The 10 Hottest New Cybersecurity Tools Of 2019
The 10 new cybersecurity tools capturing the market’s attention allow businesses to better assess, prioritize, detect, and respond to threats by automating repeatable processes and ensuring security teams are dealing with the most important alerts.

Taking Threats Seriously
See the latest entry: The 10 Coolest Cybersecurity Tools and Products of 2022 (So Far)
Vendors have spent 2019 beefing up their capabilities around assessing, prioritization, detecting and responding to threats by correlating global threat activity with organization-specific risks, automating repeatable processes, and ensuring security teams are dealing with the most important alerts.
Enhancements to protecting networks, endpoints, gateways and devices have also been a major area of focus in 2019, with advancements around detecting malicious user behavior, expanding the performance of security gateways, managing device and policy settings in a consistent manner, and extending the benefits of SD-WAN to network access.
Six of the 10 hottest new cybersecurity tools of 2019 came from companies based on the West Coast of the United States, one came from a company based on the East Coast of the U.S., and three came from companies based abroad. Read on to learn where suppliers are investing in hopes of keeping customers and partners safe.
Get more of CRN's 2019 tech year in review.
BlackBerry Intelligent Security
BlackBerry Intelligent Security was released in August, and leverages the power of adaptive authentication and AI-driven security to create a more secure, contextual system for unified endpoint management. It solves dynamic threat landscape challenges by intelligently driving security policies across endpoints based on risk and the context of actions being performed in real time.
The product enforces security by detecting and preventing anomalous and malicious user behavior according to an organization's regulatory and security policies. BlackBerry Intelligent Security utilizes a range of personal identifiers and capabilities to seamlessly secure endpoints across financial services, government, transportation, professional services and other industries.
BlackBerry Intelligent Security uses AI to accommodate employees' workflows and maintain security protocols that otherwise might be compromised by well-intentioned workarounds. And machine- learning capabilities enable the system to identify the behavioral and locational patterns of multiple users to determine risk and grant the appropriate access.

Check Point Maestro
Check Point Maestro was released in January and allows organizations to easily scale up their existing Check Point security gateways on demand, in the same way that new servers and compute resources are spun up in the public cloud. Maestro enables a gateway to expand to the capacity and performance of 52 gateways in minutes, giving companies flexibility and enabling massive firewall throughput.
Customers using Maestro can scale up their existing gateways of any size within minutes to support more than 50 times their original throughput, Check Point said. It is managed intuitively by Maestro Security Orchestrator, which controls all of an organization's gateway as a single unified security system, minimizing management overhead.
Maestro is the only unified security system that can offer cloud-level resilience and reliability to all organizations, Check Point said. The almost limitless scalability of Maestro enables organizations to support the high data rates and ultra-low latency of 5G networks, and secure the largest, most resource-hungry environments.
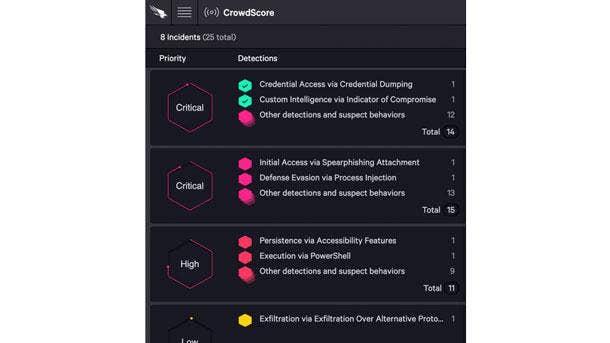
CrowdStrike CrowdScore
CrowdStrike CrowdScore debuted in August, and leverages cloud-based analytics and artificial intelligence to provide a single view for executives about the real-time threat level their organizations are facing, enabling them to speed up triage, prioritization and incident response. It leverages CrowdStrike's global visibility and advanced analytics to produce actionable insight for executives, analysts and investigators.
CrowdScore's organizational “Defcon” score makes it easy for security leaders to understand if they are under attack and the severity of the threat so they can immediately mobilize the appropriate response. The tool's smart prioritization streamlines the triage process and presents the most important incidents to analysts via a central dashboard, ensuring they are directed to the most critical threats first.
Meanwhile, CrowdScore's Incident Workbench will automate the cumbersome labor involved in collecting the data needed to understand the scope of an emerging threat. Incident Workbench's sophisticated visualizations and workflows significantly reduce the time needed to orient and act against modern threats of all types.
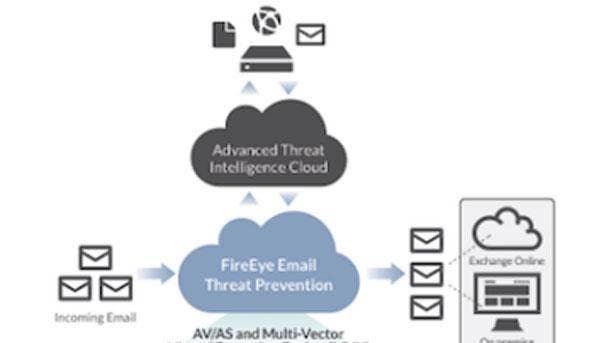
FireEye Cloud Security Solution
FireEye in October extended its threat detection and protection capabilities through a cloud-based architecture to defend increasingly complex hybrid security environments. More than half the breaches FireEye responds to involve cloud infrastructure, according to the company.
The company said its new FireEye Cloud Security Solution provides scalable detection, centralized visibility, configuration monitoring, and user behavior analytics across complex multi-cloud infrastructure. This makes it possible for businesses to identify advanced attacks that got past traditional or poorly integrated defenses, according to FireEye.
Organizations too often lack the controls and expertise necessary to extend their visibility and protection across multi-cloud infrastructure, according to FireEye. But FireEye said its new capabilities will allow businesses to protect the assets and workflows they’re running in the cloud and deliver protection for inline, passive, on-premise, hybrid and virtual deployment scenarios.
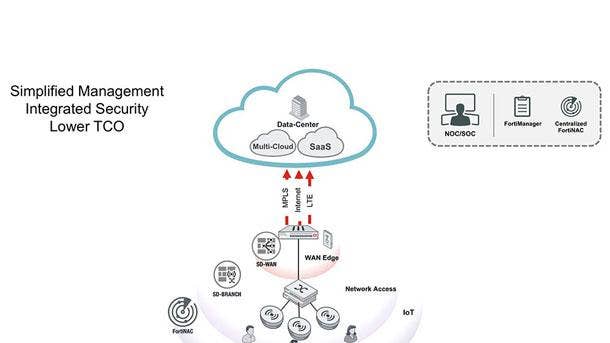
Fortinet Secure SD-Branch
Fortinet's Secure SD-Branch offering was released in June and secures the WAN (Wide Area Network) and access edge to enable security-driven networking for distributed enterprises. The tool extends the benefits of SD-WAN to network access, converging WAN and security to increase visibility, reduce complexity, improve performance and agility, and lower overall IT costs at the edge of the network.
The Secure SD-Branch tool is comprised of the FortiGate Next-Generation Firewall, FortiNAC Network Access Control, FortiSwitch and FortiAP Access Points. This unique technology combination provides better integration of LAN (local area network) and WAN platforms and delivers integrated security, simplified management, and a lower total cost of ownership to customers.
Extending firewall security through the access layer helps consolidate security and network access and is a unique architecture ideal for secure SD-branch deployment, Fortinet said. Plus the new FortiNAC 8.6 release increases anomaly detection via traffic scanning by leveraging FortiGate as a sensor, with no additional hardware required at the branch.

IBM X-Force Red Blockchain Testing Service
The IBM X-Force Red Blockchain Testing Service was released in March and evaluates the entire implementation process including chain code, public key infrastructure and hyperledgers. It also tests the backend processes, applications and physical hardware used to control access to and management of the blockchain networks.
IBM X-Force Red evaluates how permissions to access and add information to the blockchain are administered, including password policies, susceptibility to brute force attacks, and the implementation of two-factor authentication. The team also tests for the secure creation, management, and distribution of digital certificates and keys associated with the blockchain network.
Common libraries and component dependency hacking can be tested by X-Force Red during design and implementation to ensure secure dependency signatures and a trust build pipeline. And while smart contracts allow for trustless execution of agreements by parties on the blockchain, IBM said proper penetration testing can still find exploitable flaws in those agreements.

McAfee MVision Insights
McAfee in October unveiled a tool to help businesses better understand what kinds of threats they should be most worried about and what they should do about them. Using the ePolicy Orchestrator, McAfee can marry what it knows about the customer's infrastructure and security posture with the threats that have been flagged as relevant to its business.
The company said MVision Insights will allow customers to understand what's going on from a global threat landscape perspective as well as what threat activity should matter specifically to them, according to Ash Kulkarni, executive vice president and chief product officer for McAfee's enterprise business group.
Sensors in the customer's environment and indicators of compromise observable within their infrastructure help McAfee determine which threats a particular customer should be most concerned about, Kulkarni said. Using machine-learning models, Kulkarni said McAfee can assess the kinds of threats customers are most likely to face based on their physical location and the industry they're in.
Microsoft Azure Sentinel
Azure Sentinel was released in February and aims to stand out from other SIEM (security information and event management) tools by leveraging the scalability and flexibility of the cloud and by tapping artificial intelligence to reduce cyberthreat noise.
The launch comes at a time when massive volumes of data have created issues for security professionals, who are often too overwhelmed by alerts to focus on solving complex security problems, according to Microsoft. Early partners working with Azure Sentinel include Accenture, Insight and New Signature, Microsoft disclosed.
The use of AI in Azure Sentinel has helped to enable a 90-percent reduction in "alert fatigue" among early users, wrote Ann Johnson, corporate vice president for cybersecurity at Microsoft, in a blog post. Organizations can bring data into Azure Sentinel from Office 365 for free, where it can be analyzed alongside the organization's other security data, Johnson said.

Sophos Managed Threat Response
Sophos in October unveiled a managed threat response service that integrates with the company's protection capabilities to ensure security teams end up dealing with the most important alerts.
The company said its managed threat response (MTR) service builds off the technology acquired from Rook Security and will initially operate using input from Sophos' endpoint security products, according to Chief Technology Officer Joe Levy. The MTR offering is intended to help resource-constrained organizations benefit from Sophos' detection and response capabilities, Levy said.
The MTR service will expand from operating only on the endpoint signal to ingesting data from the Sophos XG Firewall and Cloud Optix by early 2020, Levy said. From there, Levy said Sophos plans to work on having the MTR service incorporate data from Sophos' email security, mobile security and wireless security products, as well as potentially building connectors to data from third-party products, Levy said.

Tanium Enforce
Tanium plans to take a slightly revised approach to device management when it rolls out Tanium Enforce in the April 2020 timeframe by providing customers with a consistent and unified approach to managing configuration, security, and other device and policy settings, said Chief Product Officer Pete Constantine. The product will make it possible to configure, enforce and report on policy settings anywhere, anytime, he said.
Tanium Enforce aims to unite end user devices, on-premise servers and cloud-hosted servers as well as different device types, hosting platforms and operating systems onto a single tool, Constantine said. The company’s approach to systems configuration and management is supported remotely and does not require being on a local area network (LAN) for the settings to apply, according to Constantine.
The product takes the 5,000 or 6,000 different configuration policies available within Windows administrative templates and makes it easy to configure, enforce and report on those items without custom scripting, according to Constantine. Configuration and systems profiles will also be provided on Apple OS X to provide the same functionality on Mac without any custom scripts or content, he said.