The 10 Hottest New Cybersecurity Tools And Products Of 2021 (So Far)
The 10 cybersecurity tools and products making noise in the market have emphasized extended detection and response, multi-cloud visibility, passwordless authentication and risk management services.

Avoiding The Mistakes Of The Past
Read the latest entry: The 10 Hottest Cloud Security Tools and Prodcuts of 2022
Vendors have spent the first half of 2021 advancing security everywhere from endpoint and identity to the cloud and web, debuting tools that securely connect on-premises users to applications without network segmentation, facilitate cloud application login through biometrics rather than passwords, or allow for the management of access, governance and privileges from a single, centralized dashboard.
Enhancements to security operations and intelligence have been a major area of focus thus far in 2021, with advancements around everything from behavioral analytics and managed account takeover monitoring to using threat intelligence and incident response data to shine a light on an organization’s risk posture.
Seven of the 10 hottest cybersecurity tools and products of 2021 (so far) came from companies based in California, with the remaining three coming from vendors based in Minnesota, England and Israel. Read on to learn how vendors have gone about making their cybersecurity portfolio even more solution- provider-friendly.
For more of the biggest startups, products and news stories of 2021 so far, click here.
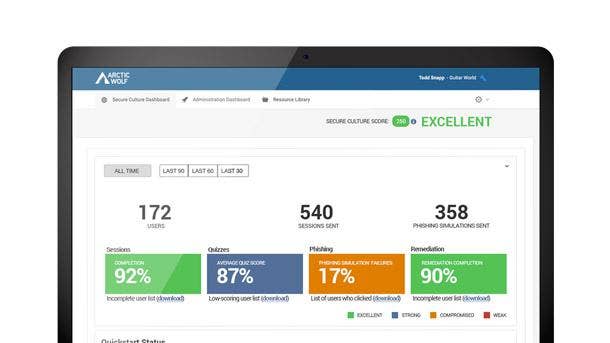
Arctic Wolf Managed Security Awareness
Arctic Wolf Managed Security Awareness debuted in May and brings together fully managed security awareness training, phishing simulation and account takeover monitoring that’s delivered as a concierge service. It’s intended to make it fast and easy for all security teams, including those who don’t have an IT or cybersecurity function, to add a security awareness and training program.
Eden Prairie, Minn.-based Arctic Wolf’s offering includes security awareness microlearning that prepares employees to stop social engineering attacks with continuous training to recognize current threats, avoid scams and understand the importance of reporting mistakes. Account takeover monitoring, meanwhile, reduces risk with immediate notification when employee credentials are found on the dark web.
The phishing simulation capabilities measure and reinforce employee awareness with automated assessments and phishing simulations based on real-life attacks. And turnkey content delivery engages employees by deploying timely content with high production value and a vision of building academic-level programming rigor.
Check Point Harmony
Check Point Software Technologies in February rolled out the Harmony unified offering to secure both internet connections as well as corporate and BYOD devices for remote workers. The platform brings together endpoint, browser, email and remote access security into a single offering that’s managed via a cloud service and is available to customers for $11 per user, per month.
The all-new Harmony Browse tool provides secure, fast and private web browsing by inspecting all SSL traffic directly on the endpoint without adding latency or re-routing traffic through a secure web service, according to San Carlos, Calif.-based Check Point. It blocks zero-day malware downloads and access to phishing websites as well as preventing the reuse of corporate passwords, according to the company.
Other elements of the Harmony bundle include Connect, which Check Point said securely connects any user or branch to any resource, supporting clientless zero trust network access from any browser. All Harmony products—including the rebranded Harmony Email and Office and Harmony Endpoint—can be managed from a single portal, simplifying the day-to-day experience for users and administrators alike.

CrowdStrike Zero Trust
CrowdStrike Zero Trust debuted in May and gives organizations visibility into workforce identity across multi-directory, multi-cloud environments. The Sunnyvale, Calif.-based company’s offering reduces dynamic friction and false positives by providing conditional access, which shortens the time to detect and resolve incidents by eliminating the need for complex, error-prone log analysis.
This in turn cuts down on alert fatigue, stops attack proliferation, and ensures that security teams are better informed. CrowdStrike Zero Trust reduces the load on Security Operations Center (SOC) analysts with high-fidelity correlations and enhances user experience with adaptive conditional access.
CrowdStrike Zero Trust also assesses endpoint security posture and enforces conditional access using resources from compliant endpoints by sharing assessment scores with ecosystem partners. It also ensures a consistent login experience for genuine users while enforcing intelligent conditional access for resources and applications only when the risk increases.

Duo Passwordless Authentication
Duo passwordless authentication debuted in March and enables users to skip the password and securely log into cloud applications through security keys or biometrics built into modern smartphones and laptops. It leverages biometrics platforms such as Windows Hello and Apple FaceID and TouchID, allowing organizations to consolidate hundreds of passwords and authentications into one easy login.
The product enables biometrics to be securely stored on and validated locally by the device as opposed to a centralized database and is designed to meet GDPR as well as standards like HIPAA and PCI. Passwordless authentication will be a default feature in higher editions of Duo, and the subsidiary of San Jose, Calif.-based Cisco hopes to have it publicly available in July.
More than 300 customers wanted to try out Duo passwordless authentication in beta even though there were just 50 slots available, and there’s been broad interest in the tool outside the federal contracting space regardless of vertical or size. Duo’s road to passwordless authentication has taken six years and required advances in biometric technology as well as more modern standards.
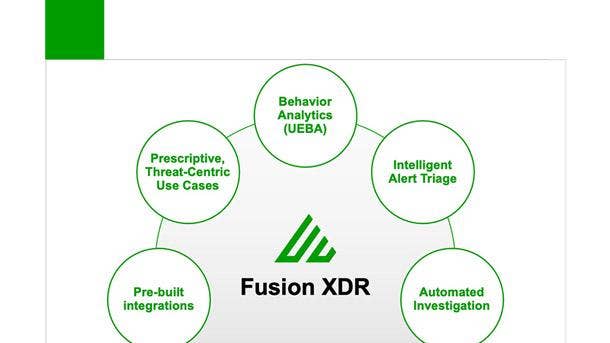
Exabeam Fusion XDR
Exabeam Fusion XDR was unveiled in May and addresses threat detection, investigation and response without disrupting an organization’s existing technology stack. The product combines behavioral analytics, automation, and prebuilt integrations with hundreds of third-party security and productivity tools to overcome weak signals from multiple products and find complex threats missed by other tools.
Customers using Exabeam Fusion XDR can easily identify and respond to critical security issues, intrusions, and attacks from a single, centralized control plane, substantially increasing analyst productivity and reducing response times. The Foster City, Calif.-based company’s offering differentiates normal behavior from abnormal activity, applies risk scoring to identify notable issues and automatically reconstructs security incidents.
The product contains prescriptive workflows guided by pre-packaged, use-case-specific context to enable security analysts to defend against common and evolving threats such as external, compromised insider, and malicious insider attacks. Exabeam Fusion SIEM, meanwhile, includes all Fusion XDR features and capabilities plus access to powerful search, centralized log stage and compliance reporting.

Fortinet FortiOS 7.0
Fortinet’s FortiOS 7.0 was unveiled in February and tackles some of the biggest security issues around working from home and securing the SASE edge. FortiOS 7.0 enables FortiGate customers to employ Zero Trust Network Access capabilities out of the box, reducing the attack surface by verifying the user and device for every application session while hiding business-critical applications from the internet.
The platform extends network connectivity and security beyond the WAN edge with innovations in 5G and LTE that improve wireless network performance and increase resiliency. FortiOS 7.0 also includes self-healing capabilities through adaptive WAN remediations to make the application experience more resilient, as well as passive application monitoring for SaaS and multi-cloud applications.
With the introduction of FortiOS 7.0, Sunnyvale, Calif.-based Fortinet’s adaptive cloud security offerings now provide central management for hybrid clouds with auto-scaling for practical usage of resources, dynamic load-balancing, and application user experience visibility. Other updates simplify SaaS management and strengthen Fortinet’s ability to reduce complex operations into a single management experience.
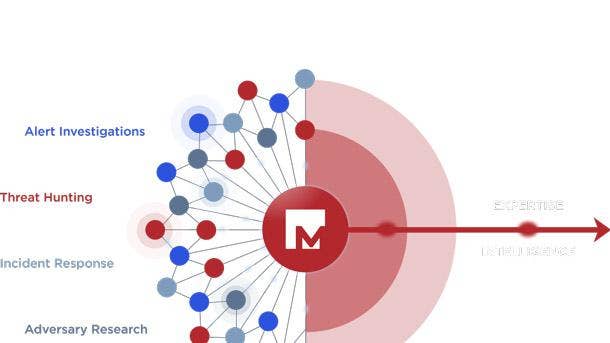
Mandiant Cyber Risk Management Services
Mandiant Cyber Risk Management Services were unveiled in May to equip executives, boards of directors, and security and cross-functional leaders with risk-based data and advice to build effective and balanced security programs. They incorporate Mandiant threat intelligence, incident response data, and proven risk methodologies to help organizations shine a light on where harmful risk exists.
The Milpitas, Calif.-based company’s services include an assessment of the customer’s existing security program capabilities and maturity, coupled with an actionable improvement road map focused on the areas with the highest risk. Mandiant’s crown jewels assessment identifies critical assets to shift security efforts and prioritize investment on the assets that matter most.
Mandiant’s cyber due diligence surfaces and manages inherited cyber risks outside an organization’s control like those found in supply chain, third-party vendors, or during corporate acquisitions and divestment. And cyber risk operations services can help design and operationalize risk programs that leverage threat intelligence and frontline experience to determine custom risk profiles and tolerances.
Okta Privileged Access and Identity Governance
Okta customers early next year will be able to leverage a single platform for identity governance, privileged access and to collect audit logs for compliance, making setup and management easier, while enhancing the user experience. Customers can enable end-to-end identity governance processes across applications, infrastructure and APIs at any level of scale using San Francisco-based Okta’s extensible APIs and no-code workflows.
Okta Identity Governance harnesses popular workplace tools to promote delegation and self-service, streamlining the evaluation and decision-making of who should have access to what resources and when. It automatically suspends access to resources based on user status changes in HR systems and directories and can produce quick audit evidence and reporting for sensitive resources.
Okta Privileged Access allows for the application of fine-grained user and role-based security policies from a central system to manage who can access what at the infrastructure level. It minimizes the attack surface area of privileged accounts and credentials by offering just-in-time, least privilege access controls, and streamlines compliance by tying session logging to specific users in a centralized view.
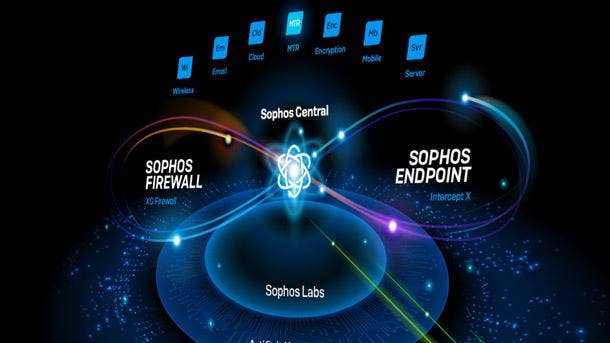
Sophos XDR
Sophos XDR debuted in May and synchronizes endpoint, server, firewall and email security to provide a holistic view of an organization’s environment with deep analysis for threat detection, investigation and response. The platform offers two types of data retention, including up to 90 days of on-device data as well as 30 days of cross-product data in the cloud-based data lake.
Blending on-device and data lake forensics provides contextualized insight that can be leveraged by security analysts through Sophos Central and via open APIs for ingestion into SIEM, SOAR, PSA and RMM systems. The data lake hosts critical information from Sophos’ endpoint, network, email, cloud and mobile products and will feed into the company’s data repository later this year, according to Sophos.
Security and IT teams can easily access this data to run cross-product threat hunts and investigations as well as to drill into granular details of past and present attacker activity. The availability of offline access to historical data further protects against lost or impacted devices, according to Oxford, U.K.-based Sophos.
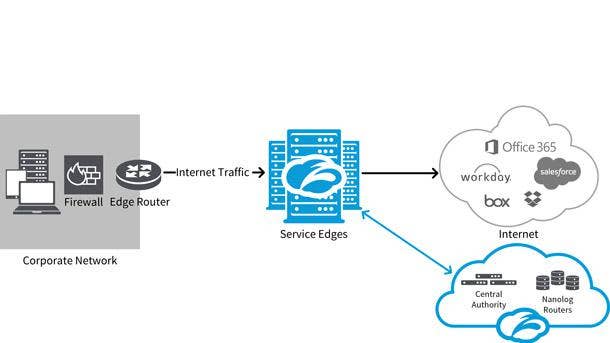
Zscaler ZPA Private Service Edge
Zscaler ZPA Private Service Edge was unveiled in April to securely broker users to private applications, removing the need for on-premises network segmentation. It is hosted by the customer, managed by Zscaler, and is ideal for on-premises environments or locations subject to internet access challenges.
The San Jose, Calif.-based company’s product provides local brokering between on-premises users and on-premises applications, which creates a faster experience for users, less complexity for network admins, and less risk for business data by having least-privilege access. Remote users can access applications running on-premises, and the product automatically determines the fastest path for each user and selects the broker that is best for the job.
ZPA Private Service Edge allows customers to comply with in-country industry regulations by running locally, and handling all brokering within the customer’s own environment. Dual access capabilities of on-premises and public cloud brokering optimizes the experience for local users when accessing private apps running on-premises and for remote users in countries where there is no local ZPA cloud broker.