vulnerabilities in Windows Defender Application Guard found in the latest Windows 10 Insider Preview slow ring.
Vulnerabilities resulting in escape from the Windows Defender Application Guard container to the host with a functioning exploit and high-quality report will receive a $30,000 payout, while similar vulnerabilities without a functioning exploit will receive a payout of $20,000.
An eligible submission also includes a remote code execution vulnerability in Application Guard that enables a guest in the Windows Defender Application Guard container to compromise the hypervisor, escape from or to the host, or escape from one container to another container.
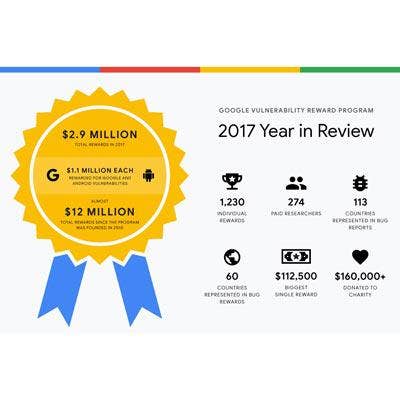
7. Google Vulnerability Reward Program
Headquarters: Mountain View, Calif.
Top Bounty: $31,337
Minimum Payout: $100
Program Managed By: Company
The company has maintained a vulnerability reward program for Google-owned web properties such as Google, YouTube and Blogger since November 2010. Bugs in Google-developed apps and extensions, as well as some of the company's hardware devices like OnHub and Next will also qualify for the program, the company said.
Remote code execution vulnerabilities that give direct access to Google servers for normal Google applications, other highly-sensitive applications, or applications that permit taking over a Google account receive a $31,337 bounty, while unrestricted file system or database access in the same situations yields a $13,337 award.
Any design or implementation issue that substantially affects the confidentiality or integrity of user data is likely to be in the scope of the program, Google said. Common examples include: cross-site scripting; cross-site request forgery; mixed-content scripts; authentication or authorization flaws; or server-side code execution bugs.

6. Google Chrome Reward Program
Headquarters: Mountain View, Calif.
Top Bounty: $100,000
Minimum Payout: $500
Program Managed By: Company
The Chrome Reward Program was launched in January 2010 to help reward the contributions of security researchers who invest their time and effort in helping Google make Chrome and Chrome OS more secure.
The company offers a $100,000 reward for participants that can compromise a Chromebook or Chromebox using guest-to-guest persistence with interim reboot delivered as a webpage. A sandbox escape with both a functioning exploit and high-quality report will receive $15,000, while a sandbox escape with a high-quality report will earn $10,000.
Google typically focuses on critical, high and medium-impact bugs, but the company said any clever vulnerability at any severity might get a reward. The company said it also loves to learn about bugs in third-party components it ships or uses such as PDFium, Adobe Flash, or Linux kernel.
5. Google Android Reward Program
Headquarters: Mountain View, Calif.
Top Bounty: $200,000
Minimum Payout: $200
Program Managed By: Company
This program covers security vulnerabilities discovered in the latest available Android versions of Pixel phones and tablets, including the Pixel 2, Pixel and Pixel XL, and the Pixel C. Eligible bugs include those in AOSP code, OEM code (libraries and drivers), the kernel, and the TrustZone OS and modules.
Critical vulnerabilities that include an exploit leading to TEE compromise will receive a $200,000 reward, while critical vulnerabilities that include an exploit leading to Kernel compromise will earn a $150,000 bounty. Meanwhile, high-level vulnerabilities that could lead to TEE compromise will receive a $100,000 reward, while high-level vulnerabilities that could lead to Kernel compromise will get a $75,000 bounty.
Vulnerabilities in other non-Android code, such as the code that runs in chipset firmware, may be eligible if they impact the security of the Android OS.
4. Samsung
Headquarters: Seoul, South Korea
Top Bounty: $200,000
Minimum Payout: $200
Program Managed By: Company
As an appreciation for helping Samsung Mobile improve the security of its products and minimize risk to end customers, the company is offering a rewards program for eligible security vulnerability reports.
Higher reward amounts will be offered for vulnerabilities with greater security risk and impact, and even higher reward amounts will be offered for vulnerabilities that lead to TEE or Bootloader compromise. On the other hand, Samsung said reward amounts may be significantly reduced if the security vulnerability requires running as a privileged process.
The following Samsung Mobile Devices in their latest available Android version are eligible: Galaxy S series; Galaxy Note series; Galaxy A series; Galaxy J series; and the Galaxy Tab series. Vulnerabilities on 3rd-party applications must be specific to Samsung Mobile devices, applications or services, the company said.

3. Microsoft Mitigation Bypass And Bounty For Defense
Headquarters: Redmond, Wash.
Top Bounty: $200,000
Minimum Payout: $500
Program Managed By: Company
Individuals have had the opportunity to submit a novel mitigation bypass against Microsoft's latest Windows program since June 2013, and are also invited to submit a defense idea that would block an exploitation technique that currently bypasses the latest platform mitigations.
A novel and fundamental advancement in exploitation technology that universally bypasses current mitigations with a high-quality report will receive up to $100,000, while the same advancement with a low-quality report will receive up to $50,000. Qualified defensive techniques are also eligible for a bounty of up to $100,000, Microsoft said.
Eligible bypass submissions include novel methods of exploiting real remote code execution vulnerabilities, as well as novel methods of bypassing mitigations imposed by a user mode sandbox. A novel exploitation method must be an integral and required component of enabling reliable remote code execution, Microsoft said.

2. Intel
Headquarters: Santa Clara, Calif.
Top Bounty: $250,000
Minimum Payout: $500
Program Managed By: Company
Six weeks after Meltdown and Spectre came to light, Intel said it was raising its bounty awards across the board and launching a new, limited-time program focused specifically on side-channel vulnerabilities. The side-channel program will run until Dec. 31 and offer awards of up to $250,000 for critical issues.
In addition, the top reward in the regular bug bounty program (for critical hardware flaws) was increased from $30,000 to $100,000. Maximum awards for identifying firmware or hardware vulnerabilities in the regular program—regardless of the bug’s severity—have at least doubled, and often tripled.
“We believe these changes will enable us to more broadly engage the security research community, and provide better incentives for coordinated response and disclosure that help protect our customers and their data,” Rick Echevarria, Intel’s vice president and general manager of platform security, said in a Feb. 14 blog post.

1. Microsoft Hyper-V Bounty Program
Headquarters: Redmond, Wash.
Top Bounty: $250,000
Minimum Payout: $5,000
Program Managed By: Company
Microsoft broadened the scope of this program in May 2017, and it now pays a bounty on remote code execution, information disclosure, and denial of service vulnerabilities.
Remote code execution vulnerabilities on a hypervisor or host kernel with functioning exploits will receive a $250,000 bounty, while those without a functioning exploit will receive a $200,000 bounty. Remote code execution vulnerabilities on a virtual machine worker process with functioning exploits will receive a $150,000 bounty, while those without a functioning exploit will receive a $100,000 bounty.
Eligible submissions should enable the guest virtual machine to compromise the hypervisor, escape from a guest virtual machine to the host, or escape from one guest virtual machine or another guest virtual machine.