20 Hot New Security Products Announced At RSA 2018

The Latest And Greatest In Security
Vendors are taking advantage of the 2018 RSA Conference's bright spotlight to launch new offerings, features and platforms that will set the stage for the year to come. For the more than 550 exhibitors typically found at RSA, the massive gathering provides a chance to explore new strategic directions and evangelize new products to an audience of more than 43,000.
Some of the more common areas for product innovation this year include identity management and data protection, endpoint security, and web, application and email security.
CRN broke down the two most popular areas for new product development -- cloud security and security orchestration, threat detection and incident response – into their own stand-alone slide shows.
From protection against Meltdown and Spectre to dynamic data protection to thwarting email impersonation, here's a look at 20 key security offerings announced at the RSA Conference this year.
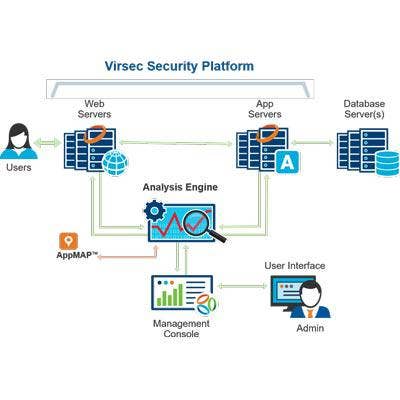
Virsec Trusted Execution
Virsec Trusted Execution protects applications against microcode attacks such as Spectre and Meltdown without requiring changes to the application code, operating system patches or microcode updates.
Unlike recently released patches that effectively turn off speculative execution, Virsec Trusted Execution does not incur significant performance degradation. It also does not require recompiling of application source code, which can be impractical for organizations with complex software stacks.
Virsec Trusted Execution detects vulnerable code and proactively puts fences in place to prevent side-channel exposure caused by speculative execution. Unlike other products that use static analysis to find vulnerable code and then require rewrites, Virsec detects and protects code as is in real-time. Because this is done selectively, it has negligible impact on overall performance.
Trend Micro Writing Style DNA
Trend Micro Writing Style DNA will sound the alarm when emails are suspected of impersonating an executive or other high-profile user as part of a Business Email Compromise (BEC) attack.
The product uses artificial intelligence to "blueprint’ a user’s style of writing, employing more than 7,000 writing characteristics. When an email is suspected of impersonating a high-profile user, the style is compared to this trained AI model and a warning is sent to the implied sender, the recipient and the IT department.
Writing Style DNA provides authorship analysis to spot attackers who hijack legitimate domains and accounts to circumvent traditional filters. Executives can provide feedback on the flagged emails to improve detection and reduce false positives.

Forcepoint Dynamic Data Protection
Forcepoint Dynamic Data Protection continuously assesses risk and automatically provides proportional enforcement that can be dialed up or down. This capability is enabled through human-centric behavior analytics that understand interactions with data across users, machines and accounts.
The product applies an anonymous and continuously updated behavioral risk score to establish a baseline of ’normal’ behavior of each end user on corporate or unmanaged networks. The company's intelligent systems, informed by the individual risk assessment, then apply a range of security countermeasures to address the identified risk.
With the industry’s first automated enforcement capability that dynamically adapts, Forcepoint Dynamic Data Protection frees up security analysts to focus on higher-value activities.

Unisys Stealth
The new version of Unisys Stealth includes upgrades to extend protection to purpose-built Internet of Things devices and other connected equipment such as medical monitoring machines, baggage scanners and surveillance cameras.
The new release of Stealth micro-segmentation software includes support for IoT devices, isolating them from untrusted network segments within a Stealth-protected network. This helps prevent intrusion and remote tampering on the devices and protects the corporate network from potential compromises initiated from unsecured devices.
By joining Stealth, high-value devices are shielded from unauthorized access, reducing the attack surface. This new capability can be delivered as a virtual or physical gateway to protect devices where Stealth cannot be installed, requiring no hardware or software changes.

Tripwire Container Analyzer Service
The Tripwire Container Analyzer Service embeds security at the beginning of the DevOps process. As a result, the service can be used to perform complete vulnerability analysis of Docker images, systematically approving images or preventing further use of them.
The Container Analyzer Service combines with continuous integration and continuous deployment tools to perform vulnerability scanning at each layer of the Docker image. Images are built earlier in the DevOps process and form the basis for building a container.
This new capability builds upon Tripwire's existing capabilities for scanning online, offline and non-running Docker containers later in the DevOps life cycle. Scanning for vulnerabilities throughout the life cycle is important as change happens frequently and rapidly throughout the DevOps process.

SonicWall NSv Virtual Firewall
SonicWall Network Security virtual (NS v) firewalls protect all critical components of private and public cloud environments, delivering the security advantages of a physical firewall with the operational and economic benefits of virtualization around speed, cost, simplicity and scalability.
The new virtual firewalls help organizations gain more visibility into intra-host communication between virtual machines; ensure appropriate placement of application security policies; implement proper security zoning and isolation; prevent unauthorized takeover of virtual systems; stop unauthorized access to protected data; and block malicious and intrusive actions.
The new SonicWall Web Application Firewall (WAF), meanwhile, delivers defense-in-depth capabilities to protect web applications running in private, public or hybrid cloud environments. It features advanced web security tools and services to keep compliance data unexposed and web properties safe, undisrupted and in peak performance.

Centrify Next-Gen Access
Centrify Next-Gen Access will make it possible for customers to reduce their exposure to common security threats in their application development pipelines without compromising security, velocity or scalability.
The offering makes it possible for customers to scale adoption of secure DevOps by simplifying the integration of security into application development pipelines. Centrify's Zero Trust approach presumes that users, applications and endpoints are not trustworthy and must be verified at every point of access so that security of the development pipeline is not compromised.
Centrify’s platform now enables containerized applications to securely access other network resources by leveraging SAML or OAuth, providing granular access controls to containers independent of the access to container hosts.
CylanceOptics
CylanceOptics takes machine learning for security to the next level, delivering zero-latency, AI-driven threat detection and response for the endpoint.
The offering brings automated incident prevention to the Security Operations Center by incorporating AI-based incident prevention targeting fileless attacks, malicious one-liners, and suspicious application behavior. CylanceOptics also uses AI to continuously analyze changes occurring on each endpoint to uncover threats that would be difficult for a human analyst to find in a reasonable amount of time.
CylanceOptics enables near-zero-latency threat detection and response by storing and analyzing data locally on the endpoint. This approach means organizations can adopt EDR and speed incident response without adding infrastructure costs.
Kenna Application Risk Module
The Kenna Application Risk Module applies data science at scale to enable security and development teams to continuously, effectively and proactively manage risk across their entire application portfolio.
It leverages the underlying Kenna Security Platform to process and normalize all application security data, including static and dynamic scanners, penetration test results, bug bounty data, and open-source scanners, giving enterprises a true measurement of cyber risk.
The Kenna Application Risk Module provides clear metrics, real-world context and prescriptive remediation guidance for enterprise applications. It also aligns security teams, DevOps and developers to efficiently fix the most critical application vulnerabilities without slowing the pace of development.
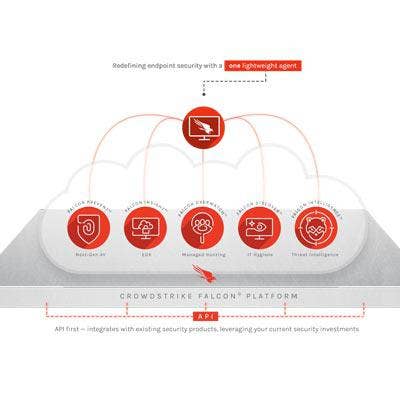
CrowdStrike Falcon Endpoint Protection Complete
CrowdStrike Falcon Endpoint Protection Complete integrates prevention, detection and response technology with IT hygiene capabilities to protect against the rapidly changing tactics, techniques and procedures used by adversaries to compromise organizations.
The company also rolled out a new Falcon Insight Remote Response feature, empowering incident responders with deep access to systems across the enterprise. Falcon’s response capabilities allow customers to contain compromised systems, investigate fully, eradicate threats with precision, and get back to business quickly.
This new feature adds unparalleled ability to respond quickly and decisively, thereby minimizing the costs associated with advanced cyberattacks.

SonicWall Capture Client
The new SonicWall Capture Client extends an organization’s ability to defend endpoint devices that connect and interact with its networks, applications and data. The offering extends advanced malware protection to endpoint devices, enables continuous behavioral monitoring, uses machine learning for highly accurate determinations, and simplifies management via a cloud-based console.
The platform delivers multiple endpoint protection capabilities, including next-generation malware protection and support for visibility into encrypted traffic. It leverages layered protection technologies, comprehensive reporting and enforcement for endpoint protection.
SonicWall Capture Client also significantly simplifies the deployment of certificates on endpoints by installing and helping manage trusted TLS certificates on all endpoints behind a firewall.

Cyxtera AppGate SDP 4.0
Cyxtera AppGate SDP 4.0 implements the zero-trust principles of a software-defined perimeter as a full network platform to provide a unified, enterprise-grade offering.
The latest version of AppGate offers Ringfence to isolate end-user devices and protect them from unauthorized access to critical resources, as well as server-to-server protection to eliminate lateral movement as an attack vector and prevent zero-day attacks.
AppGate 4.0's updated live entitlements engine provides powerful and dynamic access controls by improving access criteria capabilities and API-driven integrations in enterprise systems. This makes it possible for the product to respond in real time to changing conditions.
The offering's enhanced user experience, meanwhile, simplifies implementation, workflows, and policy management.

Qualys CertView
Qualys CertView helps customers inventory and assess certificates, underlying SSL/TLS configurations and vulnerabilities across external-facing assets to prevent downtime and outages. The product also mitigates the risks associated with expired or vulnerable SSL/TLS certificates and configurations.
CertView's certificate discovery enables companies to continuously scan global IT assets from the same console to discover every internet-facing certificate issued from any certificate authority.
Certificate inventory, meanwhile, enables reduced administrative costs by bringing the entire certificate estate under central control. This provides comprehensive visibility of all external certificates in use across the DevSecOps, InfoSec and IT teams.
CertView also generates certificate instance grades (A, B, C, D, etc.) without requiring users to become SSL experts. It uses SSL Labs’ methodology, which allows administrators to assess often-overlooked server SSL/TLS configurations.
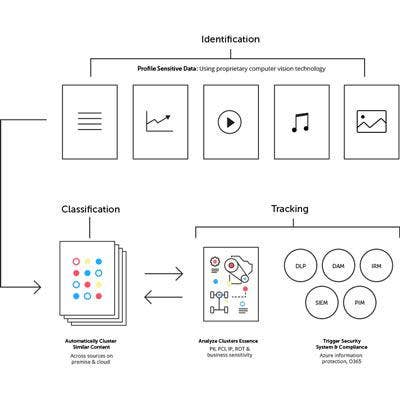
MinerEye Data Tracker
MinerEye Data Tracker will enable companies to identify, organize, track and protect vast information assets for safe and compliant cloud migration, including undermanaged, unstructured and dark data.
The product helps companies consolidate internal file server data into OneDrive as part of Office 365 and Azure adoption. As a result, customers can swiftly identify, classify, track and downsize the on-premise data before and after it moves to the cloud.
MinerEye Data Tracker classifies and mediates the movement of current and legacy data while continually monitoring both cloud and on-premise repositories. The product can also detect and understand unusual data behavior, flagging activities that could present risk such as suspicious or irregular movement, deletion or modification of specific data.
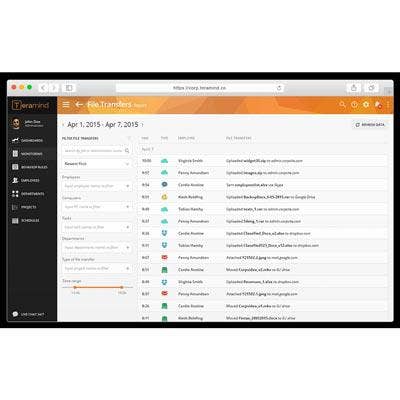
Teramind Data Loss Prevention
Teramind rolled out a comprehensive platform that combines behavioral data analytics with technology supporting traditional data loss prevention (DLP) to bringing forth the next generation of forensic insight.
The company's software streamlines employee data collection to identify suspicious activity, detect possible threats, monitor employee efficiency and ensure industry compliance.
Teramind’s new file anti-exfiltration analysis combined with the software’s traditional DLP software capabilities and behavioral data analytics brings forth a stronger layer of protection against data breaches. File anti-exfiltration analysis targets and tags sensitive file repositories and sensitive content.
Teramind said its new approach should help organizations from health care to banking, legal, energy and customer service address their internal cybersecurity and data breach vulnerabilities.

Varonis Edge
Varonis Edge analyzes perimeter devices including DNS, VPN and Web Proxy to detect attacks like malware, APT intrusion, and data exfiltration. The product enables enterprises to correlate events and alerts to track potential data leaks and spot vulnerabilities at the point of entry.
The product increases the number of ways Varonis can detect cyberattacks and adds valuable context about what’s happening within core data stores. Varonis Edge provides detailed insight for investigation and analysis, allowing companies to better defend their data.
The company can also automatically identify and classify data that falls under the upcoming European Union General Data Protection Regulation with over 280 patterns in GDPR Patterns. Customers can identify regulated data, while GDPR-focused threat models flag unusual activity around this data.
AlienVault Threat Scanning Service
AlienVault's new, free threat scanning service will make it possible for organizations to identify and gather information in real time on malware, ransomware and other threats.
The service scans all endpoints for indicators of compromise and notifies organizations of any active threats, as well as if any of their endpoints have been compromised in cyberattacks.
The threat scanning service is able to provide unprecedented threat detection since it references the 19 million indicators of compromise shared daily in AlienVault's Open Threat Exchange, which is the world's largest threat intelligence community with 80,000 participants.

Zimperium zANTI 3.0
Zimperium zANTI 3.0 includes advanced capabilities that enable penetration testers to scan, list and identify properties of all connected devices on the network. Some of the properties that can be identified by zANTI 3.0 include: name; IP/MAC address; OS version; vulnerabilities; and open ports.
The product can also commit man-in-the-middle attacks, taking on an entire network in less than a minute. As a result, the company said zANTI 3.0 sees what data can be captured, emulates phishing redirects and exploit delivery, and determines if devices can identify the attacks.
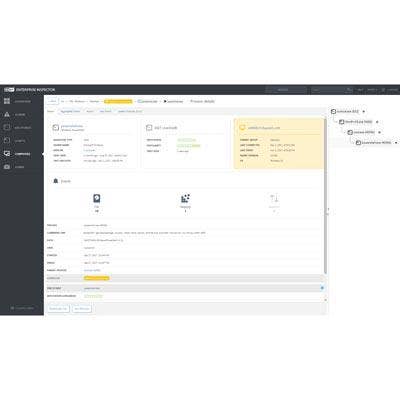
Eset Enterprise Inspector
The all-new Eset Enterprise Inspector is an endpoint detection and response (EDR) offering with features and granularity that surpass anything on the market.
All of Eset’s enterprise solutions integrate seamlessly into a single pane of glass and allow for visibility into threats like zero days, APTs and botnets. They also make adjustments to policies and configurations of endpoint security products seamless and easy.
Eset’s enterprise solutions are built by cybersecurity experts and backed by machine learning. The use of machine learning to automate decisions and evaluate possible threats is a vital part of Eset’s approach.

Supermicro Intelligent Network Edge
Supermicro is introducing a full line of offerings that support the latest Intel Xeon D-2100 processors with up to 1.6X compute performance improvement compared to the last generation.
The company's X11SDV platforms deliver balanced compute, storage and networking for the intelligent edge. These advanced technology building blocks offer the best workload optimized offerings and long-life availability with up to 18 processor cores.
Supermicro platforms also support Intel QuickAssist Technology, providing cryptography engines for faster encryption and decryption of messages or information for authorized and intended use.
Meanwhile, Supermicro's new SYS-E300-9D is a compact box-embedded system that is well-suited for applications such as network security appliances.