20 Hot Cybersecurity Products Announced At Black Hat 2018

What's Next In Security?
Vendors are taking advantage of Black Hat 2018's bright spotlight to launch new cybersecurity products, features and platforms that will set the stage for the year to come. For the more than 300 exhibitors expected at Black Hat, the massive gathering provides a chance to explore new strategic directions and evangelize new products to an audience of more than 17,000.
Some of the more common areas for product innovation this year include security operations and incident response, identity and access management, web security, and application security.
CRN broke down the most popular area for new product development – network and endpoint security – into its own stand-alone slideshow. Several vendors have also debuted new cybersecurity partnerships at Black Hat, which are explored in another slideshow.
From securing large print fleets to using artificial intelligence to assess suspicious emails in real time to deploying deception to derail attacks targeting nontraditional surfaces, here's a look at 20 hot cybersecurity products announced at Black Hat 2018.
Ironscales Themis
Ironscales Themis is an artificial intelligence-assisted virtual security analyst built to automatically determine a verdict on suspicious email incidents in real time. Themis is designed to add another layer of email security protection for companies under siege from modern phishing attacks such as ransomware and business email compromise.
By mimicking a security analyst's decision-making criteria, Themis can predict with high confidence the legitimacy of any suspicious email, improving the efficiency of email phishing classification and expediting the resolution of confirmed phishing threats. And when a new incident is not automatically resolved, Themis immediately logs the attack details and checks it against previous verdicts.
Specifically, the product reduces risk by resolving unknown phishing threats faster, and keeps real human intervention to a minimum.

Unisys TrustCheck
Unisys TrustCheck draws on the strength of the analytics model used in the cyber insurance industry to quickly and easily assess the potential financial impact of cyber risks. TrustCheck is delivered as a managed service on an annual subscription basis, giving security professionals constantly updated information about an organization's cybersecurity posture and recommended steps for remediation.
TrustCheck enables organizations to assess cyber-risk posture in economic terms, augment traditional gap assessment data with analysis of threats and controls from a client's existing security products, determine the likelihood of a cyber-related financial loss, and easily communicate risk-reduction initiatives to the board.
Through the TrustCheck service, clients have ongoing access to risk dashboards to review their cybersecurity stance. In addition, Unisys reviews the dashboards with clients on a monthly basis to discuss how to adapt to new threats and shifting positions.

Attivo ThreatDefend
Attivo Networks enhanced its portfolio with new deception techniques designed to derail attacks targeting nontraditional surfaces. In addition to Internet of Things and operational technology, attackers are now targeting devices and applications that can be harder to secure as organizations look for the weak link in an organization's network.
Network devices have their own sets of vulnerabilities, and attackers target these systems because organizations don't often replace them once installed. With network device decoys from Attivo, organizations now have a way to alert when attackers target their network communications infrastructure.
Meanwhile, adding native support for additional specialized services and applications such as camera streaming server, Docker apps, big data, retail web portal and printers gives organizations decoy capabilities that alert when attackers attempt to compromise them. Adding these capabilities increases the breadth and depth of Attivo's deception capabilities, according to the company.

Proofpoint Targeted Attack Protection Isolation
Proofpoint Targeted Attack Protection Isolation separates web content to provide corporate users with safe and anonymous access to web and internet browsing while protecting the endpoint and the corporate network. These capabilities meet GDPR requirements by enabling employers to establish a filtered, proxied, anonymous, and secure internet service for personal webmail and browsing use.
Personal email accounts are the second most popular threat vectors behind only corporate email accounts, Proofpoint said. For this reason, employee personal web use has historically introduced significant security, productivity, and privacy challenges to an organization's security posture.
In addition, new Targeted Attack Protection sandbox environments feature enhanced phishing detection capabilities that catch a wider variety of phishing attacks while speeding up scanning and response times.

Symphion Print Fleet Cyber-Security-as-a-Service
The Symphion Print Fleet Cyber-Security-as-a-Service is designed to easily and cost-effectively secure large print fleets.
Symphion's service manages the security configuration of every printer in a large fleet – regardless of its make or model – and monitors hourly that each printer is configured correctly. In the event of an incorrect configuration, changes are adapted to and the security settings are automatically remediated to their planned, controlled state.
Symphion Print Fleet Cyber-Security-as-a-Service resolves the complexities inherent in any large print fleet by automating device inventory, printer security configuration management, and compliance reporting. At the same time, Symphion professionals work remotely to implement and administer the products, delivering ongoing support including responding to changes and service requests.
CrowdStrike Falcon X Premium
CrowdStrike Falcon X Premium broadens the scope of the company's endpoint protection offering by adding reports with global Indicators of Compromise (IoCs), intelligence support and custom malware analysis.
Falcon X Premium makes it possible for cybersecurity teams to automatically analyze malware found on endpoints, find related samples from a malware search engine, and enrich the results with CrowdStrike's cyber-threat intelligence. The closed-loop system provides customers with IoCs as well as intelligence reporting, resulting in a richer, more complete picture of an attack.
The product combines automated intelligence and human analysis to provide threat alerts, technical reports, customized malware analysis, intelligence orchestration, and a team of intelligence advisers. This makes it possible for security teams to learn from the attacks in their environment and apply that knowledge to proactively prevent future attacks, according to CrowdStrike.

Carbon Black Cb LiveOps
Cb LiveOps empowers organizations to ask questions of all endpoints, take action to remediate in real time and simplify operational reporting all from a single platform. The tool provides additional value in bridging the gap between security and operations, empowering security administrators to provide ROI well beyond the typical security analysis.
Cb LiveOps gives administrators visibility into even the most precise details about the current state of health on all endpoints, enabling them to make quick, confident decisions to reduce risk. From there, Cb LiveOps enables administrators to perform full investigations and remote remediations.
The tool makes it possible for organizations to consolidate a variety of security and operations capabilities into a single platform by combining advanced prevention, detection, response and operations with a single console and single agent.

Forcepoint Web Security Cloud Application Module
The Cloud App Module for Forcepoint Web Security eliminates security blind spots through real-time, inline visibility and control of all sanctioned and unsanctioned applications.
The module provides User and Entity Behavior Analytics (UEBA) and anomaly detection capabilities, critical for determining high risk and vulnerabilities within an organization. UEBA is also the underpinning for Forcepoint Dynamic Data Protection, which was introduced in April.
The new Cloud App Module goes beyond the shadow IT functionality already included in Forcepoint Web Security to deliver detailed risk assessment. Without purchasing a Cloud Access Security Broker (CASB), the tool makes it possible for customers to enjoy CASB-like functionality for up to 15 Cloud Apps.

Fidelis Managed Detection and Response
The Fidelis Managed Detection and Response (MDR) service provides a team of highly skilled security experts who analyze network and endpoint metadata, content, behavioral and asset characteristics and enterprise IoT devices to aid in hunting and investigations.
By analyzing rich metadata and content derived from Fidelis' inspection of network traffic, the MDR team can understand whether a document or executable has been seen before, what the file type is, who authored it, who received a copy, and who logged into the machine that sent the document.
This data-driven insight aids the Fidelis MDR team with a seamless incident response workflow, ensuring quick and accurate detection and response that removes false positives and produces only actionable intelligence. The Fidelis MDR service also incorporates deception technology, which enables the classification of assets and the deployment of breadcrumbs as lures to decoys.
Gemalto SafeNet Virtual KeySecure
Gemalto's SafeNet Virtual KeySecure integrates with leading cloud service providers and virtual platforms to provide companies with a single key management solution that spans multiple private or public cloud environments.
Data protection operations can be simplified by using SafeNet Virtual KeySecure to uniformly view, control, and administer cryptographic policies and keys for sensitive data. SafeNet Virtual KeySecure also supports key storage in a hardware security module, an appliance option deployed on-premises for enhanced security.
Centralized, efficient auditing of key management with Virtual KeySecure offers simplified compliance for cloud environments and consolidates key security policies across multiple, disparate encryption systems. And with Virtual KeySecure, customers can easily deploy flexible, high-availability configurations across geographically dispersed data centers or cloud service providers.
F5 Networks Access Manager
The F5 Access Manager protects sensitive data with a zero-trust model, provides access for authorized users, devices, and APIs, and guards against pervasive threats such as man-in-the-middle attacks. Product features make it possible for organizations to unlock operational efficiencies without compromising protections around apps, users and data, according to F5 Networks.
Context-sensitive policies with guided configuration from F5 deliver trusted access to users, devices and APIs for increased business efficiency, while real-time web-form encryption safeguards user credentials and prevents fraud.
The product also provides a centralized solution for access control, allowing DevOps teams to hand off apps to NetOps personnel more quickly. Access Manager also provides the necessary scale to bridge on-prem app functionality to the cloud, effectively integrating with IDaaS solutions and capabilities to support evolving heterogeneous environments.
Cofense Phishing SOAR
Cofense's Phishing SOAR platform combines the power of improved Cofense Triage with the new Cofense Vision product to improve the identify and disrupt active phishing attacks in progress and improve the effectiveness and efficiency of incident response efforts.
Cofense Triage leverages real-time, internally reporting attack intelligence from conditioned users to help assess, analyze, and remediate active phishing threats. Recent enhancements eliminate abuse mailbox noise and speed up the automation of responses with playbooks, making it possible for organizations to respond to threats faster while using fewer resources.
Cofense Vision, meanwhile, mitigates identified threats and potential impact by determining where else malicious emails are luring within an organization. This makes it possible for organizations to store, index and enrich email messages for fast querying and quarantining before any damage occurs.

Check Point SandBlast Mobile 3.0
SandBlast Mobile 3.0 has been enhanced with unique on-device technology to prevent malicious malware, botnets and phishing attacks on all mobile applications, according to Check Point.
The latest additions to SandBlast Mobile also prevent browsing to malicious sites where devices may become infected, block infected devices from sending sensitive data to botnets, keep infected devices from accessing corporate applications and data, and mitigate threats without relying on user action or mobile management platforms.
The SandBlast Mobile technology protects against threats to the OS, apps and network, according to Check Point, scoring the industry's highest threat catch rate without impacting performance or user experience.
OneLogin Protect 4.0 Authenticator
The OneLogin Protect 4.0 authenticator cuts down on organizational cost and management time by eliminating the need for multiple one-time password authenticators on iOS or Android mobile devices.
The token provides an enterprise-grade one-time passcode for both OneLogin and third-party cloud services, reducing the number of distinct authenticators that each user needs to manage on their devices and eliminating the need for multiple access vendors.
With Protect 4.0, users save time by receiving push notifications that they simply click to accept, rather than being required to manually enter a code for authentication. And by leveraging OneLogin's adaptive authentication capabilities in conjunction with Protect 4.0, users will be asked for multifactor authentication only when the risk is deemed to be high.
Mimecast Domain Name System Security Gateway
The Mimecast Domain Name System (DNS) Security Gateway cloud-based service guards against malicious activity initiated by user action or malware while blocking access to websites deemed unsafe or inappropriate based on each organization's objectives and policies.
Combining Mimecast DNS Security Gateway with the Mimecast Secure Email Gateway services enables organizations to implement an agile, easy-to-deploy offering that protects against the two most prevalent cyberattack vectors – email and web.
The DNS Security Gateway is intended to add an important security layer for web-based activity given that DNS requests make up a large portion of activity on the web. The new web security service is also supported by the Security Operations Center (SOC) team, as well as global threat intelligence and analytics that support Mimecast's email security services.

Fortinet Enterprise Services Bundle
The Fortinet Enterprise Services Bundle now includes protection for more than a thousand different protocols to help organizations with the difficult task of securing their IT/OT convergence efforts. New attacks targeting OT networks can not only have a devastating impact on an organization, but can also damage critical infrastructure and even result in direct harm to humans.
The enhanced enterprise bundle also includes FortiCASB, which helps establish and maintain policy and security governance across multi-cloud environments by enabling IT teams to maintain secure user access and centralized visibility across some of today's most widely used SaaS applications.
Fortinet's Security Rating Service is also an essential part of the enterprise bundle, guiding organizations in designing, implementing, and continually maintaining their targeted security postures and maturity levels. After identifying infrastructure vulnerabilities and weaknesses, it then provides best practices guidance to improve security posture.

Allure Security Data Loss Sensors
Allure Security has introduced an intelligent new user interface for deploying its Data Loss Sensors to enable faster deployments via automation and self-service. The new capabilities will also improve the relevance of geofencing and telemetry, making it easier to identify and respond to data loss alerts.
With the new enhancements, Allure Security customers will have the power to receive guidance on where to insert data loss sensors within the organization's file folder structure based on automated evaluation of where the most sensitive and easily accessible data lives.
The Data Loss Sensors can be quickly and easily deployed through an easy-to-use, intelligent interface that generates highly convincing file names to entice adversaries, according to Allure. Plus organizations can know in real time when sensitive corporate data has left the hands of a trusted third party and traveled outside a defined perimeter.
F5 Networks SSL Orchestrator
The F5 SSL Orchestrator provides policy-based orchestration capabilities for the full security service chain for any network topology, device or application, going well beyond mere SSL awareness and offload.
Orchestration on this level groups devices into services to intelligently decrypt and steer traffic, allowing for independent monitoring, load balancing and scaling to adapt to changing network conditions and increasing traffic demands. This marks a vast improvement over the industry's legacy model, where piecemeal inspection devices performed decryption independently, often resulting in gaps for attackers.
Dynamic service chaining and policy-based traffic steering in the SSL Orchestrator help organizations intelligently manage encrypted traffic flows across the entire app security infrastructure. High-performance decryption and encryption of inbound and outbound SSL/TLS traffic, meanwhile, enables quicker threat detection and attack remediation.
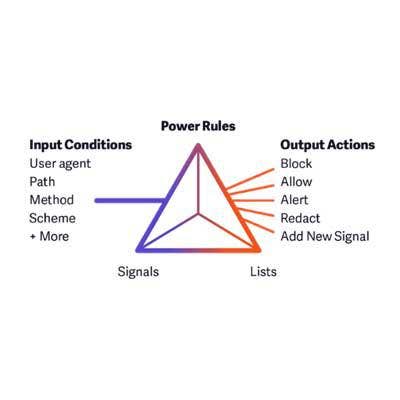
Signal Sciences Power Rules
Power Rules provides a flexible and easy-to-use platform for achieving business logic protection, negating the need for point security offerings around account takeover, fraud, bots and others.
With Power Rules, security and DevOps teams can start by defining signals using the intuitive user interface in the console to gain greater visibility. From there, they can trigger automated actions using those signals, and then augment agent detections with customer-sourced lists of IPs, user agents, and other useful sources.
The tool helps broaden the capabilities for enterprises to see and stop attacks beyond OWASP injection, which has been the focus of legacy Web Application Firewall (WAF) and Runtime Application Self Protection (RASP) tools. Power Rules doesn't require users to learn or manage any complicated rules or scripting language.

Synopsys Seeker 2018.07
Synopsys' Seeker 2018.07 interactive application security testing offering has been redesigned to enable DevSecOps and continuous delivery of secure web applications. Seeker monitors web applications during preproduction testing cycles and automatically verifies whether vulnerabilities are exploitable, providing developers with accurate, actionable information in real time.
Seeker enables security teams to identify and track sensitive data such as credit cards numbers, usernames and passwords to ensure that they are handled securely and not stored in log files or databases with weak or no encryption. Sensitive data tracking helps organizations comply with data security regulations such as GDPR.
The tool also provides automatic active verification to confirm that detected vulnerabilities are exploitable, resulting in a near-zero false positive rate. This verification is achieved through patented technology that replays original HTTP(S) requests with tainted parameters and monitors the resulting application data flow.