The 20 Hottest Cybersecurity Products At Black Hat 2021
From protecting containers and cloud-native workloads against common threats to simplifying the process of hunting and mitigating external threats to automating incident investigations with actionable insight, here’s a look at the 20 hottest cybersecurity products unleashed at Black Hat 2021.

Securing The Future
Vendors are taking advantage of Black Hat 2021’s bright spotlight to launch new cybersecurity products, features, platforms and tools that will set the stage for the months and years to come. For the hundreds of exhibitors found at Black Hat, the Business Hall provides a chance to promote new products and highlight strategic shifts to an in-person audience of approximately 5,000.
Some of the most common areas for product innovation this year include cloud security, zero trust, and detection and response. New cloud security tools focus on everything from protecting cloud workloads and apps to integrating and safeguarding data in the public cloud, while the detection and response investments are intended to bolster threat hunting, investigations and management capabilities.
From protecting containers and cloud-native workloads against common threats to simplifying the process of hunting and mitigating external threats to automating incident investigations with actionable insight, here’s a look at the 20 hottest cybersecurity products unleashed at Black Hat 2021.
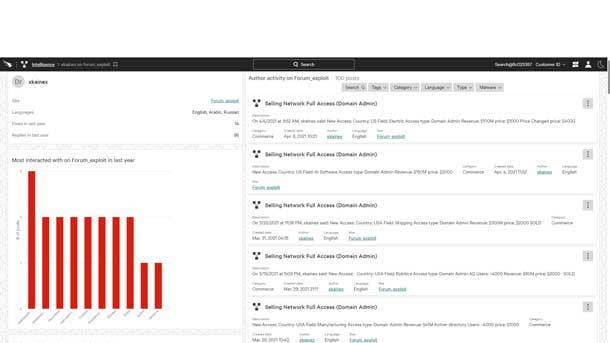
CrowdStrike Falcon X Recon+
CrowdStrike Falcon X Recon+ simplifies the process of hunting and mitigating external threats to brands, employees and sensitive data. Falcon X Recon+ threat experts manage digital risk protection efforts by monitoring, triaging and assessing the responding to threats across the criminal underground, enabling customers to focus solely on their business.
Falcon X Recon+ experts monitor data from thousands of restricted forums, marketplaces, messaging platforms, social media posts and data leak sites to provide relevant real-time warnings, identifying data exposure and threats to the enterprise. The offering delivers visibility into cybercriminal activity that goes beyond the internet to include botnet, DDoS configurations and messaging applications.
Falcon X Recon+ experts work on the customer’s behalf to identity and facilitate the takedown of fraudulent accounts, phishing websites, domains and malicious posts that potentially harm a business’ reputation. Customers are also invited to the CrowdStrike Quarterly Threat Brief, where the company’s experts provide insight into current and trending activity across the threat landscape, the company said.
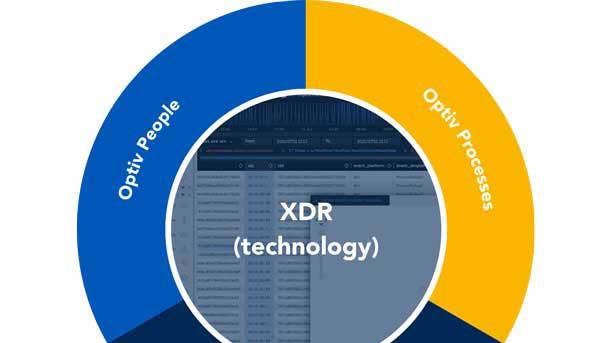
Optiv Managed Extended Detection and Response
Optiv Managed Extended Detection and Response () ingests data across various layers of technologies to correlate, normalize, enrich and enable automated responses to malicious activity in real time. By automating incident investigations with actionable insight, organizations can detect threats faster and prioritize which threats to mitigate first, significantly reducing the attack surface.
The product is integrated into an organization’s current security technology to gather events, enrich the event data and escalate potential threats. From there, Optiv MXDR can identify the threats that matter to ensure rapid investigation as well as determine the severity, impact, affected assets and root cause of the attack, properly assessing business risk.
Optiv MXDR leverages Security Orchestration, Automation and Response (SOAR) to respond quickly, eliminate threats and administer containment actions with runbook development. Security incidents are managed to completion by Optiv MXDR with corresponding after-action reviews, the company said.

Bitdefender GravityZone Security For Containers
Bitdefender’s GravityZone Security for Containers delivers threat prevention, extended endpoint detection and response and anti-exploit protection for containers running in private and public clouds with comprehensive visibility and control. It has an unmatched ability to prevent, detect and remediate threats against cloud workloads, including those made against Docker and Kubernetes containers.
GravityZone Security for Containers protects containers and cloud-native workloads against Linux kernel, application zero-day and known exploit attacks in real time, identifying which images and pods were involved in an incident. It eliminates Linux security compatibility challenges via a single, lightweight agent that enables companies to update Linux distributions faster without sacrificing security efficacy.
The product is multiplatform and provides complete security visibility and controls over all containers and workloads across hybrid or multi-cloud environments from a single dashboard, Bitdefender said. It also maps cloud workload container attacks to the MITRE ATT&CK Framework, detecting 100 percent of attack techniques against Linux systems in the most recent MITRE ATT&CK test.

McAfee Enterprise MVision Private Access
McAfee Enterprise MVision Private Access enables granular zero trust access to private applications hosted in public or hybrid cloud environments from any location or device. It offers integrated data loss prevention and threat protection capabilities for securing access and data collaboration around zero trust network access (ZTNA), according to McAfee Enterprise.
MVision Private Access provides complete coverage across managed and unmanaged devices and performs continuous risk assessment by deriving enhanced device posture information through McAfee’s endpoint security technology. It also works in conjunction with MVision Unified Cloud Edge to provide visibility and control across cloud, private applications, web and endpoints, the company said.
MVision Private Access enables advanced threat protection and complete control over data collaborated through private access sessions, preventing inappropriate handling of sensitive data and blocking files with malicious content. It also creates software-defined perimeters to provide limited access to applications based upon the user and device entitlements, preventing the lateral movement of threats.

Fortinet FortiTrust
Fortinet’s FortiTrust security services offer user-based licensing across all networks, endpoints and cloud and are initially focused on zero trust network access and identity verification. FortiTrust’s flexible user-based licensing eliminates the need to track device counts or bandwidth consumption and makes it easy to calculate total cost with built-in volume discounts, according to the company.
FortiTrust’s initial services portfolio includes FortiTrust Access and FortiTrust Identity with additional service options for SASE, CASB and endpoint protection platforms expected to be released. FortiTrust Access enables organizations to deploy zero trust network access with user-based pricing, which is crucial to maintaining consistent protection, visibility and control across highly distributed networks.
FortiTrust Identity, meanwhile, offers cloud-based multifactor authentication for identity verification while also providing the multifactor authentication needed to control application access. All told, Fortinet said FortiTrust provides organizations with a unified services offering to protect any network, endpoint or cloud with a simplified consumption and single licensing model for all form factors.
Balbix Automated Cyber Risk Quantification
Balbix’s new Automated Cyber Risk Quantification (CRQ) offering allows organizations to produce a single, comprehensive view of their cyber-risk in dollars so they can prioritize and fix security issues faster. To protect itself against ransomware attacks, an organization could for example use Balbix to identify the assets that would be most costly if held to ransom and act quickly to reduce these risks.
Calculating breach risk in monetary terms provides a common language that organizations can use to prioritize projects and spending and track the effectiveness of their overall cybersecurity program. But most organizations have struggled with measuring cyber-risk due to their reliance on complicated manual processes and dozens of isolated IT, security and business tools, according to Balbix.
Balbix CRQ uses machine learning and automation to quantify the likelihood and the impact of a potential breach, as well as remove complex and error-prone tasks. As a result, Balbix said organizations can build a unified cybersecurity asset management program; prioritize enterprise vulnerabilities; quantify cyber-risk in monetary terms; and customize security analytics and board-level reporting.
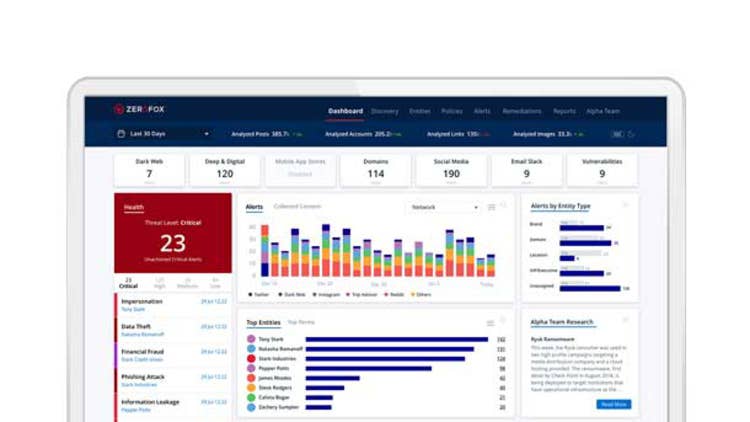
ZeroFox External Threat Hunting Platform
ZeroFox’s enhanced threat hunting platform delivers a complete global view of active and historical threat intelligence data to understand risks across both physical and cyberdomains including social media as well as the surface, deep and dark webs. The platform provides integration into existing systems through workflows, a new hunting interface and integrated data services, ZeroFox said.
The enhanced ZeroFox threat hunting capabilities will increase access to raw data and finished intelligence to help quickly inform security decisions, according to the company. The new threat hunting capabilities allows for direct access to enriched and raw intelligence feeds, searching across the company’s global data lake, and an elite team of dark web operations skilled at adversary engagement.
Customers can deeply investigate relationships between various actor and threat indicators as well as access ZeroFox’s unique threat intelligence data lakes. These data lakes consist of petabytes of curated intelligence and raw threat data on malicious domains and URLs, hosts, command and control networks, compromised credentials, attacker attribution, attacker tools and phishing kits, and ransomware.
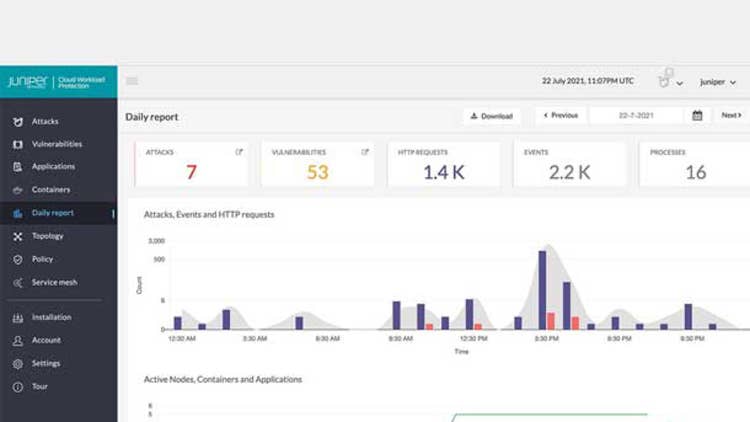
Juniper Cloud Workload Protection
Juniper Cloud Workload Protection automatically defends application workloads in any cloud or on-premises data center environment against application exploits as they happen, including memory-based attacks. It ensures that production applications always have a safety net against vulnerability exploits, keeping business-critical services connected and protected.
The software protects applications from malicious actions such as exploitation and data theft without any manual intervention, catching sophisticated attacks that endpoint detection and web application firewall tools cannot. Juniper Cloud Workload Protection also provides real-time protection against memory-based attacks, including fileless, return-oriented programming and buffer overflow attacks.
Juniper Cloud Workload Protection continuously assesses vulnerabilities in applications and containers to detect serious and critical exploit attempts as they happen and delivers information on the exploit attempt to DevSecOps teams. The tool also provides rich application-level security event generation and reporting, including application connectivity, topology and detailed notes about the attempted attack.

Aqua Platform
Aqua Security’s new cloud-native application protection platform leverages a unified console to ease the journey from scanning and visibility to workload protection in cloud-native environments. The platform reduces administrative burden and allows security teams to start with scanning and cloud security posture management, and then add in sandboxing capabilities and workload protection as needed.
The unified approach lowers management overhead for advanced runtime features and is available as a SaaS or self-hosted deployment, according to Aqua Security. It also enables customers to benefit from better context and prioritization in identifying risks and threats, adopting a full life-cycle approach to securing cloud-native applications.
The Aqua Platform enhances runtime protection with file integrity monitoring for containers as well as threat response policies that specifically block reverse shell attempts and cryptomining. The platform can also define custom severities for specific vulnerabilities to conform with customers’ internal standards, according to Aqua Security.
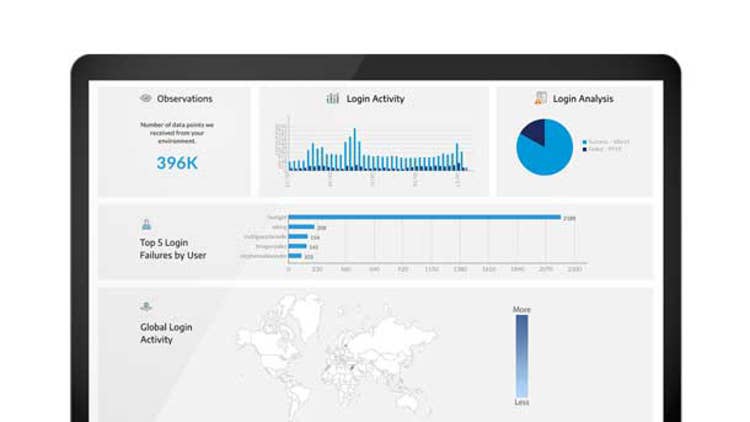
Arctic Wolf Cloud Security Posture Management
The new Cloud Security Posture Management feature of Arctic Wolf Managed Risk scans Amazon Web Services, Microsoft Azure and Google Cloud environments to identity potential misconfigurations and other cyber-risks. Most security offerings don’t have the autonomous capability to easily identify and remediate cloud misconfigurations, which Arctic Wolf said leaves organizations exposed to massive risk.
The CSPM feature of Arctic Wolf Managed Risk provides customers with a complete inventory and categorization of all assets found within the cloud environment for auditing, monitoring and executive reporting purposes, according to the company.
Arctic Wolf CSPM assigns a risk score to quantify how a cloud environment compares with generally accepted cloud configuration benchmarks, the company said. It also provides rich context and remediation recommendations to close cloud vulnerability gaps and harden security posture, according to Arctic Wolf.

DomainTools IP Risk Feeds
DomainTools rolled out the Domain Discovery Feed, IP Hotlist and Hosting IP Risk Feed to provide security teams with visibility into risk levels of domain and IP traffic to strengthen network defense. The IP Hotlist identifies the riskiest population of hosting IP addresses by examining the ratio of high-risk to legitimate domains as well as the level of traffic with known or predicted malicious domains.
The Hosting IP Risk Feed, meanwhile, is a daily feed of all IP addresses to be found hosting at least one domain regardless of traffic or risk. Typical Risk Feed size can exceed 15 million to 20 million IP addresses, and the feed is ideal for users who wish to apply their own criteria to evaluate IP addresses for risk or characterize them for other purposes.
The Domain Discovery Feed is a simple text file of newly registered and newly observed domain names, giving users the maximum flexibility to create alerts or block rules for network and host defenses. The feed can enable the creation of automatic blocking rules for most traffic, or quarantine/inspection rules for SMTP and other protocols that can accommodate various dispositions.
Sumo Logic Span Analytics
Sumo Logic Span Analytics allows customers to search, analyze and query structured and unstructured application data, including transaction traces, logs and metrics. This provides observers with a simplified search experience as well as the ability to filter, transform and aggregate data to diagnose and resolve problems faster, according to Sumo Logic.
With Sumo Logic Span Analytics, developers can identify issues and troubleshoot performance problems more quickly by discovering emergent patterns and relationships that are impossible to predefine.
Teams can leverage the familiar Sumo Logic Query Language to interrogate multiple sets of telemetry from a single console, according to the company. Alternatively, the company said teams can skip the Sumo Logic Query Language and use an intuitive user interface to build simple or sophisticated queries and aggregate results.

Nuspire Managed Endpoint Detection And Response
Nuspire’s Endpoint Detection and Response (EDR) service provides the SOC as a Service for customers when that have limited resources, time or expertise to manage or monitor their Carbon Black or SentinelOne EDR technology. With this service, Nuspire’s security experts automatically respond to incidents, help customers understand what technology best suits their organization’s needs, and receive full visibility.
Managed EDR givers CISOs and security analysts a crystal-clear picture into the security posture of their organizations in real time while controlling and contextualizing all available information about a security program at a glance. Organizations are increasingly realizing how essential the right skills and staff are to managing and monitoring EDR technology purchased during the pandemic, according to Nuspire.
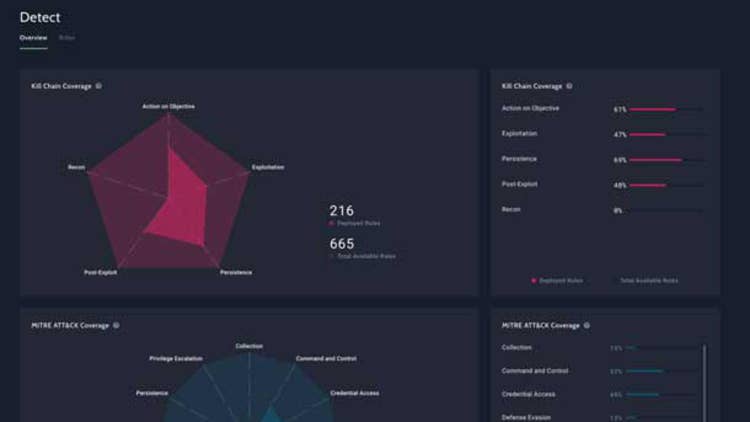
ReliaQuest GreyMatter Detection And Hunt Capabilities
A new set of capabilities in ReliaQuest’s open XDR-as-a-Service platform will allow security operations teams to improve detection, threat hunting and ease of management on the platform. The new release of GreyMatter extends the ability for analysts to see in an instant what their coverage is versus gaps against industry-standard frameworks like MITRE ATT&CK and Kill Chain, according to ReliaQuest.
In addition, analysts using GreyMatter can now drill down into specific detections to understand how a rule was triggered, allowing them to gather the right contextual information for further investigation and analysis. Proactive threat hunting capabilities, meanwhile, are geared toward helping analysts manage overall risk better, with analysts getting not only efficiency but also reliability and consistency.
GreyMatter reduces complexity by enabling analysts to run additional queries from within a hunt campaign outside the original parameters, reducing the need for analysts to pivot to other tools, ReliaQuest said. Customers can also integrate GreyMatter into their single sign-on to improve security and simplify access while also reducing the complexity of managing GreyMatter in their environment.
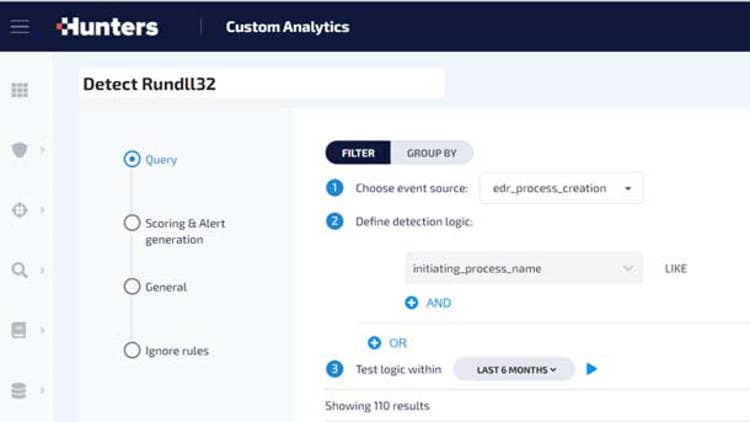
Hunters Open XDR Capabilities
Hunters rolled out a set of capabilities that further strengthen its position as a key alternative to SIEM for companies looking to boost their incident detection, investigation and response. Every alert in the Hunters platform is now enriched with additional supporting data correlated with information from external sources, allowing investigations to now focus on the key entities involved in an activity.
Auto-Investigations are grouped into key meaningful entities that are related to the alert such as host, person and process, to enable a deeper understanding of the maliciousness of the alert. And with Custom Detections, users can add their own detection logic on top of the ingested and normalized data, defining their own detection rules or using logic taken from external public repositories.
Signals and leads generated by these detections are automatically investigated, scored, cross-correlated and presented to the user with comprehensive context, Hunters said. And the Hunters XDR Dashboard and Reporting function allows security teams to use Hunters’ data as well as raw data from the security data lake to create custom dashboards to visualize SOC metrics and monitor activity in the network.
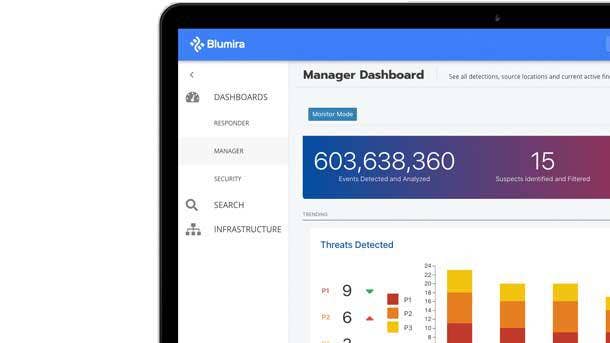
Blumira Cloud Collector
Cloud Collector will enable time-strapped IT administrators to set up integrations within Blumira more quickly and easily, connecting to cloud services like Amazon Web Services, Microsoft 365, Azure and Duo Security through APIs. The new proprietary detection system delivers real-time threat notifications in a matter of milliseconds so that IT staff can respond early enough to minimize the impact of an attack.
Blumira also plans this fall to release new visualized security reports for Windows, Azure and Active Directory to help administrators gain more visibility and insight into their environment at a glance. This is expected to make it easier for administrators to quickly triage or investigate incidents further, Blumira said.
The company said it offers the fastest time to deployment with broad cloud coverage, enabling organizations of all sizes to detect and respond to cloud security threats five times faster than the average SIEM provider. Blumira automatically provides ongoing parsing support for many different data types, saving customers a substantial amount of development time.

Fortinet FortiGate 3500F
Fortinet’s new FortiGate 3500F next-generation firewall is designed to protect organizations with hybrid data centers against the ever-growing threat landscape and ransomware attacks. It’s built with zero trust network access capabilities to deliver consistent security and a seamless user experience to any user at any location, according to the company.
The FortiGate 3500F secures the data center edge, core and interconnect by providing ultra-fast secure data-center-to-data-center paths to build disaster recovery sites. It also enables organizations to secure data-center-to-cloud paths for cloud on-ramps with full compliance and controls, according to Fortinet.
The firewall offers the industry’s highest security compute rating to protect organizations from network, application and file-based attacks, Fortinet said. The FortiGate 3500F also allows organizations to host applications anywhere with consistent policy controls to enable and secure hybrid workforce models with a seamless and superior user experience.
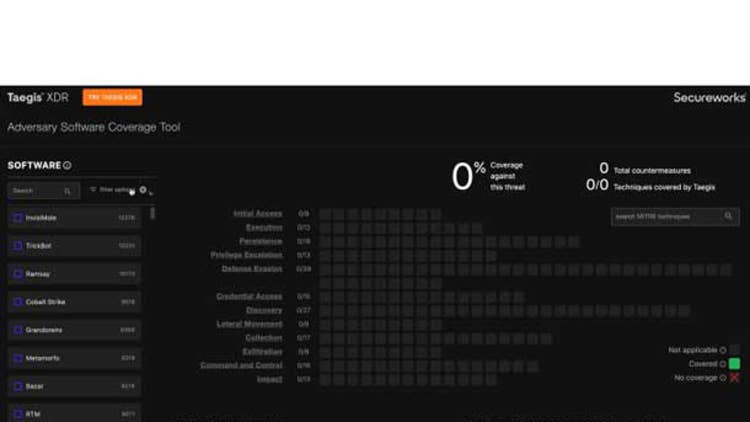
Secureworks Adversary Software Coverage
Secureworks’ new free Adversary Software Coverage (ASC) tool lets security operations professionals interactively explore how Taegis XDR (extended detection and response) coverage and countermeasures map to the specific MITRE ATT&CK tactics, techniques and procedures. These tactics and techniques are used by more than 500 adversarial software types against the MITRE framework, including ATT&CK v9.
Taegis XDR ASC models cyberattacks by threat category or malware name based on security use cases, according to Secureworks. It also allows defenders to understand attack sequences in terms of adversary software behaviors that are mapped to MITRE ATT&CK techniques, Secureworks said.
Finally, Secureworks said the Taegis XDR ASC tool can visualize the end-to-end attack surface as well as the security tools required to minimize exposure and reduce risk.

Corelight Smart PCAP
Corelight Smart PCAP delivers weeks to months of packet visibility interlinked with Corelight logs, extracted files and security insight for fast pivots and investigation. Smart PCAP is available for the Corelight AP 3000 Sensor, allowing defenders to capture just the packets needed for investigations and retrieve them with a single click from their Security Information and Event Management platform.
The offering is encryption-aware, tracks protocol activity across ports, and directly integrates with Zeek, the security gold standard for network evidence, according to Corelight. With Smart PCAP, Corelight said analysts can configure and selectively capture packets based on protocols, detection and anomalous traffic activity.
Corelight Smart PCAP delivers a superior and more cost-effective offering for security teams, delivering up 50 percent cost savings and 10 times longer retention versus full packet capture. With Corelight logs and captured packets, the company said defenders can achieve 100 percent visibility and investigate network activity that occurred months, even years, in the past.
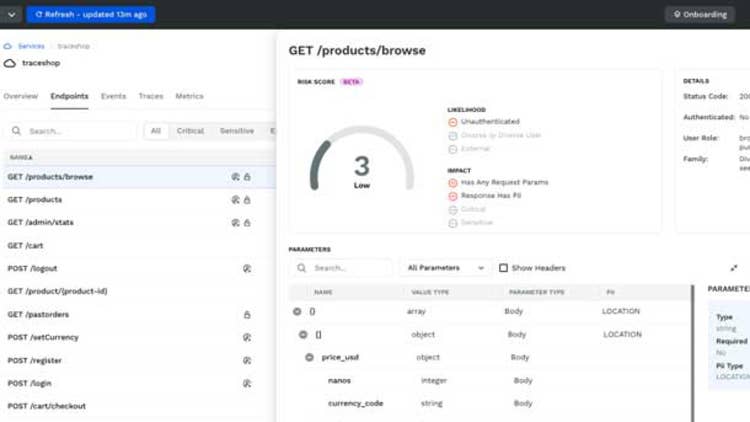
Traceable Free API Security Solution
Traceable’s free API security offering enables developers and security operations teams to improve the API security of their applications without the holdup of budgetary approval for costly technology. The company said its enterprise-grade API offering provides visibility, protection and analytical insight to help organizations manage their API security risks.
Powered by its distributed tracing and unsupervised machine learning technologies, Traceable AI addresses API security by learning the application context and normal behaviors. Deep API insight and machine learning-enhanced anomaly detection enable the Traceable AI Free tier offering to detect and block known and unknown threats with no signature tuning and minimal false positives, according to the company.
The free version of Traceable API includes continuous discovery and inventory of all APIs; real-time, automatic API documentation; insight into API runtime behavior; continuously updated API risk scores; API and web application protection; vulnerability detection of API misconfigurations; performance metrics for establishing normal versus abnormal behavior; as well as the ability to block threats.