Tech 10: Getting Smart About Advanced Threat Protection
These 10 offerings thwart the most insidious ransomware and zero-day threats through sandboxing, shared intelligence and automated processes.

The Worst Of The Worst
Advanced persistent threats are a prolonged type of cyberattack focused on stealing sensitive and confidential information from the targeted organization. APT protection offerings combine multiple tools and techniques to help the targeted organization respond to threats more quickly, actively, and effectively.
The APT protection market is poised for growth due to a desire to improve visibility and control across an organization's network, lower business risk by preventing and responding to APT attacks, and secure highly confidential and sensitive information from being stolen by attackers.
The global advanced persistent threat protection market is expected to expand at a compound annual growth rate (CAGR) of 18.1 percent, reaching $16.2 billion by 2024, according to Kenneth Research. North America is expected to dominate the APT protection market due to an increasing number of cyberattacks and stringent government regulations.
Here's a look at ten of the most advanced threat protection offerings available on the market today.
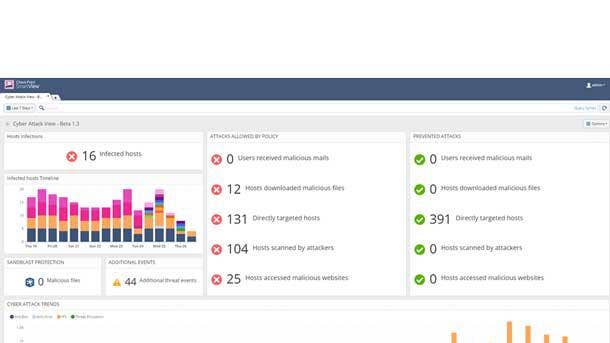
Check Point Sandblast Network
Check Point SandBlast Network detects and blocks previously undiscovered malware to keep organizations threat-free. It uses threat emulation and CPU-level inspection to deliver the best possible catch rate for unknown malware. And the threat extraction capabilities ensure that safe content, or clean and reconstructed versions of potentially malicious files, are delivered to maintain uninterrupted business flow.
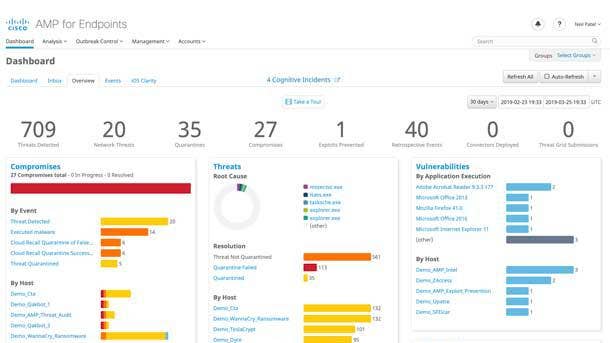
Cisco Advanced Malware Protection
Cisco Advanced Malware Protection provides global threat intelligence, advanced sandboxing and real-time malware blocking. The tool continuously analyzes file activity across an organization’s extended network to quickly detect, contain and remove advanced malware. It correlates files, telemetry data and file behavior against intelligence from Cisco Talos to proactively defend against known and emerging threats. Advanced sandboxing, meanwhile, uncovers stealthy threats to help block sophisticated attacks.
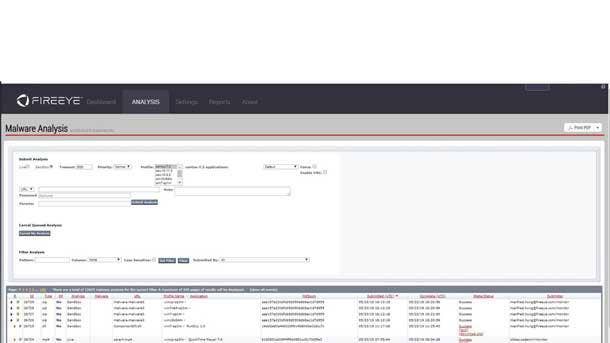
FireEye Malware Analysis
FireEye Malware Analysis provides a secure environment to test, replay, characterize and document advanced malicious activities. It shows the cyberattack life cycle from the initial exploit and malware execution path to callback destinations and follow-on binary download attempts. The tool also stops the spread of attacks by using auto-generated local attack profiles, which are instantly shared across the FireEye ecosystem.
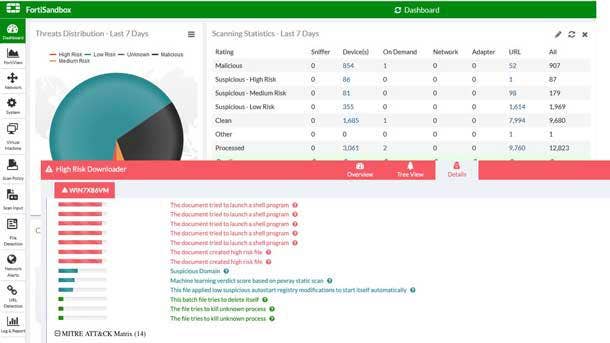
Fortinet Advanced Threat Protection
Fortinet Advanced Threat Protection leverages integrated detection of advanced threats for automated response and mitigation. The product delivers sandboxing as an integrated feature of established security technologies already in place across the network, email, web application and endpoint. This ensures that almost all malware gets routed for inspection, and new intelligence about unknown malware is returned for automated response and improved protection.
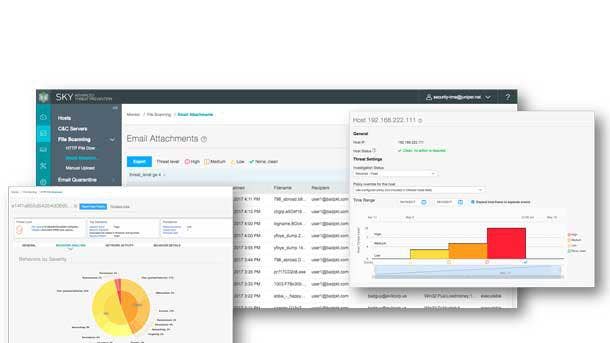
Juniper Sky Advanced Threat Prevention
Juniper Sky Advanced Threat Prevention provides advanced anti-malware and anti-ransomware protection, delivering progressive verdicts that assess the risk level of each potential attack. The tool uses many techniques to quickly identify a threat and prevent an impending attack. These range from rapid cache lookups to identify known files to dynamic analysis using unique deception techniques applied in a sandbox environment to trick malware into activating and self-identifying.
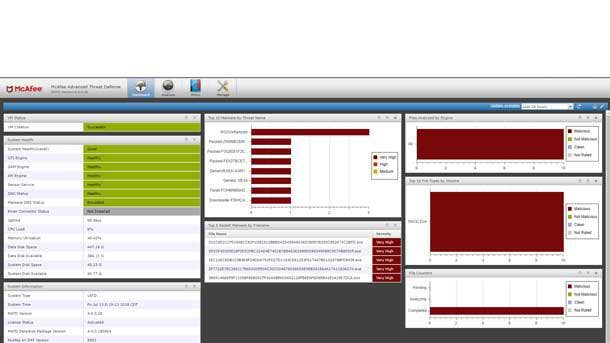
McAfee Advanced Threat Defense
McAfee Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action. The product combines in-depth static code analysis, dynamic analysis and machine learning to increase zero-day threat detection. The tool includes inspection capabilities that go beyond traditional sandboxes to broaden detection and expose evasive threats. Tight integration between network and endpoint security capabilities enables instant sharing of threat information.
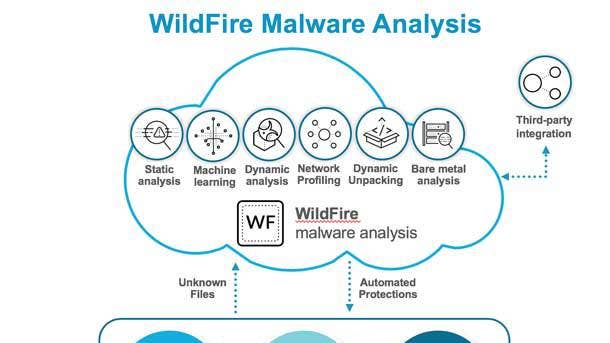
Palo Alto Networks Wildfire
The Palo Alto Networks WildFire malware analysis service applies advanced analysis to data and threat intelligence to automatically identify threats. It combines dynamic and static analysis, machine learning and bare-metal analysis to detect and prevent evasive threats, orchestrating automated prevention in as little as five minutes from first discovery without requiring manual response. It also builds collective immunity for unknown malware and exploits with shared intelligence from some 26,000 subscribers.
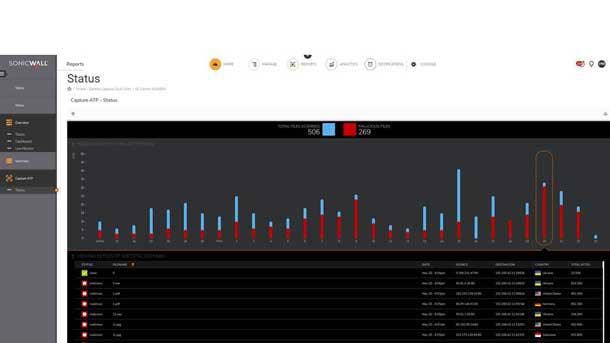
SonicWall Capture Advanced Threat Protection
SonicWall’s Capture Advanced Threat Protection service stops unknown, zero-day attacks at the gateway with automated remediation. This cloud-based multi-engine sandbox analyzes suspicious code to help discover and block newly developed malware from entering a network. The tool extends firewall threat protection to detect and prevent zero-day attacks and prevents potentially malicious files from entering the network, returning a verdict quickly by processing files in parallel using multiple engines.

Sophos Sandstorm
Sophos Sandstorm provides a dedicated cloud sandbox environment to stop zero-day and unknown threats. The product delivers an extra layer of security as well as zero-day malware disguised as executables, PDFs and Microsoft Office documents. Sandstorm prefilters all files to ensure high performance, focusing detonation on unknown, suspicious files to increase performance.
Symantec Endpoint Detection And Response
Symantec Endpoint Detection and Response hunts, isolates and eliminates intrusions across all endpoints using AI-driven analytics, investigation playbooks and threat intelligence. It supports “zero trust” threat hunting with advanced forensics that use full memory scans and metadata acquisition to find injections, process hollowing and shellcode. The tool reduces mean time to remediation through deep endpoint visibility and superior detection analytics.