The 11 Biggest Ransomware Attacks Of 2020 (So Far)
Municipal governments, universities and private businesses have spent more than $144 million responding to the biggest ransomware attacks of 2020 (so far), spending on everything from rebuilding networks and restoring backups to paying the hackers ransom.

Weaponizing The Data
The line between ransomware attacks and data breaches continues to blur in early 2020, with a number of prolific ransomware operators – including Maze, Sodinokibi, DoppelPaymer, Nemty, Nefilim, CLOP and Sekhmet – creating their own websites where they publish the stolen data of non-paying victims, according to cybersecurity firm Emsisoft.
In 2020, Emsisoft said ransomware groups have threatened to: sell stolen data to competitors; use stolen data to attack victims’ business partners; and publicize victims’ “dirty secrets” on the clear web for all to see. Some attackers took advantage of COVID-19 to coax people into opening malicious emails and attachments, while other ransomware groups agreed to an ad-hoc ceasefire on healthcare vendors.
Victims of the 11 biggest ransomware attacks (so far) have spent at least $144.2 million on costs ranging from investigating the attack, rebuilding networks and restoring backups to paying the hackers ransom and putting preventative measures in place to avoid future incidents. The victims allegedly paid a ransom in seven of the cases. Recorded Future assisting with compiling some of the incidents.
Five of the ransomware victims were municipal governments, while the remaining spanned verticals from legal, manufacturing and financial services to IT services, facility management and higher education. Eight of the affected entities are in the United States, two are in England and one is in Denmark. Here’s an examination of 10 of the biggest ransomware attacks during the first half of 2020.
For more of the biggest startups, products and news stories of 2020, click here.
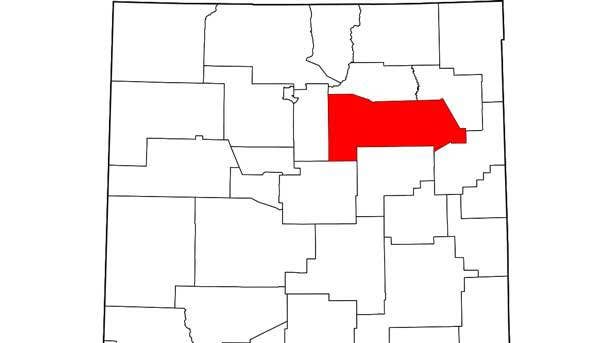
11. San Miguel County, N.M.
Recovery And Mitigation Costs: $250,000
A late-January ransomware attack infected one of San Miguel County’s servers, prompting the county to bring in outside lawyers and IT experts to negotiate a ransom with the hackers, County Attorney Dave Romero told the Las Vegas (N.M.) Optic on Feb. 6. The county wasn’t clear what information had been exposed during the attack, and was in the process of verifying that other servers hadn’t been hit as well.
The ransomware attack ultimately locked San Miguel County out of 10 computers and compromised its backup system, but the county was able to get its computers up and running quickly because it had purchased cyber insurance, Taylor Horst, risk management director of the New Mexico Association of Counties, told the Albuquerque Journal in March.
The forensics firm brought in through the association’s commercial cyber liability insurance policy was able to negotiate a ransom of 24 bitcoins, worth about $250,000, down from the initial demand of 43 bitcoins, Horst said. The county also changed all its passwords, and contacted banks, creditors and phone companies to make them aware of the situation, according to Romero.
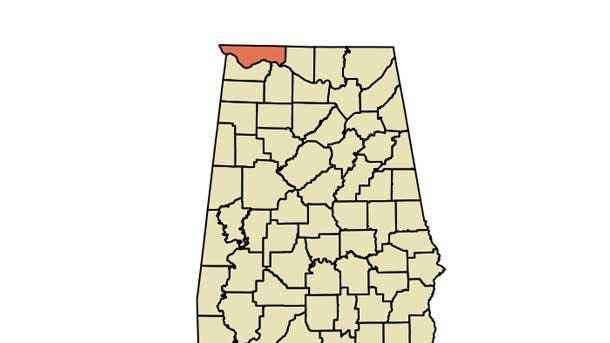
10. Florence, Ala.
Recovery And Mitigation Costs: $291,000
A Windows 10 system in the IT environment of Florence, Ala. was commandeered by a ransomware gang, with hackers gaining a foothold in the city’s network on May 6 with the username for the city’s manager of information systems, according to KrebsOnSecurity. Then in early June, a cyberattack by ransomware gang DoppelPaymer shut down the city’s email system, Florence Mayor Steve Holt said.
DoppelPaymer appears to have simultaneously compromised networks belonging to four other victims within an hour of Florence, including another municipality, Holt told KrebsOnSecurity. DoppelPaymer initially demanded $378,000 in Bitcoin, Holt said, but an outside security firm hired by the city was able to negotiate the price down to $291,000 in Bitcoin.
Holt told KrebsOnSecurity that Florence couldn’t afford to see its citizens’ personal and financial data jeopardized by not paying. The Florence City Council unanimously approved the ransom payment at an emergency meeting on June 10, saying they did so to preserve information about city workers and customers, according to The TimesDaily.
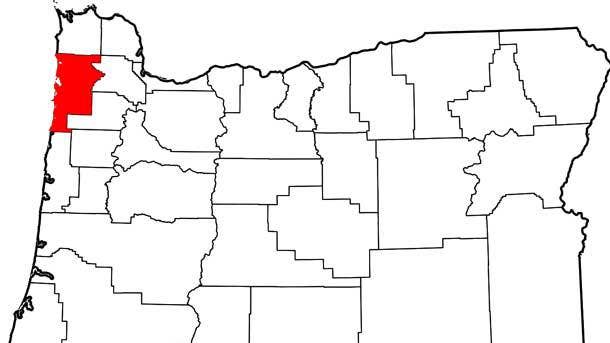
9. Tillamook County, Ore.
Recovery And Mitigation Costs: $300,000
A Jan. 22 ransomware attack took down Tillamook County’s server, internal computer systems, website, phone systems and email networks, forcing the county to disable to computer network connection to contain the spread of malware, according to the Tillamook Headlight Herald. The attack originated from a group called REvil, which also goes by Sodinokibi or Sodin.
Commissioner Bill Baertlein said Tillamook County’s rapid and aggressive response to the incident mitigated the compromise and container the encryption to 17 of 55 servers and five of 280 county workstations. However, the cyberattack resulted in encrypted backups, meaning that data critical to county operations couldn’t be restored without paying the cyberattacker for decryption keys, he said.
It could have taken 12 to 24 months and cost $1 million to unlock the county’s computer system if the ransom went unpaid, Baertlein said at a March 11 Tillamook County Board of Commissioners meeting. As a result, county officials said a $300,000 ransom was paid to regain data access after the cyberattack, and county systems were operational by mid-March, the Tillamook Headlight Herald reported.

8. Grubman Shire Meiselas & Sacks
Recovery And Mitigation Costs: $365,000 (Disputed)
Entertainment and media law firm Grubman Shire Meiselas & Sacks confirmed in mid-May that its computer systems were hacked which allegedly resulted in the theft of 756 gigabytes of private documents and correspondence, according to Variety. The attack was carried out by REvil, also known as Sodinokibi, according to cybersecurity firm Emsisoft.
The hacker collective claimed to be holding thousands of the law firm’s documents hostage, including private info on Lady Gaga, Madonna, Nicki Minaj, Bruce Springsteen, Mary J. Blige, Ella Mai, Christina Aguilera and Mariah Carey, Variety reported. The hackers said President Donald Trump would be the next subject of a public data dump if they weren’t paid within a week, according to Variety.
REvil initially demanded a $21 million ransom and claims to have received payment of $365,000 in connection with the documents stolen from the law firm, prompting the hackers to double their ransom demand to $42 million. However, a rep for Grubman Shire Meiselas & Sacks told Variety in mid-May that it was categorically false that any payments had been made to the cybercriminals.
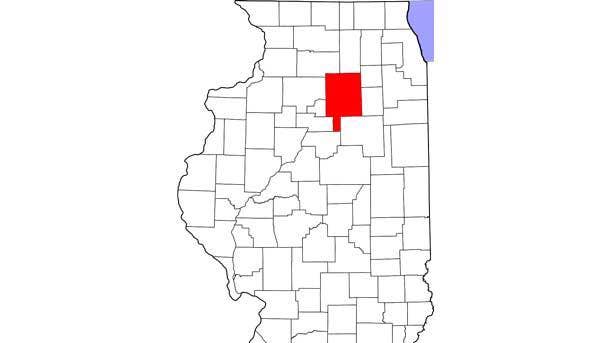
7. La Salle County, Ill.
Recovery And Mitigation Costs: $500,000
A Feb. 23 ransomware attack infected La Salle County’s governmental offices, taking down email accounts, limiting access to documents and causing many county services to be provided “the old-fashioned way” with paper, according to The Times (Ill.). Most of the data had already been backed up, and a vendor was on-site three days later to restore the system, WLPO radio reported.
The county declined to pay the ransom, and IT Director John Haag said in June that the total cost of the ransomware attack could be about $500,000 when all is said and done. The investigation alone cost more than $100,000, and the county spent $66,250.76 on new equipment, according to Haag.
La Salle County will be able to pay just a $5,000 deductible to its insurance company to cover all the costs, including hundreds of hours of overtime put in by its IT staff, The Times reported. But Haag said some of the tools bought to remedy the attack may not be reimbursed since insurance typically only covers what’s been lost.

6. Communications & Power Industries (CPI)
Recovery And Mitigation Costs: $500,000
A “domain admin” with the highest level of privileges on the network of California-based Communications & Power Industries (CPI) clicked on a malicious link in mid-January while logged in, triggering file-encrypted malware, TechCrunch reported in March.
Because the thousands of computers on the network were on the same, unsigned domain, the ransomware quickly spread to every CPI office, including its on-site backups, a source told TechCrunch. Only a quarter of CPI’s computers were back up and running as of the end of February, according to TechCrunch.
CPI paid a ransom of about $500,000 shortly after the incident, TechCrunch said, allowing the company to obtain a decryption key that was used to recover sensitive military data on affected computers. One system is said to have files related to Aegis, a naval weapons system developed by Lockheed Martin, according to TechCrunch.

5. University of California San Francisco (UCSF)
Recovery And Mitigation Costs: $1.14 Million
Malware launched on June 1 encrypted a limited number of servers within UCSF’s School of Medicine, making them temporarily inaccessible, UCSF disclosed on June 26. The malware is believed to have encrypted the UCSF servers opportunistically, with no particular area being targeted, and the attackers obtained some data as proof of their action to use in their demand for a ransom payment.
The data that was encrypted is important to some of the academic work that UCSF pursues, the university said. UCSF said it therefore agreed to pay a portion of the ransom – approximately $1.14 million – to the individuals behind the malware attack in exchange for a tool to unlock the encrypted data and have the data they obtained returned.
UCSF said it doesn’t currently believe that patient medical records were exposed in the ransomware attack. The breached IT systems were successfully isolated from the core UCSF network, meaning that the university’s patient care delivery operations, overall campus network and COVID-19 work weren’t impacted, according to UCSF.

4. Travelex
Recovery And Mitigation Costs: $2.3 Million
A New Year’s Eve ransomware attack crippled Travelex, forcing the world’s largest chain of money-exchange shops to take its internal networks, consumer-facing websites and app offline for several weeks to stop the virus, The Wall Street Journal reported. The company reportedly begun reinstating some of its operations in January and revived its consumer business in the second half of February.
The incident disrupted cash deliveries from Travelex’s global network of vaults to divisions of major international banks including Barclays PLC and Lloyds Banking Group PLC, The Wall Street Journal said. The Sodinokibi group of hackers who claim to have hacked Travelex declined to provide specifics on what they had stolen from the company, The Wall Street Journal reported.
Travelex responded to the attack by paying the hackers a $2.3 million ransom in the form of 285 bitcoin, a person familiar with the transaction told The Wall Street Journal in April. A Travelex spokesman told the paper the firm has taken advice from a number of experts and has kept regulators and partners informed about its efforts to manage the recovery.

3. Redcar And Cleveland Council (England)
Recovery And Mitigation Costs: $13.6 Million To $22.2 Million
A ransomware cyberattacks on Feb. 8 forced Redcar and Cleveland council staff off council computers, tablets and mobile devices for three weeks, forcing them to instead rely on “pen and paper,” the Guardian reported. In the weeks following the attack, the council was forced to build a new server and website and mobilize a temporary call center, according to council leader Mary Lanigan.
But as of late February, the Guardian reported the council website was still not functioning properly and residents complained of being cut off repeatedly when ringing the local authority as instructed, instead of emailing. Events several weeks away had been cancelled, with officials blaming the IT problems, according to the Guardian.
One Redcar and Cleveland councilor told the Guardian they had been advised it would take several months and cost between $13.6 million an $22.2 million to repair the damage – far more than the $9.1 million funding grant the council is set to receive in 2020/2021 from the central government. A council spokesman told that Guardian in late February they didn’t have an official cost figure for the clean-up.

2. Cognizant
Recovery And Mitigation Costs: $50 Million To $70 Million
Cognizant publicly admitted April 18 that its network was infected with Maze ransomware, which ended up encrypting servers and taking out some of the company’s work from home capabilities. It slowed the ability of the Teaneck, N.J.-based company, No. 6 on the 2020 CRN Solution Provider 500, to enable more work from home by taking out tools that Cognizant used to automate and provision laptops.
CRN first reported that some Cognizant employees lost email access as a result of the ransomware, forcing them to communicate with coworkers and customers through other means. By May 7, Cognizant was saying that it had fully recovered from the ransomware infection and restored most of its services. The incident only impacted Cognizant’s internal network and not customer systems, the company said.
The revenue and corresponding margin impact of the ransomware attack are expected to be in the range of $50 million to $70 million in the second quarter of 2020, Cognizant said May 7. The company said it expects to incur additional legal and consulting costs tied to the investigation, service restoration and remediation of the ransomware attack.

1. ISS World
Recovery And Mitigation Costs: $75 Million To $112.4 Million
A Feb. 17 ransomware attack forced Denmark-based facilities management firm ISS World to switch off its networks and leave hundreds of thousands of employees without access to their systems or email, according to Computer Weekly. Three days later, ISS World said the root cause of the attack had been identified and the company was working with outside experts to gradually restore our IT systems.
By March 20, ISS World said it had regained control of most of its IT infrastructure and was systematically relaunching business-critical systems, albeit with somewhat reduced functionalities. ISS said it expects to be finished with restoring and rebuilding its systems and IT assets by the end of 2020.
ISS expects to spend $45 million to $75 million on: remediating the IT incident; putting in workarounds to enable the continuous delivery of service; service underperformance because of system down-time; and cost duplication associated with contract operation. A rebuild of part of ISS’s IT infrastructure due to damage to some of the company’s IT assets is expected to cost between $22.5 million and $45 million.