RSA 2018: 10 Hot New Security Orchestration, Threat Detection, And Incident Response Products

Taking Threats Seriously
Vendors attending the 2018 RSA Conference have doubled down on a threat-based approach to security, investing in everything from detection and response to simulations and intelligence.
Security companies have committed to improving their centralized management platform through a combination of automation, orchestration, artificial intelligence, and machine learning. Analytics plays a key role as well, with suppliers and partners working in tandem to help end customers make sense of all their data.
Here's a look at what 10 key vendors are doing to better understand how threats work and how organizations can most effectively respond to them.
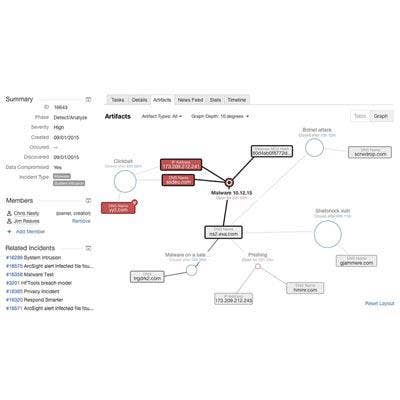
IBM Security Resilient Incident Response Platform
IBM Security's Resilient Incident Response Platform dramatically accelerates and sharpens incident response by combining incident case management, orchestration, automation, intelligence, and deep two-way partner integrations into a single platform.
Resilient allows security analysts to orchestrate and automate hundreds of time-consuming, repetitive and complicated response actions that previously required significant human intervention across their Security Operations Center tools. The new platform provides also analysts with integrations out of the box and a new drag-and-drop business process management workflow engine.
The new platform makes it possible for analysts to move and reuse integrations without needing to understand the technical or implementation background. As a result, organizations can improve the speed and agility of their response process and achieve rapid time to value on their security investments.

Symantec Targeted Attack Analytics
Symantec is for the first time granting customers access to the threat detection technology used by its internal research team, making it easier to discover targeted attacks.
The company said Targeted Attack Analytics can look at all the machines in a single enterprise and collate the telemetry with the endpoints to verify if there's an active attack taking place inside the network. The company said the technology can detect more advanced attacks that get by traditional security offerings.
In addition to looking holistically across all devices to build a more concrete picture of what's going on, Symantec said Targeted Attack Analytics can alert users to incidents with absolute certainty, rather than simply indicating that there's the likelihood or a probability that something's taking place.
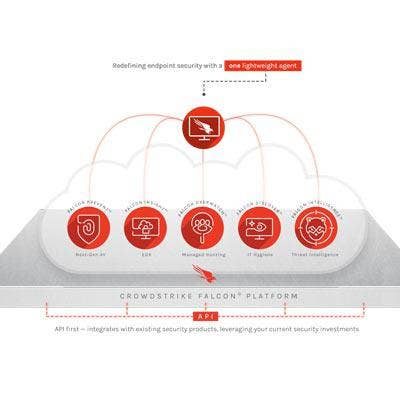
CrowdStrike Falcon X
CrowdStrike Falcon X automates threat analysis, delivering customized intelligence and Security Operations Center automation to large and small organizations.
Falcon X brings endpoint protection to the next level by combining malware sandboxing, malware search and threat intelligence into an integrated offering that can perform comprehensive threat analysis in seconds instead of hours or days. The product produces indicators of compromise for the threat that was actually encountered in the organization as well as all of its known variants.
Falcon X immediately shares indicators of compromise with other security tools like firewalls, gateways and security orchestration tools via APIs. The product also provides integrated threat intelligence alongside its security alerts to accelerate incident research, streamline the investigative process, and drive better security responses.
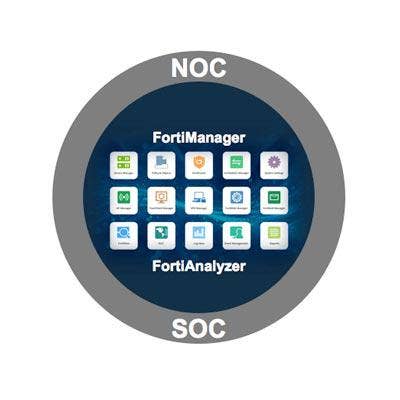
Fortinet NOC-SOC
Fortinet unveiled a purpose-built Network Operations Center-Security Operations Center offering that bridges workflows, analysis and automated response across operational and security processes. This approach to management enables enhanced security operations visibility with a new graphical topology view and extensions into both private and public cloud environments.
Fortinet’s centralized security management now natively manages FortiAnalyzer, incorporating all data, analysis, control and perspective in a single-pane-of-glass view of NOC and SOC operations. Having a NOC-SOC consolidated view of operations and security unlocks automation and enables security teams to act more quickly and efficiently, Fortinet said.
Fortinet's Security Rating feature, meanwhile, continuously evaluates a multitude of elements to quantify the implementation of security best practices with suggestions on ways to improve operations across the NOC and SOC.

FireMon Global Policy Controller
FireMon Global Policy Controller is a single-console offering that allows for policy definition, oversight and orchestration of global security infrastructure. The offering delivers efficient, compliant security configurations in seconds, visibility and management of network posture, and continuous security control for traditional and virtual platforms.
The product enables application owners and line-of-business leaders to directly define and manage their intent for access while also allowing security teams to enforce templates that govern the access that gets created. The operating model supports the transition to cloud-native and container-first environments with consistent automation and DevOps practices.
FireMon Global Policy Controller eliminates deviations from policy compliance through its Policy Compute Engine, which provides dynamic policy change, embedded security, intent translation and automated distribution.
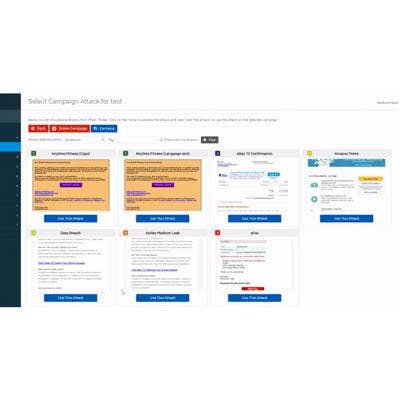
Sophos Phish Threat
Sophos has expanded its phishing attack simulator and training offering into Europe and Asia. Phish Threat simplifies employee awareness and training with enhanced dashboards and new analytics to track organizational risk and employee performance.
With the ability to choose from hosting locations in Ireland, Germany or the U.S., global organizations can now access multi-language, interactive security training from within the Sophos Central management platform.
Phish Threat automates the entire training process and provides visual analytics to identify vulnerable employees, according to Sophos. It can be managed alongside email, endpoint and network security from one console for improved risk management and incident response.
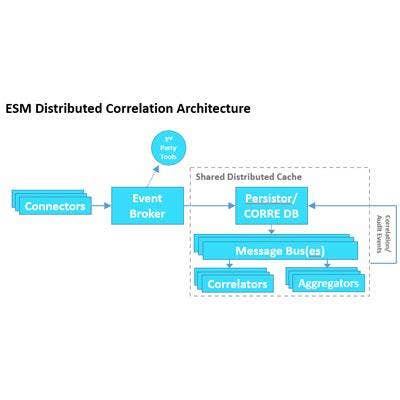
Micro Focus ArcSight ESM 7.0
ArcSight Enterprise Security Manager (ESM) 7.0 prioritizes security threats and compliance violations with real-time threat intelligence to quickly identify and impede potential cyberattacks. The product can help organizations meet demanding security requirements by collecting, correlating and reporting security event information at a massive scale.
By using distributed correlation, Micro Focus said it can offer a new way to scale SIEM analytics and event correlation without the need to incur excess costs. This makes it possible for customers to focus on providing security insight and scaling their business.
With ArcSight ESM 7.0 and its newly introduced distributed correlation, customers will find more contextual event analysis; improvements to ESM availability and redundancy; better cost and performance flexibility; and the ability to get more value from existing security tools and events.
Infocyte Hunt 3.0
Infocyte Hunt 3.0 addresses the threats and vulnerabilities across all assets, both in the cloud and on premises for enterprises and small to midsize organizations. The product leverages advances in threat hunting capabilities utilized by the U.S. military and top cybersecurity providers.
Infocyte Hunt is an automated platform that reduces the skill set requirement for hunting malware and advanced persistent threats (APTs). It significantly reduces the period between infection and discovery to deny bad actors the ability to persist undetected.
Infocyte's malware and threat hunting expertise can now be purchased as a subscription service. Subscribers will additionally receive a monthly report and scoring to indicate an organization's relative risk and security posture states.

ThreatQuotient ThreatQ Investigations
ThreatQ Investigations accelerates security operations through threat understanding, collaborative analysis and coordinated response. The product allows for real-time visualization of an investigation as it unfolds within a shared environment, enabling teams to better anticipate threats.
ThreatQ Investigations provides a single visual representation of the complete situation, including what actions were taken, by whom and when. The product also gives individuals the freedom to test theories prior to sharing them with the entire group.
Those in technical roles performing analysis as well as the decision-makers relying on the outcomes, will benefit from ThreatQ Investigations. Incident handlers, malware researchers, SOC analysts and investigation leads will all gain more control, be able to take the right steps at the right time, and accelerate overall security operations.

Easy Solutions Digital Threat Protection
The Easy Solutions Digital Threat Protection suite now offers intelligence-based context on the victim and insight into compromised credentials. This makes it possible for financial institutions to have more visibility of the internet threats targeting their organizations, arming them with actionable data that will strengthen their plan of action for each subsequent attack.
The new victim insight feature means that organizations can determine the number of end users who visited the dangerous site, clicked on the malicious URL, and disclosed personal information and credentials.
The detect monitoring service, meanwhile, combines machine-learning algorithms with the power of computer vision to disrupt and deter attacks. Features include rogue mobile application protection; extensive coverage; and built-in client data sources integration.